- Get Started with Correlation Rules
- Create Correlation Rules
- Manage Correlation Rules
- Find Correlation Rules
- Share Correlation Rules
- View Correlation Rules Metrics
Detect Absent Events or Fields Using Correlation Rules
Build sequences that detect a missing event or field that was previously present.
You may want to detect an absent event or field to identify if you've stopped receiving a specific log and diagnose issues with collecting or ingesting data.
You define the logic to detect an absent event or field in the correlation rule sequence when you create or edit a rule.
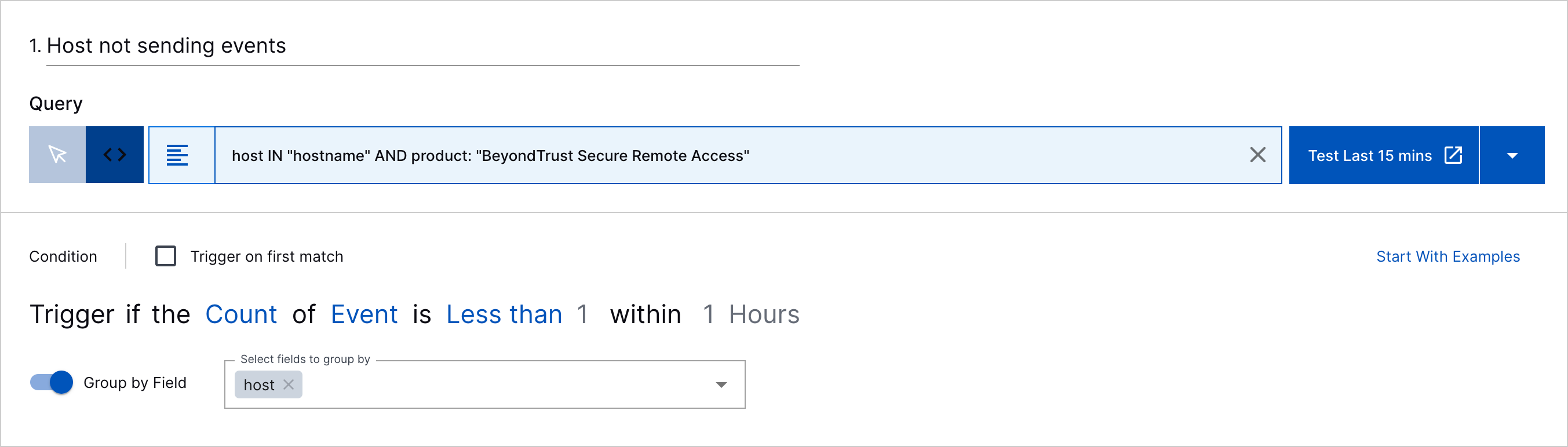
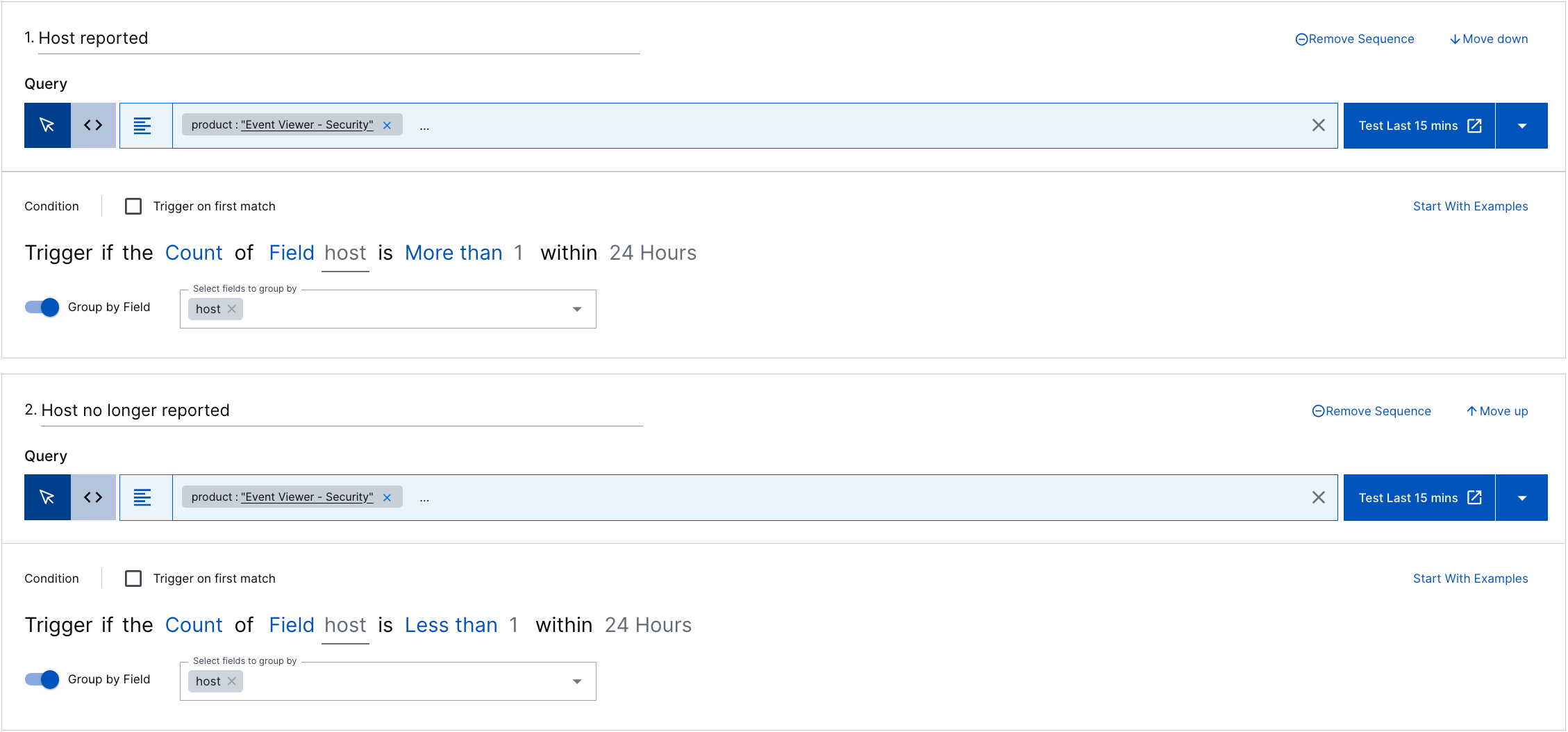
In most cases, you create two ordered sequences: the first sequence identifies the events or fields of interest; the second sequence defines the logic for detecting those absent events or fields. For the first sequence, query for events of interest, then define the condition statement as Trigger if the Count of an event or field is More than 1 within a certain period. For the second sequence, enter the same query as the first sequence, then define the condition statement as Trigger if the Count of an event or field is Less than 1 within the same period used in the first sequence. For example, to determine if you've stopped receiving host information from Event Viewer - Security events, create the following correlation rule:
If you use a context table in your query to identify events of interest, you only need to create one sequence where the the condition statement is Trigger if the Count of an event or field is less than 1 within a specified period. For example, to detect if you've stopped receiving BeyondTrust Secure Remote Access events whose host field value appears in the hostname context table, create the following correlation rule: