- Get Started with Correlation Rules
- Create Correlation Rules
- Manage Correlation Rules
- Find Correlation Rules
- Share Correlation Rules
- View Correlation Rules Metrics
Create a Correlation Rule from a Template
If you don't want to create a correlation rule from scratch, use a pre-built template. You can also create a correlation rule using a Search query as a starting point.
1. Select a Template
On the Exabeam Template tab, click Use for the template you're using.
2. Edit a Sequence or Create Additional Sequences
To create a sequence, first search for events on which your rule triggers. Searching for events is similar to Search. You can choose to build a search or type one out, you use the same syntax when typing a search, and you can select recent and saved searches. After you define events of interest, you define the conditions that the events must meet.
If the rule triggers on a set of related events, define multiple sequences. The condition of all sequences must be satisfied for the rule to trigger. For example, to detect a brute force attempt, define the first sequence as a certain number of failed log-on events from an external IP address within five seconds and the second sequence as a successful log-on event from the same external IP address within 30 minutes. Sequences can be ordered, so sequences and their conditions must be satisfied in a specific order for the rule to trigger; or unordered, so all sequences and their conditions can be satisfied in any order for the rule to trigger.
When you create a rule from a template, the first sequence is predefined. To customize the rule, edit the sequence or add additional sequences.
(Optional) In Sequence name, name the sequence.
To define the events that trigger the correlation rule, search for events of interest:
Build a query.
Enter a query.
To select a recent or saved query in Search, click
 , then select a query.
, then select a query.You can only see saved queries marked private. You can't see public saved query.
To see events that match your query and were created in in the last 15 minutes in Search, click Test Last 15 mins. If you modify your query in Search, you're prompted to update your query with those changes when you return to Correlation Rules. To retain the changes you made in Search, click Update Query.
Under Condition, define conditions that must be satisfied for the rule to trigger.
If the rule triggers with the first event that matches the query you defined, select Trigger on first match. You must select this if you used a context table lookup to build your query.
To define a condition, click a term in the condition statement, then select another term. The available terms and fields change dynamically.
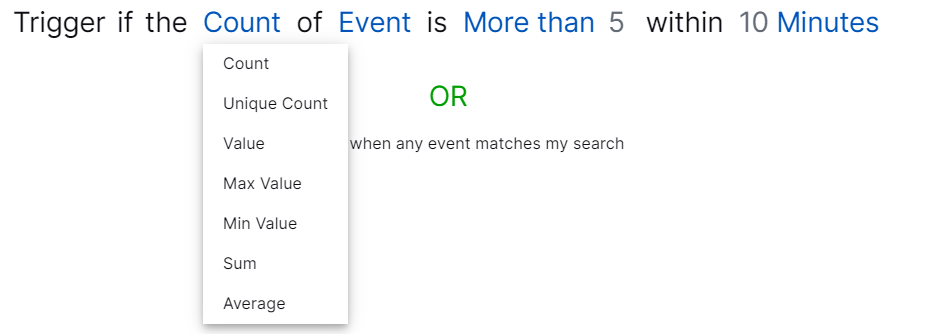
As you define the condition, Correlation Rules validates the condition statement. If a term turns red, the condition statement is invalid and you can't continue. Click the invalid term, then select another option.
The Count and Unique Count terms are case insensitive; for example, for Event A with
dest_hosthost123 and Event B withdest_hostHost123, the count is two.To select from a list of common conditions, click Start With Examples. For a condition, click Select, then click Apply.
To consolidate the query results by specific fields into subsets of events and evaluate the condition against each subset, toggle Group by Field on, then select a field. You can select up to five fields.
To define additional sequences, click + New Sequence.
(Optional) After you define multiple sequences, you can remove them, order them, define which field values all events returned across sequences should share for the rule to trigger, and specify whether the sequences are ordered or unordered:
To remove a sequence, click Remove Sequence.
If your sequences are ordered and a sequence should be satisfied before other sequences, click Move Up.
If your sequences are ordered and a sequence should be satisfied after other sequences, click Move Down.
If events returned by all sequences should share the same field value for the rule to trigger, under Common Properties > Select fields to group by, select the field. For example, if the rule triggers when all events returned across sequences contain the same source IP address, select src_ip. You can select up to 10 fields.
If you selected a field in the Group by Field functionality in an individual sequence and the field value is shared across sequences, it automatically appears in the list.
To specify that the sequences be satisfied in a specific order for the rule to trigger, under Common Properties > Exabeam Sequences, select In Order.
To specify that the sequences can be satisfied in any order for the rule to trigger, under Common Properties > Exabeam Sequences, select Unordered.
If you defined multiple sequences, under Overall Rule Threshold, you must define a period in which all sequences must be evaluated for the rule to trigger.
If the sequences are ordered, the value should be more than the sum of time taken for each sequence to evaluate its condition. For example, if your first sequence is defined as Trigger if the Count of Event is More than 5 in the last 3 Minutes and your second sequence is defined as Trigger if the Count of Events is More than 5 in the last 5 Minutes , your overall rule threshold must be more than eight minutes.
If the sequences are unordered, the value should be at least the maximum time taken across sequences to evaluate their conditions. For example, if your first sequence is defined as Trigger if the Count of Event is More than 5 in the last 3 Minutes and your second sequence is defined as Trigger if the Count of Events is More Than 5 in the last 5 Minutes, your overall rule threshold must be five minutes or more.
3. (Optional) Schedule correlation rule trigger
Under Trigger Schedules, schedule a correlation rule to trigger daily, weekly, monthly, or during a custom time period with specific start and end times.
You can create multiple schedules. After you create a schedule, you can edit or delete the schedule.
When you're done creating and managing schedules, click Next.
Create a schedule
Under Trigger Schedules, click + Add.
Under Recurrences, select the schedule on which the correlation rule triggers:
Daily – The correlation rule triggers every day.
Weekly – The correlation rule triggers on the same days of the week, every week. Under Every, select the days of the week on which the correlation rule triggers.
Monthly – The correlation rule triggers on the same day of the month, every month. Under Day, select the days of the month on which the correlation rule triggers.
Custom – The correlation rule triggers during a specific period you define using the From and To fields.
Under From, select the time from when the correlation rule is allowed to start triggering. If you selected Custom under Recurrences, you must also specify a day of the week.
Under To, select the time at when the correlation rule stops triggering. If you selected Custom under Recurrences, you must also specify a day of the week.
Click Add.
Edit a schedule
For an existing schedule, click the More menu
 , then select Edit.
, then select Edit.Make your changes to the schedule.
Click Add.
Delete a schedule
For an existing schedule, click the More menu  , then select Delete.
, then select Delete.
4. (Optional) Define outcomes
Specify what happens when the rule triggers. There are four possible outcomes:
Threat Center creates an alert.
Threat Center creates a case or Case Manager creates an incident.
Correlation Rules sends an email notification. If you have an Exabeam Security Log Management license, this is the only possible outcome.
Correlation Rules sends information to a webhook.
Whether or not you define an outcome, an event is automatically created every time the rule triggers. If the rule triggers and isn't in test mode, the activity type of the event is rule-trigger. If the rule triggers in test mode, the activity type of the event is rule-trigger-test.
If you have Threat Center, Threat Center also automatically creates an alert every time the rule triggers, depending on whether the rule is in test mode. If the rule triggers and isn't in test mode, Threat Center creates an alert. If the rule triggers in test mode, Threat Center doesn't create an alert.
For Advanced Analytics to generate Smart Timeline alerts from a triggered correlation rule, two conditions must be met:
The event that triggered the rule must contain
user,src_host, anddest_hostfields and at least one must have a value.At least one sequence in the rule must use the Group by Field functionality with
user,src_host, ordest_hostfields and these fields must have a value.
Designate Threat Center Alert as an Outcome
To create an alert in Threat Center, click Next. You don't specify an outcome. If the correlation rule triggers and isn't in test mode, an alert containing the correlation rule detection is automatically created in Threat Center.
Designate Threat Center Case or Case Manager Incident as an Outcome
Depending on your license, Threat Center creates a case or Case Manager creates an incident.
If you're designating a Threat Center case as an outcome, ensure you've enabled the Create Correlation Case pre-built Automation Management playbooks. The Create Correlation Case pre-built playbooks must be enabled for Threat Center to create a case when the correlation rule triggers.
Select Create a Case.
Enter a case description.
Click Next.
Designate Email Notification as an Outcome
Notify people in your organization that the rule was triggered. If you have a Exabeam Security Log Management license, this is the only possible outcome. The notification is sent from the email address [email protected].
Select Send an Email.
Enter information about the email:
In Recipients, enter the recipients' email addresses.
In Subject, enter the email subject.
In Description, enter the email content.
To send the top 1000 associated events as an email attachment, select Attach events as CSV (limit 1,000).
Click Next.
Designate Webhook as an Outcome
Ensure that you've added the webhook in New-Scale Security Operations Platform settings.
Select Send to Webhook.
From the list, select up to three Webhooks. If there are no Webhooks defined in your system or the Webhook you want to use is not in the list, click Add a new webhook in settings and add a Webhook.
Click Next.
5. Finalize correlation rule details
Enter information about the rule:
Rule Name – Enter a rule name.
(Optional) Rule Description – Describe the rule. The description appears in the list of correlation rules and in the correlation rule details. By default, the template description is automatically entered.
(Optional) Use Case – From the list, select an Exabeam use case most relevant to the rule. To search for a specific use case, start typing.
(Optional) Tags – Add up to 10 tags. Select from a list of existing tags or create a new one. Tags are shared among New-Scale Security Operations Platform applications, and you can search for them in Search, Dashboards, and Threat Center using the
tags:field.(Optional) MITRE – From the list, select up to 10 MITRE ATT&CK® techniques most relevant to the rule. To search for a specific ATT&CK technique, start typing. To view more information about a technique on the MITRE organization's website, click
 .
.(Optional) Rule Severity – On the scale, select a severity: None, Low, Medium, High or Critical.
(Optional) To prevent an rule from over-triggering, suppress the rule from triggering repeatedly:
Under Triggering Suppression, toggle Suppress Repeating Trigger on, then specify how long the rule is suppressed after it's first triggered. For example, if you set the suppression period to two minutes, if a rule triggers once, then triggers again within two minutes, the second trigger is suppressed. If events satisfy the conditions of any sequence more than 500 times in five minutes or the rule triggers more than 50 times in five minutes, Correlation Rules automatically disables the rule and the rule status is changed to Stopped.
(Optional) If you used the Group by Field functionality in any sequence or designated common properties for the rule, you can suppress the rule when it triggers repeatedly on the values of a specified field. Within the suppression period, the rule triggers on the first event with a specific field value but is suppressed for all subsequent events with the same field value. For another event with the same field but a different value, the rule triggers again.
Toggle Granular Suppression on, then under Grouping Field/s, select the fields by which the rule is suppressed.
(Optional) To ensure the rule evaluates late-arriving events, delay the rule from evaluating events until all events have arrived:
In DELAY RULE EVALUATION IS SET TO 7 MINS BY DEFAULT, click Edit.
Specify how long the rule waits before evaluating events. You can specify a time between seven and 360 minutes. To determine the correct value using the Log Delay Insights dashboard, click Log Delay Dashboard.
Click Save.
(Optional) Determine if and how the rule is enabled:
To immediately enable the rule after it's created, toggle Enable Rule on.
To test the rule, enabling it but suppressing the outcomes, click Test Mode.
6. Review and save the correlation rule
Under Summary, review the sequences and outcomes you defined.
Click Save.
