- Exabeam Data Lake Architecture Overview
- Exabeam Product Deployment in On-premises or Virtual Environments
- Administrator Operations
- User Management
- Universal Role-Based Access
- Legacy Role-Based Access Control
- Exabeam Data Lake Object-based Access Control
- Exabeam Data Lake Secured Resources Overview
- Audit Log Management in Data Lake
- Set Up LDAP Server
- Azure AD Context Enrichment
- Set Up LDAP Authentication
- User Password Policies
- User Engagement Analytics Policy
- Exabeam Threat Intelligence Service
- Threat Intelligence Service Prerequisites
- View Threat Intelligence Feeds
- Threat Intelligence Context Tables
- View Threat Intelligence Context Tables
- Assign a Threat Intelligence Feed to a New Context Table
- Create a New Context Table from a Threat Intelligence Feed
- Using Threat Intelligence Service with Data Lake
- Check ExaCloud Connector Service Health Status
- Index Management
- Parser Management
- Forwarding to Other Destinations
- Syslog Forwarding Management in Exabeam Data Lake
- Syslog Forwarding Destinations
- Configure Log Forwarding Rate
- How to Forward Syslog to Exabeam Advanced Analytics from Exabeam Data Lake
- How to Forward Syslog from Exabeam Data Lake to Non-Exabeam External Destinations
- Exabeam Data Lake Selective Forwarding using Conditions
- How to Configure Exabeam Data Lake Log Destinations for Correlation Rule Outcomes
- Forward Exabeam Data Lake Incident to Exabeam Incident Responder
- Syslog Forwarding Management in Exabeam Data Lake
- Cluster Operations
- Cross-cluster Search in Exabeam Data Lake
- Prerequisites for Exabeam Data Lake Cross-cluster Search
- Remote Cluster Management for Exabeam Data Lake Cross-cluster Search
- Register a Remote Cluster in Exabeam Data Lake for Cross-cluster Search
- Exabeam Data Lake Cross-cluster Health Monitoring and Handling
- How to Enable/Disable/Delete Exabeam Data Lake Remote Clusters for Cross-cluster Search
- Exabeam Data Lake Remote Cluster Data Access Permissions for Cross-cluster Search
- Exabeam Cloud Telemetry Service
- System Health Page
- A. Technical Support Information
- B. List of Exabeam Services
- C. Network Ports
- D. Supported Browsers
Cluster Operations
Hardware and Virtual Deployments Only
Configuring Exabeam Directory Services Data Retention in Exabeam Data Lake
Hardware and Virtual Deployments Only
Note
To configure this feature, please contact your Exabeam technical representative.
By default, the retention policy for Exabeam Directory Services (EDS) data is 30 days. Therefore, LDIF (LDAP Data Interchange Format) files collected daily from the LDAP (Lightweight Directory Access Protocol) server(s) are retained for 30 days.
In general, the 30-day default period is suitable for the average customer and does not affect product behavior performance. However, some customers may need to reprocess older events, which may include events related to users or assets that are no longer active, and won’t be found in the current context tables. In this specific case, the events will be reprocessed but might not be able to leverage the historical contextual information.
To configure the EDS data retention period:
Access the EDS custom application.conf file:
/opt/exabeam/config/common/eds/custom/application.confAdd the value here, where
Nis the total number of retention days:EDS.Defaults.RetentionPeriod = N daysStop, and then start EDS again:
eds-stop eds-start
Display a Custom Login Message
You can create and display a custom login message for your users. The message is displayed to all users before they can proceed to login.
To display a custom login message:
On a web browser, log in to your Exabeam web console using an account with administrator privileges.
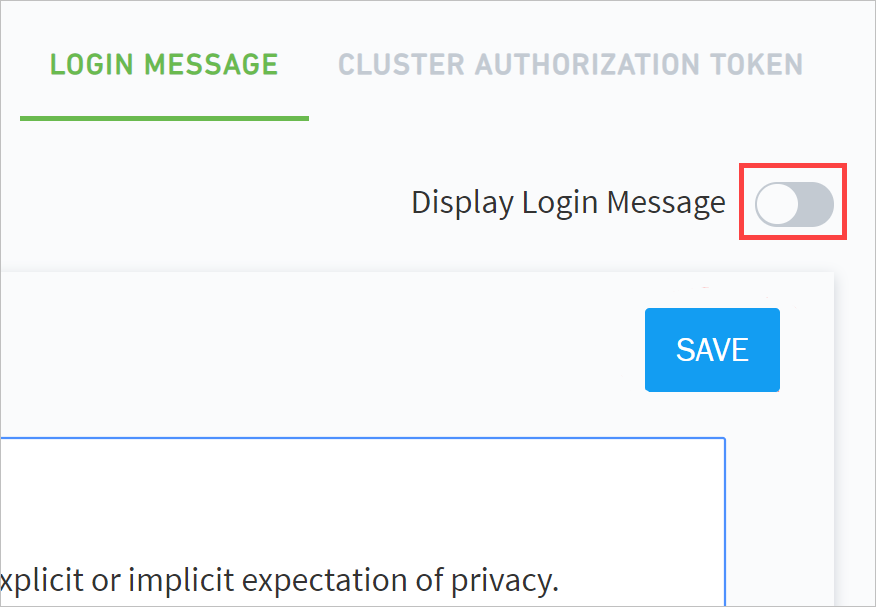
Navigate to Settings > Admin Operations > Login Message.
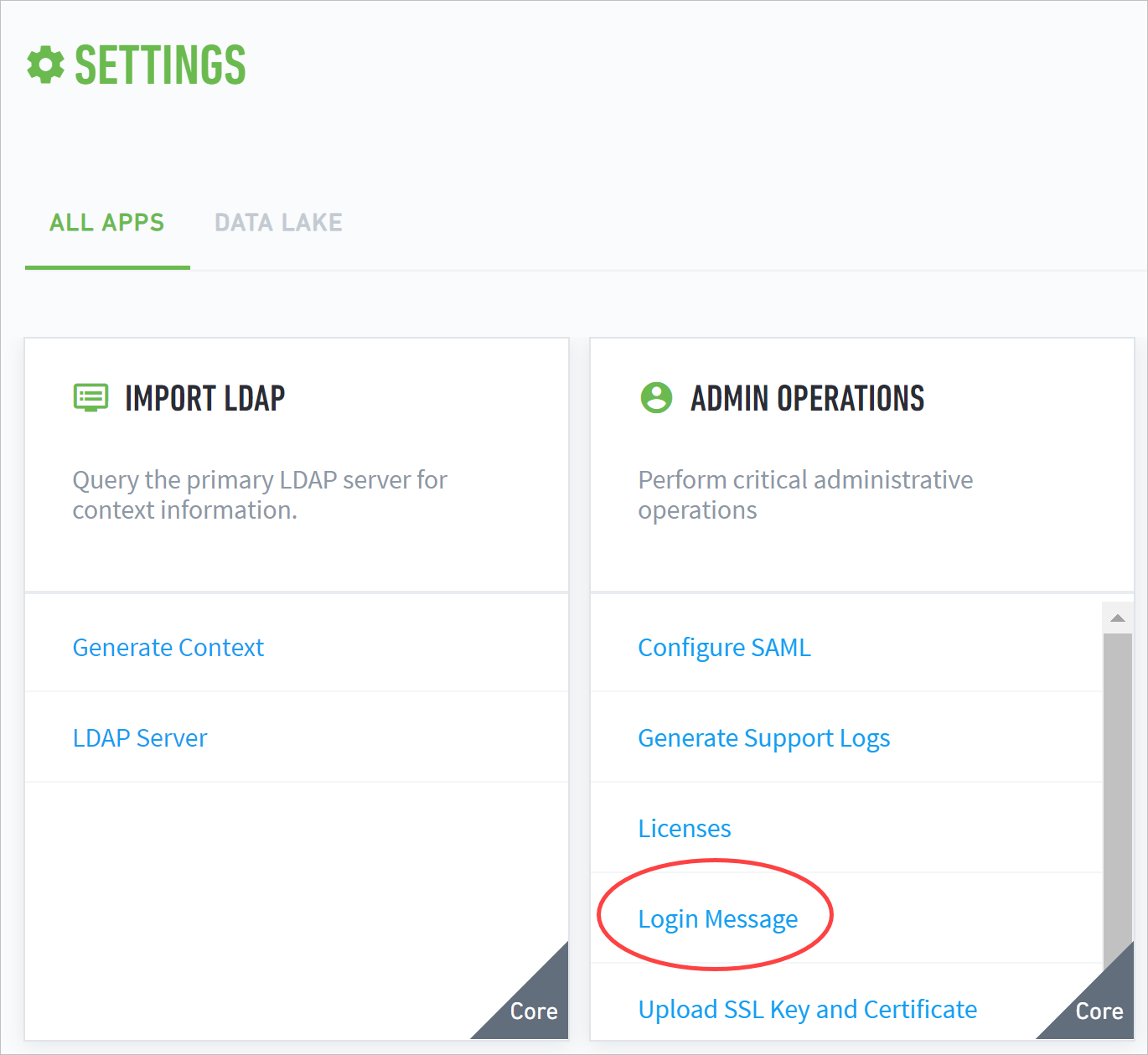
Click EDIT.
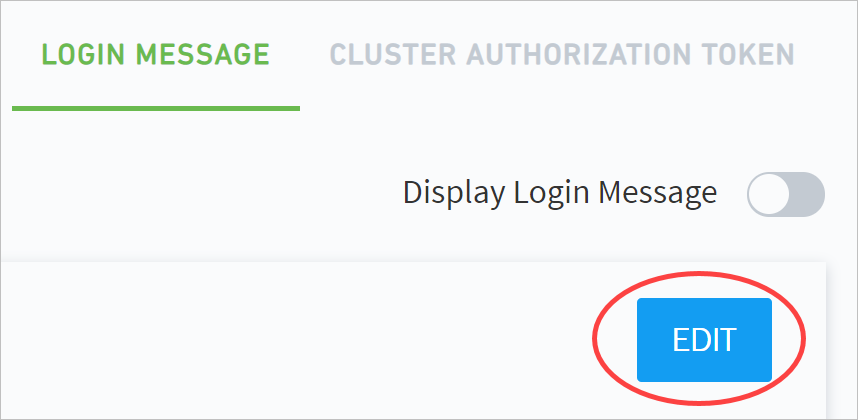
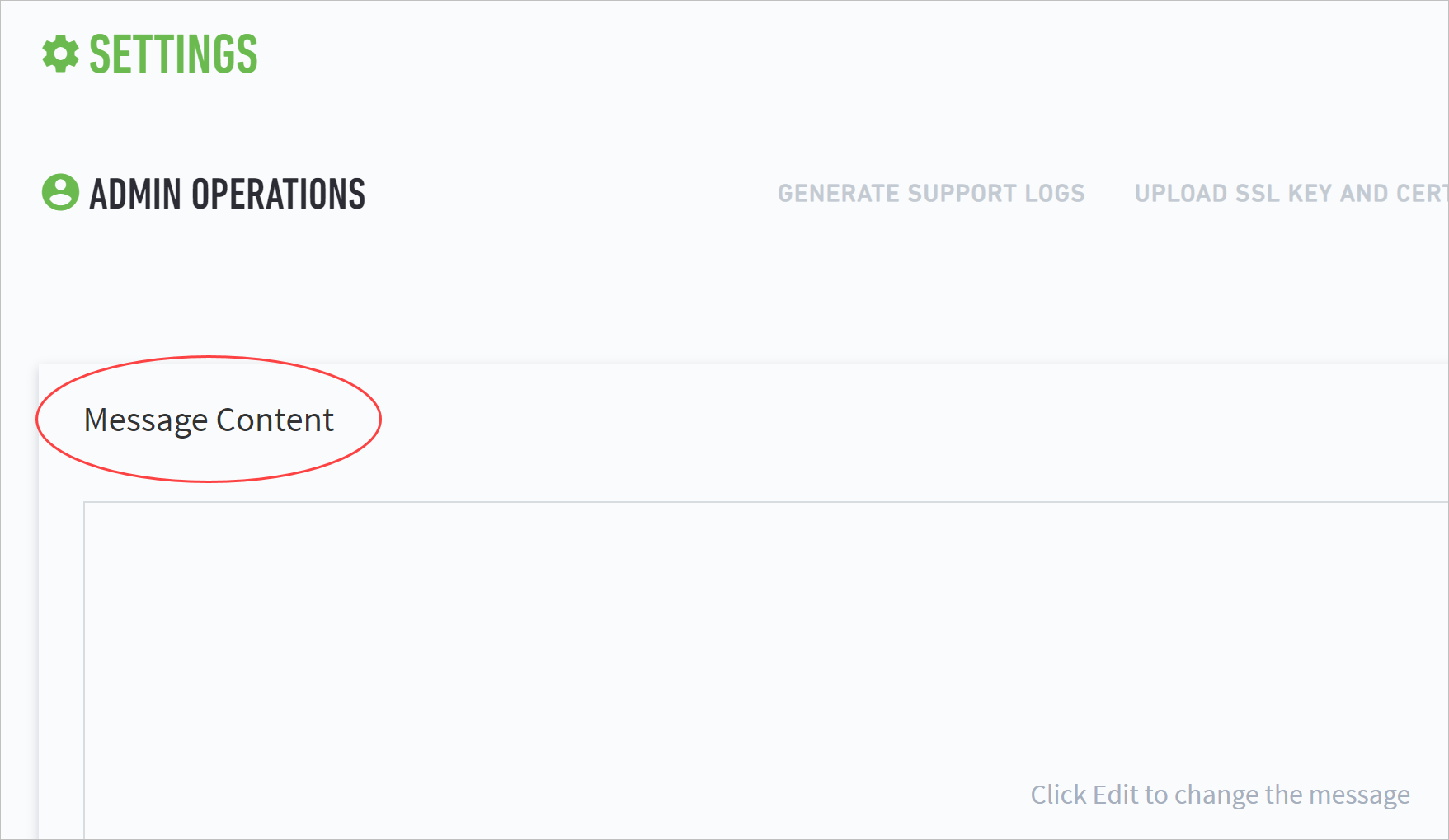
Enter a login message in Message Content.
Note
The message content has no character limit and must follow UTF-8 format. It supports empty lines between text. However, it does not support special print types, links, or images.
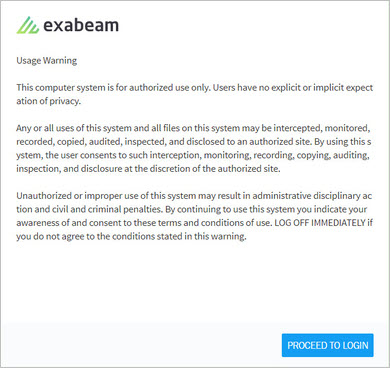
A common type of message is a warning message. The following example is a sample message:
Usage Warning
This computer system is for authorized use only. Users have no explicit or implicit expectation of privacy.
Any or all uses of this system and all files on this system may be intercepted, monitored, recorded, copied, audited, inspected, and disclosed to an authorized site. By using this system, the user consents to such interception, monitoring, recording, copying, auditing, inspection, and disclosure at the discretion of the authorized site.
Unauthorized or improper use of this system may result in administrative disciplinary action and civil and criminal penalties. By continuing to use this system you indicate your awareness of and consent to these terms and conditions of use. LOG OFF IMMEDIATELY if you do not agree to the conditions stated in this warning.
Note
This sample warning message is intended to be used only as an example. Do not use this message in your deployment.
Click SAVE.
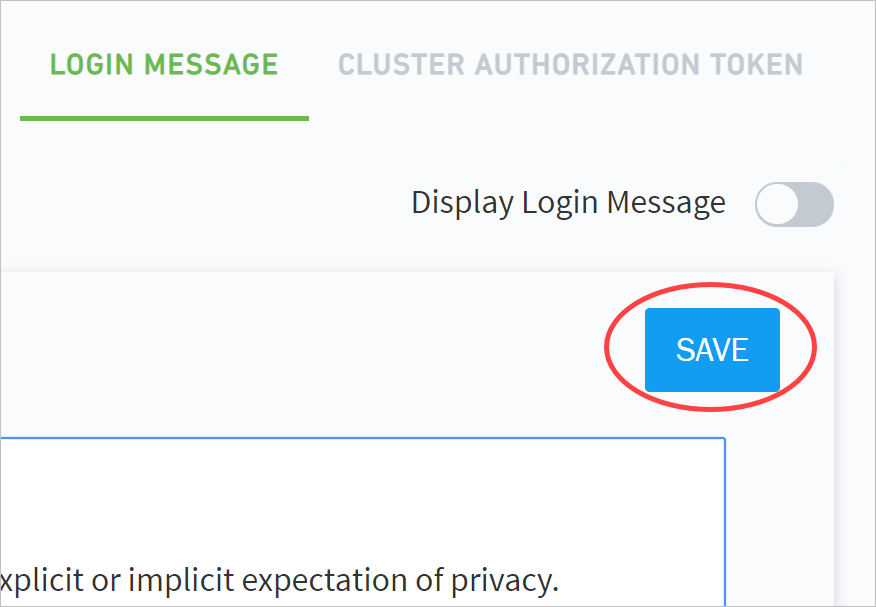
Click the Display Login Message toggle to enable the message.
Note
You can hide your message at any time without deleting it by disabling the message content.
Your custom login message is now shared with all users before they proceed to the login screen.
 |
Exabeam Cluster Authentication Token
The cluster authentication token is used to verify identities between clusters that have been deployed in phases as well as HTTP-based log collectors. Each peer cluster in a query pool must have its own token. You can set expiration dates during token creation or manually revoke tokens at any time.
Note
This operation is not supported for Data Lake versions i40.2 through i40.5. For i40.6 and higher, please see the Contents of the exabeam-API-docs.zip file section of the following document: Exabeam Saas API Documentation.
To generate a token:
Go to Settings > Core > Admin Operations > Cluster Authentication Token.
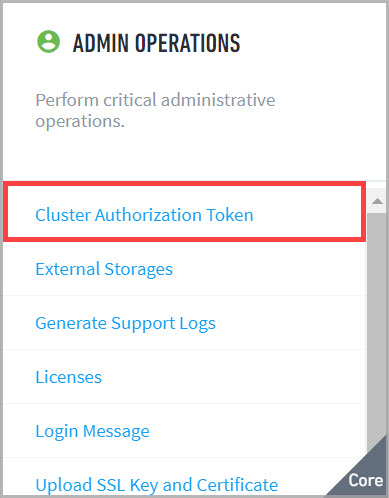
The Cluster Authorization Token page appears.
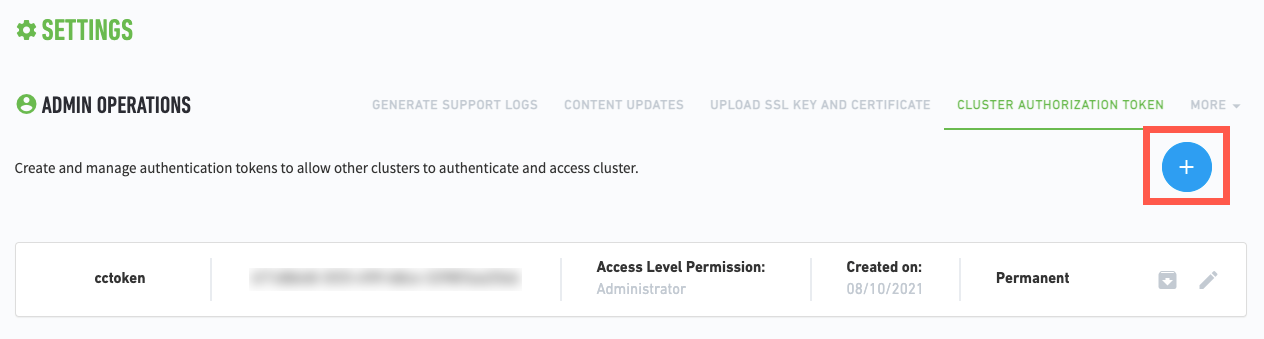
Click
 .
.The Setup Token dialog box appears.
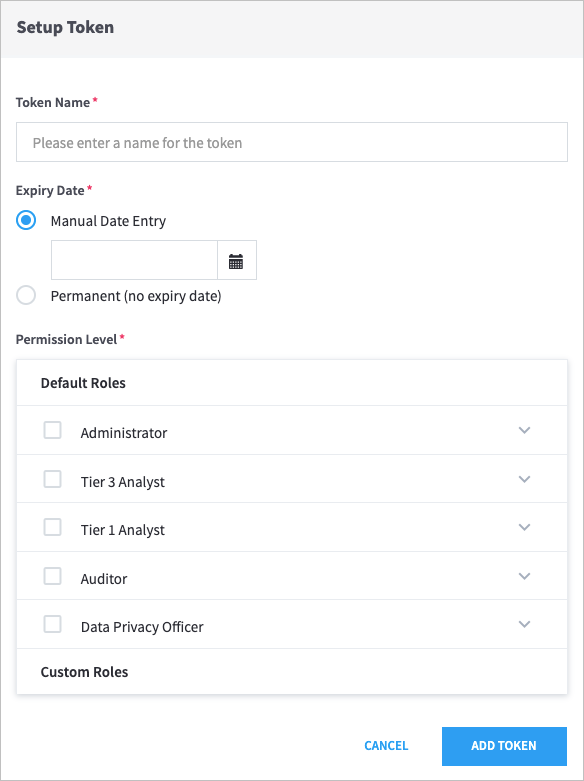
Enter a Token Name, and then select an Expiry Date.
Important
Token names can contain only letters, numbers, and spaces.
Select the Default Roles for the token.
Click Add Token.
Use this generated file to allow your API(s) to authenticate by token. Ensure that your API uses
ExaAuthTokenin its requests. For curl clients, the request structure resembles the following:curl -H "ExaAuthToken:<generated_token>" https://<external_host>:<api_port>/<api_request_path>
