- Welcome to Exabeam Security Content
- What is Security Content?
- Common Information Model
- What is the Common Information Model?
- Common Information Model Context Elements
- Common Information Model Interface
- Common Information Model Event-naming Format
- Common Information Model Impact on Downstream Processes
- Using the Common Information Model to Create Custom Content
- Transitioning to the Common Information Model
- Understanding the Log
- Exabeam Parsers
- Exabeam Event Building
- Exabeam Enrichment
- Exabeam Persistence and Templates
- Exabeam Models
- Exabeam Rules
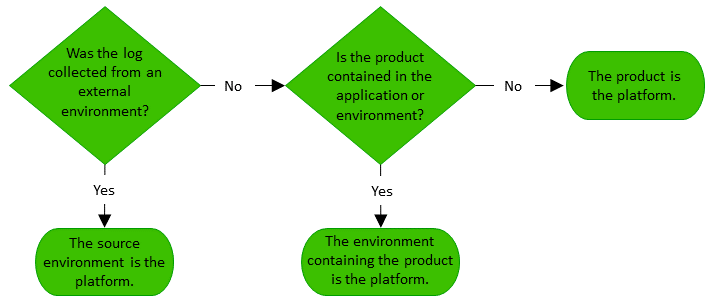
Identifying the Platform
A platform is the virtual environment or application in which an event took place. To identify the platform in an event, ask the following questions:
Was the log collected from an external environment? If so, the source environment is the platform.
Is the product contained in the application or environment? If so, the environment that contains the product is the platform.
If neither of these is the case, then the product is the platform.
Platform Example 1
Check Point NGFW – Network Connection
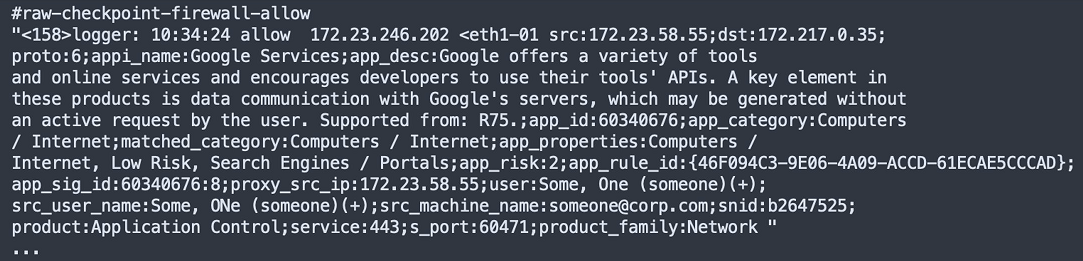
In this example, the event was logged by a Check Point Next Generation Firewall (NGFW), but the source of the event is identified as the network. Therefore, the event platform for this log is network.
Platform Example 2
GCP UpdateRole – Role Permission Modification
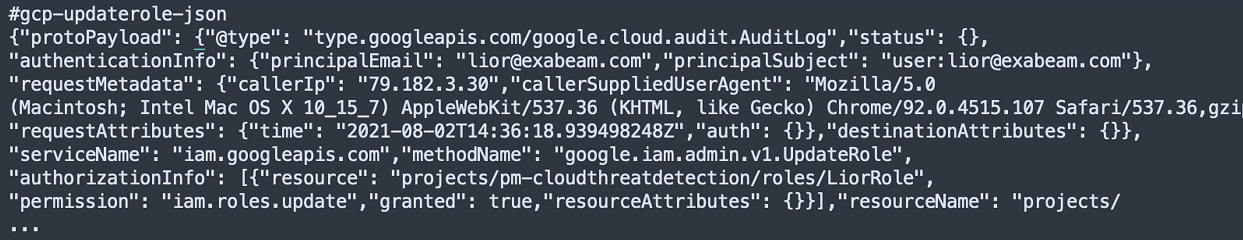
In this example, the event was logged by GCP CloudAudit. But CloudAudit is a logging product inside the Google Cloud Platform (GCP) environment. In this case, the platform is actually gcp.
Platform Example 3
CheckPoint NGFW – Application Login
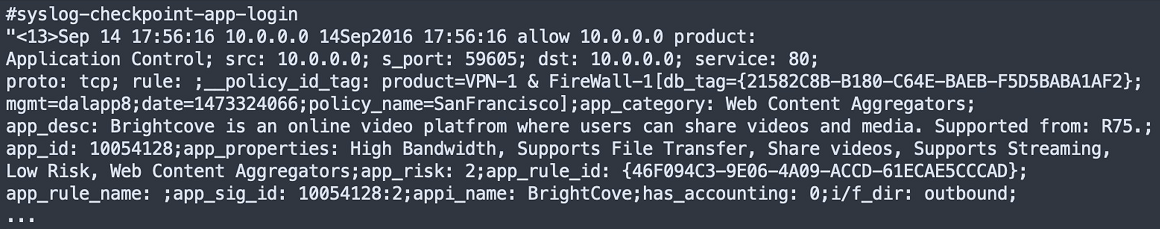
As in Example 1, this log shows an event that was logged by a Check Point Next Generation Firewall (NGFW). However, in this case, the event is both monitored by the firewall and represents an operation on the firewall. Therefore, the platform is check point ngfw.
Tips for Unique Platform Cases
If you're still unsure about the event platform, consider the following questions:
What is the purpose of the product?
Is it possible that the product could audit other environments?
Products like centralized logging services, EDRs, firewalls, and other security products are designed to monitor multiple platforms. These types of cases may require a deeper investigation to identify the platform.
