- Welcome to Exabeam Security Content
- What is Security Content?
- Common Information Model
- What is the Common Information Model?
- Common Information Model Context Elements
- Common Information Model Interface
- Common Information Model Event-naming Format
- Common Information Model Impact on Downstream Processes
- Using the Common Information Model to Create Custom Content
- Transitioning to the Common Information Model
- Understanding the Log
- Exabeam Parsers
- Exabeam Event Building
- Exabeam Enrichment
- Exabeam Persistence and Templates
- Exabeam Models
- Exabeam Rules
Exabeam Rules
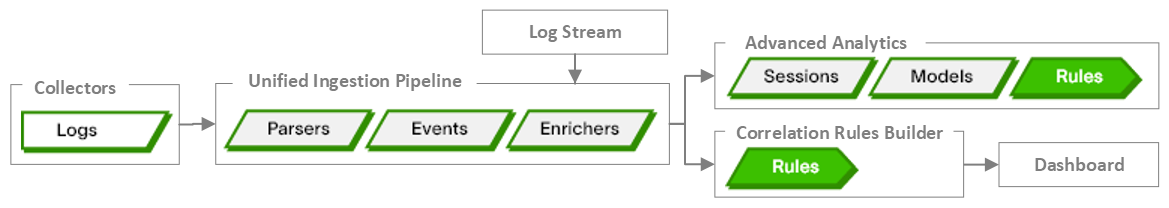
Once a log has passed through the unified ingestion pipeline, where event building and enrichment have been completed, the log becomes available for evaluation against a set of rules. Rules contain the logical expressions that define unwanted or malicious behavior, or behavior you want to be alerted on.
Depending on the Exabeam applications in use, different types of rules are available:
Advanced Analytics– In this on-premises and legacy SaaS application, both fact-based rules and model-based rules are available. Each rule includes a
RuleExpressionattribute that contains the conditions under which the rule should trigger. These rules can generate alerts and can provide scoring so that points are added to session timelines. For overview information about working with rules in Advanced Analytics, see Types of Rules and Create Rules. For information about the attributes contained in Advanced Analytics rules, see the table in Rule Attributes.Note that before any rules can begin to evaluate parsed and enriched logs for Advanced Analytics, an event selection statement must be in place. The logic contained in the event selection statement helps to define which events should be passed to Advanced Analytics for analysis. For information about creating and editing these statements, see the Event Selection Guide.
Correlation Rules – In this cloud-native application, fact-based correlation rules are available. These correlation rules can be built from scratch or converted from search queries. These rules can trigger various alerting outcomes. For information about these rules, see the Correlation Rules Guide.
