Create a Log Source Policy
You can configure a log source policy that defines criteria for monitoring log sources and set up notifications for log sources that go silent. Based on the configured policy, you can easily monitor log sources and generate real-time alerts for any anomalies, ensuring timely threat detection and proactive incident response. With the help of log source policies you can identify unique log sources and detect the silent log sources.
Log in to the New-Scale Security Operations Platform with your registered credentials as an administrator.
On the New-Scale Security Operations Platform home page, click the Log Sources tile to view Log Source details. Alternatively, in the left pane, navigate to the Log Sources section.
Click New Policy.
On the New Policy page, enter the following information.
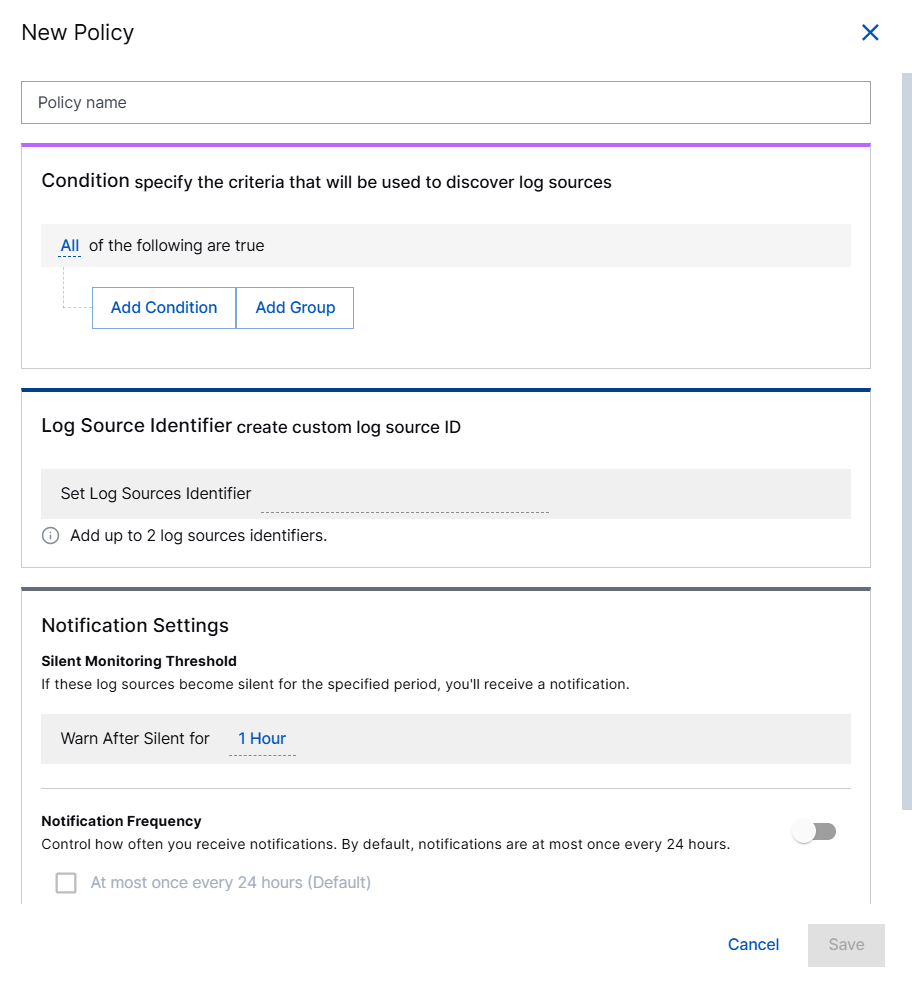
Policy Name – Specify a name for the log source policy.
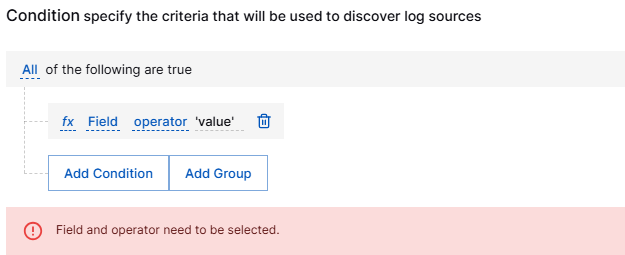
Condition – Define criteria to discover log sources using conditions.
Add Condition – Specify the values for Field and operator based on which you want to discover various log sources.
You can use any CIM field as a Filter field. For example, to apply the filter for all Microsoft logs, configure the filter
vendor contains 'Microsoft'.Note
A log source is always matched to the same policy consistently. After a log source is matched to a specific policy, it will remain associated with that policy unless the policy is disabled or deleted. As for policy conditions, expressions like
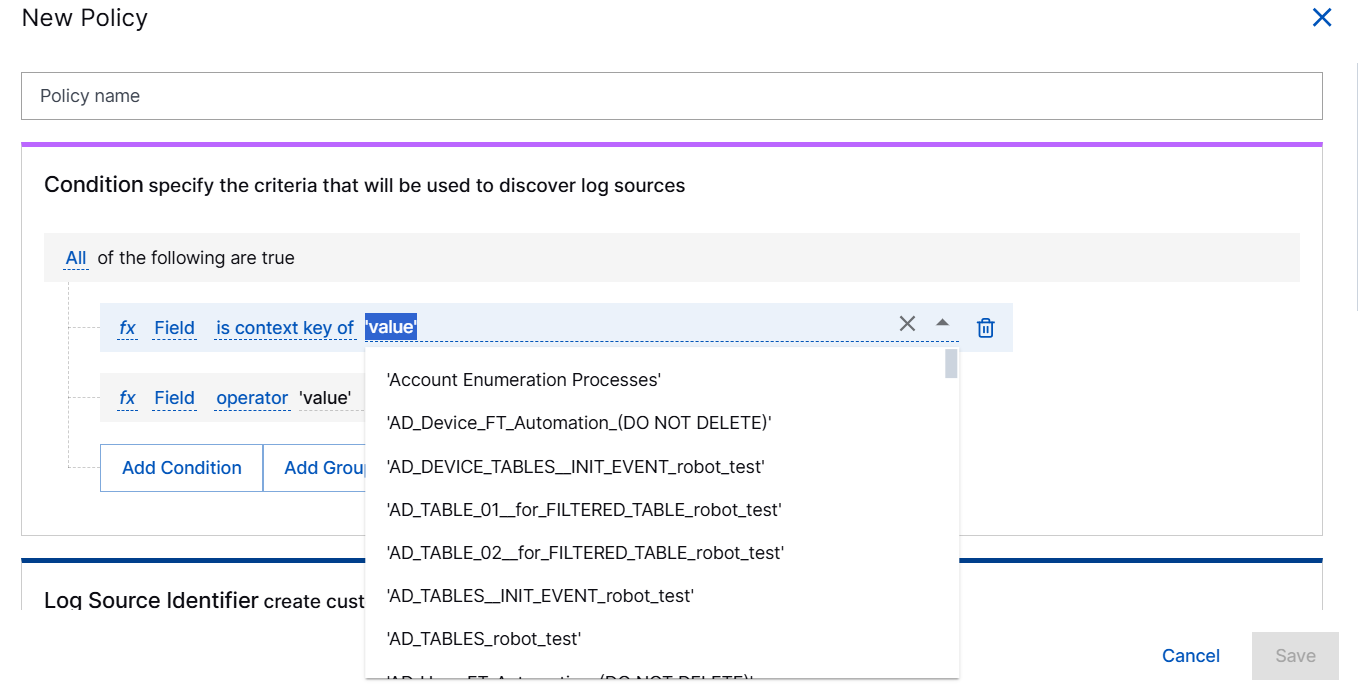
IsContextKey,GetContextAttribute, andGetDynamicContextAttributeare not supported. Although these expressions are available when configuring enrichment rules, you cannot use them in log source policy conditions.The IsContextKey can be used with any Context Tables available in your environment.
If you select the Operator Is Context Key, you can select a context table from the list of context table names.
Add Group – Click Add Group to configure complex filters based on multiple conditions.
Log Source Identifier – Select up to two identifiers to serve as unique identifiers to discover log sources.
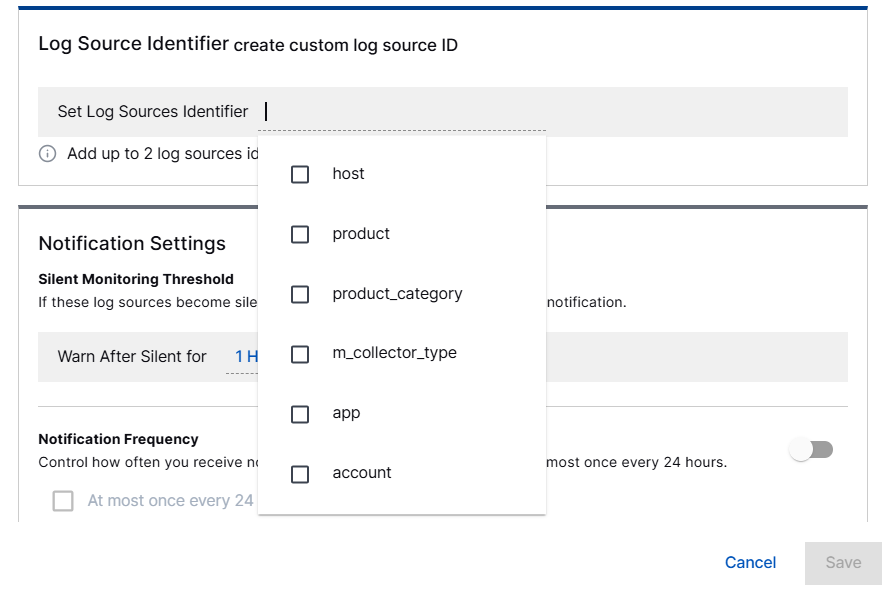
Most commonly, you can use a single identifier. For example, to identify Windows hosts, you can select the host option as the Log Source Identifier. In more complex cases, such as monitoring individual applications within each host, two Log Source Identifiers can be configured—host and product.
Notification Settings – Set the threshold and frequency for notifications about silent log sources. See Configure Notification Settings for Log Sources for details.
Configure Notification Settings for Log Sources
Using the notification settings, you can configure when and how you get notifications about silent log sources in a log source policy.
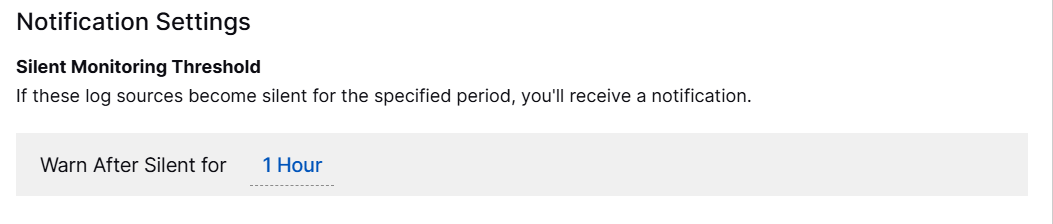
Set Silent Monitoring Threshold
Under Silent Monitoring Threshold, in the Warn After Silent for field, select a duration between 1 - 72 hours to set a condition for detecting a silent log source. You can define a period of inactivity after which a log source is considered silent. For example, if a certain log source remains inactive for the specified duration, it will be classified as silent.
Configure Notification Frequency
To manage notification frequency for detecting silent log sources, enable the toggle and select the following options based on your preference.
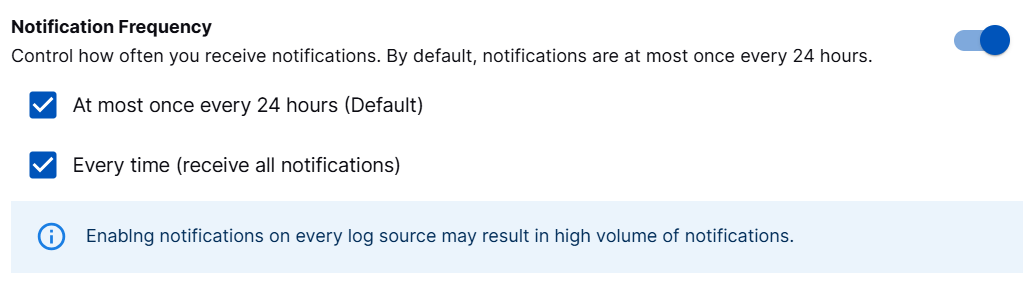
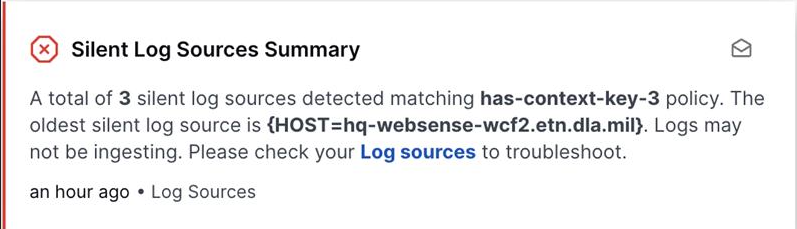
At most once every 24 hours (Default) – Select to receive in-app notifications. The first notification is sent when a log source first goes silent, with follow-up notifications every 24 hours while it stays silent. This is a default option that provides a daily summary of silent log sources.
Refer to the following example of an in-app notification.
Every time (receive all notifications) – Select to receive all notifications immediately each time a log source goes silent via your preferred notification channel based on the webhook that you configured.
You can create a notification channel and set the notification preferences by navigating to Settings > Global Notifications > Add Channel.
For more information about creating a notification channel for silent log sources, see Add a New Notification Channel in Manage Global Notifications Preferences.
Refer to the following example of a notification that is sent to the notification channel that you configured.
{ "application": "Log Sources", "subject": "Silent Log Sources Detected", "description": "An active Log sources is detected to be silent.", "severity": "Critical", "category": "Collectors", "message": "The status of the log source with identifiers {host=IyobdhiL, product=Sysmon} in policy Microsoft_Windows_Domain has changed to silent. Logs may not be ingesting.", "recommendation": "Please check your Log sources to troubleshoot." }Note
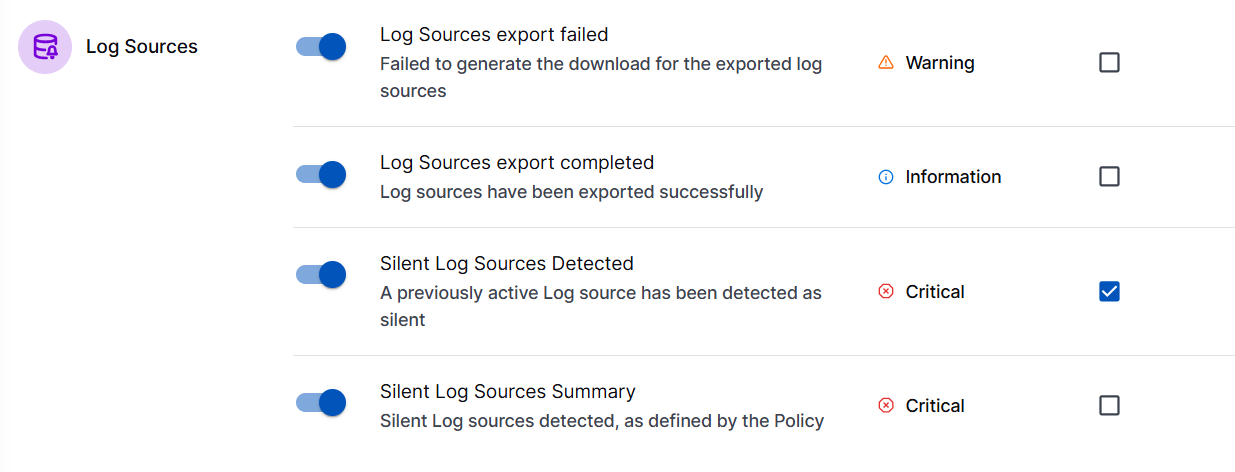
When you configure Global Notification options by navigating to Settings > Global Notifications > Delivery, ensure that the notifications for Silent Log Sources Detected and Silent Log Sources Summary are enabled. Enable or disable notification individually at the policy level.
Use the Global Notifications option to enable of disable receiving webhook notifications for Silent Log Sources Detected at subscription level and in-app notifications for Silent Log Source Summary at user level.
Silent Log Sources Detected – Enable to receive notifications for each log source, every time a log source goes silent. These webhook notifications are sent if you selected the Every time (receive all notifications) option in the log source policy.
Silent Log Source Summary – Enable to receive notifications for all associated log source policies. These in-app notifications are sent if you selected the At most once every 24 hours (Default) option in the log source policy.