- Welcome to Exabeam Security Content
- What is Security Content?
- Common Information Model
- What is the Common Information Model?
- Common Information Model Context Elements
- Common Information Model Interface
- Common Information Model Event-naming Format
- Common Information Model Impact on Downstream Processes
- Using the Common Information Model to Create Custom Content
- Transitioning to the Common Information Model
- Understanding the Log
- Exabeam Parsers
- Exabeam Event Building
- Exabeam Enrichment
- Exabeam Persistence and Templates
- Exabeam Models
- Exabeam Rules
Sample Log
Let's consider the sample log below and figure out what information of value it contains for parsing.
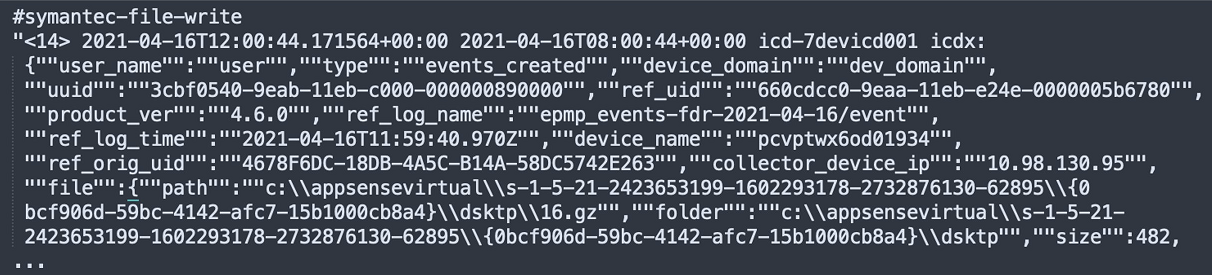
We can start by identifying the context elements contained in the sample log, as shown in the list below.
Subject =
fileActivity Type =
file-writeOutcome =
successVendor =
symantecProduct =
symantec siemProduct Category =
siemPlatform =
windowsLandscape =
endpoint
If we look up the file subject in the common information model, we see the following field designations:
"fields": {
"file_name": {
"core": "1",
"detection": "0",
"informational": "0"
},
"file_path": {
"core": "0",
"detection": "1",
"informational": "0"
},
"file_ext": {
"core": "0",
"detection": "1",
"informational": "0"
},
"file_dir": {
"core": "0",
"detection": "1",
"informational": "0"
}This indicates that for a log where the subject is file, the file_name is a required minimum field. The file_path, file_ext, and file_dir fields may be required for specific detection activities but are not necessarily required to parse the log. In the sample above, the file_name is 16 and is the only subject field required to parse the log.
If we look up the file-write activity type in the common information model, we see the following field designations:
"fields": {
"is_dok": {
"core": "0",
"detection": "1",
"informational": "0"
}This indicates that there are no core fields required to parse a file-write activity. However the is_dok field may be necessary for certain detection capabilities.
