Threat Detection Management Features Introduced in 2025
June 2025
The following features were introduced in Threat Detection Management in June 2025:
|
Feature |
Description |
|---|---|
|
New and Updated Correlation Rule Templates |
You can now better identify insider threats with new and updated correlation templates. New correlation rule templates include:
Updated correlation rule templates include:
|
May 2025
The following features were introduced in Threat Detection Management in May 2025:
Feature | Description |
|---|---|
Correlation Rules Insights | To make informed decisions about authoring and tuning rules, you can now view insights about your correlation rules directly in the Correlation Rules tab, including:
|
Optional Exclusion Descriptions | When you create an exclusion, the description field is now optional. |
April 2025
This release does not include new features for Threat Detection Management.
March 2025
The following features were introduced in Threat Detection Management in March 2025:
Feature | Description |
|---|---|
Incompatible Analytics Rule Disablement | To ensure the analytics engine runs normally, the analytics engine monitors rule training and evaluation processes and prevents you from enabling analytics rules that are incompatible with your data or are highly likely to generate false positive results. Under the Compatability, column, these analytics rules are marked as Incompatible. |
February 2025
The following features were introduced in Threat Detection Management in February 2025:
Feature | Description |
|---|---|
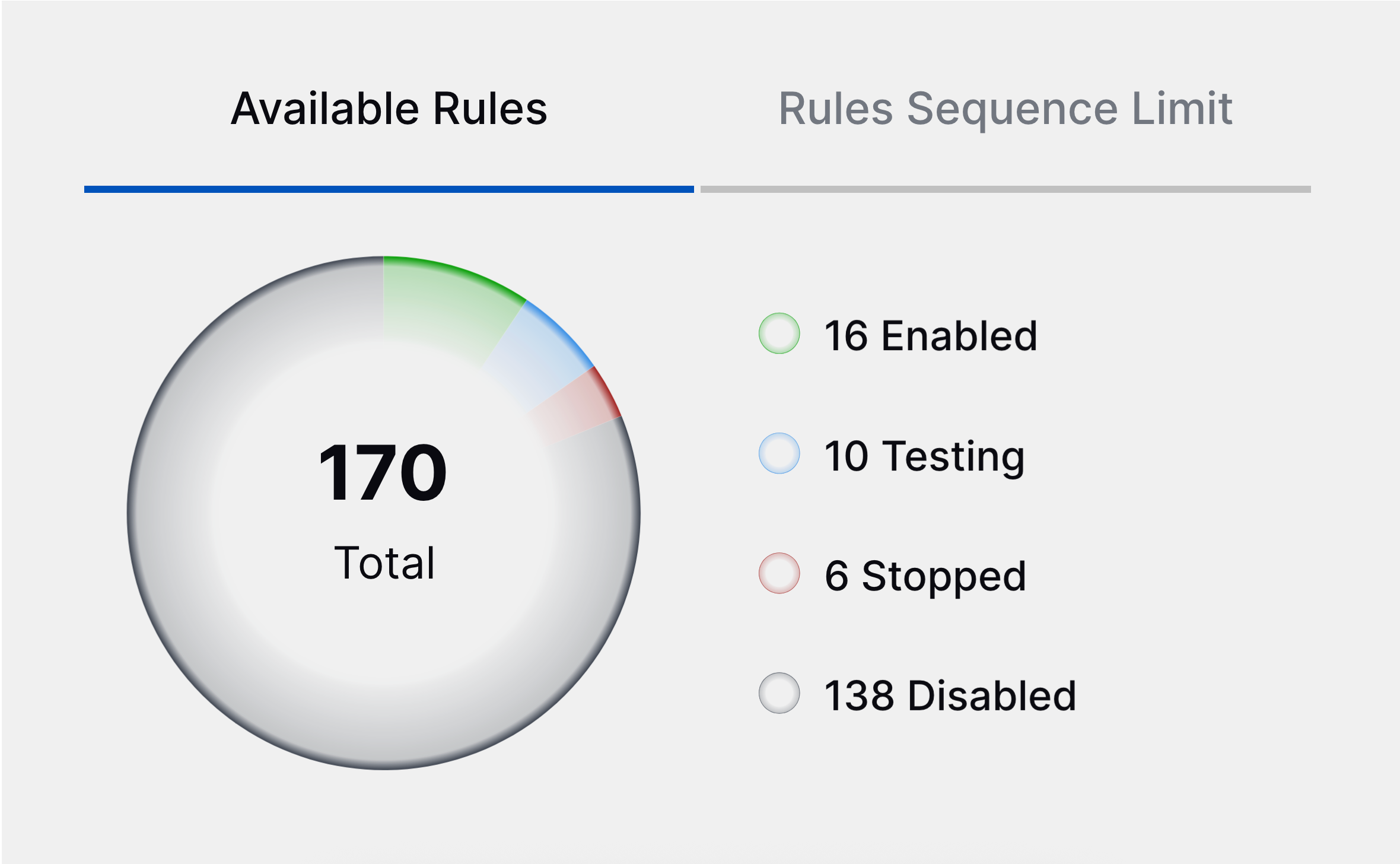
Correlation Rules Stopped and Testing Statuses | You can now better understand the state of a correlation rule with two new statuses: Stopped and Testing. The Stopped status indicates that the rule has triggered more than 50 times in five minutes and has automatically been disabled. The Testing status indicates that the rule is enabled in test mode and its outcomes are suppressed.  You can also filter correlation rules by the new statuses. 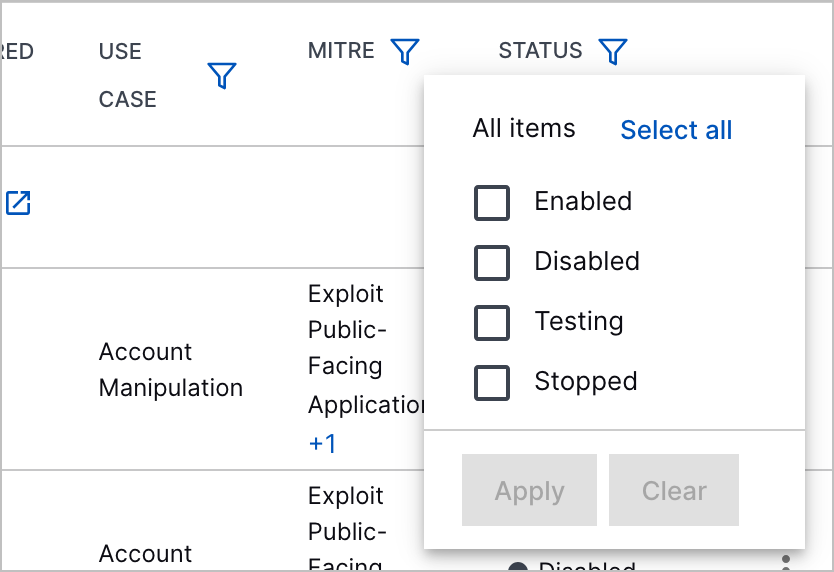 |
Apply Analytics Rule Updates Without Training | To immediately apply changes to analytics rules, minimize disruptions to other Exabeam applications, ensure the analytics engine continues to run in real time, and ensure you don't use any of your entitled training days, you can now apply analytics rules changes without training the analytics engine. When you apply changes to enabled rules in bulk, you now have the option to select Apply Changes Without Training. |
Correlation Rules Select Outcomes Enhancement | When you create or edit a correlation rule, the step to Select Outcomes now clearly explains what happens when a rule triggers and the possible outcomes:
|
Correlation Rule Details Severity Enhancement | When you view correlation rule details, you can now more quickly identify the correlation rule severity: 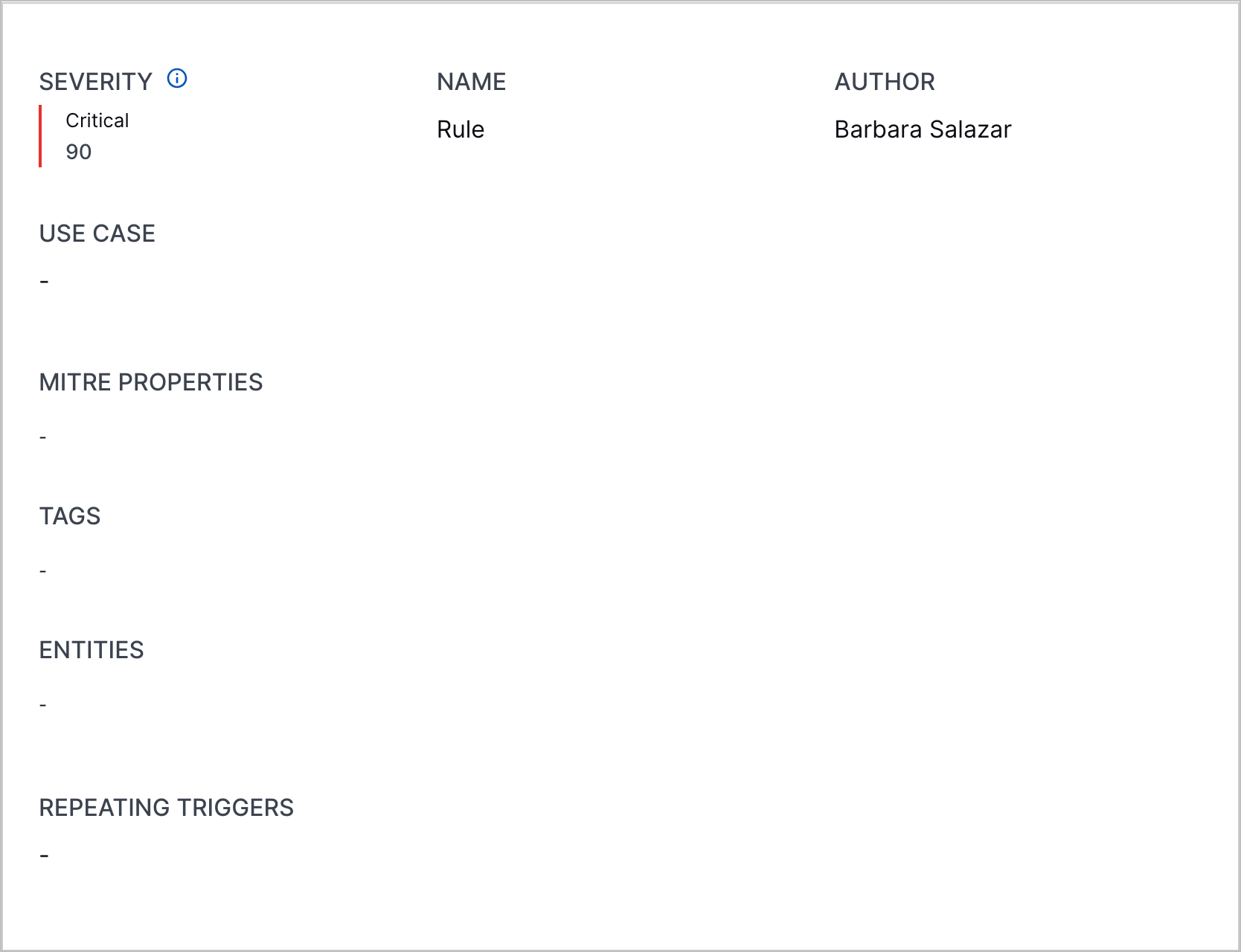
|
Correlation Rule Evaluation Delay Explanation | When you create or edit a correlation rule, the step to configure a rule evaluation delay now clearly explains what correlation rule evaluation delay is and that correlation rules are delayed from evaluating events for seven minutes by default. 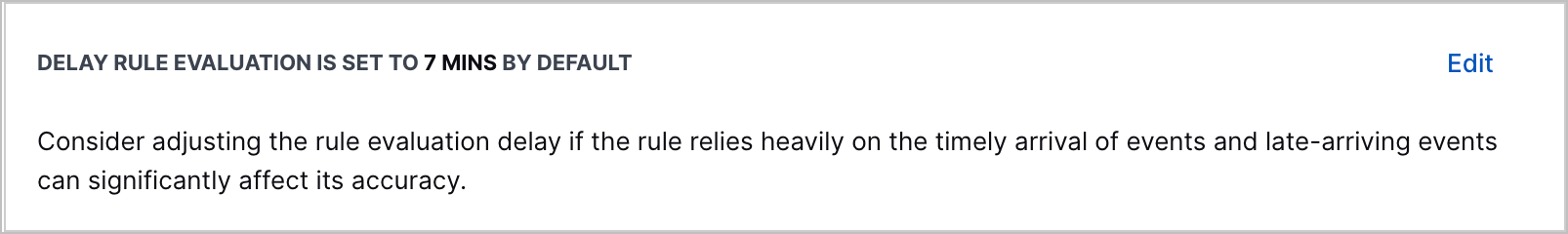 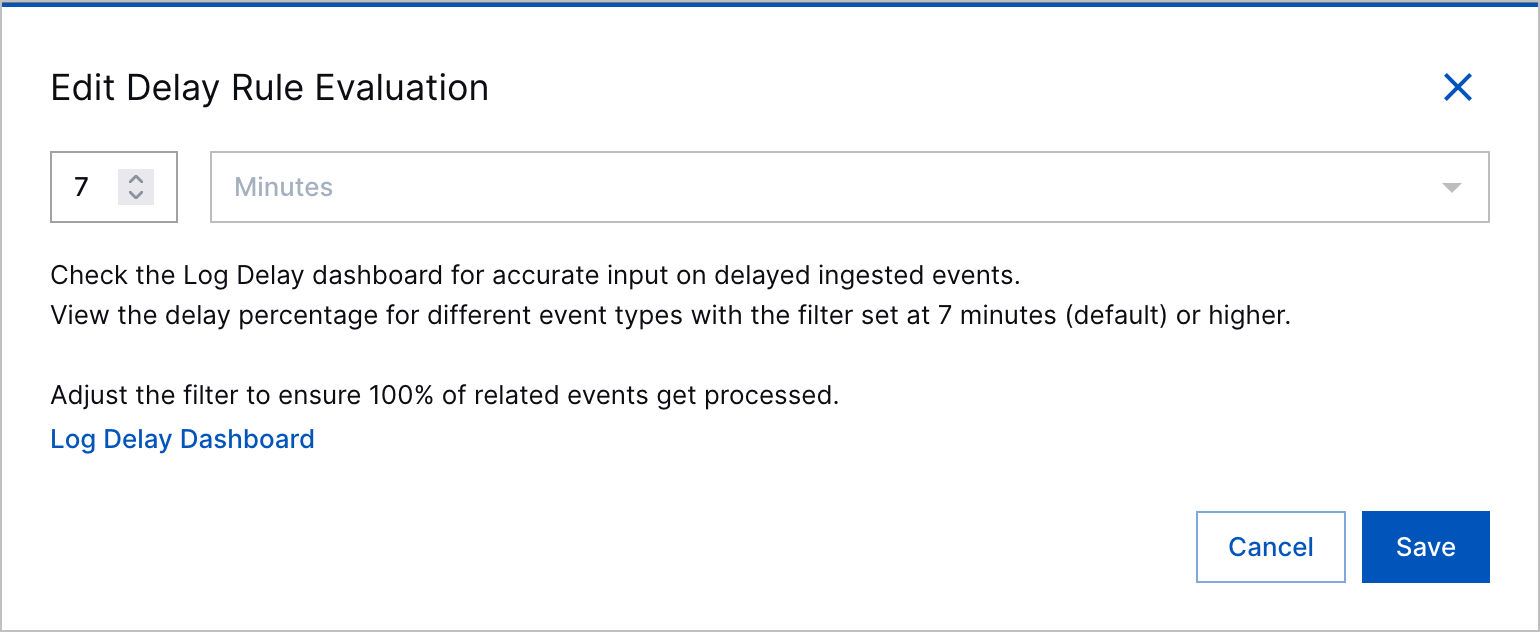 |
Correlation Rule Description Enhancements | You can now add more information to a correlation rule with descriptions. When you create or edit a correlation rule, you can now add a description about the correlation rule. 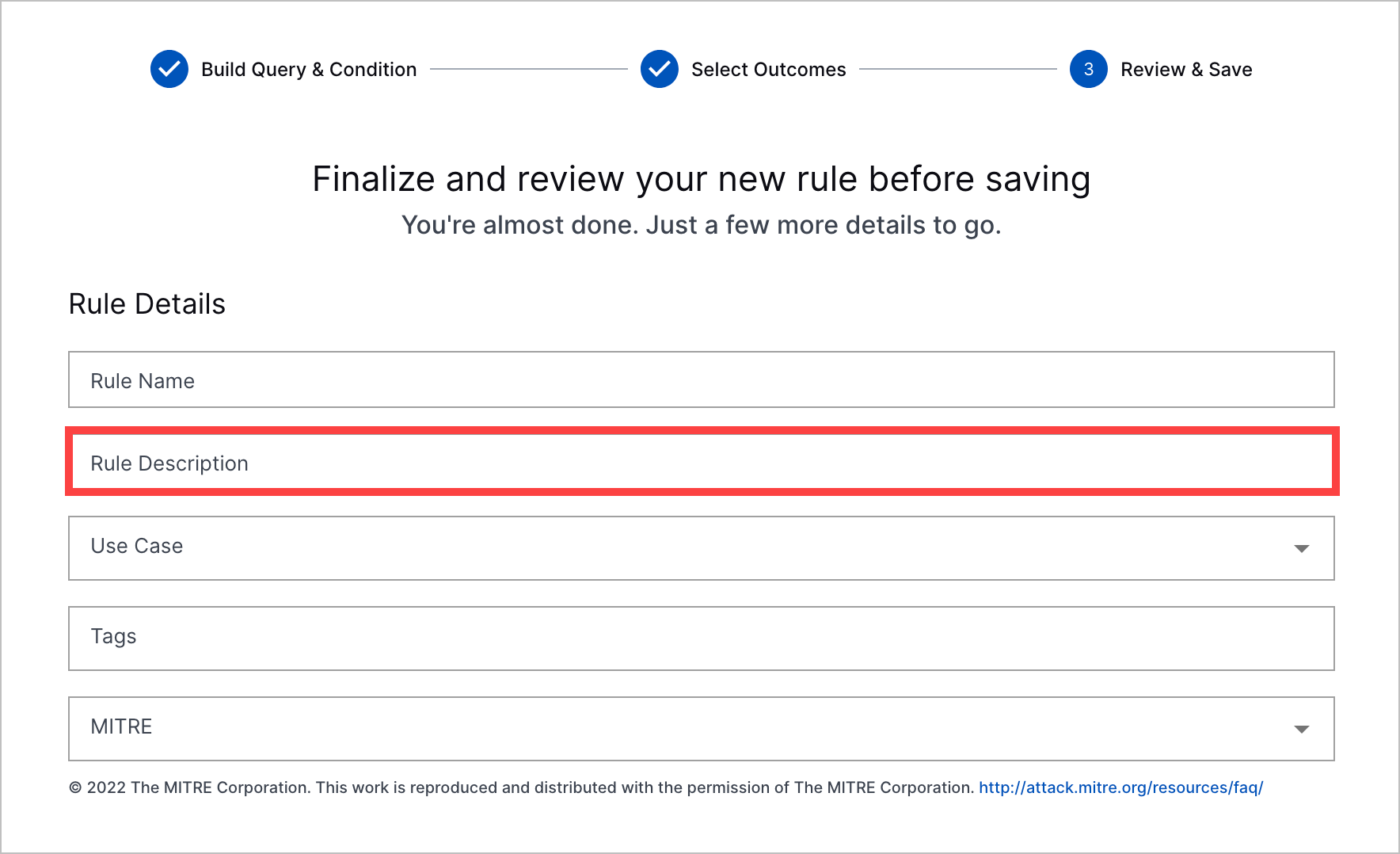 This description appears in the list of correlation rules and correlation rule details.  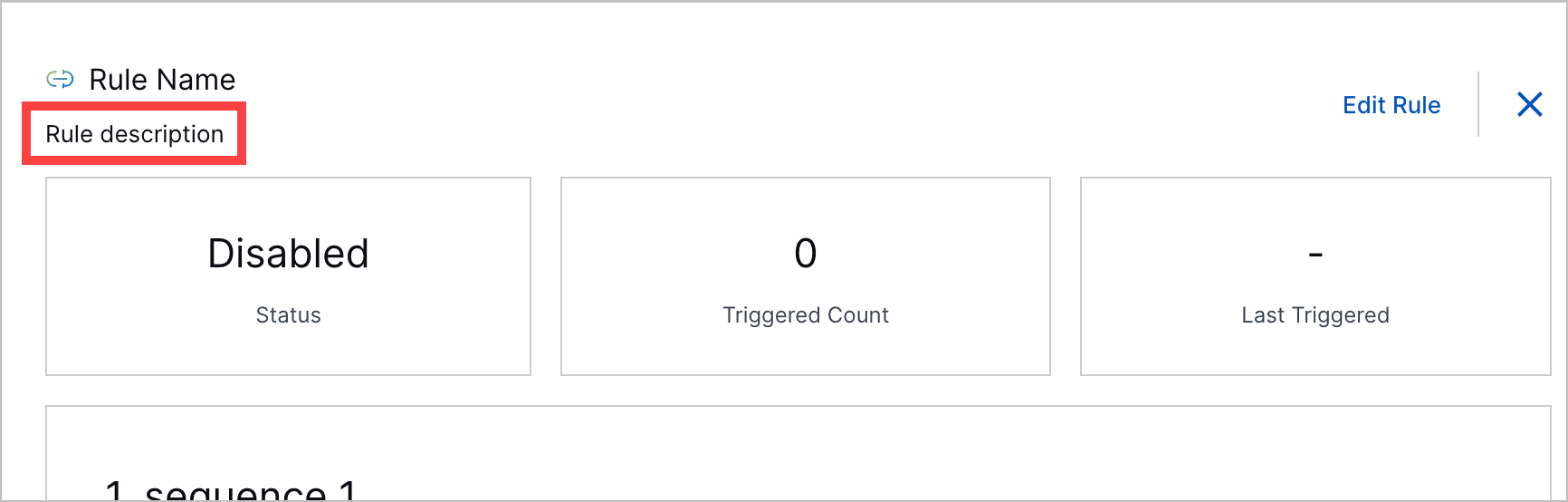 If you use a correlation rule template, the correlation rule template description is automatically reused as the description of your new correlation rule. |
Correlation Rule Triggered Value to Search Navigation | To view all events related to a correlation rule, you can now navigate to Search using a link next to the number times a rule has been triggered. The query automatically entered in Search is rules.rule: "<rule name>". The link appears in the list of correlation rules: 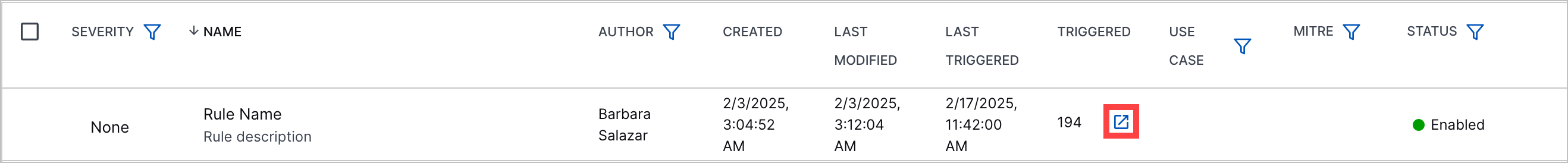 The link also appears when you view the correlation rule details: 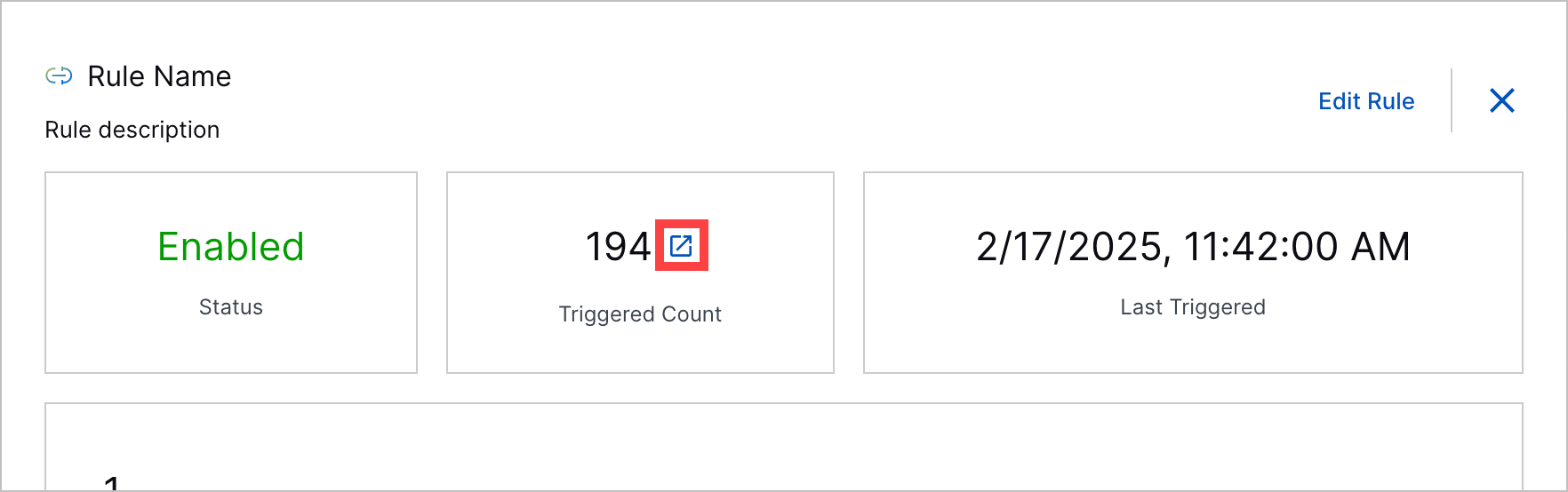 |
Correlation Rule Email Notification Address Change | Email notifications sent as a correlation rule outcome are now sent from [email protected]. To ensure any rules for filtering emails or creating third-party tickets work properly, ensure they use the new email address. |
New Region Support for the UK | Support for Threat Detection Management now extends to the UK region. You can now access and use Threat Detection Management in the UK. |
January 2025
The following features were introduced in Threat Detection Management in January 2025:
Feature | Description |
|---|---|
Introducing Threat Detection Management | Welcome to Threat Detection Management, the the hub on New-Scale Security Operations Platform for the rules you use to detect threats. It centralizes all rules, including both correlation and analytics, and both pre-built and custom, so you can ensure you're surfacing what's important to your organization in one place. Threat Detection Management is supported with a New-Scale SIEM, New-Scale Analytics, or New-Scale Fusion license. To get started with Threat Detection Management, view the Threat Detection Management documentation. |
Threat Center Outcomes Exclusions for Test Mode | To ensure you investigate and triage only real threats in Threat Center, correlation rules in test mode no longer create Threat Center cases or alerts. Events created from a triggered correlation rules in test mode have the activity type |