- Get Started with Threat Center
- Threat Center
- Threat Center Permissions
- Threat Center Alerts: Read
- Threat Center Alerts: Read, Write, and Delete
- Threat Center Cases: Read
- Threat Center Cases: Read, Write, and Delete
- Threat Center Detection Grouping Rules: Read
- Threat Center Detection Grouping Rules: Read, Write, and Delete
- Threat Center Watchlist: Read
- Threat Center Watchlist: Read, Write, and Delete
- Threat Center Cases
- Threat Center Alerts
- Threat Center Detections
- Threat Center Risk Score
- Monitor Entities of Interest in Threat Center
- Group Detections
- Work on Cases
- Work on Alerts
- Edit and Collaborate in Threat Center
- Use Automation Tools in Threat Center
- Find Cases and Alerts
- Sort Cases or Alerts
- Filter Cases or Alerts
- Search for Cases or Alerts in Threat Center
- Build a Search in Threat Center
- Enter a Search Using Exabeam Query Language in Threat Center
- Enter a Search Using Natural Language in Threat Center
- Run a Recent Search in Threat Center
- Create a New Saved Search in Threat Center
- Run a Saved Search in Threat Center
- Edit a Saved Search in Threat Center
- Delete a Saved Search in Threat Center
- View Case and Alert Metrics
- Get Notified About Threat Center
- Threat Center APIs
Threat Center Cases
Get to know cases, which represent a response to a threat.
A case is a record of how you respond to a threat. As you investigate the threat, you collect all information and evidence and add them to the case. You assign a case to someone to respond and track their progress through the response stages.
You can create a case automatically based on conditions you define using Automation Management playbooks, by converting an alert to a case, or manually.
View cases under the Cases tab. By default, you see open cases created in the last week sorted by risk score, from highest to lowest, then age, from newest to oldest. To view other cases of interest, search for them. To view and update information about the case, select the case under the Cases tab. When you select an alert with an associated case, you are automatically redirected to the case.
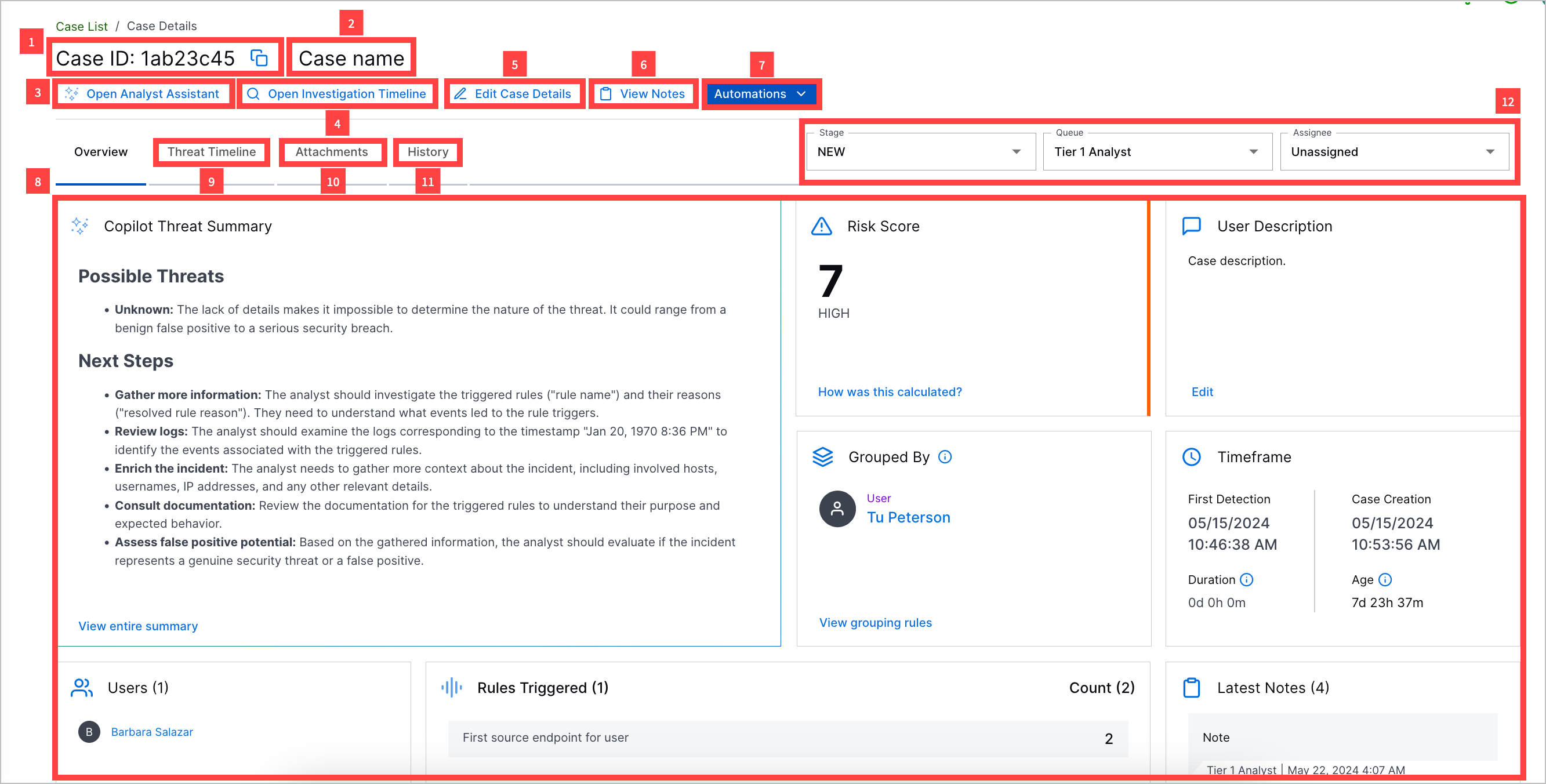
1 View and copy the case ID. If the case is manually created, it is labeled as Manually Created.
2 View the case name.
3 Navigate to the timeline view in Search to view all related detections. If the case is manually created, this action isn't available.
4 Use AI tools. Under the Analyst Assistant tab, ask a security-trained AI assistant questions about the case. Under the Investigation Summary tab, view an AI-generated summary of the case and recommended next steps.
5 In the Overview tab, get an overview of core case information, including:
Case Closed – Appears only if the case stage is Closed. Shows the reason why the case was closed, the queue and assignee assigned to the case when it was closed, and the date and time the case was closed.
Exabeam Nova Investigation Summary – An AI-generated summary of the case and recommended next steps. This summary is updated every time detections are added to the case.
Risk Score – The case risk score and associated priority.
User Description – The case description.
Created – The date and time the case was created and the time elapsed since the case was created.
Timeframe – Important markers of time associated with the case, including:
First Detection – The date and time the first detection was added to the alert.
Duration – The days, hours, and minutes elapsed between when the first and last detection was added to the alert.
Case Creation – The date and time the case was created.
Age – For an open case, the days, hours, and minutes elapsed between when the case was created and the current time; or, for a closed case, the days, hours, and minutes between when the case was created and last closed.
Users – Users associated with related detections.
Devices – The source and destination hosts associated with related detections.
Rules Triggered – The top seven triggered rules from which associated detections are created and the number of times they created associated detections. To view all triggered rules from which associate detections are created, click View all rules.
Latest Notes – The notes most recently added to the case.
Automation – The five Automation Management playbooks and actions most recently run on the case. View whether the run was successful, the playbook or action name, and the date and time the playbook or action was run. To view all playbooks and actions run on the case in the Automation tab, click View all.
MITRE TTPs – The ATT&CK tactics and techniques that best describe the case.
Use Cases – The Exabeam use cases that best describe the case.
Attachments – Files attached to the case.
6 In the Threat Timeline tab, view a timeline of related detections and key response moments, including when the alert was created, when the associated case was created, when the investigation started, when remediation ended, and when the associated case was closed. If the case is manually created, this tab isn't available.
7 In the Attachments tab, add, download, and remove attachments.
8 In the History tab, view a history of all changes made to the case.
9 In the Automation tab, view a history of Automation Management playbooks and actions run on the case. If the case is manually created, this tab isn't available.
10 Assign a stage, queue, and assignee to the case.
11 Update case attributes, including case name, description, stage, queue, assignee, priority, MITRE ATT&CK® tactics and techniques, use cases, and tags.[1]
12 Document your investigation and remediation using case notes.
13 Send case information to email, send case information to webhook, or manually run a playbook on the case.
[1] MITRE ATT&CK and ATT&CK are trademarks of The MITRE Corporation ("MITRE"). Exabeam is not affiliated with or sponsored or endorsed by MITRE. Nothing herein is a representation of the views or opinions of MITRE or its personnel.
