- Welcome to Threat Detection Management
- Analytics Rules
- Correlation Rules
- Threat Scoring
Manage Analytics Rule Exclusions
From the Threat Detection Management app, you can view and manage exclusions for analytics rules. You can configure up to 1000 exclusions.
Exclusions can apply across the entire rule base or to specific rules or groups of rule families. To define an exclusion, you write conditions to exclude some rules from triggering on specific event field’s value or context tables.
View all Rule Exclusions
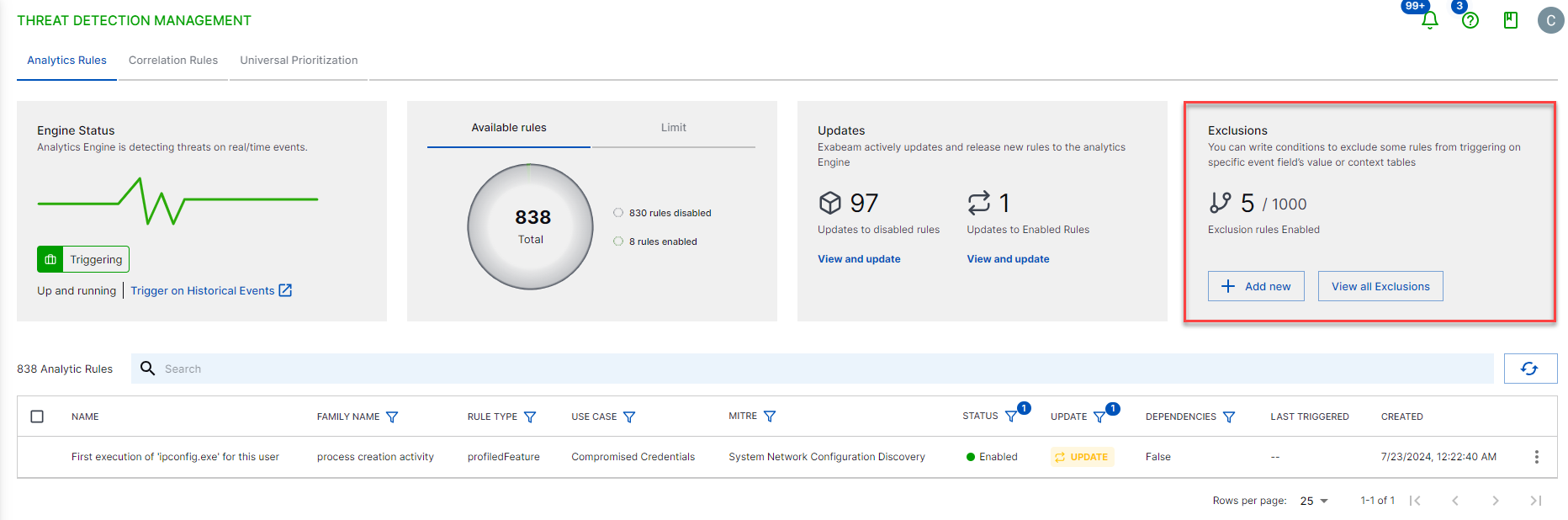 |
From the main Threat Detection Management page, you can view the total number of applied exclusions. To view details for exclusions, click the View all Exclusions link in the Exclusions summary. For each exclusion, you can see the title and description, rule scope, author (created by), creation date, last modified date, and current status. To view the definition of conditions that exclude the rule from triggering, click the more actions menu ( ) > View.
) > View.
For each exclusion, you can view the
Add a Rule Exclusion
Log in to the New-Scale Security Operations Platform and go to the Threat Detection Management app.
From the Exclusions summary, select New Exclusion.
From the Exclusions page, you can also click New Rule to create a new exclusion.
Define the exclusion details:
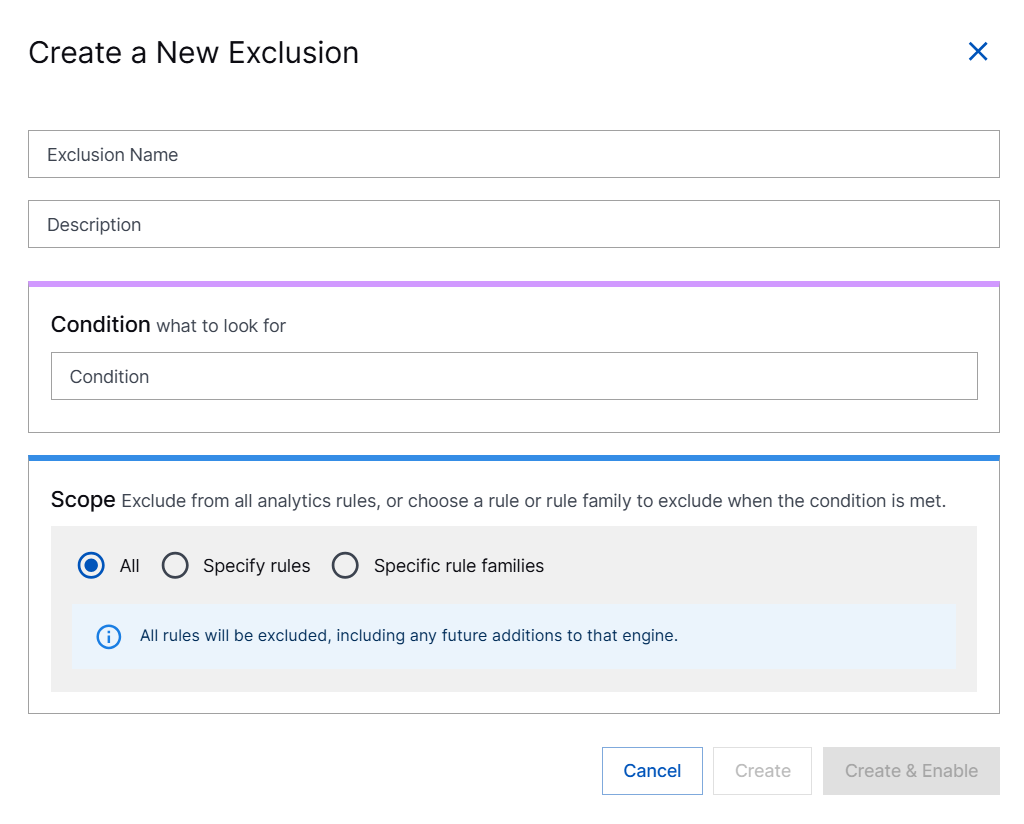
Exclusion Name – Enter a descriptive name for the exclusion.
Description – Provide more details about the purpose or use of the exclusion.
Condition – Specify the match conditions for which you want to exclude rules from applying. Keep in mind the guidelines when specifying the condition expression. For more details, see Rule Conditions.
Scope – Define the rule scope to specify the rules for which the exclusion applies. You can set the exclusion to any of the following scopes:
All – (Default) Apply the exclusion to all rules so that when the condition is met, no alerts are raised.
Specific rules – When the condition is matched, apply the exclusion to one or more specific rules.
Specific rule families – When the condition is matched, apply the exclusion to one or more rule families. For example, you could apply the exclusion to any rule categorized as cloud-policy-management-activity.
Create your exclusion in an disabled state to save your changes, or if you are ready to activate it, click Create & Enable.
After exclusions are enabled, the analytics engine will restart. This can take up to 10 minutes to complete. Enabling exclusions in batch mode will decrease the number of restarts required.
Tip
If you intend to create multiple exclusions, it is recommended to create them in a disabled state and enable them all at once. This will minimize the number of required restarts.
Manage an Existing Rule Exclusion
After you Add a Rule Exclusion, you can take additional action to manage the exclusion. Actions include editing the exclusion details, enabling or disabling the exclusion, and deleting the exclusion.
To manage the exclusion:
Log in to the New-Scale Security Operations Platform and go to the Threat Detection Management app.
From the Exclusions summary, select View all Exclusions.
(Optional) Use the search to narrow the list of results.
You can search for a full or partial exclusion name, exclusion description, or creator. As you type, the list of exclusions updates to display results that match your search term.
In the row of your exclusion, select the more actions menu (
 ) and then select the desired action:
) and then select the desired action: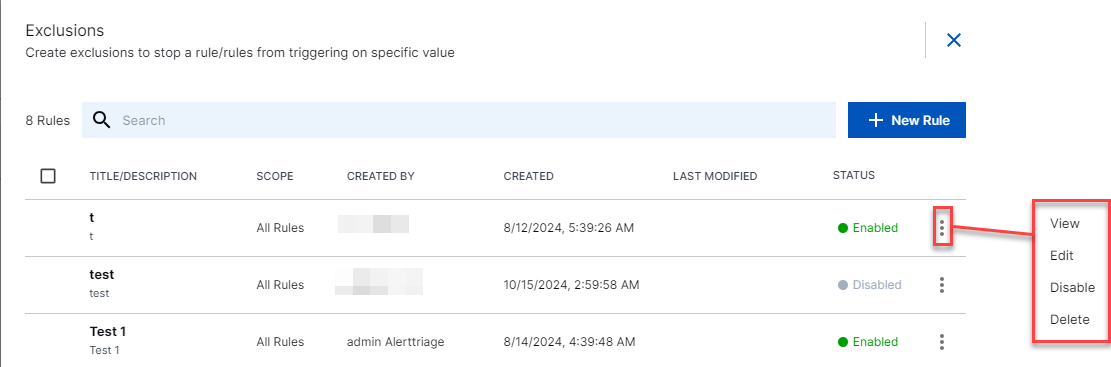
View – View the exclusion definition.
Edit – Modify the exclusion definition.
Disable | Enable – Change the status of the exclusion.
Delete – Permanently delete this exclusion. If you later change your mind, you will need to recreate a new exclusion.