- Get Started with Threat Detection Management
- Analytics Rules
- Analytics Rule Classifications
- Create an Analytics Rule
- Manage Analytics Rules
- Tune Analytics Rules
- Find Analytics Rules
- Share Analytics Rules
- Troubleshoot Analytics Rules
- Analytics Rules Syntax
- Advanced Analytics Rule Syntax vs. Analytics Rule Syntax
- Logical Expressions in Analytics Rule Syntax'
- String Operations Using Analytics Rule Syntax
- Integer Operations Using Analytics Rule Syntax
- Time Operations Using Analytics Rule Syntax
- Network Operations Using Analytics Rule Syntax
- Context Operations Using Analytics Rule Syntax
- Entity Operations Using Analytics Rule Syntax
- Correlation Rule Operations Using Analytics Rule Syntax
- Analytics Engine Status
- Correlation Rules
- Threat Scoring
Analytics Rules
Get to know analytics rules, rules that identify how risky an event is.
Analytics rules are rules that assess events for potential risk as a part of the analytics engine. With the statistical analysis and pattern recognition capabilities of the analytics engine, you can identify trends and deviations that may indicate a security risk.
Each analytics rule represents an individual measure or characteristic of an event that may indicate risk; for example, whether an IP is blacklisted or whether a user failed to log in to an application an abnormal number of times. Each incoming event is assessed against a collection of analytics rules.
When an analytics rule triggers, an analytics rule detection is created and the analytics engine uses information about the analytics rule and the trigger to calculate a rarity score for the detection.
Analytics rules are classified into types, families, and groups. The analytics rule type organizes analytics rules into how the analytics rule functions; for example, directly evaluating event data or profiling historical activity to identify unusual patterns. The analytics rule family organizes analytics rules into the type of event the rule evaluates; for example, authentication activity events or web activity events. The analytics rule group organizes analytics rules into statistical relationships.
To ensure you have the latest threat detection capabilities, Exabeam threat researchers regularly deliver new pre-built analytics rules and updates to existing pre-built analytics rules through security content packages. When these updates are delivered, you must apply the updates. To detect a security threat not addressed with a pre-built analytics rule, you can create your own analytics rule. After you create an analytics rule, you can share and delete it. To further tune analytics rules, you can exclude specific events or event field values from triggering an analytics rule.
For analytics rules to trigger, you must enable them. Once enabled, you can disable them. Threat Detection Management may automatically disable an analytics rule if it over triggers, triggers more than 50 times in five minutes, or if the analytics engine determines the analytics rule is incompatible with your data or is highly likely to generate false positive results.
To ensure the analytics engine is running smoothly so your analytics rule can actively detect threats, you can monitor the analytics engine directly in Threat Detection Management.
To navigate to analytics rules in Threat Detection Management, click the Analytics Rules tab.
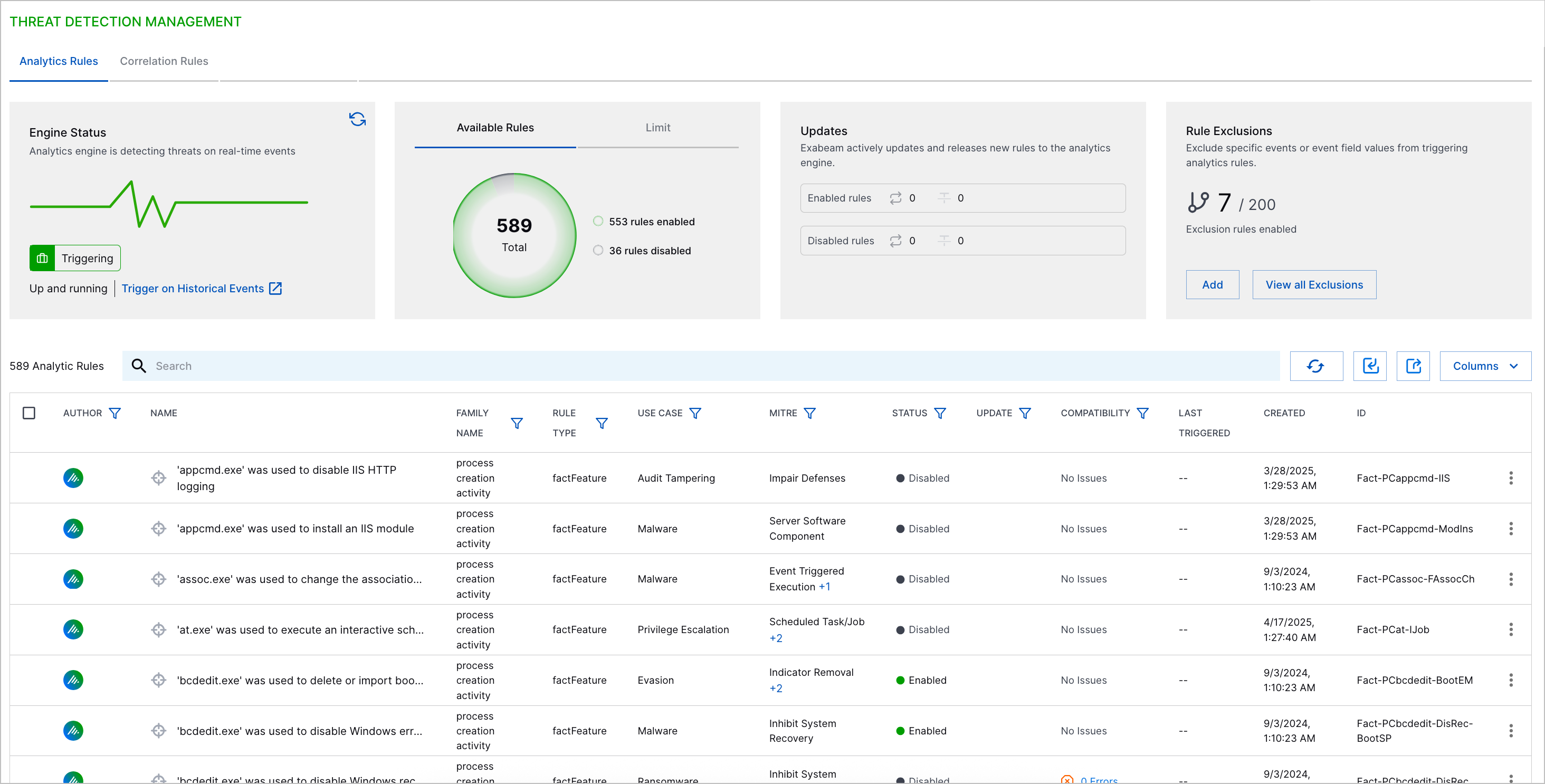 |
For each analytics rule, view:
Author – Who created the analytics rule. For pre-built analytics rules, the author is Exabeam
 .
.Name – The analytics rule name
Family name – The analytics rule family to which the analytics rule belongs
Rule type – The analytics rule type
Use case – The Exabeam use case associated with the analytics rule
MITRE – The MITRE ATT&CK® tactic associated with the analytics rule[1]
Status – The state of the analytics rule:
Enabled – The analytics rule is enabled.
Disabled – The analytics rule is disabled.
Stopped – The analytics rule has triggered more than 50 times in five minutes and has automatically been disabled.
Testing – The analytics rule is enabled in test mode and its outcomes are suppressed.
Training – The analytics rule is in a training period and won't trigger. To view how much time is left until training is completed, hover over the status. After the analytics rule is finished training, its status is automatically changed to Enabled.
Update – How the analytics rule is changed with pending updates:
Update – The rule is modified with the update.
Obsolete – The rule is removed with the update.
None – The rule is not affected by the update.
Rule insights – Whether the analytics rule over-triggers. To ensure the analytics engine runs normally, the analytics engine monitors rule training and evaluation processes and prevents you from enabling analytics rules that are incompatible with your data or are highly likely to generate false positive results. These analytics rules are marked as having Insights. To troubleshoot the analytics rule, click the column value, Insights.
Last triggered – The date and time the analytics rule was last triggered
Last modified – The date and time the analytics rule was last modified.
Created – The date and time the analytics rule was created
ID – A unique identifier assigned to the analytics rule
[1] MITRE ATT&CK and ATT&CK are trademarks of The MITRE Corporation ("MITRE"). Exabeam is not affiliated with or sponsored or endorsed by MITRE. Nothing herein is a representation of the views or opinions of MITRE or its personnel.
