- Welcome to Exabeam Security Content
- What is Security Content?
- Common Information Model
- What is the Common Information Model?
- Common Information Model Context Elements
- Common Information Model Interface
- Common Information Model Event-naming Format
- Common Information Model Impact on Downstream Processes
- Using the Common Information Model to Create Custom Content
- Transitioning to the Common Information Model
- Understanding the Log
- Exabeam Parsers
- Exabeam Event Building
- Exabeam Enrichment
- Exabeam Persistence and Templates
- Exabeam Models
- Exabeam Rules
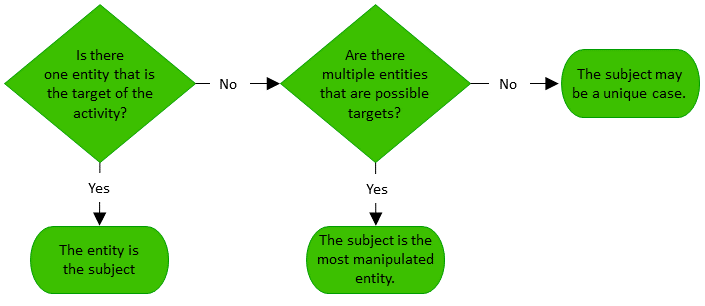
Identifying the Subject
The subject is the target entity in an event. To identify the subject of an event, ask the following questions:
Is there one entity that is the target of the operation? If so, that entity is the subject.
Are there multiple possible entities that are the target? If so, the subject is the most manipulated entity.
If neither of these questions identifies the subject, see Tips for Unique Subject Cases.
Subject Example 1
Symantec SIEM – File Write
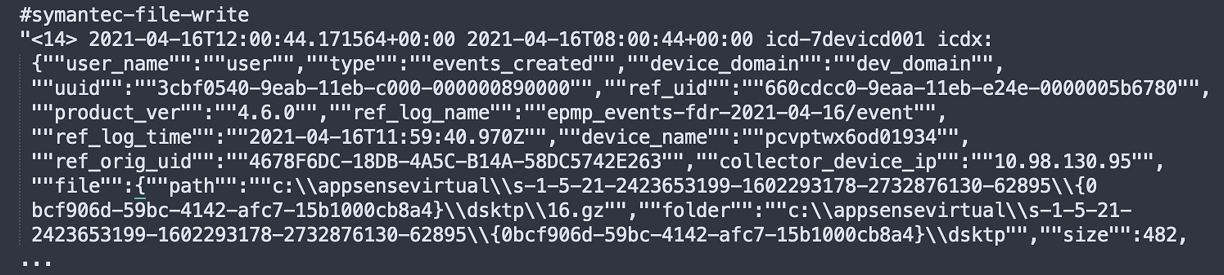
In this straight-forward example, the activity is performed on a file. Therefore, file is the subject and there is no need to reference the platform or the product.
Subject Example 2
Logrhythm – Office 365 Password Change
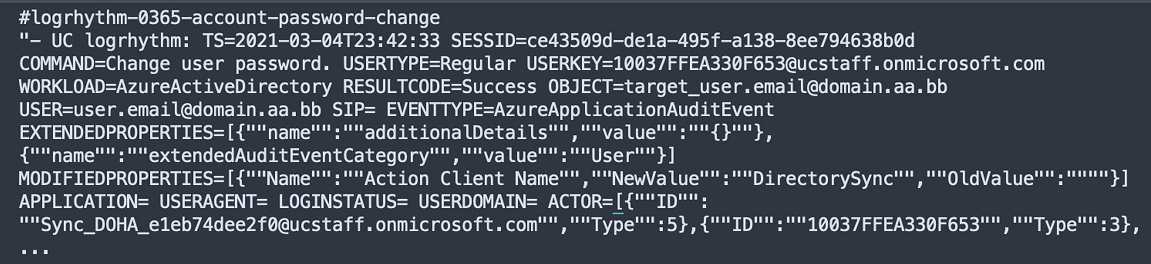
In this example, the password modification was performed on a user. This means that user is the subject. Notice that the user is the subject because the activity was performed on a user, not because it was performed by a user.
Subject Example 3
Unix – Group Member Addition
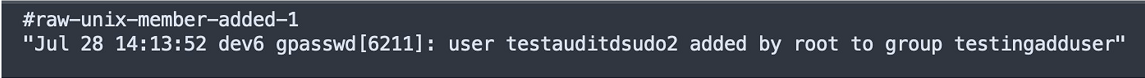
In this example, identifying the subject is less straight forward. From different perspectives, either the user or the group might serve as the subject. In this type of scenario, either refer to the common information model structure to find a similar case or identify which entity is the most manipulated. In this example, the group is the logical subject because it's the entity being modified. The user is a passive entity in this activity.
Tips for Unique Subject Cases
In network events, the subject is the
network protocol, or simplynetworkif a protocol is not specified.In authorization and login events, the subject is the target of the identification attempt, usually an
endpointor anapp.Some landscapes double as subjects, such as
endpoint,vpn, ordatabase.If you're unsure of the subject, leverage the common information model structure to your advantage. Try to find a similar event already defined in the information model. To validate your selection, check the predefined subjects in the Subject Interface of the Common Information Model Library.
