- Get Started with Threat Center
- Threat Center
- Threat Center Permissions
- Threat Center Alerts: Read
- Threat Center Alerts: Read, Write, and Delete
- Threat Center Cases: Read
- Threat Center Cases: Read, Write, and Delete
- Threat Center Detection Grouping Rules: Read
- Threat Center Detection Grouping Rules: Read, Write, and Delete
- Threat Center Watchlist: Read
- Threat Center Watchlist: Read, Write, and Delete
- Threat Center Cases
- Threat Center Alerts
- Threat Center Detections
- Threat Center Risk Score
- Monitor Entities of Interest in Threat Center
- Group Detections
- Work on Cases
- Work on Alerts
- Edit and Collaborate in Threat Center
- Use Automation Tools in Threat Center
- Find Cases and Alerts
- Sort Cases or Alerts
- Filter Cases or Alerts
- Search for Cases or Alerts in Threat Center
- Build a Search in Threat Center
- Enter a Search Using Exabeam Query Language in Threat Center
- Enter a Search Using Natural Language in Threat Center
- Run a Recent Search in Threat Center
- Create a New Saved Search in Threat Center
- Run a Saved Search in Threat Center
- Edit a Saved Search in Threat Center
- Delete a Saved Search in Threat Center
- View Case and Alert Metrics
- Get Notified About Threat Center
- Threat Center APIs
Threat Center Alerts
Get to know alerts, potential threats to which you might respond.
An alert is a group of related detections, which indicate a potential threat. You triage high-priority alerts or other alerts of interest to validate their risk and determine if you need to respond.
View alerts under the Alerts tab. By default, you see alerts created in the last 24 hours without an associated case sorted by risk score, from highest to lowest, then age, from newest to oldest. To view other alerts of interest, search for them. To view and update information about a specific alert, select the alert:
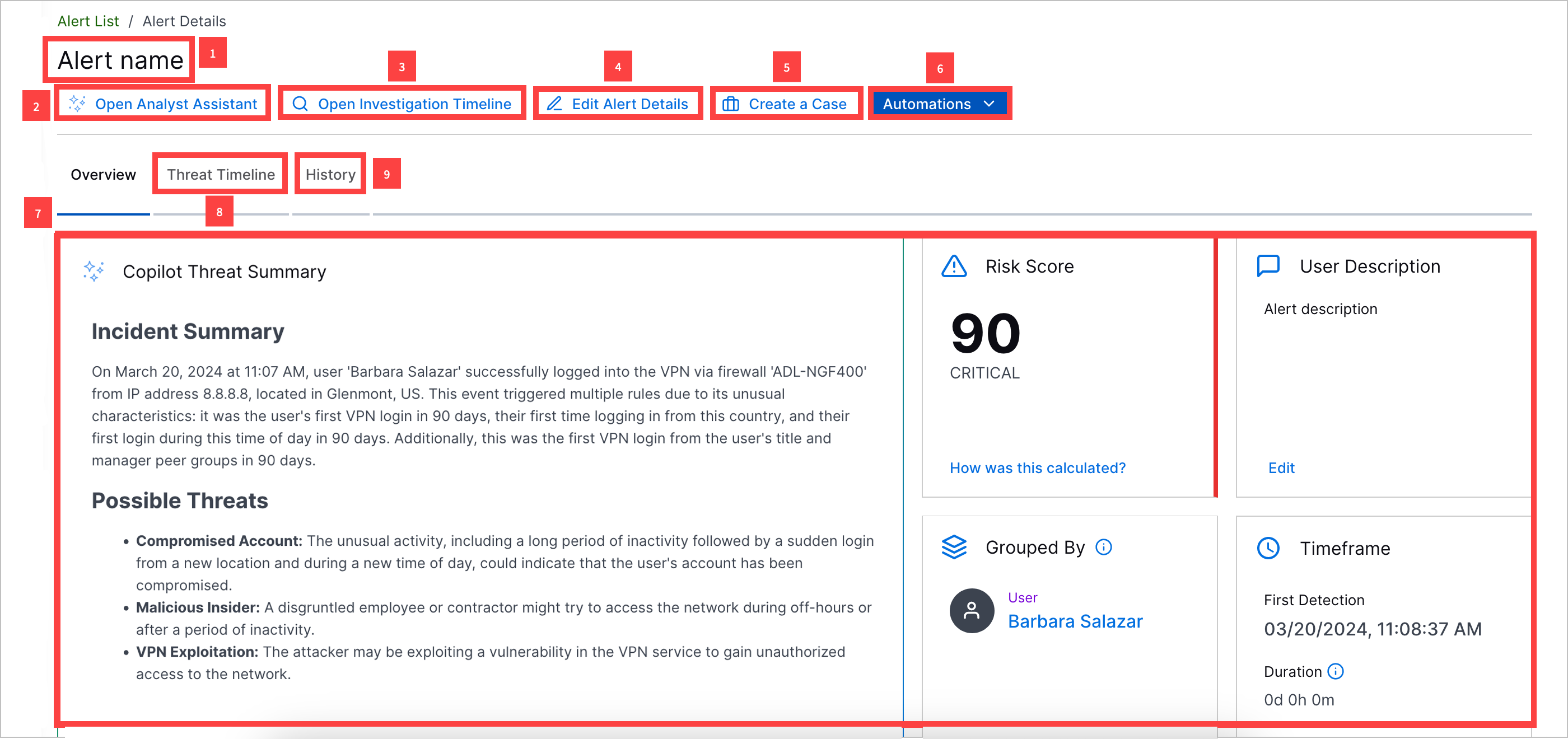
1 View the alert name.
2 Navigate to the timeline view in Search to view all related detections.
3 Use AI tools. Under the Analyst Assistant tab, ask a security-trained AI assistant questions about the alert. Under the Investigation Summary tab, view an AI-generated summary of the alert and recommended next steps.[2]
4 Under the Overview tab, view an overview of core alert information, including:
Exabeam Nova Investigation Summary – An AI-generated summary of the alert and recommended next steps. This summary is updated every time detections are added to the alert.
Risk Score – The case risk score and associated priority.
User Description – The alert description.
Created – The date and time the case was created and the time elapsed since the case was created.
Timeframe – Important markers of time associated with the alert, including:
First Detection – The date and time the first detection was added to the alert.
Duration – The days, hours, and minutes elapsed between when the first and last detection was added to the alert.
Users – Users associated with related detections.
Devices – The source and destination hosts associated with related detections.
Rules Triggered – The top seven triggered rules from which associated detections are created and the number of times they created associated detections. To view all triggered rules from which associate detections are created, click View all rules.
Automation – The five Automation Management playbooks and actions most recently run on the alert. View whether the run was successful, the playbook or action name, and the date and time the playbook or action was run. To view all playbooks and actions run on the case in the Automation tab, click View all.
MITRE TTPs – The ATT&CK tactics and techniques that best describe the case.
Use Cases – The Exabeam use cases that best describe the case.
5 In the Threat Timeline tab, view a timeline of related detections and key response moments, like when the alert was created.
6 View a history of all changes made to the alert.
7 In the Automation tab, view a history of Automation Management playbooks and actions run on the alert.
10 Convert the alert to a case.
11 Update alert attributes, including alert name, description, priority, associated MITRE ATT&CK® tactics and techniques, associated Exabeam use cases, and tags.[3]
12 Send alert information to email addresses, send alert information to webhooks, or manually run a playbook on the alert.
If you select an alert with an associated case, you're automatically redirected to the case.
Threat Center Alerts permissions determine what you're permitted to see and do with alerts.
[2] This tool is designed to condense security event data into easy-to-understand language, focusing on important security details. It can also answer follow-up questions and discuss security tech topics, but its accuracy might vary outside these areas. Always double-check responses for crucial decisions. Your queries and data will only be retained temporarily and won't be used for AI training. Exabeam is actively improving this tool and welcomes feedback.
[3] MITRE ATT&CK and ATT&CK are trademarks of The MITRE Corporation ("MITRE"). Exabeam is not affiliated with or sponsored or endorsed by MITRE. Nothing herein is a representation of the views or opinions of MITRE or its personnel.
