Investigate Alerts
Understand the contextual information available to determine which alerts are worth looking at, assess an alert's potential impact, and decide your next steps.
Although Alert Triage has already automated much of your workflow, there may still be hundreds of alerts that appear under a filter. Use the contextual information provided with each alert to correlate alerts and build a complete picture of your organization's threat landscape. Once you understand this context, you can make informed decisions about what to investigate and how to respond.
1. Determine where to start investigating
Get an overview of what's happening and decide where to start:
To view all alerts, navigate to the All Saved Filters
 tab, then click Review All Alerts.
tab, then click Review All Alerts.To view a subset of alerts you want to investigate further, apply an existing filter or create your own filter.
Alerts are sorted based on when they were created, from latest to oldest.
To further narrow down the alerts you see, filter them by priority.
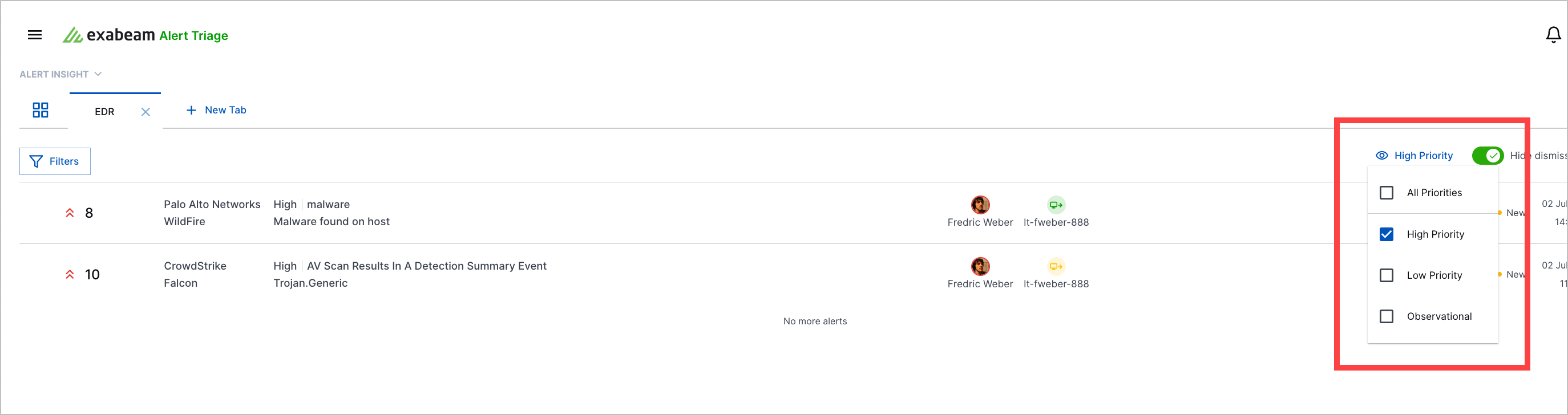
From the contextual information provided at a glance, learn about:
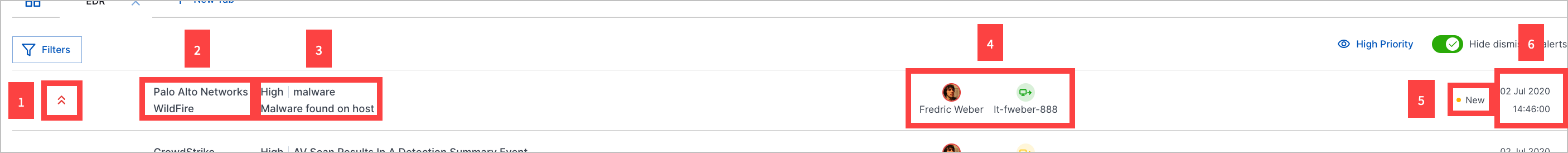
1 The alert's priority: high priority, low priority or observational.
A high priority suggests you should investigate the alert first.
A low priority suggests you should investigate the alert after higher priority alerts.
Observational suggests the alert is uninteresting.
2 The vendor that created the alert; for example, Crowdstrike Falcon
3 The alert severity according to the alert source: low, medium, high, or critical; the alert type; and the alert name.
4 The users and assets associated with the alert. The colors indicate their Advanced Analytics risk score: red for high, green for low. Assets are classified as a source using an outbound arrow or destination using an inbound arrow.
5 The alert status:
New – By default, an alert has a New status. Once you change an alert to another status, you can't revert the status to New.
In Progress – Someone was assigned to investigate the alert and assess its impact. The alert is unassigned by default. If you ever reassign the alert to Unassigned, the alert status won't change.
Escalated – The alert is a potential true positive you want to report. This creates an incident in Case Manager.
Dismissed – The alert is a false positive.
Resolved – You resolved the alert without escalating it.
6 The date and time the alert was created.
If an alert looks like it may be worth investigating further, click the alert to view more details.
2. Assess an alert's potential impact
To better understand if an alert may be a true positive, view further details about the alert to further investigate it and assess its potential business impact.
From the list, select an alert.
To view the raw log, select the View logs. View details about time, date, alert type, severity, source IP, source host, or user.
View the alert's priority.
Under USER/DEVICE, view the users and devices associated with the alert and whether they triggered other alerts in the past week. To learn more about the user or device, click on its name and view more details in Advanced Analytics. To understand the alert in the context of other anomalies, click Go to Timeline.
To understand what happened before this alert was triggered, under NEARBY ANOMALIES, view the five anomalies with the highest risk scores that occurred previously. To view all previous anomalies in the session, click Show all.
3. Respond to the alert
After assessing this contextual information about the alert and associated users or devices, resolve, dismiss, or escalate it.
