How to Run Query Searches in Exabeam Data Lake
Data Lake can be customized to search for variations and combinations in the captured data to suit needs and circumstances. The Search UI offers an input box for customers to apply their own criteria.
Complex or heavily used queries can be saved to the local library for re-use.
Note
Here are additional methods to consider when handling large data volumes:
Filtered Searches -- Narrow the amount of data to search, you can apply filters using context tables to optimize your queries.
Cross-cluster Searches -- In a multi-cluster deployment, you can perform searches simultaneously across all log ingesting clusters.
The following table shows the accepted syntax for querying in Data Lake . Data Lake query semantics applies a limited subset of Lucene.
Note
Note that AND, TO, NOT, and OR are case-sensitive operators (i.e. all upper-case only).
Types | Description | Example |
|---|---|---|
Terms | Alpha-numeric text to search for |
Look for records with string |
Fields | Data type or category name (i.e. key within [key,value] of structured data) | Search any field by field name followed by a colon "
|
Operators | Joining of two or more criteria | |
or | Both terms must exist |
Look for records with both |
| Either term may exist |
Look for records with either in category user |
or | Term must not exist |
Look for records with NoteThe |
| Range of values with lower and/or upper limits, expressed as numeric values
|
|
Grouping
| Multi-term search processed first by criterium set in parentheses |
Look for records with leading string |
Wildcards
| [empty] Single character variation search (Cannot be used as leading character.) [empty] Multi-character variation search (Cannot be used as leading character.) |
Look for records with string
Look for records with string |
Special Characters
| Characters |
Look for records with string Alternative method: Look for record with hyphenated string |
Regular Expressions | Regular expression patterns can be embedded in the queries by wrapping them in forward-slashes (" |
|
Tokenized Fields | System field names invoke parsing when standardized delimiters are encountered, such as | Sample search for "[email protected]"
Yields results because
No results because |
| Determine whether fields that exist (have a value) or not |
Yields logs where user field is populated
Yields logs where |
| Search string qualifier when a keyword type field cannot be parsed. Do not use |
This search will return data with a non-parsable host field. |
Note
The default operator in searches is OR unless you explicitly form your query to not apply it.
Correctly searching and synchronizing time between log messages is critical to forming a timeline of events you are analyzing. There are multiple ways time information is stored in log messages. It is important to distinguish between them and use them accordingly.
Parameter | Description |
|---|---|
@timestamp | This is a search value. It is the default time field that reflects the time when log message was received at the Data Lake ingestion layer. |
indexTime | This is a search value. It is the time the Data Lake parser/enricher processed the log message for indexing. |
exa_adjustedEventTime | This is a message log field. It is the time value derived from event itself with adjustments such as time zone, if present in log message and parsed out. |
exa_rawEventTime | This is a message log field. It is the non-adjusted time value derived from log message itself. If log message does not have a time field, it defaults to ~indexTime. |
In addition to using manually created search strings, users have the option to filter data using out-of-the-box filters available in the Search UI.
The Field Explorer is the quick pick tool for viewing captured data in known categories (both out-of-the-box and custom filters). Click on the hyperlink for a given sub-category and menu of known values are listed to filter further. View field visualization can be selected to immediately visually organize data from the shown list.
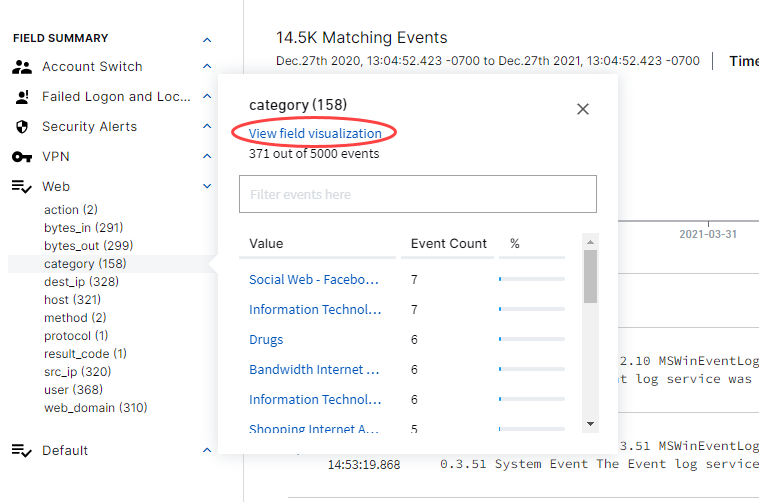
Out-of-the-box filters are available in the Search UI. Once data, using preliminary parameters (e.g. time range) is gathered, a categorized Field Explorer appears below the Timeline. Information is separated by areas of focus such as: Account Management, Failed Logon and Lockout, Windows Authentication, and Default. Select links under each area to further filter data by sub-selection or field query. Events counts are listed in each linked category. Each activated filter is reflected in query syntax in the Search input field.
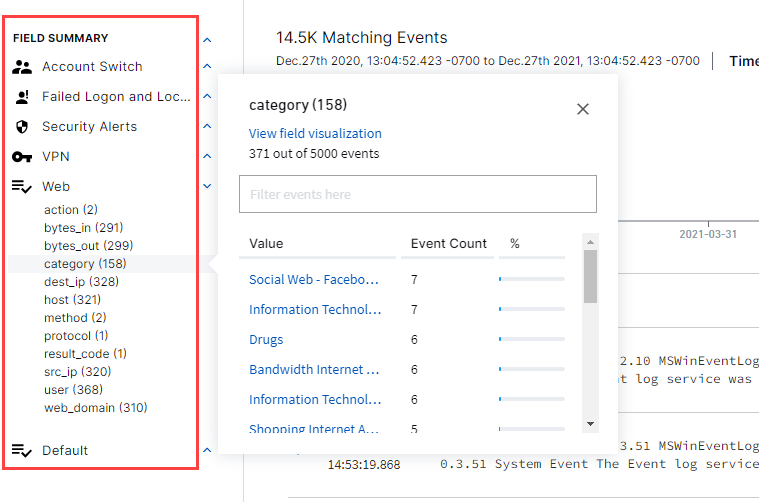
These categories are part of the "exa_category" set and there exist subcategories to narrow searches with. The queries are in the form:
exa_category:"<category>" AND <field>:"<value>"
Category (for exa_category) | Description | Field |
|---|---|---|
Account Management | Events relating to creation, deletion, and modification of entity's computer accounts |
|
Account Switch | Events indicating that user A is operating as user B (e.g. runas, sudo) |
|
Active Directory | Events related to Microsoft Active Directory |
|
Application | Events relating to applications (e.g. pull/sync from a code repository) |
|
Audit Change | Changes to the audit policy of a computer |
|
Authentication | Events related to connection credentials |
|
Badge | Physical access log events |
|
Configuration Change | Events indicating the setting of a system has changed |
|
DHCP | Events from DHCP service |
|
DLP | Events from a data leak protection system |
|
DNS | Events from a DNS system |
|
Database | Change events for database endpoints |
|
Endpoint | Actions of interest at endpoints |
|
Failed Logons and Lockouts | Login failure events |
|
File | File access events |
|
Logout | Logout events |
|
Network | Network traffic events |
|
Network Alert | Network access events |
|
Print Activity | Printing/Printer action events |
|
Privileged Access | Action events connected to highly restricted assets |
|
Security Alerts | Actions for known malicious payloads |
|
System Event | System-level events |
|
VPN | VPN login events |
|
Web | Web-based access events of interest |
|
Windows Authentication | Microsoft Windows login-based events |
|
Exabeam parses and categorizes different values for fast searching, using the query format:
<field>:"<value>"
Field | Description | Value |
|---|---|---|
exa_activity_type | Actions that are considered behaviors of concern in general practice |
|
exa_addRiskToAsset | Incremental risk score changes marking milestone triggers |
|
exa_adjustedEventTime | Time offsets for event of interest. It is the time value derived from event itself with adjustments such as time zone, if present in log message and parsed out |
|
exa_category | Exabeam core categories of interest in threat detection | See "Searches using Exabeam exa_category" section |
exa_device_type | Device category |
|
exa_outcome | Milestone marker for event result triggers |
|
exa_parser_name | Filter by parser name |
|
exa_rawEventTime | Event time window of interest (UTC). It is the non-adjusted time value derived from log message itself. If the message does not have a time field, it defaults to ~indexTime. |
|
exa_rule_category* | Filter by defined rule category | category name (See "Searches using Exabeam exa_category" section) |
exa_rule_config_cardinality_field* |
| |
exa_rule_config_is_enabled* | Events when rule is enforced or disabled |
|
exa_rule_config_max_cardinality* |
| |
exa_rule_config_num_events* | Threshold count for events of interest |
|
exa_rule_config_query_key* |
| |
exa_rule_config_realert* | Threshold count for recurring events |
|
exa_rule_config_terms_size* |
| |
exa_rule_config_timeframe* | Time range for events of interest |
|
exa_rule_config_top_count_key* |
| |
exa_rule_description* |
| |
exa_rule_id* | Filter for events that trigger a specified rule, specified by rule ID |
|
exa_rule_name* | Filter for events that trigger a specified rule, specified by rule name |
|
exa_rule_search_query* | See query rules in "Syntax" section | |
exa_rule_severity* | Threshold trigger based on severity level |
|
exa_rule_type* |
| |
exa_security_alerts |
|
* "exa_rule_" fields are parsed out of correlation rules triggered by Data Lake .
