Threat Center Features Introduced in 2024
November 2024
This release does not include new features for Threat Center.
October 2024
The following features were introduced in Threat Center in October 2024:
Feature | Description |
|---|---|
View All Rules in Rules Triggered Overview | You can now better identify all rules associated with a case or alert. In the Overview tab, under Rules Triggered > View all rules, you can now view all unique rules from which associated detections are created and the number of times a rule created associated detections. 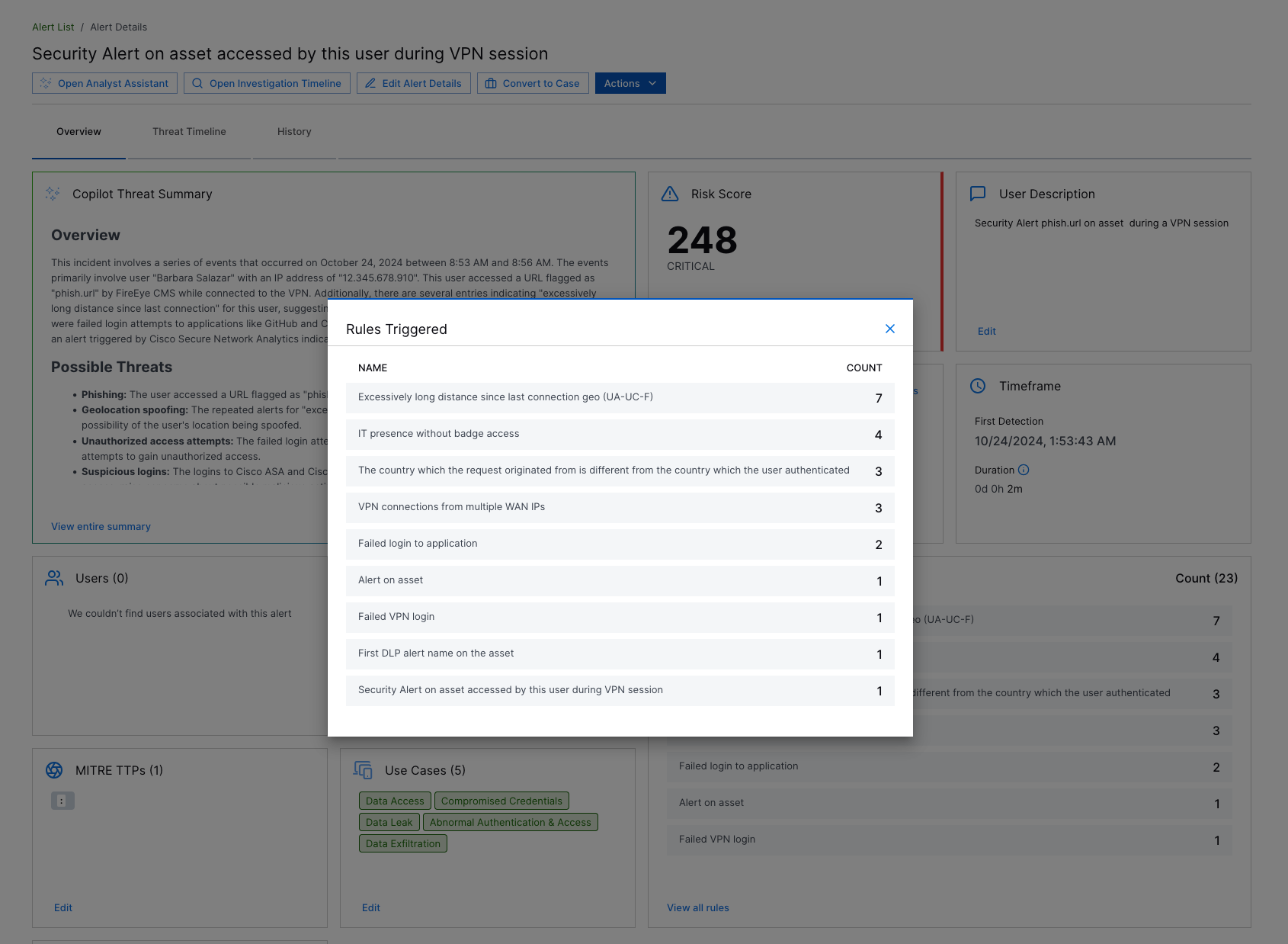 |
Copilot Threat Summary Streaming Text | To better show the AI at work, a new summary for the Copilot Threat Summary now appears progressively as it's generated. |
September 2024
This release does not include new features for Threat Center.
August 2024
This release does not include new features for Threat Center.
July 2024
This release does not include new features for Threat Center.
June 2024
The following features were introduced in Threat Center in June 2024:
Feature | Description |
|---|---|
Correlation Rule Details | To expedite your triage and investigation for correlation rules detections, you can now view correlation rule details directly in Threat Center under Rule Definition. |
May 2024
The following features were introduced in Threat Center in May 2024:
Feature | Description |
|---|---|
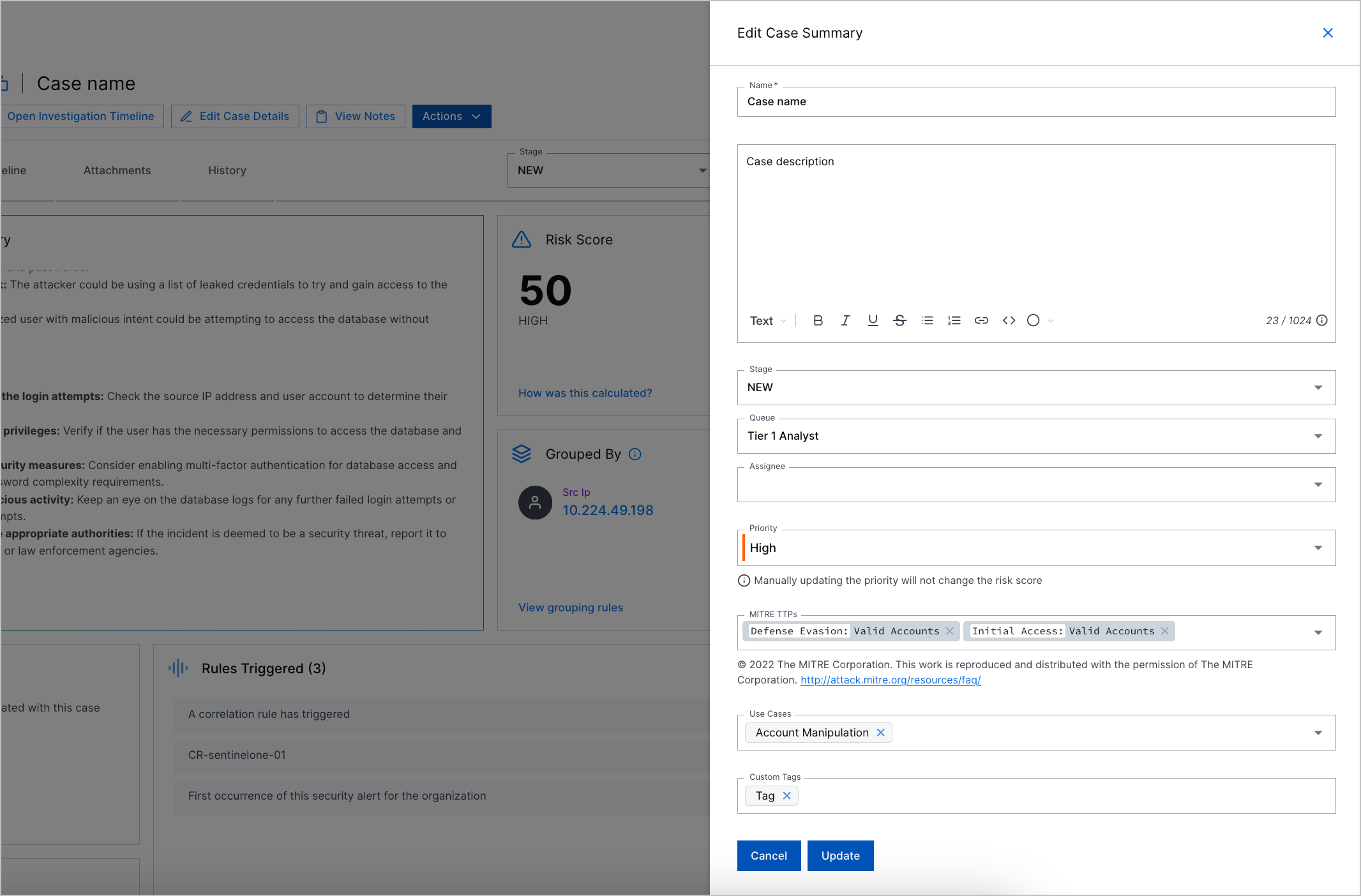
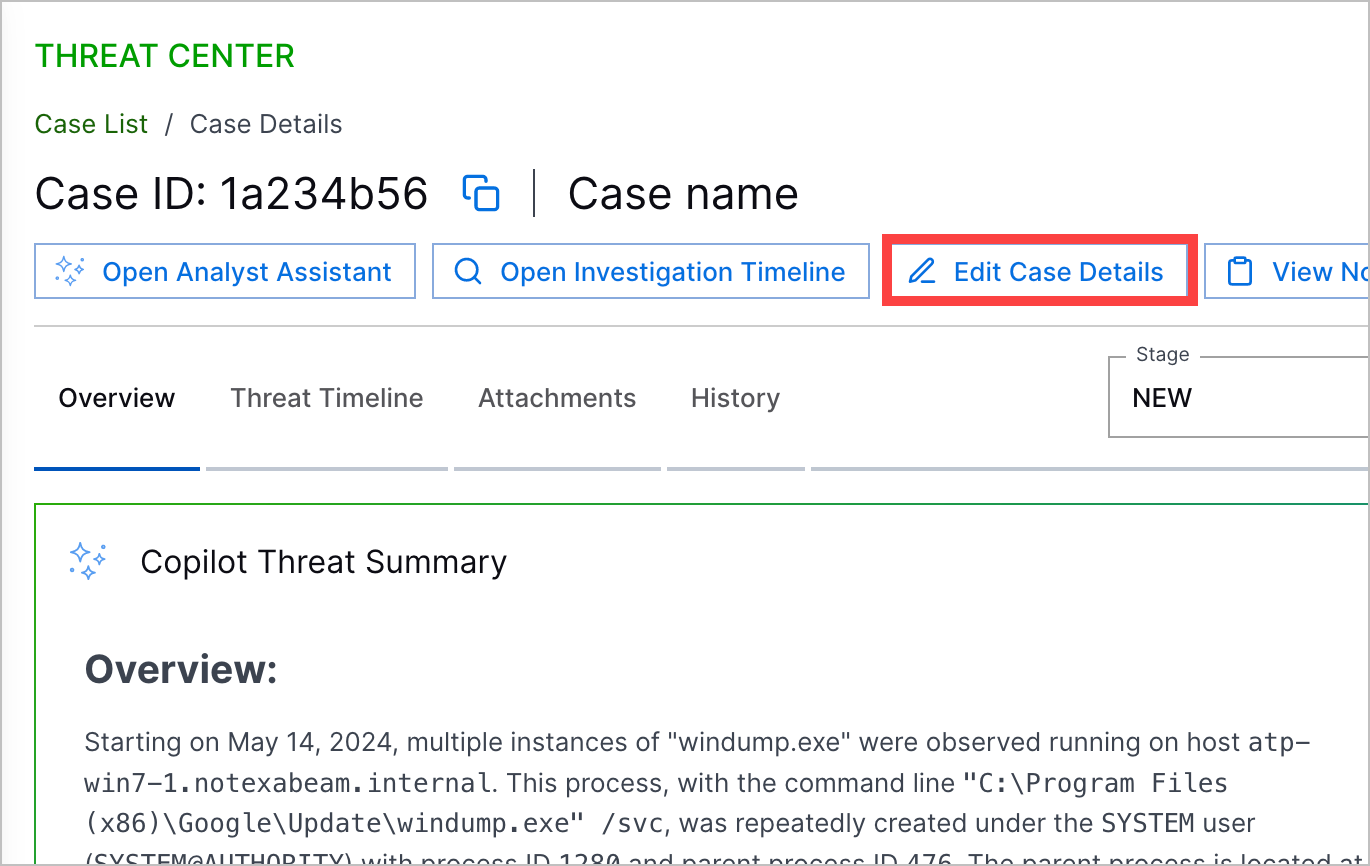
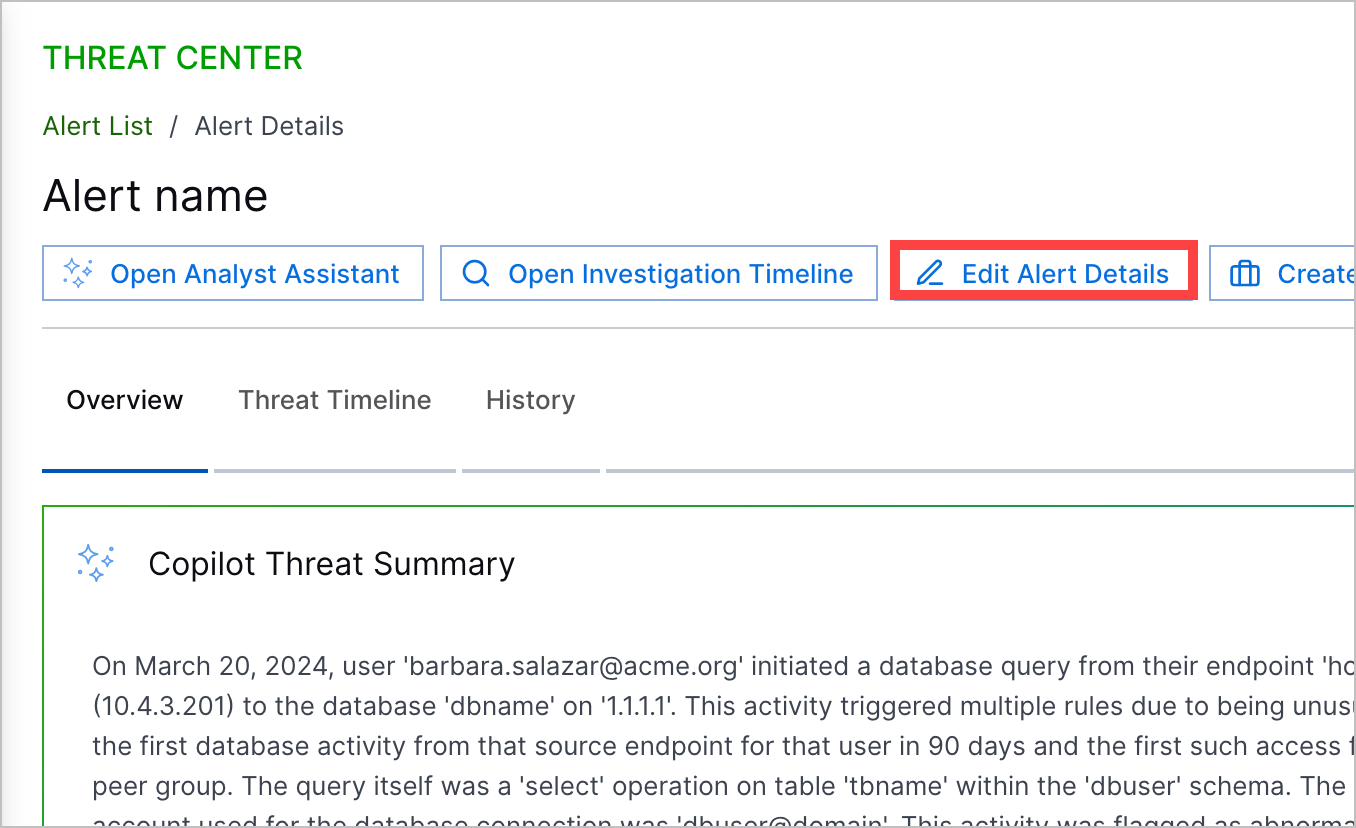
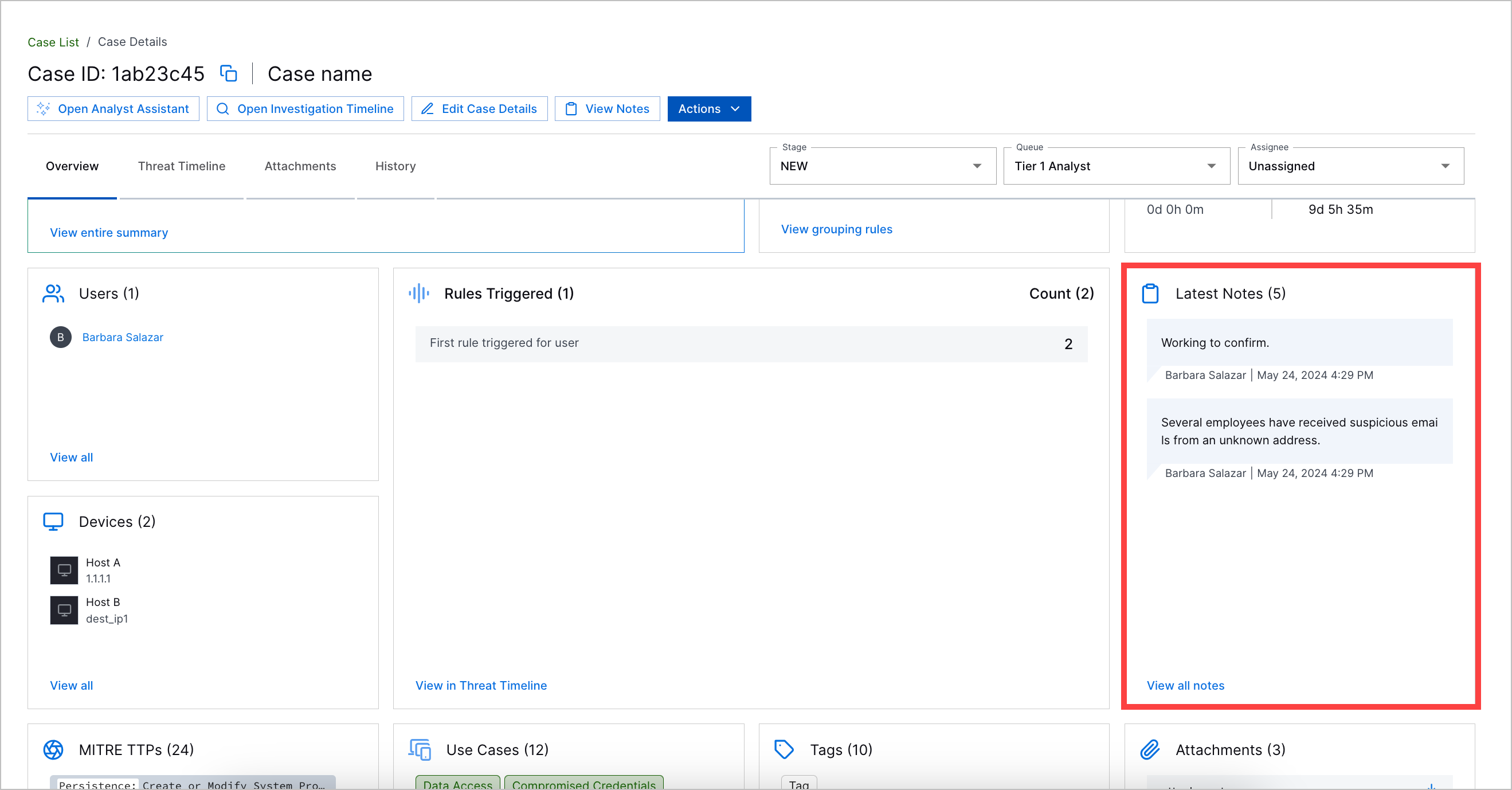
Case and Alert Overview | To understand the nature of a case or alert, you can now get an overview of core case or alert information in the Overview tab. Core information displayed include the Copilot Threat Summary, case or alert risk score, description, the attribute by which associated detections are grouped, and more. When you open a case or alert, the first thing you see is the Overview tab. The Threat Timeline is now in a separate Threat Timeline tab. 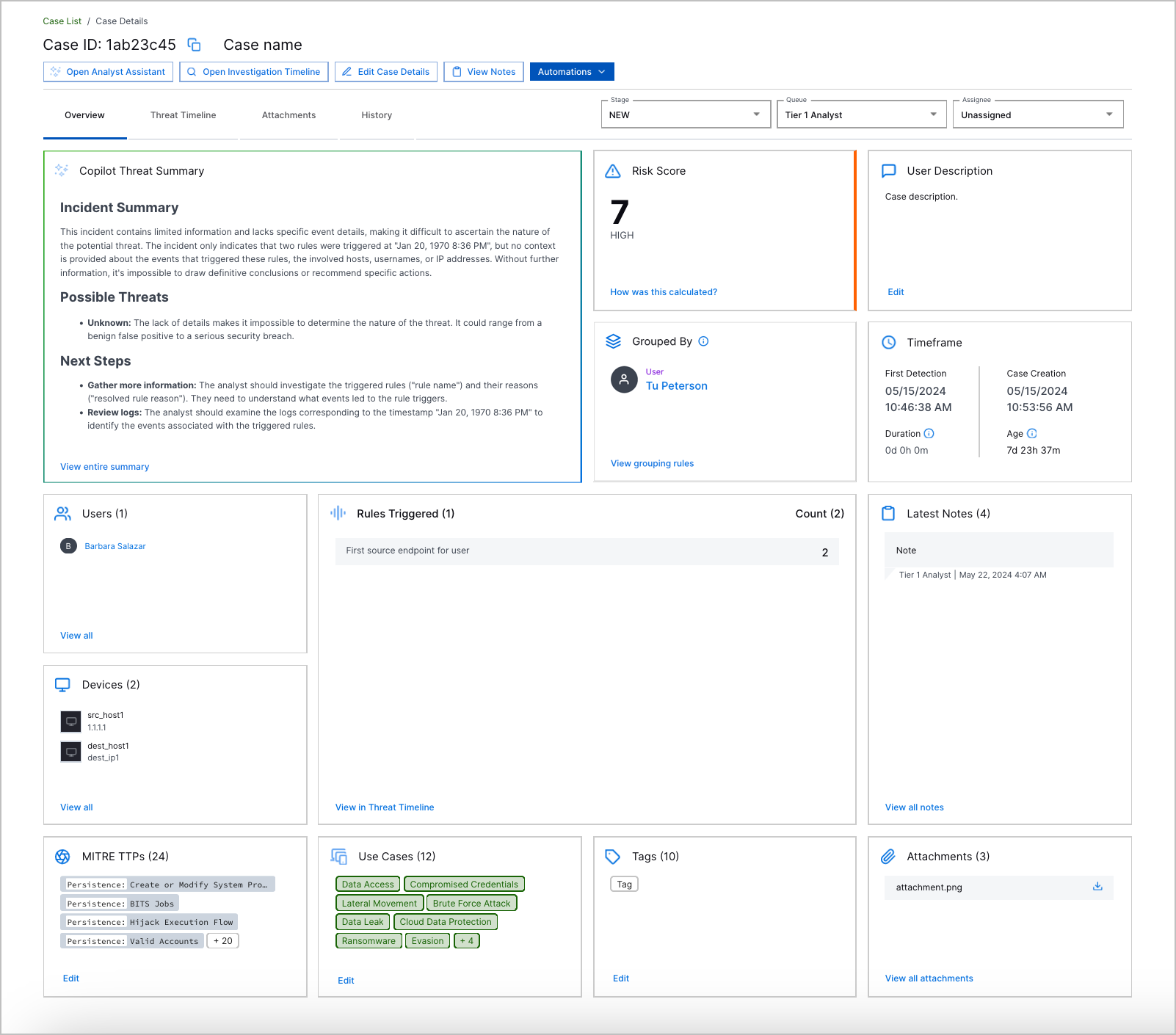 |
New Attribute Updating Experience | With the new attribute updating experience, you can now:
|
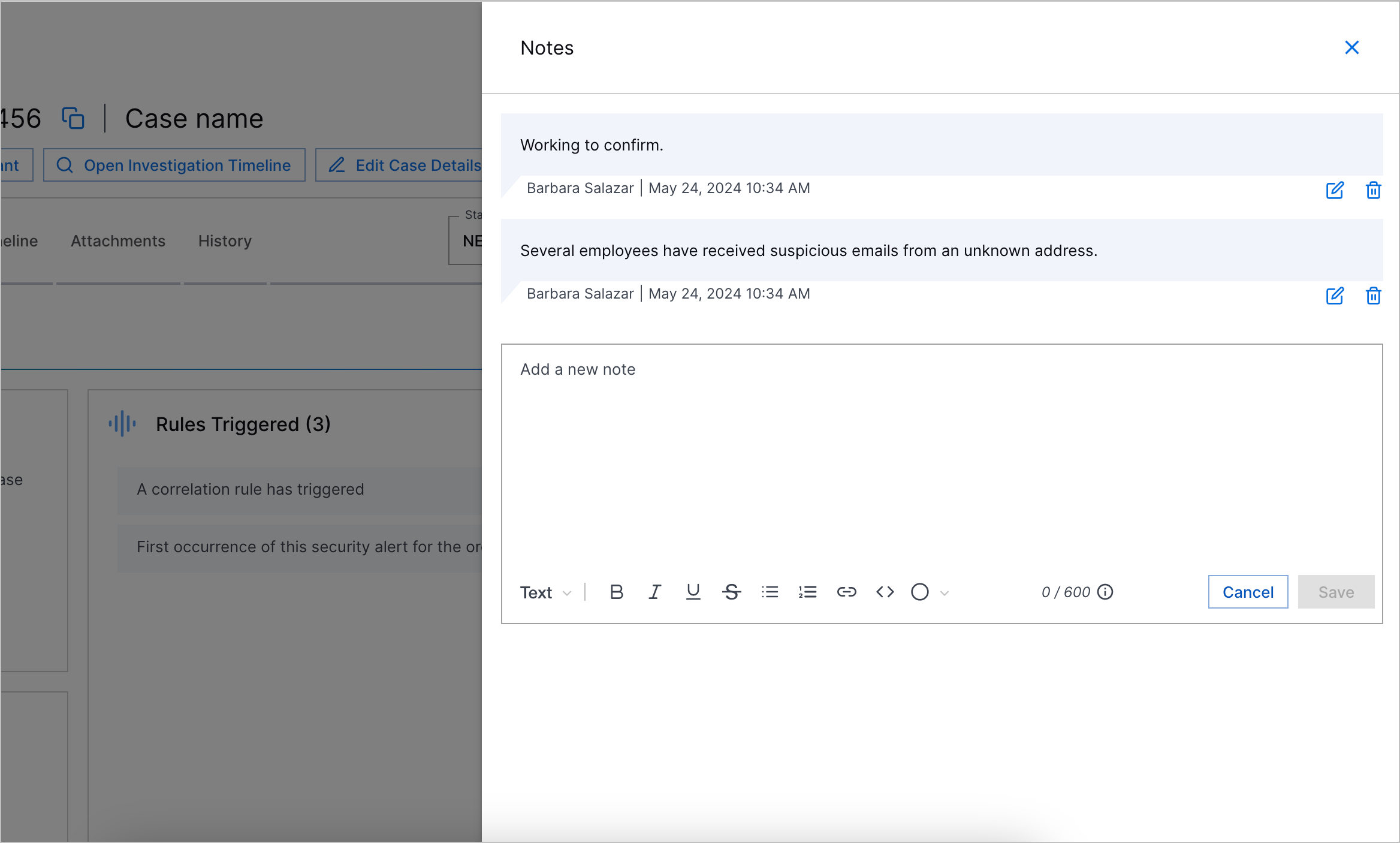
New Case Notes Experience | With the new case notes experience, you can now: |
Search Timeline View Navigation | To deepen your triage or investigation, you can now navigate directly to the Search timeline from a case or alert to view all events associated with grouped detections using the Open Investigation Timeline button. Search opens in the timeline view and queries for events with the attribute by which the case or alert detections are grouped. 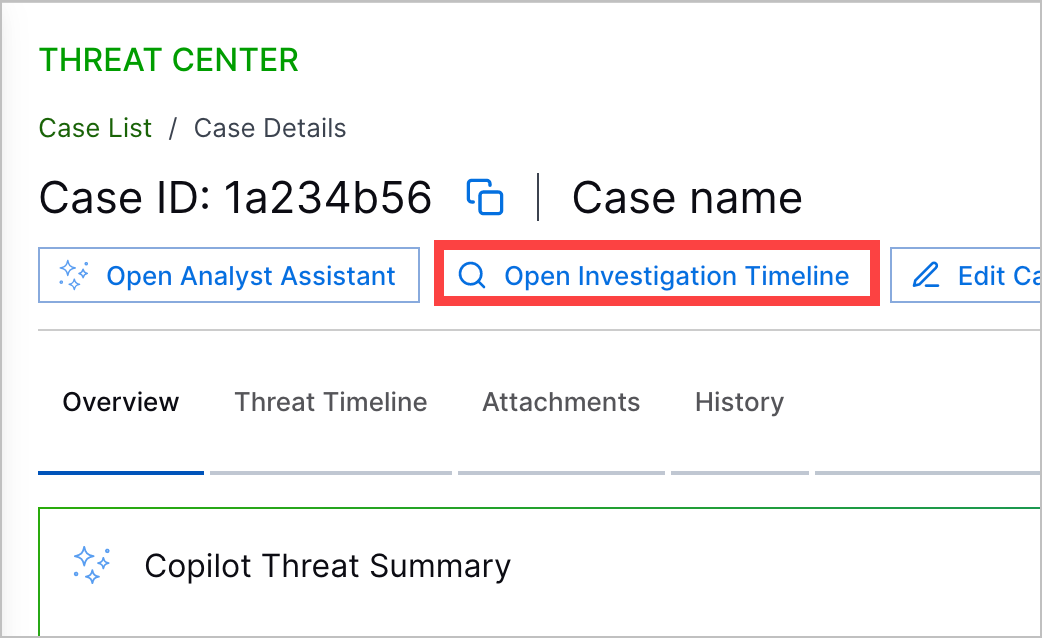 |
Case Closed Reason in Threat Center Global Notifications | To ensure notification recipients understand why a case was closed, the case closed reason is now included in the Case has been closed. global notification. |
Case Closed Reason in Individual Alert and Case Information Sharing | To ensure recipients understand why a case was closed, the case closed reason is now included in the emails and webhook messages you send when you share individual case or alert information. |
Search Bar Redesign | The improved search bar experience now extends to Threat Center. To more easily search for cases and alerts, you can now select from Basic, Advanced, and Natural Language search modes from a Search mode menu. The search bar displays each search mode differently. The search button and time range menu are now inside the search bar. 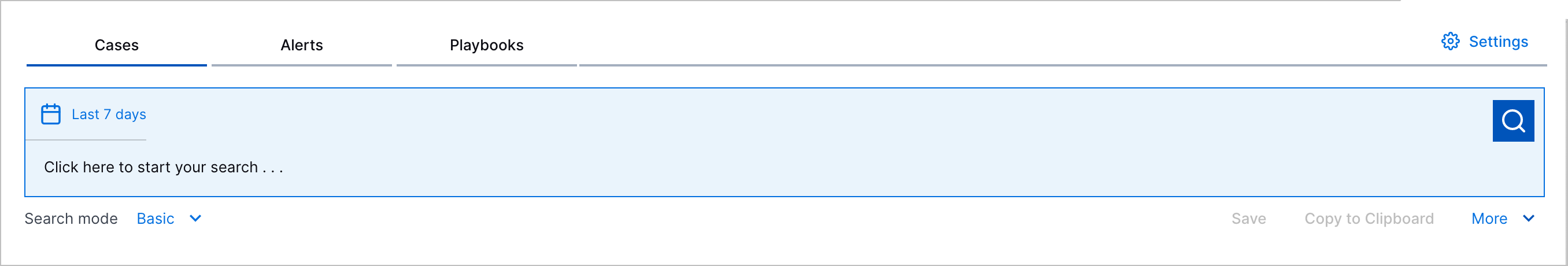 You can now also easily read search queries in Advanced search mode:
|
April 2024
The following features were introduced in Threat Center in April 2024:
Feature | Description |
|---|---|
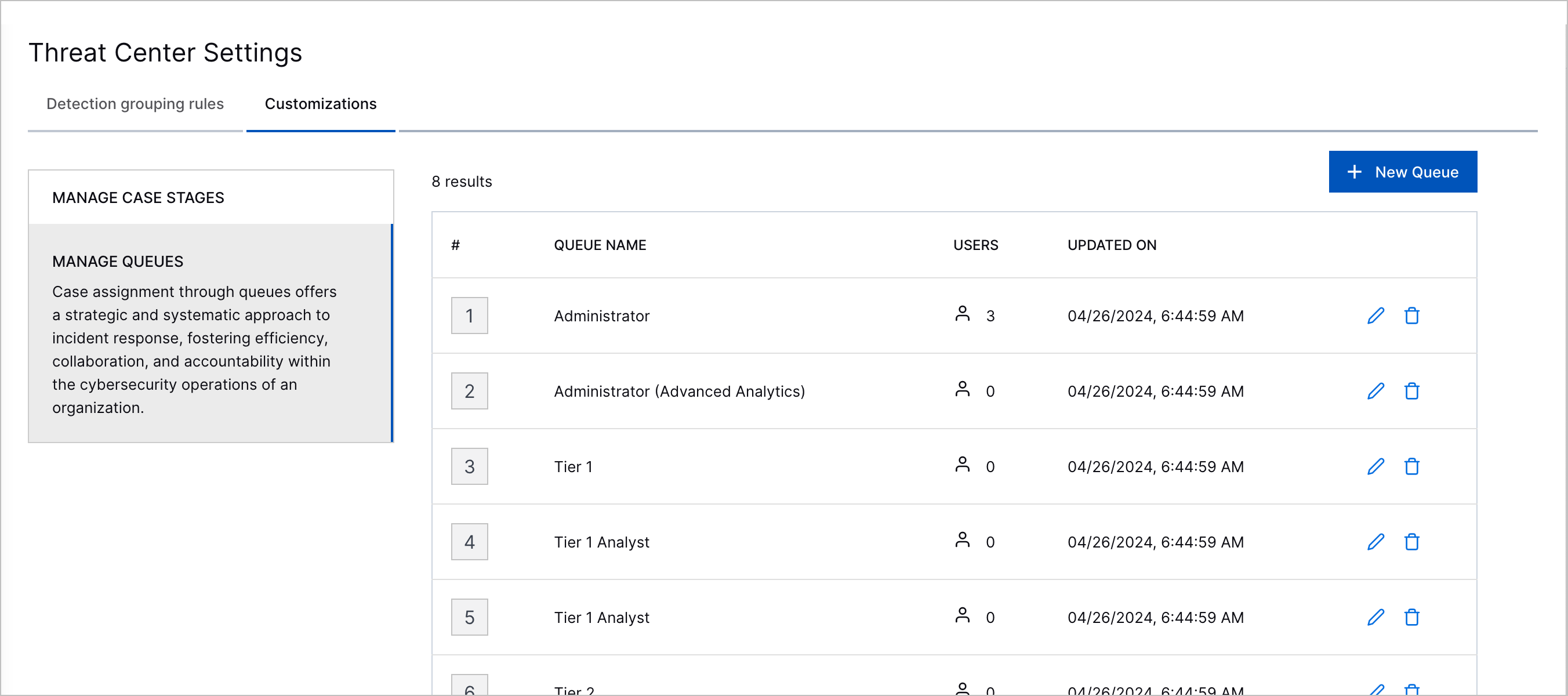
Custom Queues | You now have more flexibility in defining queues. With custom queues:
 |
Custom Case Stages | You can now better convey where you are in your case response with custom stages that reflect your organization's response workflow. For example, if your workflow requires you to isolate affected entities, you can create a custom stage called Containment. 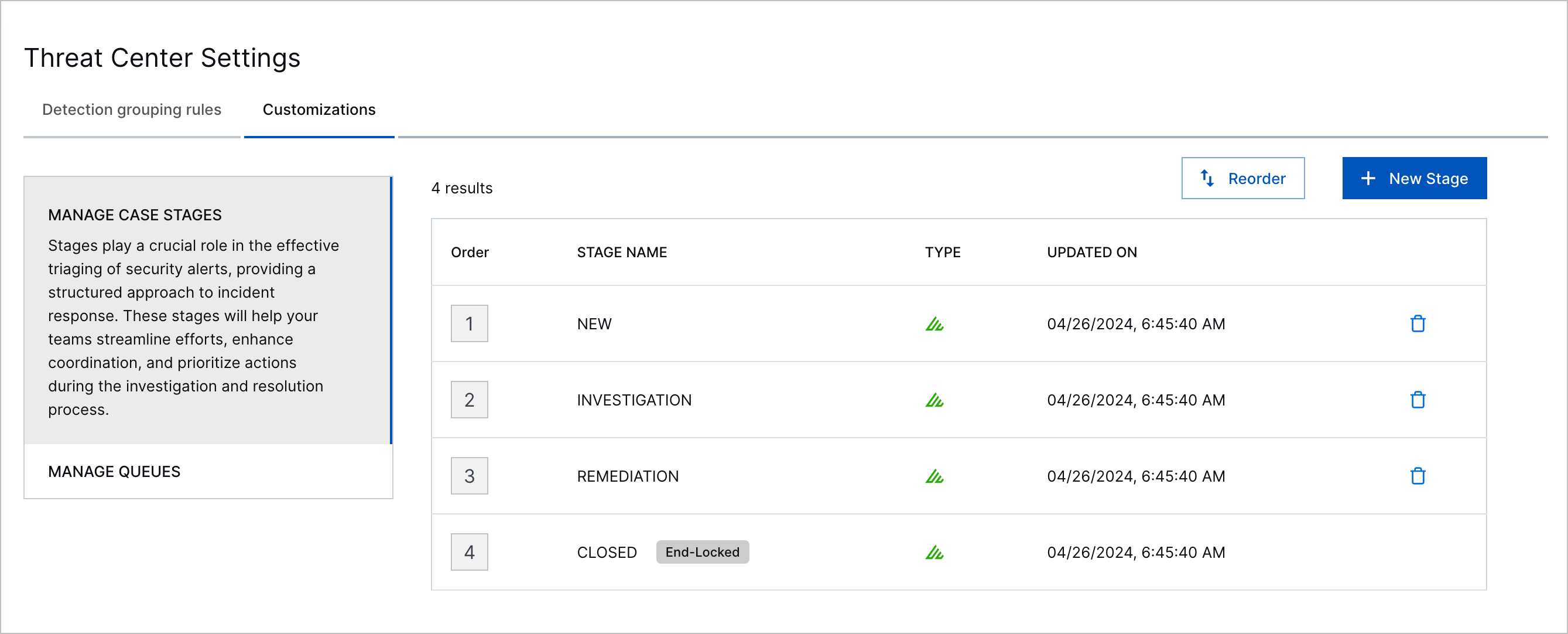 |
Copilot Natural Language Search | Copilot Natural Language Search now extends to Threat Center. To quickly create complex searches without knowing Exabeam Query Language, you can now enter a search prompt in natural language. After you enter your natural language search prompt, Threat Center uses AI to convert it into Exabeam Query Language syntax. 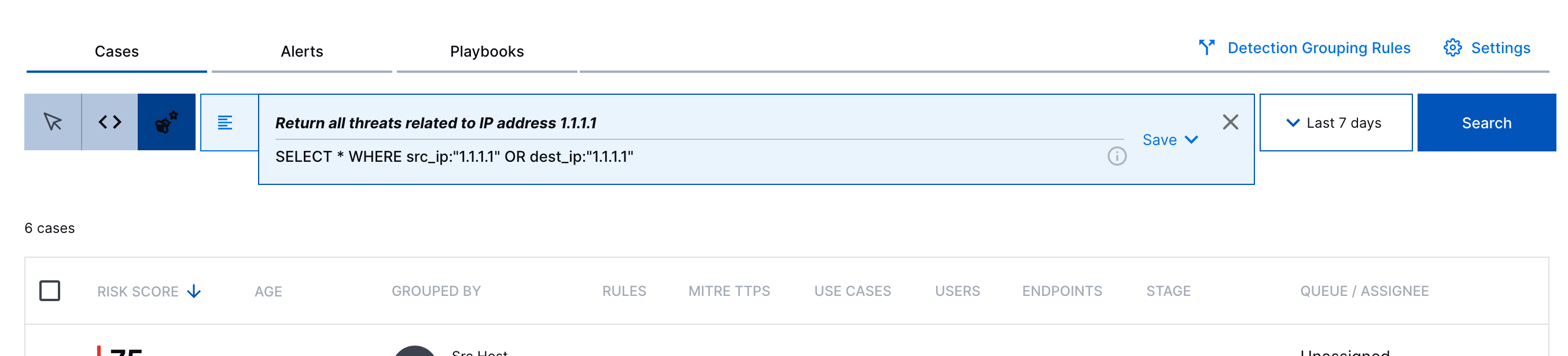 |
Copilot Threat Summary Enhancements | You can now view a more accurate overview of a case or alert with optimizations to the query sent to the language learning model. |
March 2024
The following features were introduced in Threat Center in March 2024:
Feature | Description |
|---|---|
Copilot Analyst Assistant | You can now quickly learn and get answers to questions about a case or alert using a security-trained AI assistant. Prompt Copilot Analyst Assistant with a message or query, and it interprets case or alert information to generate a natural language response. 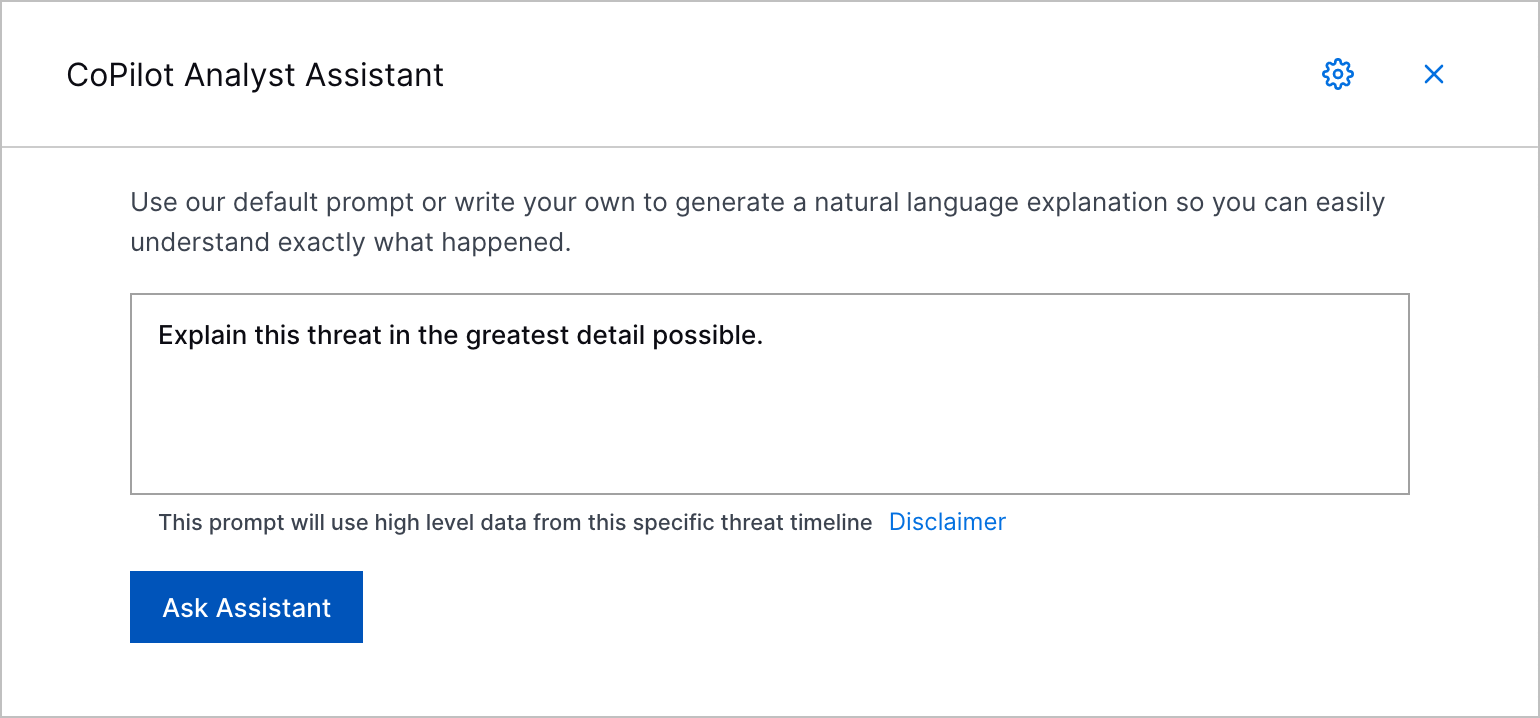 |
Copilot Threat Summary | To help you quickly make sense of a case or alert without reviewing all the details, you can now get an overview of a threat described in a case or alert with an AI-generated summary. In the Threat Timeline tab, Copilot Threat Summary uses case or alert information to summarize the case or alert and recommend next steps for addressing the case or alert. 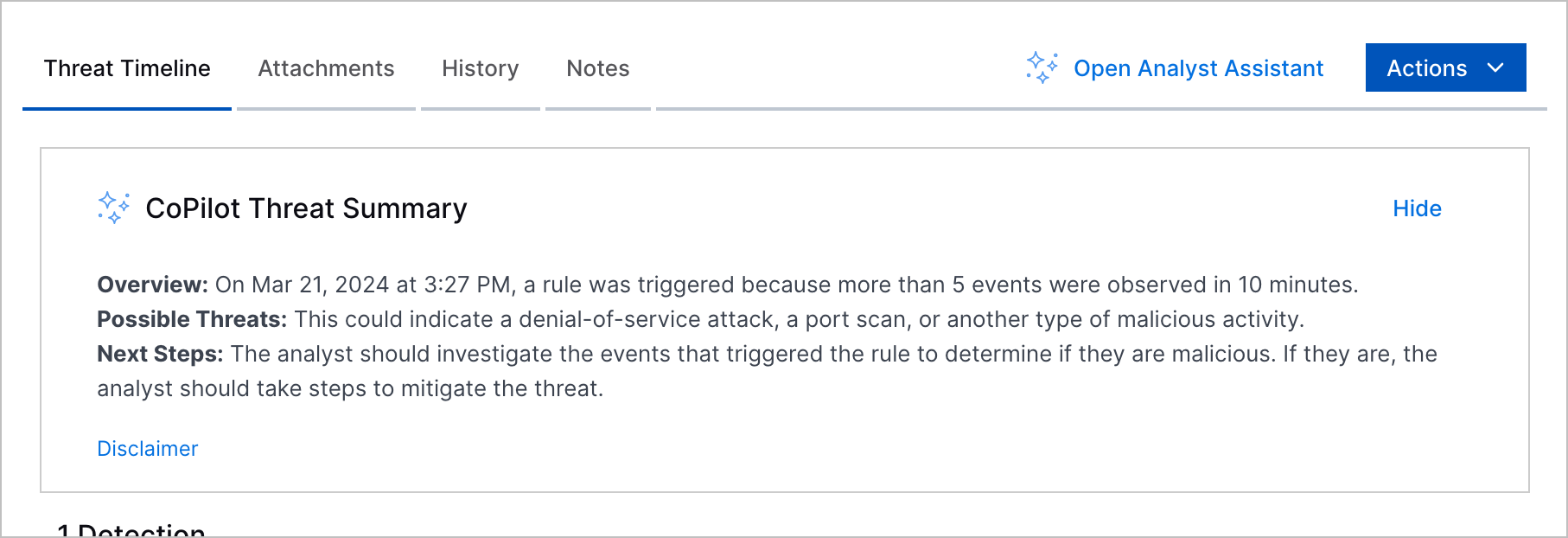 |
Data Retention Changes | You can now access 365 days of data, including case and alert attributes, detections and related events, case notes, attachments, and case and alert history, by default. |
Case Closed Reason | You can now ensure everyone working on a case understands why a case was closed. When you change the case stage to Closed, you must document why you're closing the case. 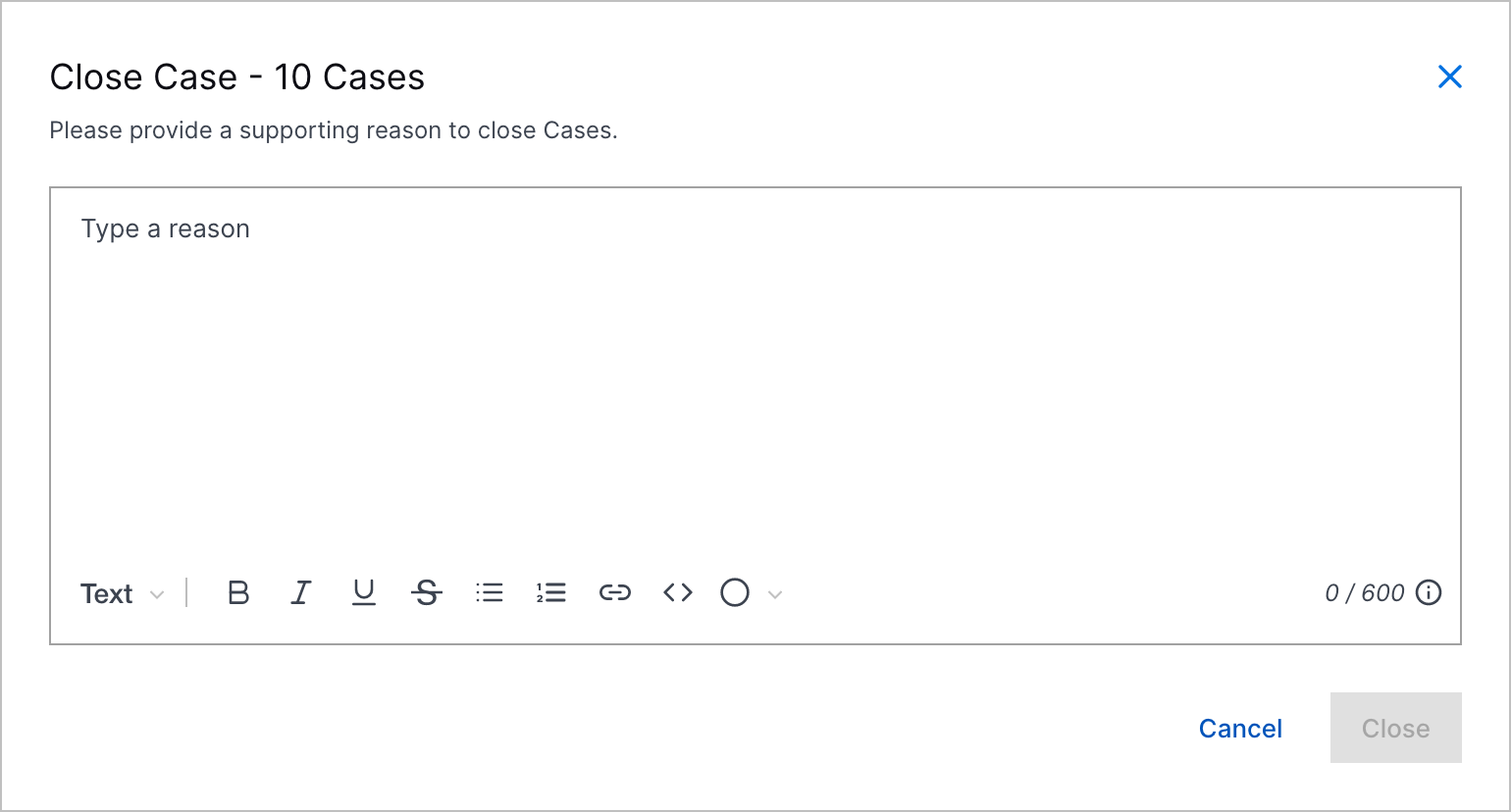 |
Case and Alert Deletion | To clear out obsolete cases and alerts, you can now delete cases and alerts. 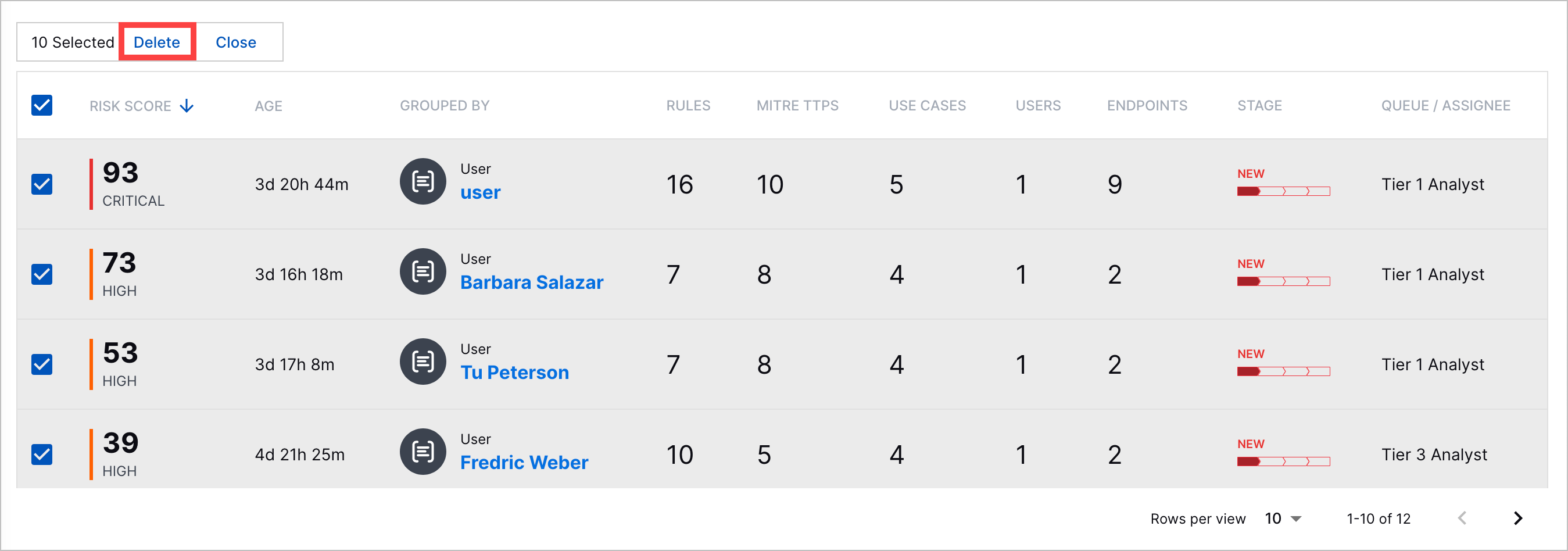 |
Bulk Case Close | You can now quickly close multiple cases at once. 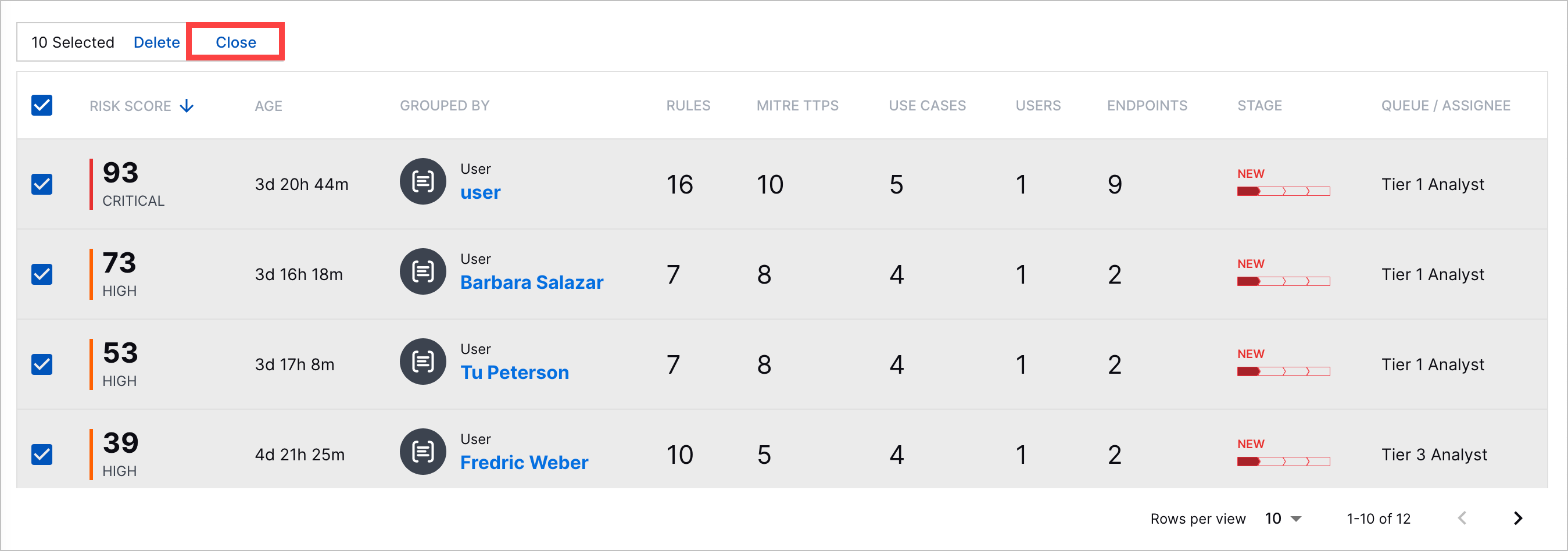 |
Case and Alert History Enhancements | You can now track relevant detection grouping and Automation Management activity in the case or alert history. You can now see when a detection grouping rule adds a detection to a case or alert and when an Automation Management playbook executes an action that affects a case or alert. 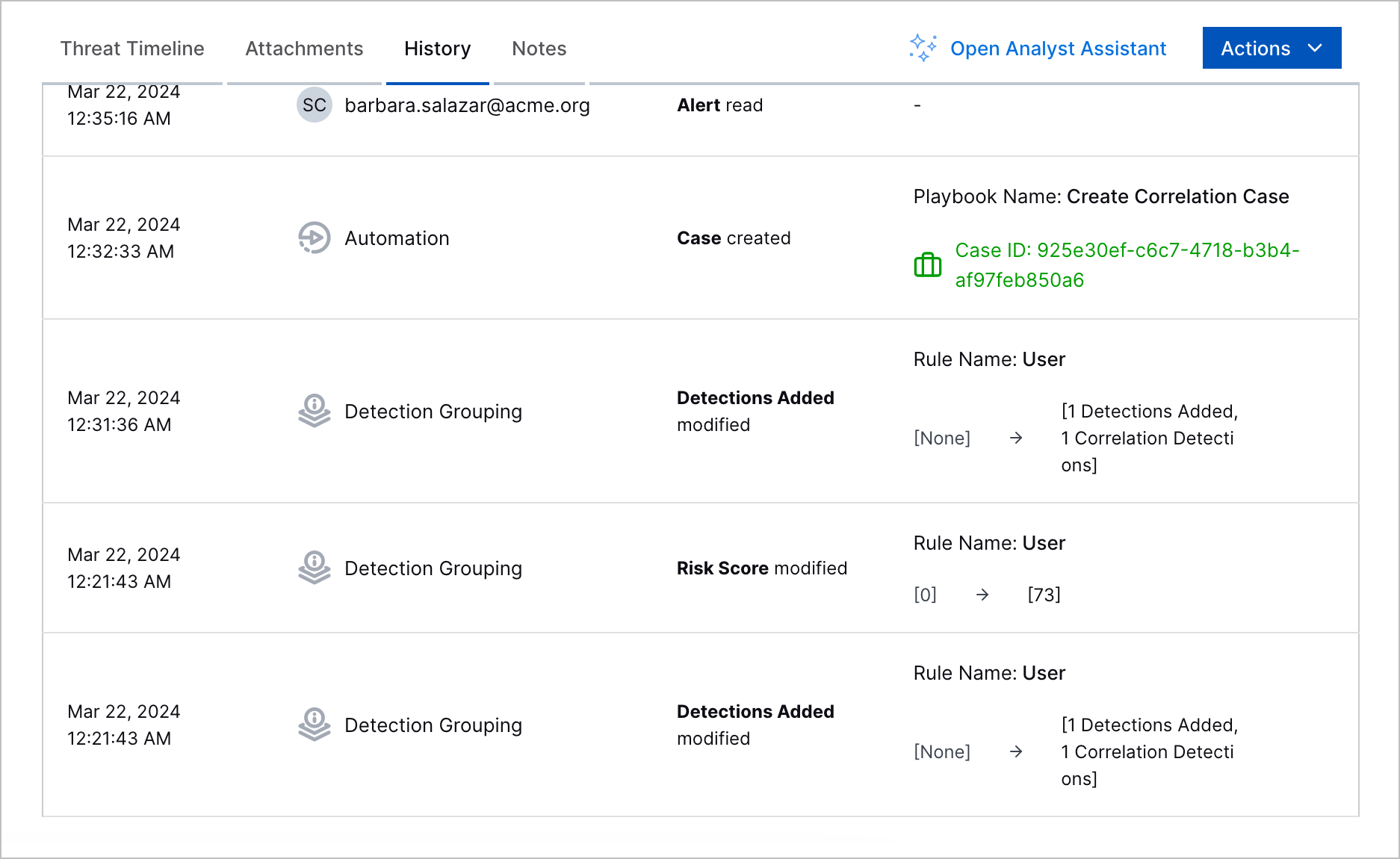 |
Detection Grouping Rule History | You can now track changes made to a detection grouping rule. In the detection grouping rule history, see what changes were made, who made the change, and when the change was made. 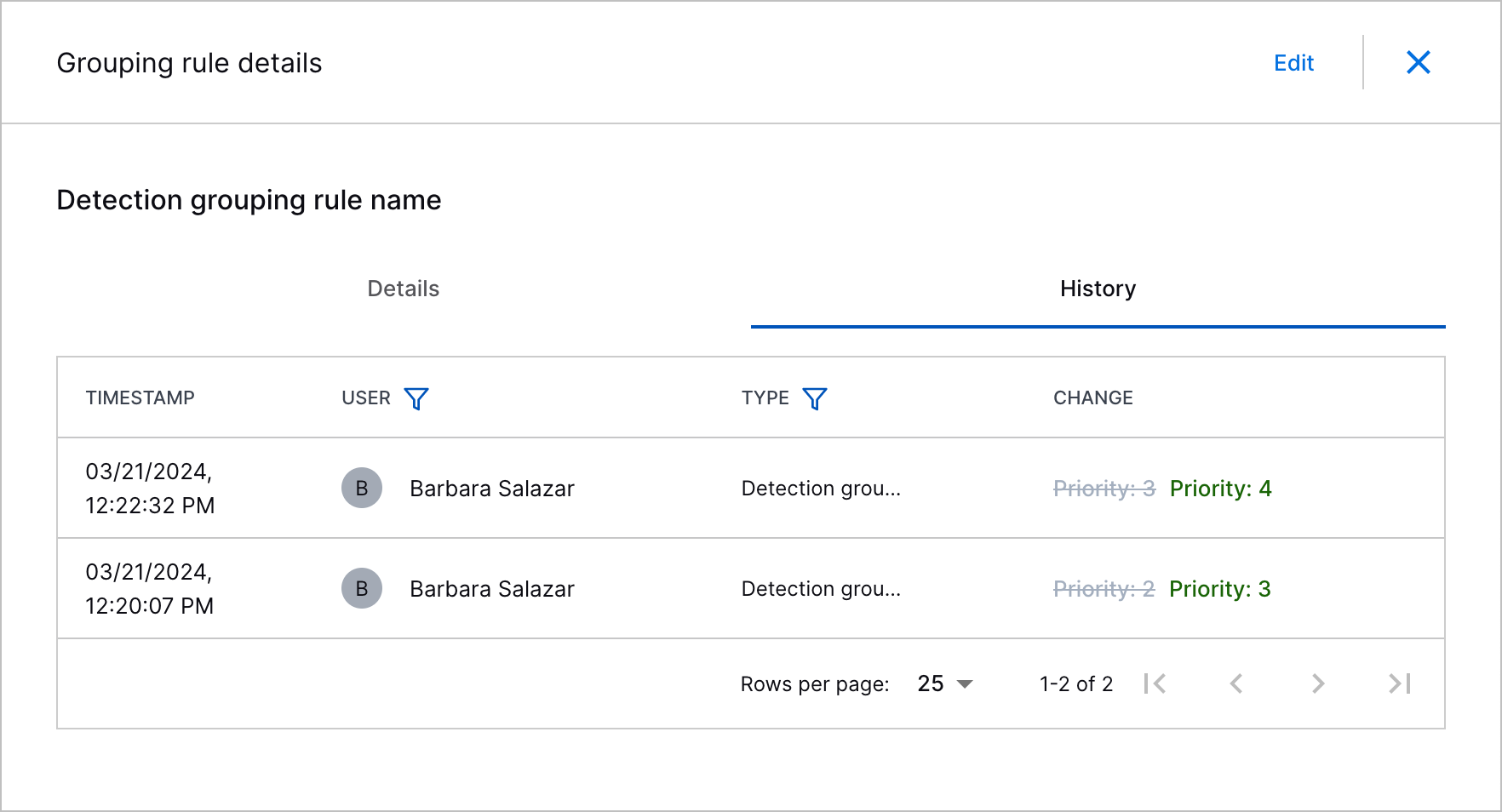 |
Advanced Analytics Detections | If you have an Exabeam Fusion license, you can now investigate triggered Advanced Analytics rules in Threat Center as detections. |
February 2024
The following features were introduced in Threat Center in February 2024:
Feature | Description | |
|---|---|---|
Threat Center Renaming | Alert and Case Management is now renamed Threat Center. | |
Detection Grouping Rules | You can now ensure alerts and cases contain all relevant evidence with detection grouping rules. By default, detections are grouped according to six pre-built detection grouping rules. You can also create your own detection grouping rules. | |
Threat Center Notifications | You can now automatically get notified about important alert and case changes. You can send notifications to Microsoft Teams or Slack using global notifications settings or to email addresses or webhooks using an Automation Management playbook. | |
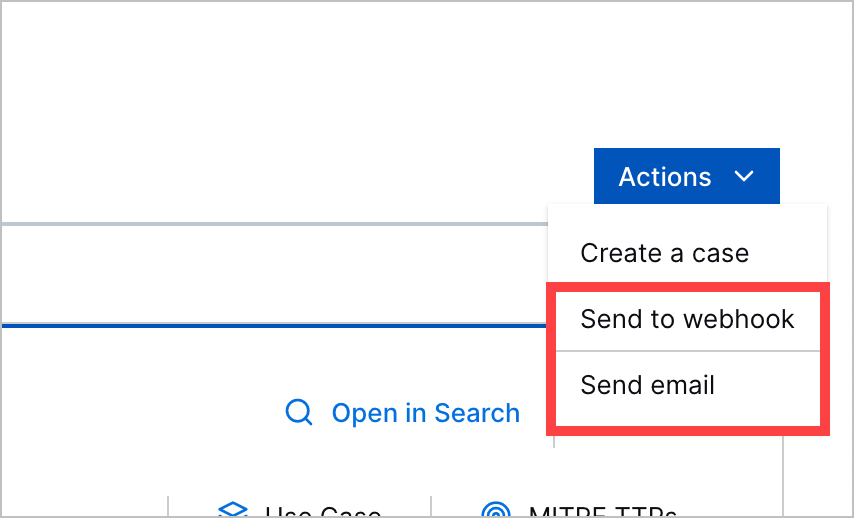
Individual Alert and Case Information Sharing | You can now share alert or case information with third-party systems or people who can't access Threat Center. You can send alert or case information directly from that alert or case to an email address or webhook.
| |
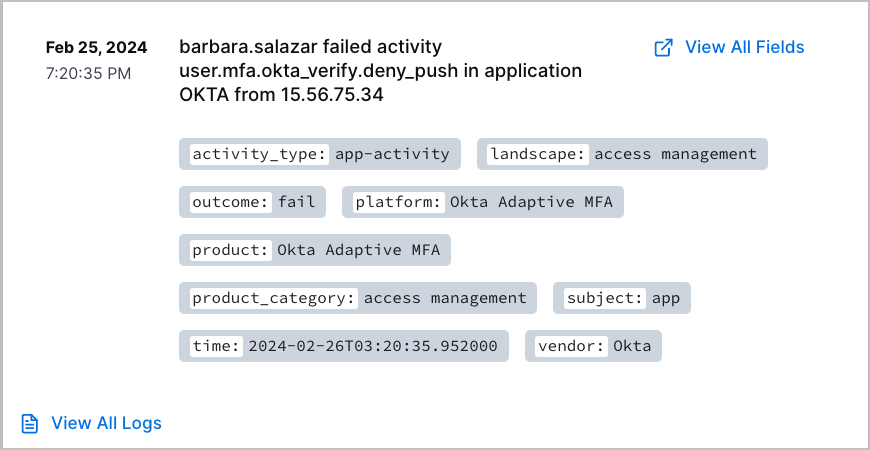
Detection Summary Titles | You can now quickly understand the threat a detection represents using the detection title. The detection title now summarizes and describes the risky activity it represents in a single sentence.
| |
Condensed User and Endpoint Summaries | You can now better understand which users and endpoints are associated with a case or alert. In a case or alert summary, related host names and IP addresses are now displayed as one endpoint, and related user names and email addresses are now displayed as one user.
|
January 2024
This release does not include new features for Alert and Case Management.