- What's New
- Fixed Issues in Data Lake i40.8
- Fixed Issues in Data Lake i40.7
- Fixed Issues in Data Lake i40.6
- Fixed Issues in Data Lake i40.5
- Fixed Issues in Data Lake i40.4
- Fixed Issues in Data Lake i40.3
- Fixed Issues in Data Lake i40.2
- Fixed Issues in Data Lake i40.1
- Fixed Issues in Data Lake i40
- Known Issues in Data Lake i40
What's New
If you use Data Lake i33.x or a later version, you can upgrade directly to Data Lake i40.x to take advantage of new features and improvements.
What's New in i40.8
The Data Lake i40.8 release consisted of various bug fixes. For more information, see Fixed Issues in Data Lake i40.8.
What's New in i40.7
The Data Lake i40.7 release consisted of various bug fixes. For more information, see Fixed Issues in Data Lake i40.7.
What's New in i40.6
The Data Lake i40.6 release consisted of various bug fixes. For more information, see Fixed Issues in i40.6.
What's New in i40.5
This release consisted of various bug fixes. For more information, see Fixed Issues in i40.5.
What's New in i40.4
Due to a known issue with Data Lake i40.4, this release is no longer available for download. For more information, see Known Issues in Data Lake i40.
What's New in i40.3
Customers who upgrade to Data Lake i40.3 can take advantage of the following new features and improvements:
Apache Log4J Security Patch
A critical vulnerability in software using Apache Log4j affected the following Exabeam Products:
Logstash and Elasticsearch in Data Lake
Logstash and Datadog Agent in Site Collector
This vulnerability has been patched. Learn more about Exabeam's response to the vulnerability on Exabeam Community.
Redesigned User Interface
The main navigation menu, previously located on the top-right side of the user interface, has been redesigned into a vertical menu on the left side of the interface. This redesign is part of a move towards unifying the navigation experience across the different Exabeam environments.
Miscellaneous Improvements and Updates
Re-added support for Windows Server 2008 R2 for agent collectors.
Updated Threat Intelligence Feeds from ZeroFox
To provide increased accuracy for risk evaluation of users and assets, Exabeam can now leverage threat intelligence feeds from ZeroFox (ZF) across Exabeam products. The ZeroFox feeds provide improved information for indicators of compromise (IoCs) such as IP addresses associated with ransomware and malware attacks.
In most cases, no configuration change is required to begin utilizing ZeroFox threat intelligence. However, if you previously disabled rules or models that utilize the new feeds, you will need to enable them to utilize the new feeds.
The following table displays the rules that leverage the ZeroFox threat intelligence feeds by IoC category:
IoC Category | Rules |
|---|---|
(ZF) IP addresses associated with ransomware attacks |
|
(ZF) IP addresses associated with ransomware or malware attacks |
|
(ZF) Domain names and URLs associated with sites that often contain malware, drive-by compromises, and more |
|
(ZF) Domain names associated with phishing or ransomware | WEB-UD-Phishing |
What's New in i40.2
Customers who upgrade to Data Lake i40.2 can take advantage of the following new features and improvements:
Display Empty/Null fields in Data Lake visualizations
Added the ability to display any field that is empty or null in Data Lake visualizations. Previously, these fields were ignored.

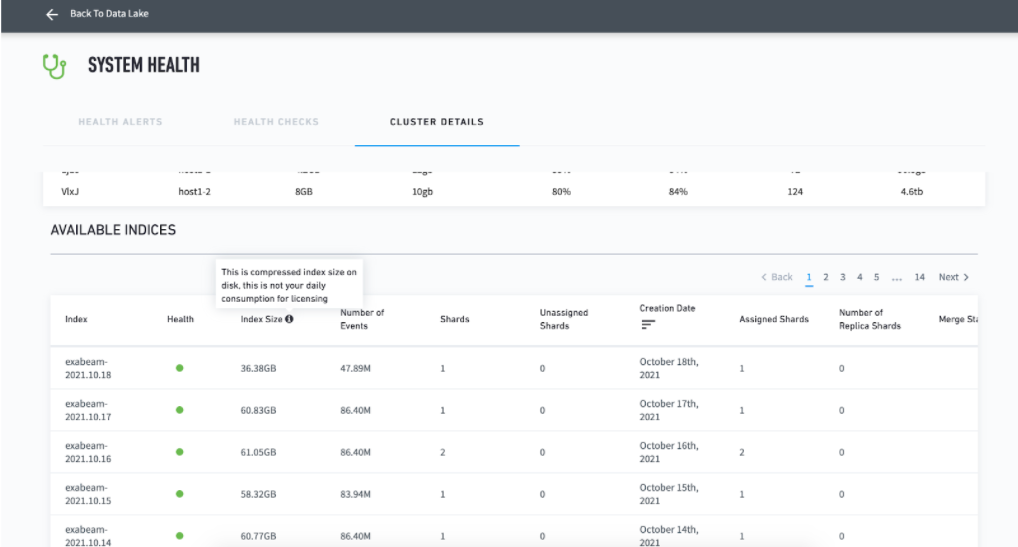
Renamed Volume to Index Size in operational stats
On the System Health page, the term Volume has been replaced with Index Size, to remove any confusion as to what is being represented. An explanation of the value has also been added.
Miscellaneous Improvements and Updates
Reduced the size of metadata information, and limited the metadata fields to the most valuable, to optimize the data and minimize the cost to customers.
Added support for Ubuntu 20.04 agents.
Added support in Site Collector for JSON logs, allowing customers to easily onboard JSON logs, eliminating issues previously experienced when parsing these logs.
What's New in i40.1
Customers who upgrade to Data Lake i40.1 can take advantage of the following new features and improvements:
The cluster charts provided in Data Lake have been improved to provide more relevant and useful information to customers.
Metadata processing in Site Collector and supported collection agents has been optimized to include only fields that provide significant value.
What's New in i40
Customers who upgrade to Data Lake i40 can take advantage of the following new features and improvements:
An Enhanced Reindexing Experience for Admins
Reindexing operations no longer compete with ongoing ingestion for resources. They now use only available resources, so they can be safely run at any time. You can also track ongoing reindexing jobs and view the history of past jobs.
For more information, see Reindex Operations.
Get More from Your Data with an Additional Syslog Destination
To leverage event data from Site Collector for additional IT operations, you can now add a secondary Syslog destination in SaaS deployments. The secondary destination can be used for a variety of purposes, such as gaining additional insights from your data in non-security applications, satisfying legal requirements for storing data, easing cloud adoption and migration, and supporting disaster recovery operations. The secondary destination can be located on premises or in a virtual environment.
For more information, see Add a Secondary Syslog Destination.
Miscellaneous Improvements and Updates
Filtered search results can now be exported to PDF files.
Context tables can now be enriched with user attributes from Azure Active Directory. These attributes can in turn be used as search filters. See Azure AD Context Enrichment.
You can now delete archived snapshots from the NFS drive. See Delete Snapshots from the Archive.
The Advanced Settings page has been redesigned and streamlined to include only supported settings.
Exported query results now include a CSV file that reports any errors that occurred in the query. The addition of the error report provides a clear picture of your results set.
To enhance the security of cloud-delivered services, Security-Enhanced Linux (SELinux) is enabled by default in Data Lake.
Data Lake now includes a user interface for upgrading site collectors to the latest software. See Upgrade Site Collector.
The primary Site Collector now supports network ports 1194 and 443 for OpenVPN to simplify the installation process.
Orphaned collectors can now be manually removed 15 days after being uninstalled. See Remove an Uninstalled Collector from the Collector Management Page.
eStreamer now uses the eNcore version 3.7.4 library.
