- Welcome to Exabeam Security Content
- What is Security Content?
- Common Information Model
- What is the Common Information Model?
- Common Information Model Context Elements
- Common Information Model Interface
- Common Information Model Event-naming Format
- Common Information Model Impact on Downstream Processes
- Using the Common Information Model to Create Custom Content
- Transitioning to the Common Information Model
- Understanding the Log
- Exabeam Parsers
- Exabeam Event Building
- Exabeam Enrichment
- Exabeam Persistence and Templates
- Exabeam Models
- Exabeam Rules
Understanding the Log
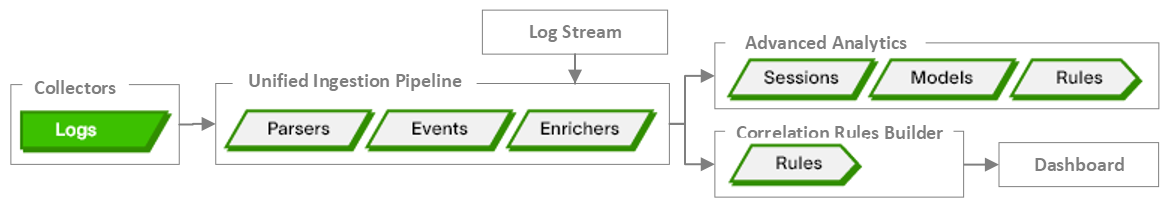
Data is collected in the form of log files from a variety of sources. Log files provide insight into the behavior of both users and entities (like servers and workstations) across your enterprise and they help surface security issues across your enterprise.
Log data enters Exabeam through a set of collector services. These services collect data from servers, applications, databases, and other devices across an infrastructure, whether the source is local, remote, or cloud-based. Logs can be collected from on-premises sites (Site Collectors) or from third-party cloud vendors (Cloud Collectors).
The data in the log files can be enriched by the collection data from contextual sources (Context Management). Context data comes from external systems such as identity services, configuration management databases, or HR management systems. Context data can also be collected from threat intelligence feeds. While the log data provides information about what the users and entities are doing in the system, the context data provides information about who the users and entities are.
Once logs have been collected, they can be parsed. A parser extracts values from a log and maps those values to the appropriate Exabeam fields. See Exabeam Parsers for more information. The following topics discuss how log data is parsed to identify values of interest:
