- What is Exabeam?
- Welcome to the Advanced Analytics Homepage
- Get to Know a User Profile
- 1 General Information
- 2 Data Insights
- 3 Active Incident(s)
- 4 User Risk Trend
- 5 Risk Reasons
- Get to Know the User Timeline Page
- Examine Events by Category with the User Session Summary
- About the User Session Timeline
- Filter User Timelines
- View Activity Summary on a Specific Day
- Get to Know the Daily Timeline
- View and Understand an Account Lockout Sequence
- Get to Know the Account Lockout Sequence Timeline
- Accepting a Session or Sequence
- Entity Analytics
- Get Started with the Asset Page
- Get Started With the Threat Hunter Page
- Search Histograms Using the Data Insights Page
- Monitor Exabeam Processes Using the System Health Page
- Contact Technical Support
What is Exabeam?
The Exabeam Security Management Platform provides end-to-end detection, User Event Behavioral Analytics, and SOAR.
Exabeam builds a layer of intelligence from the logs collected in an environment either through a SIEM platform or directly ingested via Syslog. Through this integration, an analyst can see the events within the attack chain to more effectively and quickly remediate the risk.
If you are a security response personnel or analyst, get started with Exabeam and learn how you can use Exabeam to investigate suspicious events.
You will understand:
How Exabeam works
Exabeam Use Cases
The pages of the Exabeam interface
For Advanced Analytics, the latest versions of the following browsers are supported:
Chrome
Internet Explorer
Firefox
Safari
Please consult the Exabeam Administration Guide for further information on installation and operation.
Exabeam’s Role
Get to Know Exabeam Terminology
The following terms are frequently used in the Exabeam UI.
An analyst is the operator of Exabeam.
An incident is an unusual occurrence that may indicate a threat to an organization's security and which a security analyst is investigating.
Users are people that Exabeam is monitoring in an organization. These users can be employees, contractors, partners, service accounts, and so on.
Events are the constituents of a session, sequence, or feed. For example, logging onto a VPN is an event, and logging onto a computer is an event. Although events constitute a logical session, it is also true that Exabeam links each event to a user or asset.
Event details contribute to the baseline and are monitored for anomalies during regular operation. For example, user activities can result in a user being marked as notable or an asset becoming compromised.
Assets are computer devices such as servers, workstations, and printers.
User Session represents all the events that Exabeam attributes to an individual user in a timeframe (after 5 hours of user inactivity or 24 hours of maximum duration, Exabeam closes the user session). Typically, user sessions are one day of activity, but there can be multiple user sessions in a day. Exabeam collects event logs that relate to the user’s assets and activities and defines these as a logical user session. A user session is a logical container that Exabeam creates and, therefore, is not a session the way an analyst may typically think of a session.
Asset Session represents all the events that Exabeam attributes to an individual asset in a timeframe. Asset Sessions are similar to User Sessions in that they are a logical container of event logs related to the asset's activities, however an Asset Session lasts for one 24-hour period, from midnight UTC to midnight UTC.
Daily Feeds are similar to User Sessions in that they are a logical container of event logs. However, unlike user sessions they represent a single day. They are high-volume feeds that are processed outside of a user session but their risk scores will be added to a user’s session score. Examples of daily feeds are proxy logs, endpoint logs, and DHCP logs.
Lockout Sequence refers to all of the account lockout related events that Exabeam attributes to an individual user in a timeframe. A sequence begins with an account change, a failed logon event, or a lockout event and all additional account lockout related events are added to the sequence until a period of inactivity has been reached. The sequence is analyzed and marked as risky if the activities in the sequence are identified as anomalous and cross a risk threshold.
A Queue is a group of users assigned to incidents. This is based on how your organization’s resources are arranged, such as analyst groups designated in Tier1, Tier2, etc. Queues contain Incidents and analysts are Queue Members who are notified when new Incidents are added to the Queue.
Get to Know Exabeam Use Cases
To make the best use of Exabeam, it's helpful to understand the out-of-the-box use cases we support.
External Compromise: Attackers gain entry into an environment by compromising the credentials of valid users. They move laterally within the environment looking for sensitive information. Compromised credentials present a significant threat to organizations due to the difficulty of differentiating between normal and risky behavior. Using machine learning and data analysis, Exabeam assembles all activities from a variety of log sources into an easy-to-understand time-line for each user within an organization and assigns a risk score to their behavior. An example includes an attacker who uses a valid credential to create a new account and then uses that account to access many assets, contacts a domain that is generated by a Domain Generation Algorithm (DGA) and ex-filtrates critical database records to a C&C server.
Insider Threat: Exabeam helps in identifying rogue insiders within the environment. It’s easy for these attacks to go undetected because insiders in the environment know where the sensitive data is and they will not trigger the same types of anomalies as an external attacker taking control of an environment using stolen credentials. Exabeam also incorporates log sources from Cloud Applications into its analytics engine and detects insider threats within the data center and on the cloud. Customers want to analyze the physical presence of their employees along with their IT activities. Exabeam will stitch physical presence into user sessions and identify anomalies across them. For example, points would be added to a session the first time a user accesses a building. This allows for cross-referencing of IT behaviors with physical behaviors for a higher level of visibility. Other scenarios include, data access outside of the job scope or a privileged insider accessing compensation records of an employee.
Data Loss Prevention (DLP): DLP solutions are widely-deployed as a means of finding sensitive data and detecting the movement of that data to the outside world. Exabeam brings unique UBA capabilities to DLP by ingesting and analyzing non-authentication events and identifying anomalous behavior around data exfiltration. Many corporate PCs contain endpoint security software that logs the use of thumb drives in USB ports. Exabeam can use this log data to identify risky operations such as the first time a user saves files to a USB drive or when a user is copying files that are outside of that user’s normal behavior. Other scenarios would be: an employee taking high net-worth client information when they leave; a terminated employee badging into a building; an employee accessing a CEO mailbox.
Alert Prioritization: As IT environments grow in scale and complexity, Security Operations teams often struggle to keep up with the resulting increase of monitoring alerts. Since alerts are a critical early warning system, finding a way to reduce false positives and prioritize alerts becomes a critical success factor. Exabeam’s machine learning technology addresses rapidly growing data volumes by automatically identifying anything that is amiss without the time and labor required to configure and maintain alert rules or thresholds. We take alerts from other security vendors, such as FireEye or Palo Alto Networks and Exabeam’s Stateful User Tracking associates an alert from any of the third party products into a user session and is able to present the activities of the user before and after the alert.
Another example would be alerts related to an organization’s Account Lockout policy. While they serve an important security purpose, they also place a strain on already short-staffed IT teams. By analyzing the events around account lockouts and presenting the information in a timeline, Exabeam accelerates efficiency and reduces the resources consumed by these investigations.
How Exabeam Works
Exabeam assigns a risk score to users and their IT environment sessions by combining user behavior intelligence and fact-based information. In a single session, Exabeam may report risk related to abnormal access to an asset, a security alert received from a 3rd party system, a new user being created from a new network location, and changes to the access privilege of the user. Asset criticality and threat intelligence information can also be factored into the risk analysis.
The following major components work together to produce a risk score:
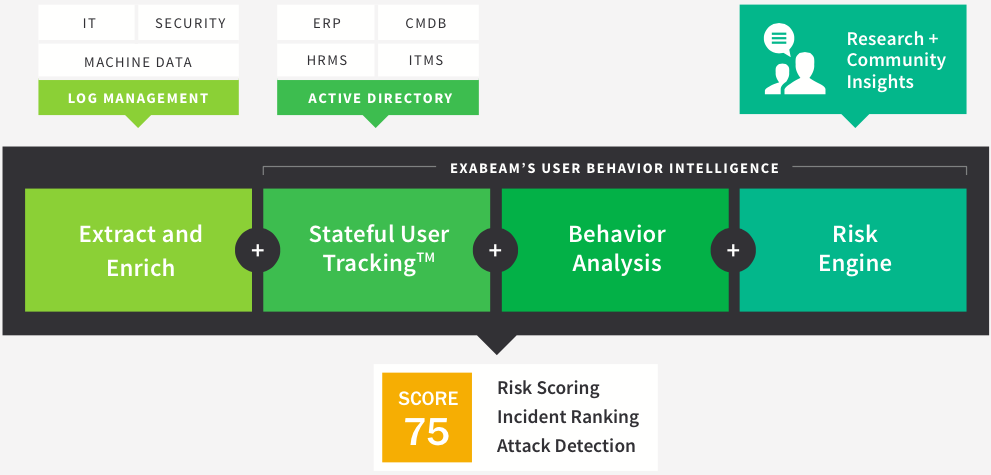 |
Extract and Enrich – Exabeam draws from the organization’s log management system and enriches the logs with identity, asset, and network information. For example, Exabeam links to Microsoft Active Directory to discover the department and roles of the users in the organization. Exabeam also uses machine learning to categorize users and assets to further enrich the contextual information. For example, Exabeam can detect certain users as service accounts based on their behavior.
Stateful User Tracking – While reading logs, Exabeam follows user sessions by tracking the state of the users’ presence within the IT environment. Sessions represent the activities performed by the users from the moment they enter the environment until they log off or remain idle for a period.
Behavior Analysis – Behavior Analysis is where Exabeam detects anomalies. Exabeam continuously maintains a baseline of normal behaviors for each user in the environment and each group, e.g. Department. New activities are then compared to the baseline and reported as anomalies if they are deemed inconsistent.
Risk Engine – The Risk Engine combines data science and security expertise to quantify the risk of the anomalies. It also adds risk according to fact-based information, such as privilege levels, security alerts or threat intelligence and produces a risk score.
Build a Baseline for Each User and Asset Using Training
To build a baseline, Exabeam extensively profiles the people, asset usage, and sessions (Exabeam’s word for profiling or base-lining is training). In a typical deployment, Exabeam starts by examining 90 days of an organization’s logs. After the initial baseline analysis is done, Exabeam starts scoring the sessions. Note the following:
In most cases during initial deployment, Exabeam uses the data from the previous 30 days as if it were scoring during that time. The purpose is to analyze a month of data and paint a meaningful picture for the analyst without waiting 30 days to create a picture.
Training does not stop. Exabeam continuously adjusts the profiles as the users and the IT environment changes.
When Exabeam categorizes behavior as anomalous, it does so based on rules and models that it applies to users, assets, peer groups, and the organization as a whole. In the case of an employee who exhibits suspicious behavior or a security device that posts an alert, Exabeam will display events that are not normal for that user or asset. However we don't display only abnormal events. We also display normal events so that the Analyst can have the full picture and can understand what led to the anomalous event. For example, behind the suspicious behavior could be VPN requests from countries never before seen or remote logons to assets or network zones that never have been accessed.
Confidence in Assessing Events
Before evaluating a specific event, Exabeam must have confidence in the basis of its evaluation of that event. In Exabeam’s case, this basis means enough quantity and consistency of data for each user and their attributes. If Exabeam lacks enough data for a specific type of event, it does not evaluate the rule for that event even as it evaluates other rules during the session. However, note that the confidence factor is not taken into account for the first time a rule is triggered.
The confidence in each user’s profile is built during the initial baseline development as well as on an ongoing basis as new events arrive. In contrast, some behaviors might require Exabeam to take more time to establish confidence. For example, if a user’s job involves irregular foreign travel, establishing confidence in a profile of VPN sessions from foreign countries takes longer.
An example of profiling that might never lead to confidence in one area of behavior is a behavior that changes every day. The only predictable thing about this behavior is that it changes daily. For example, if an ISP starts a policy of assigning a different IP address every day, Exabeam cannot establish a histogram that applies to that behavior. An organization can accept this because if the new IP address were part of an attack, many other rules would be triggered. Put another way, a new IP address every day does not automatically indicate a threat. The total score for all anomalies during a session indicates attacks.
Analysts also have an option for choosing certain behaviors to accept, as the Sessions chapter describes. After sufficient examination of a session, an analyst can manually add the session’s events to a user’s profile so that those events stop triggering the applicable rules.
Role-Based Access Control
Access to configuration, data views, actions, and analysis in Advanced Analytics is restricted based on user-assigned roles. Roles are functional groups you configure and adjust based on your organization’s task structure.
For example, you may have two tiers of security analysts along with a group of auditors who all need access to Advanced Analytics. The three groups do not have equal level of privileges to view, run tasks, or adjust system configurations. You may have roles named SA1, SA2, and Auditor. While users in the SA1 and SA2 roles are allowed to view notable users, those in the Auditor role may not. A SA1 user may make a copy of URLs from a suspicious session and sends it them to a user in SA2 who can see the information in clear text. Another SA1 user will not be able to see that same information if the role excludes viewing data that is masked due to privacy policies.
Users are assigned a role in their profile. More than one role can be assigned, but be aware of tasks with conflicting privileges. In the case of conflicting privileges, we combine the privileges and give all explicitly allowed permissions between them.
When a user tries to access a view, menu, or execute a task outside the designated role, an error message is presented advising the user does not have sufficient privileges.
For information on how to configure access restrictions, see Universal Role-Based Access in the Advanced Analytics Administration Guide.
Mask Data in the Advanced Analytics UI
Exabeam supports Data Masking to meet the data privacy directives of enterprise organizations.
It ensures that personal data cannot be read, copied, modified, or removed without authorization during processing or use. With data masking enabled the only SOC analysts that will be able to see clear text PII will be those administrators that are assigned to the Data Privacy Officer role. All other administrators will see disguised information:
Data Masking can be enabled via a configurable setting. It is turned off by default. Please see the Administration Guide for more information on how to enable the feature.
Data Masking Fields
The data masking fields are individually configurable. For example, the administrator is able to decide to only mask username, photo, and contact information. In such a case, all the other fields are available in an unmasked form for any analyst. The user name, photo, and contact information can only be seen in a clear text form for those users whose roles have the "View clear text PII data" permission.
See the section Configure Data Masking Fields in the Administration Guide for more details.
Obfuscate PII When Exporting Logs
When exporting logs from the session timeline or Threat Hunter, all fields that are configured to be obfuscated are shown in a masked form when the logs are downloaded.
Mask Data in Search & Threat Hunter Functionality
The Search & Threat Hunter functionality work with data masking enabled. An analyst is able to provide a masked value and find matching results. For example, if a User Name is masked as DondU8 then any search for DondU8 will return results for that same user, with all configured fields masked.
Unmask Data with Clear-Text Permissions
The session URLs of masked users can be sent to administrators with clear-text permissions. For example, a Tier 1 Analyst (a data masked role) views a suspicious user, then copies the URL of the specific session for that user and sends it to a Data Privacy Officer (a clear-text role). When opening the URL, the Data Privacy Officer is able to view that user's information in clear-text.
