- Welcome to Exabeam Security Content
- What is Security Content?
- Common Information Model
- What is the Common Information Model?
- Common Information Model Context Elements
- Common Information Model Interface
- Common Information Model Event-naming Format
- Common Information Model Impact on Downstream Processes
- Using the Common Information Model to Create Custom Content
- Transitioning to the Common Information Model
- Understanding the Log
- Exabeam Parsers
- Exabeam Event Building
- Exabeam Enrichment
- Exabeam Persistence and Templates
- Exabeam Models
- Exabeam Rules
The Security Content Pipeline
In the cloud-native environment, log data enters Exabeam through a set of collector services. The collected log data is then ingested by the Exabeam unified ingestion pipeline, where the logs are parsed, events are built, and contextual enrichment takes place. You can view and tune these activities in Log Stream.
On the other side of the unified ingestion pipeline, downstream Exabeam applications make use of the processed event data. In Advanced Analytics, the processed data is analyzed using statistical modeling that profiles user and asset behavior. Machine learning is applied to detect anomalous activity. In Search and Dashboard, the processed data is indexed into a structure that optimizes searching, visualization, and other forms of presentation. In Correlation Rules, the enriched event data is available for building correlation rules.
The sections below outline the path of security content through through the Exabeam environment. This pipeline, as shown in the image below, will serve as a framework for discussing security content functionality throughout this documentation.
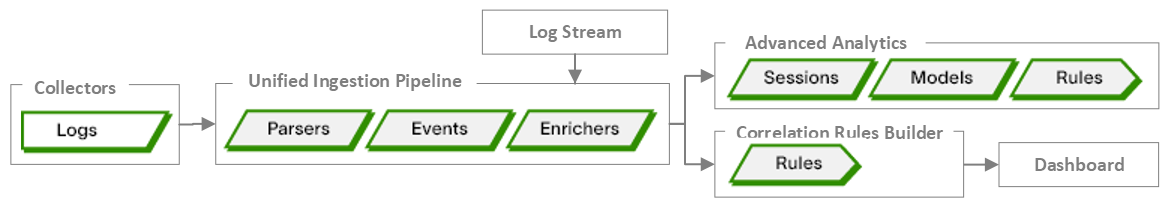
Logs – Data is collected in the form of log files from a variety of sources. Log data enters Exabeam through a set of collector services. These services collect data from servers, applications, databases, and other devices across an infrastructure, whether the source is local, remote, or cloud-based. Logs can be collected from on-premises sites (Site Collectors), third-party cloud vendors (Cloud Collectors), and from sources that provide contextual information, such as threat intelligence services and identity providers (Context Management). For more information. see Understanding the Log.
Parsers – In the unified ingestion pipeline, parsers are used to extract meaningful values from verbose log data. Log files are associated with specific parsers based on each parser's set of conditions. When a log meets parser conditions, a set of regular expressions (regexes) are used to extract values of interest from the log and map them to Exabeam fields. For more information, see Exabeam Parsers.
Events – In order for events to be created, each parser is matched to an event builder definition. When a parsed message is output from a parser, it runs through an event builder to be categorized as a specific event. The event becomes the key to further analysis. The framework of the Exabeam common information model determines the minimum required fields necessary for models and rules to process different types of events. For more information, see Exabeam Event Building.
Enrichers – Enrichers provide contextual information for an event. While most log information describes what users and entities are doing, context information describes who the users and entities are. Enrichers can add new values, modify values, or create new fields based on existing fields or on context tables. Enrichers can provide system-based or user-based context. For more information, and several enrichment use cases, see Exabeam Enrichment.
Sessions – Once events have been built and enriched, they must be added to a session in order for any analysis to take place. A session is the visual representation of all the events attributed to a user in the course of a workday. Before an event can be used to train a model, visualize a timeline, or trigger a rule, it must be part of a session.
Models – In Advanced Analytics, machine learning functionality models behavior at the user, peer group, entity, and organization levels. Once an event is part of a session, it's checked against the available user-based and asset-based models to determine if the event should be used for model training. When training begins, historical values are tracked so that anomalous behavior can be detected. For more information about the different types of models available, see Exabeam Models.
Rules – Rules contain the logical expressions that define malicious or unwanted behavior. When an event matches the conditions defined in a rule, the rule is triggered. Multiple types of rules are available, depending on the Exabeam product in use:
Advanced Analytics– When a rule is triggered, points are assigned to a user's session. Two types of rules are available. Model-based rules use historical values stored in a model and usually trigger when an event is evaluated as anomalous. Fact-based rules use field values from an event to determine whether or not to trigger. For more information and some sample rules, see Exabeam Rules.
Correlation Rules – Contains fact-based correlation rules that use field values from processed event data to determine whether or not to trigger. These correlation rules can be built from scratch or converted from search queries. For information about these rules, see the Correlation Rules Guide.
