Threat Center Features Introduced in 2025
June 2025
This release does not include new features for Threat Center.
May 2025
The following features were introduced in Threat Center in May 2025:
Feature | Description | |||
|---|---|---|---|---|
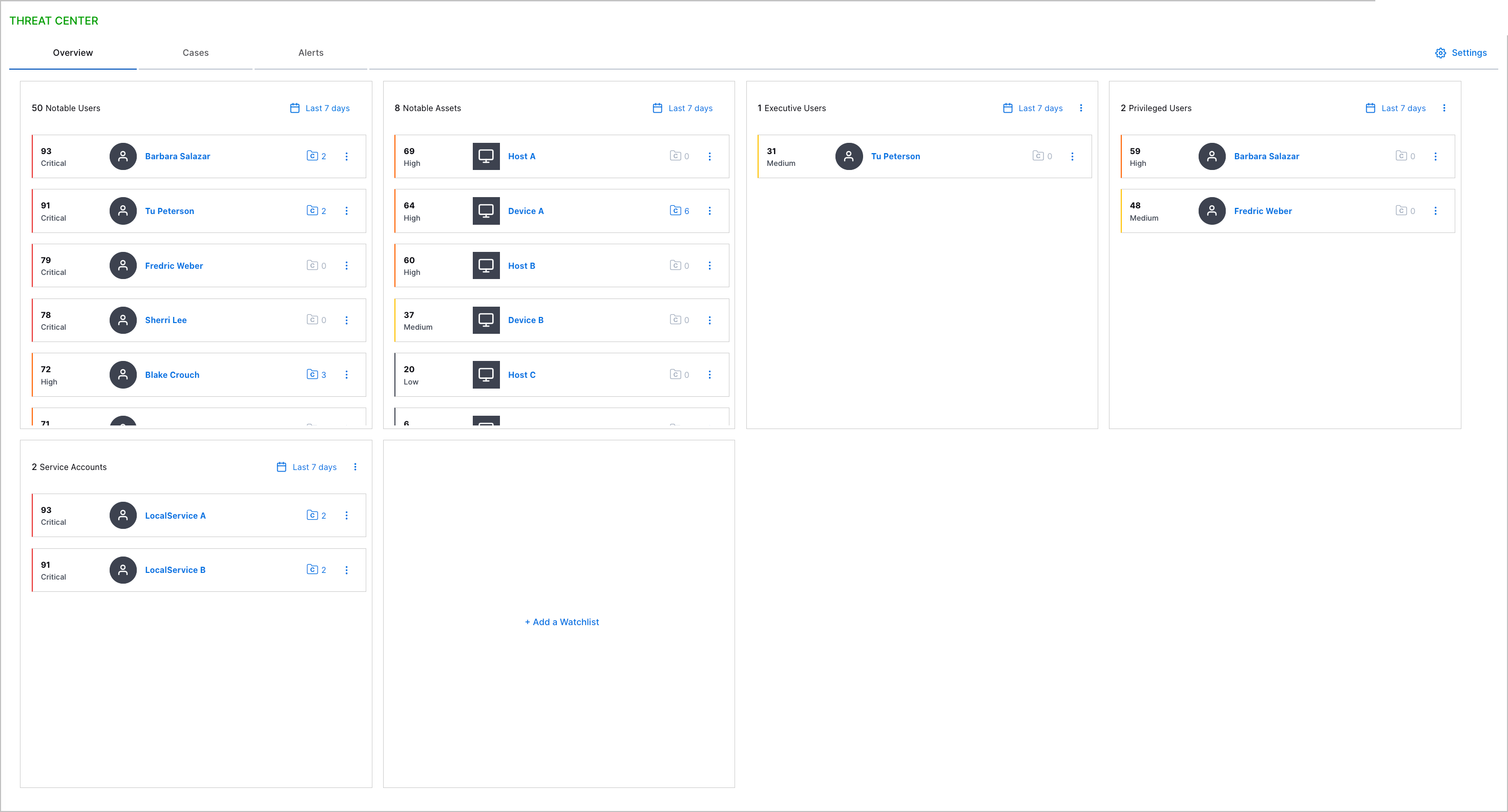
Watchlists | You can now monitor and quickly get an overview of entities of interest using watchlists.
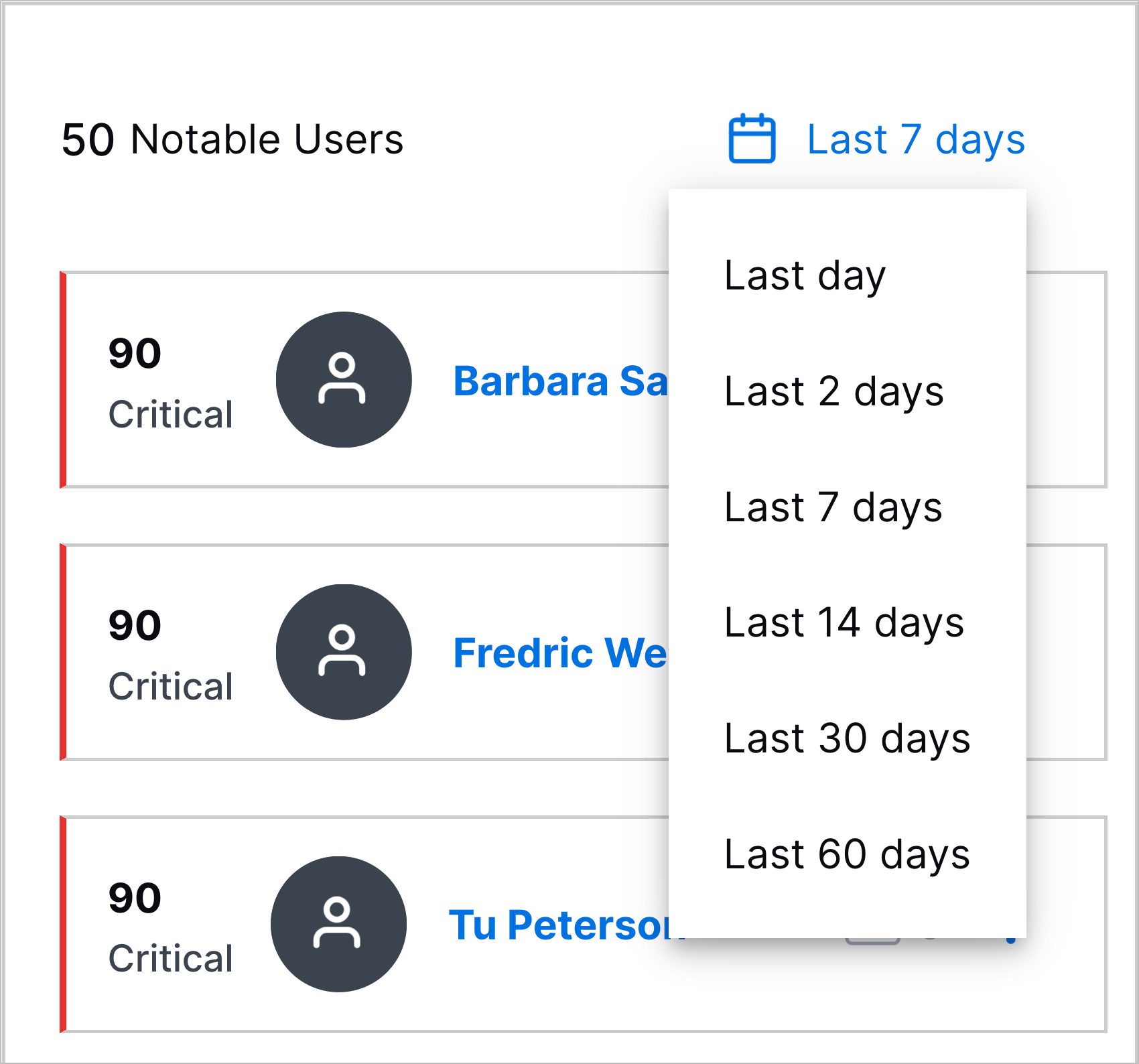
Watchlists dynamically rank entities from highest to lowest risk score over a time frame you specify: the past day, two days, seven days, 14 days, 30 days, or 60 days.
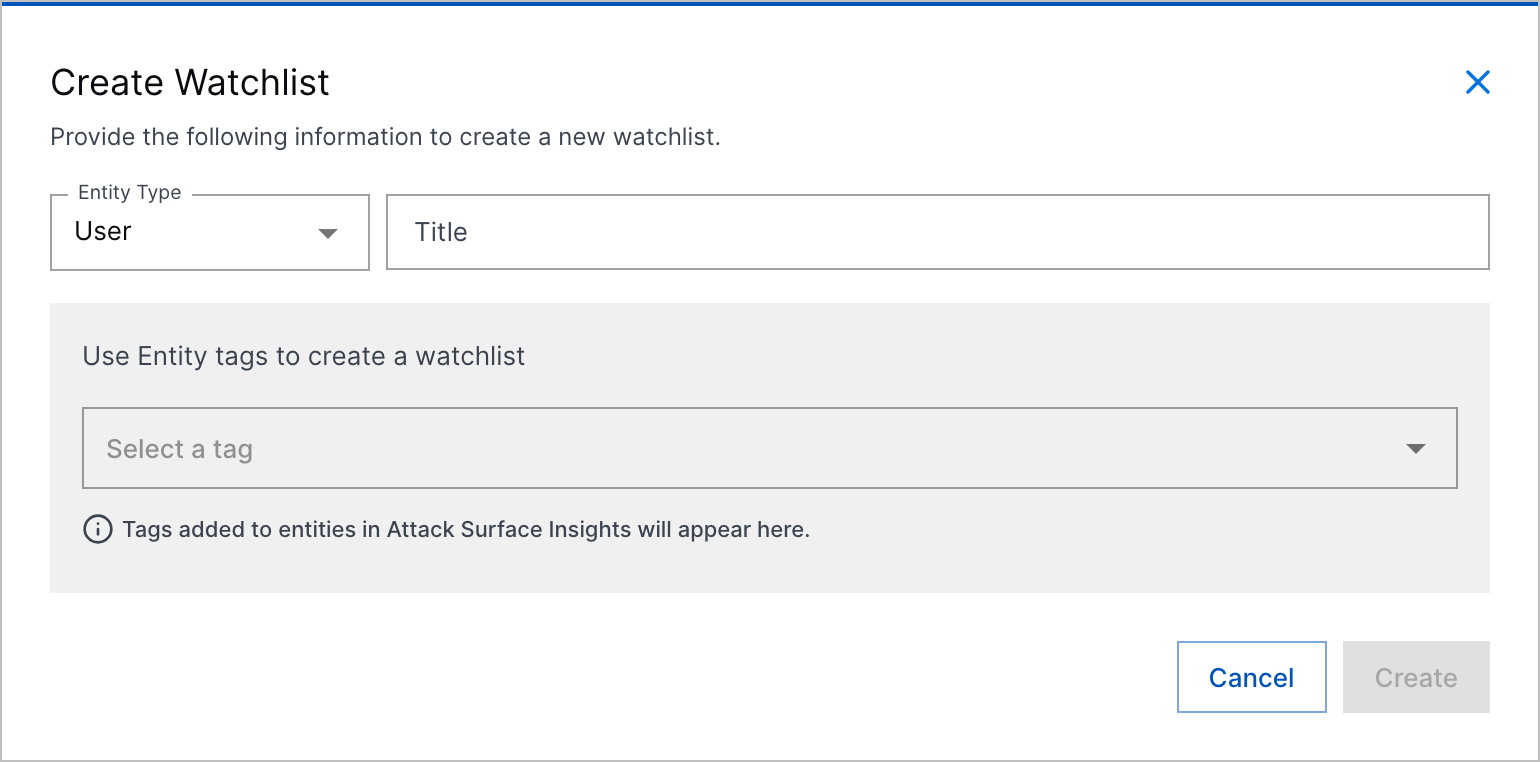
There are five pre-built watchlists for notable users, notable assets, executive users, privileged users, and service accounts. You can also create your custom watchlists based on tags applied to entities in Attack Surface Insights. After you create a watchlist, you can edit and delete it.
Watchlists are available only with a New-Scale Security Operations portfolio license. | |||
Attack Surface Insights Entity Tags in Threat Center | You can now find Threat Center cases or alerts related to groups of entities. When the detections of a case or alert are grouped by entity, the tags of that entity are automatically added to the tags of the case or alert. You can then use the tags to search for cases or alerts involving certain kinds of entities. Entity tags are copied to the case or alert. If you remove a tag from the entity, the tag remains in the case or alert. If you remove a tag from the case or alert, it remains in the entity. This feature is available only with a New-Scale Security Operations portfolio license. | |||
Alert Dismissal | To indicate that you reviewed an alert and other team members don't need to review it, you can now dismiss alerts. You can dismiss an individual alert or multiple alerts at once. 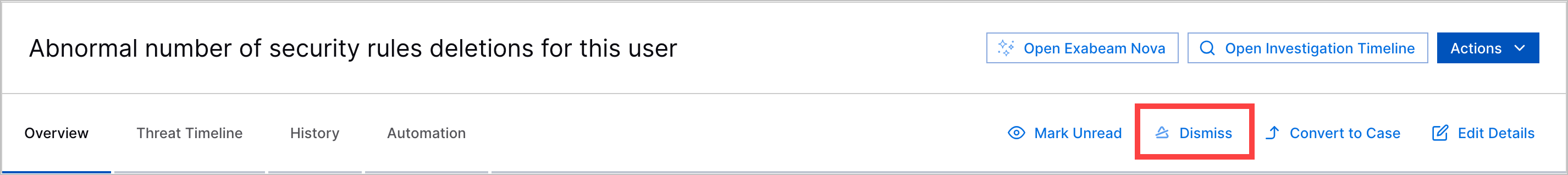 When an alert is dismissed, the dismissed reason, who dismissed the alert, and the date and time they dismissed the alert appears in the alert Overview tab. It is also recorded in the alert history. | |||
Alert Read and Unread Statuses | To track your alert triage workflow, you can now mark an alert as read and unread. An alert is automatically marked as read when you open it. After an alert is read, you can manually mark it as unread. 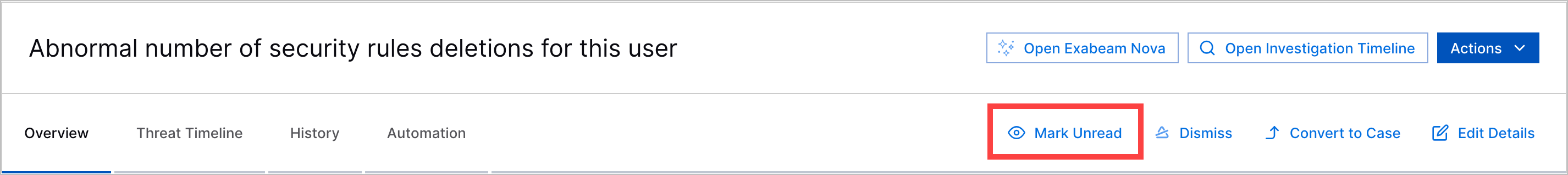 Dismissed alerts are automatically reverted to unread status when their risk scores increase by a percentage you specify. By default, the percentage is 10 percent. Any time an alert is marked as read or unread, it is recorded in the alert history. | |||
Alert Status Column | You can now view whether an alert is read, unread, or dismissed in the Alerts tab, under the STATUS column. 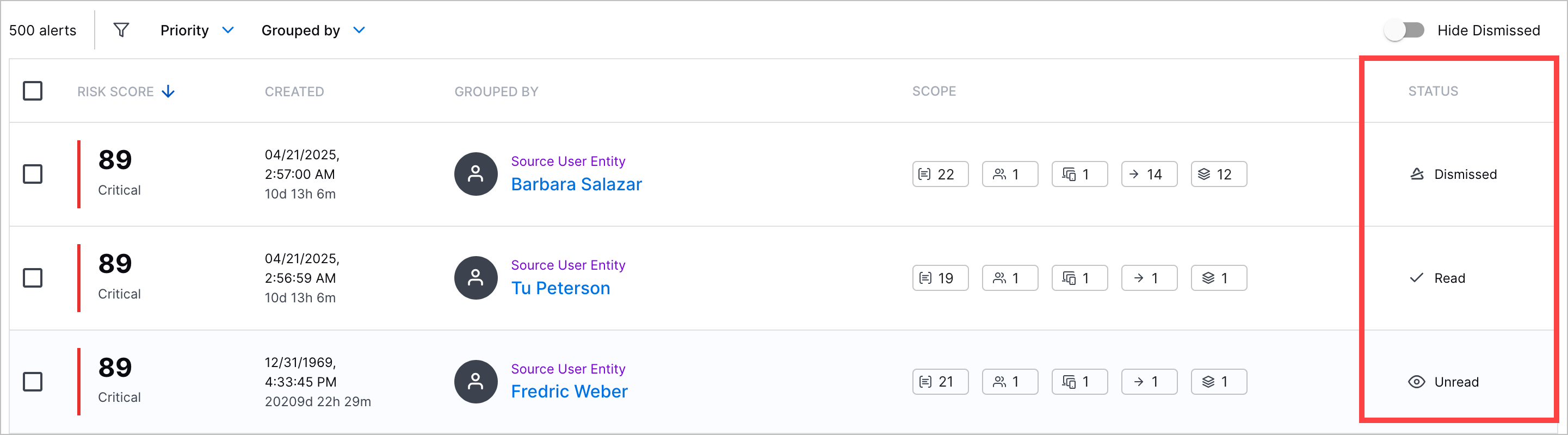 You can also search for alerts by status. To filter dismissed alerts from the list, toggle Hide Dismissed on. 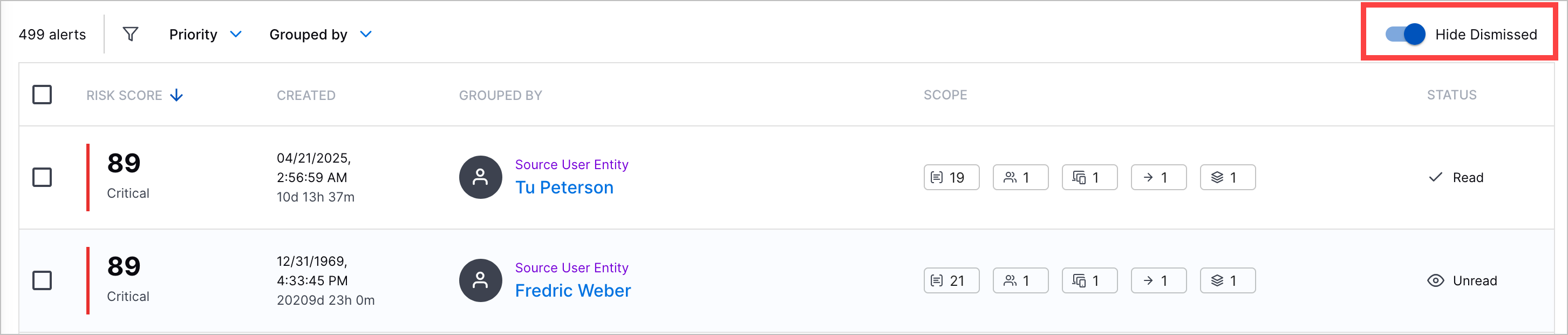 | |||
Permission for Sending Information to Webhooks | To send case or alert information to a webhook, you must have the Manage webhooks: Read, Write and Delete permission. |
April 2025
The following features were introduced in Threat Center in April 2025:
Feature | Description |
|---|---|
Exabeam Nova Case Name Enhancement | To ensure AI-generated case names help you quickly decide which cases to work on, the prompt used to generate case names has been refined to produce more concise case names. |
Increased Case and Alert List Default View | By default, you now see more cases or alerts in the case and alert lists. By default, 50 cases or alerts are displayed per page. You can also adjust the list to display 10, 25, or 100 cases or alerts per page. |
March 2025
The following features were introduced in Threat Center in March 2025:
Feature | Description | ||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Threat Center Exabeam Nova Enhancement | If you have a license that includes Advanced Analytics, Exabeam Nova Analyst Assistant and Exabeam Nova Threat Summary now have a better understanding of a case or alert, considering the 50 most recently grouped detections when generating a response.[a] If you have a New-Scale Security Operations portfolio license, you can now get more accurate and trustworthy responses with minimal hallucinations from Exabeam Nova Analyst Assistant and Copilot Threat Summary. Exabeam Nova now has a better understanding of a case or alert, considering associated entity information and all associated detections when generating a response. | ||||||||||||||||||||||||||||||||||||||||||||||||
Created Column | To ensure you're investigating the right case or alert, you can now view the date and time a case or alert was created and time elapsed since the case or alert was created under the Created column. 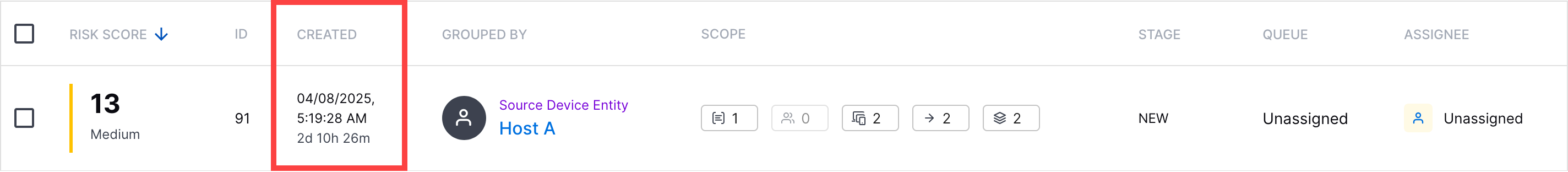 | ||||||||||||||||||||||||||||||||||||||||||||||||
Queue and Assignee Columns | To support sorting by queue and assignee, cases now have separate queue and assignee columns. 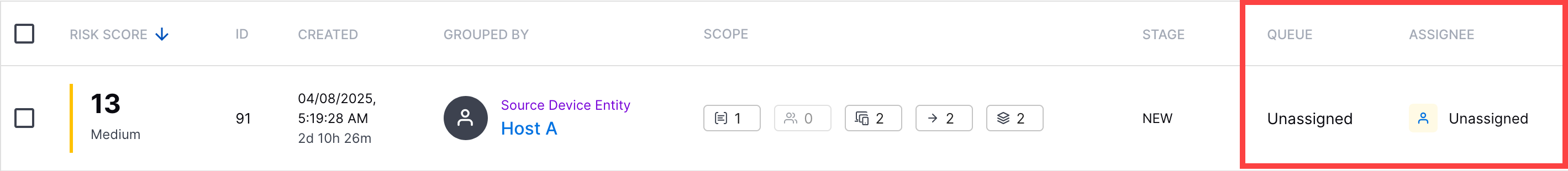 | ||||||||||||||||||||||||||||||||||||||||||||||||
Sorting Enhancements | To help you quickly find a case or alert, you can now sort cases and alerts by three additional columns: Grouped By, Stage, Queue, and Assignee. | ||||||||||||||||||||||||||||||||||||||||||||||||
Filters | To view only certain kinds of cases or alerts, you can now filter cases and alerts. For cases, you can filter by priority, grouped by value, stage, queue, and assignee.
For alerts, you can filter by priority and grouped by value.
| ||||||||||||||||||||||||||||||||||||||||||||||||
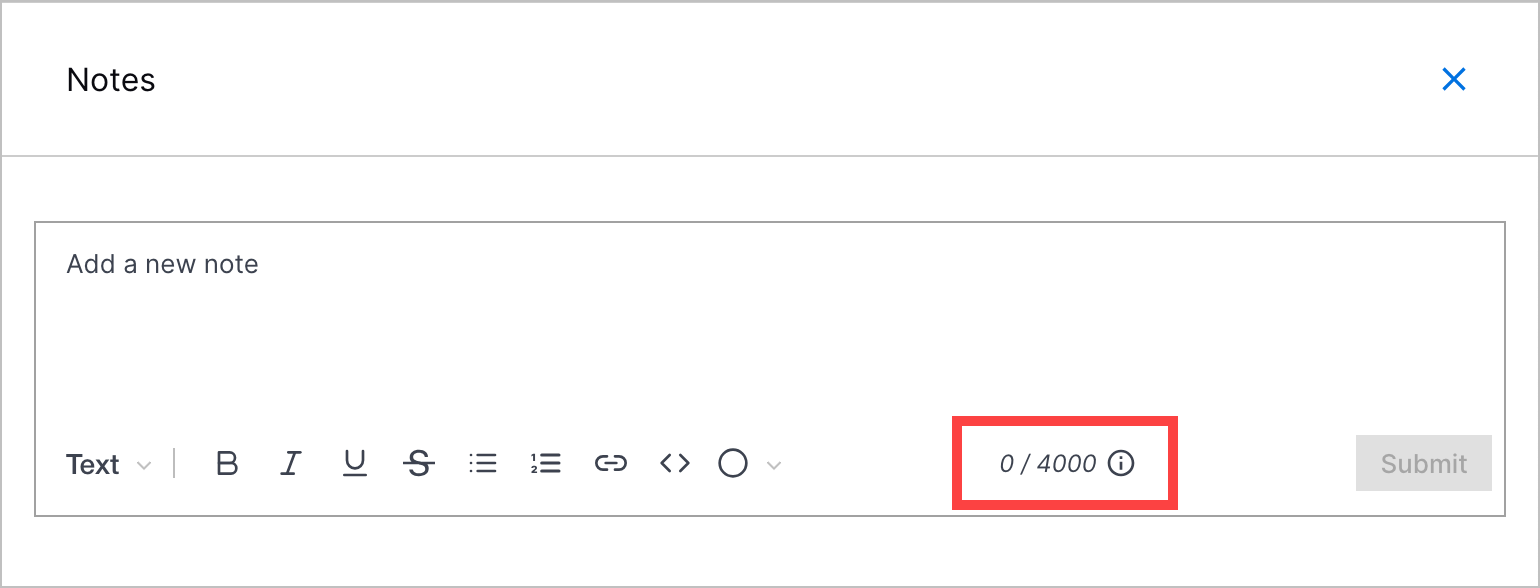
Increased Notes Character Limit | To ensure you can communicate everything you want with case notes, you can now add up to 4,000 characters in a single note.
| ||||||||||||||||||||||||||||||||||||||||||||||||
Threat Timeline Rule Name Enhancement | To better discern the type of rule associated with a detection, you can now see the full name of the rule type in the Threat Timeline.
| ||||||||||||||||||||||||||||||||||||||||||||||||
[a] This tool is designed to condense security event data into easy-to-understand language, focusing on important security details. It can also answer follow-up questions and discuss security tech topics, but its accuracy might vary outside these areas. Always double-check responses for crucial decisions. Your queries and data will only be retained temporarily and won't be used for AI training. Exabeam is actively improving this tool and welcomes feedback. | |||||||||||||||||||||||||||||||||||||||||||||||||
February 2025
The following features were introduced in Threat Center in February 2025:
Feature | Description | |
|---|---|---|
Case ID Enhancement | To ensure all cases have a human-readable identifier to which you can refer, all cases are now automatically assigned a unique number as the case ID. You can view the case ID in the list of cases, in a case, emails sent from the case, and webhook notifications sent from the case. You can also search for a case using its case ID. Case IDs for existing cases remain the same and won't have new case IDs retroactively assigned to them. | |
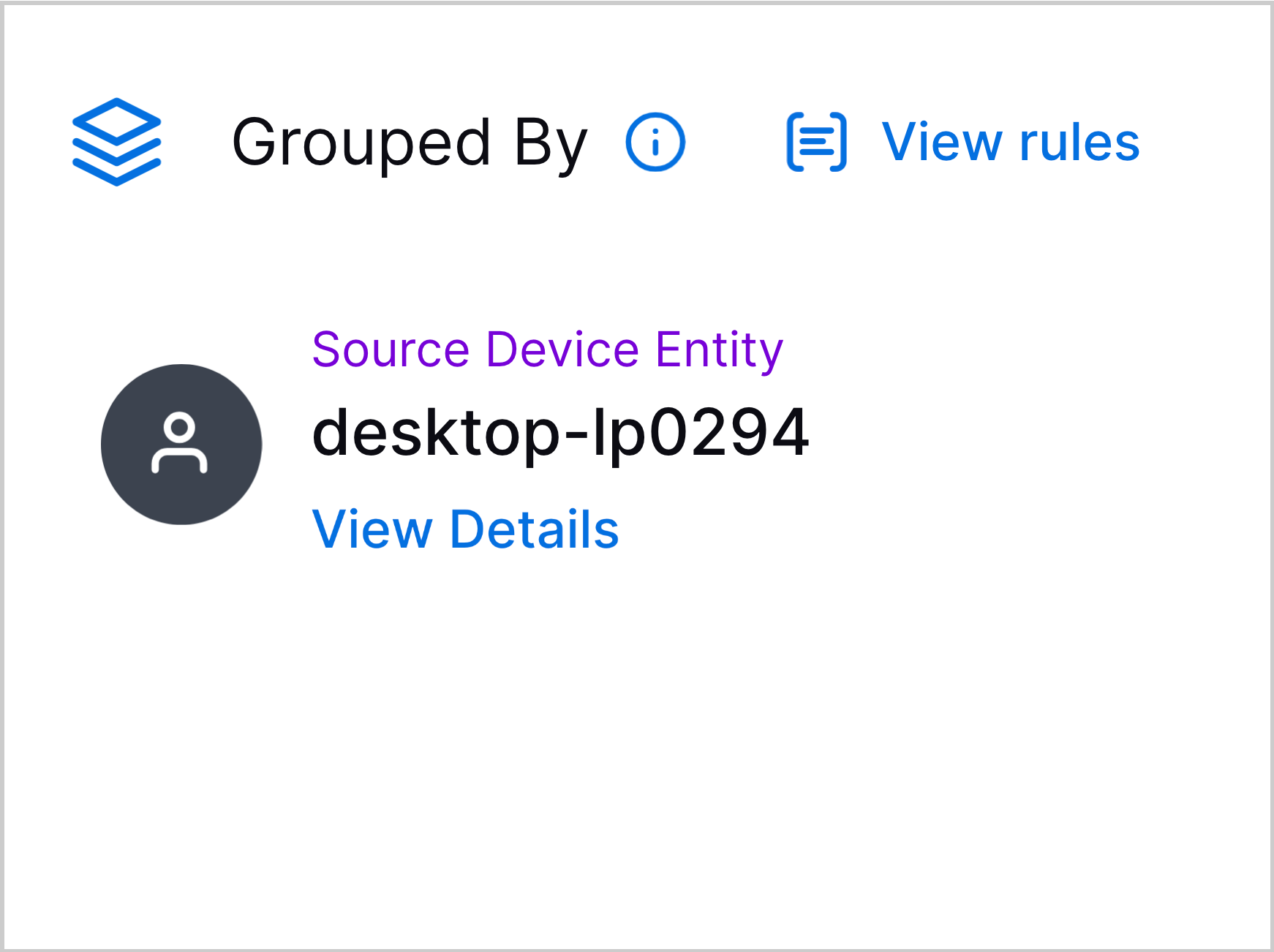
Entity Attribute Enhancements | If a case or alert contains detections grouped by entity, you can now learn more about the entity and view the entity attributes directly in Threat Center:
| |
New Region Support for the UK | Support for Threat Center now extends to the UK region. You can now access and use Threat Center in the UK. |
January 2025
The following features were introduced in Threat Center in January 2025:
Feature | Description | |
|---|---|---|
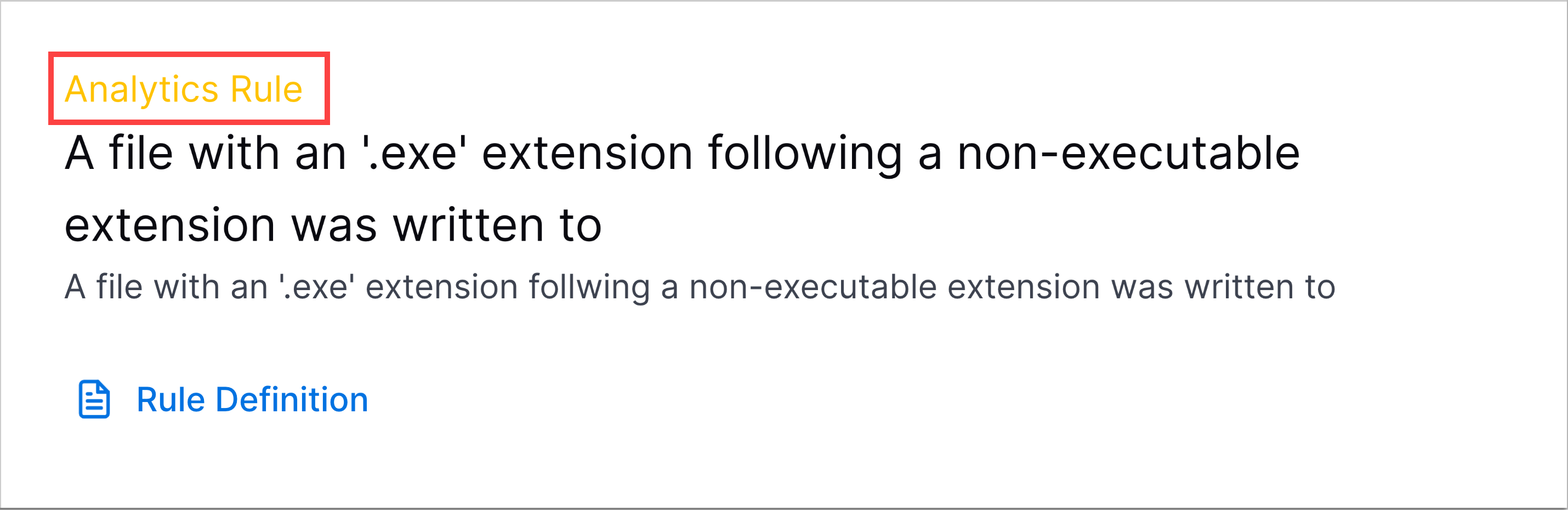
Analytics Rules Detections | If you have a New-Scale Security Operations Portfolio license, you can now investigate triggered analytics rules in Threat Center as detections. 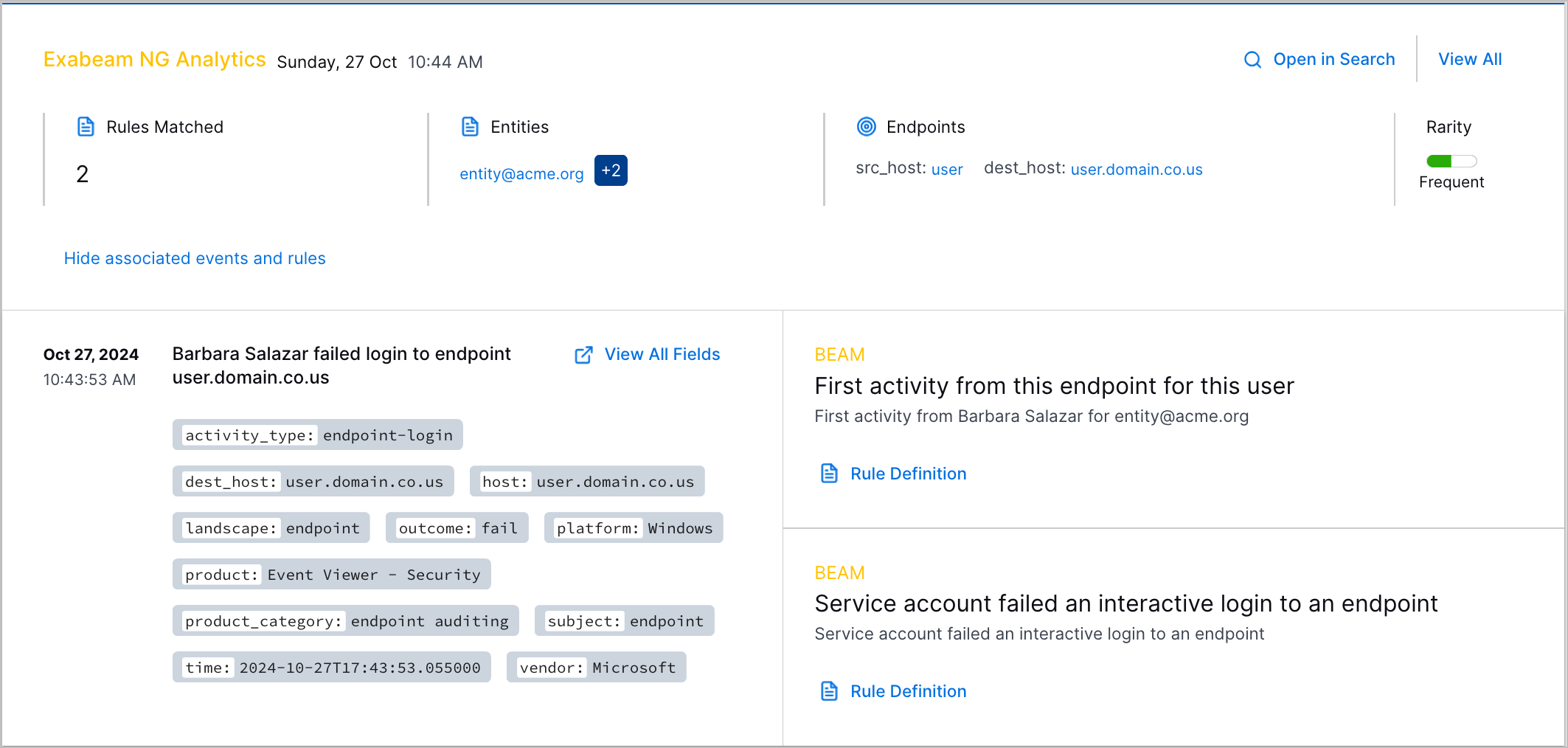 | |
Risk Score Calculation with Behavioral Analytics | With Threat Detection Management on the New-Scale Security Operations platform, risk score calculations for alerts and cases are now based on behavioral analytics insights and more accurately reflect real risk. The analytics engine assigns detections a rarity score depending on how often Threat Detection Management rules trigger in your environment. Case and alert risk scores are calculated using a combination of detection rarity scores and certain confidence factors. | |
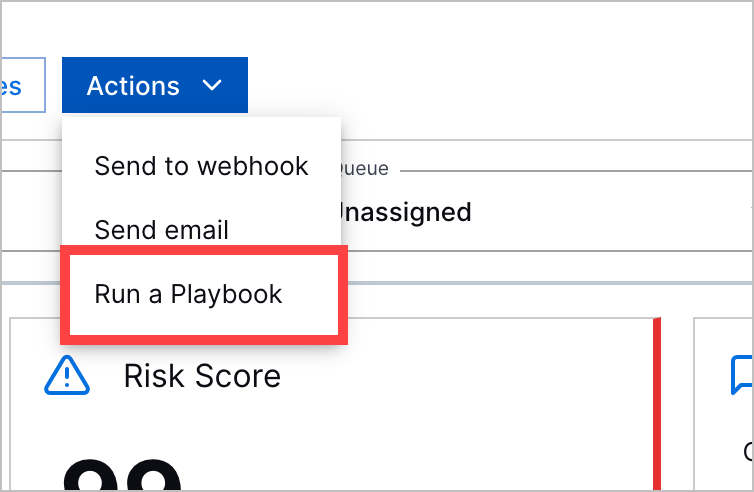
Automation Management in Threat Center | Threat Center is now more deeply integrated with Automation Management. You can now:
| |
Manual Case Creation | You can now manually create a case from scratch, without associating it with an alert.
| |
Copilot Case Names | You can now better understand what a case represents and quickly decide which case to work on with AI-generated case names. Only cases converted from an alert have AI-generated case names. | |
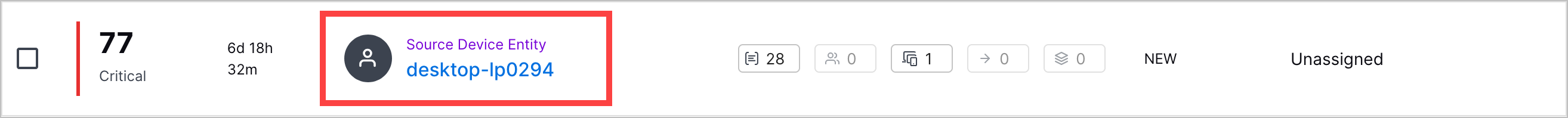
Enhanced Entity Display | Entities are now displayed more intuitively. User entities are shown as their full name or email address. If neither information is available, user entities are shown as their username. Device entities are shown as their host name. | |
Device Entity Details | To better understand a device entity in the context of a case or alert, you can now view entity device details from Attack Surface Insights directly in Threat Center. | |
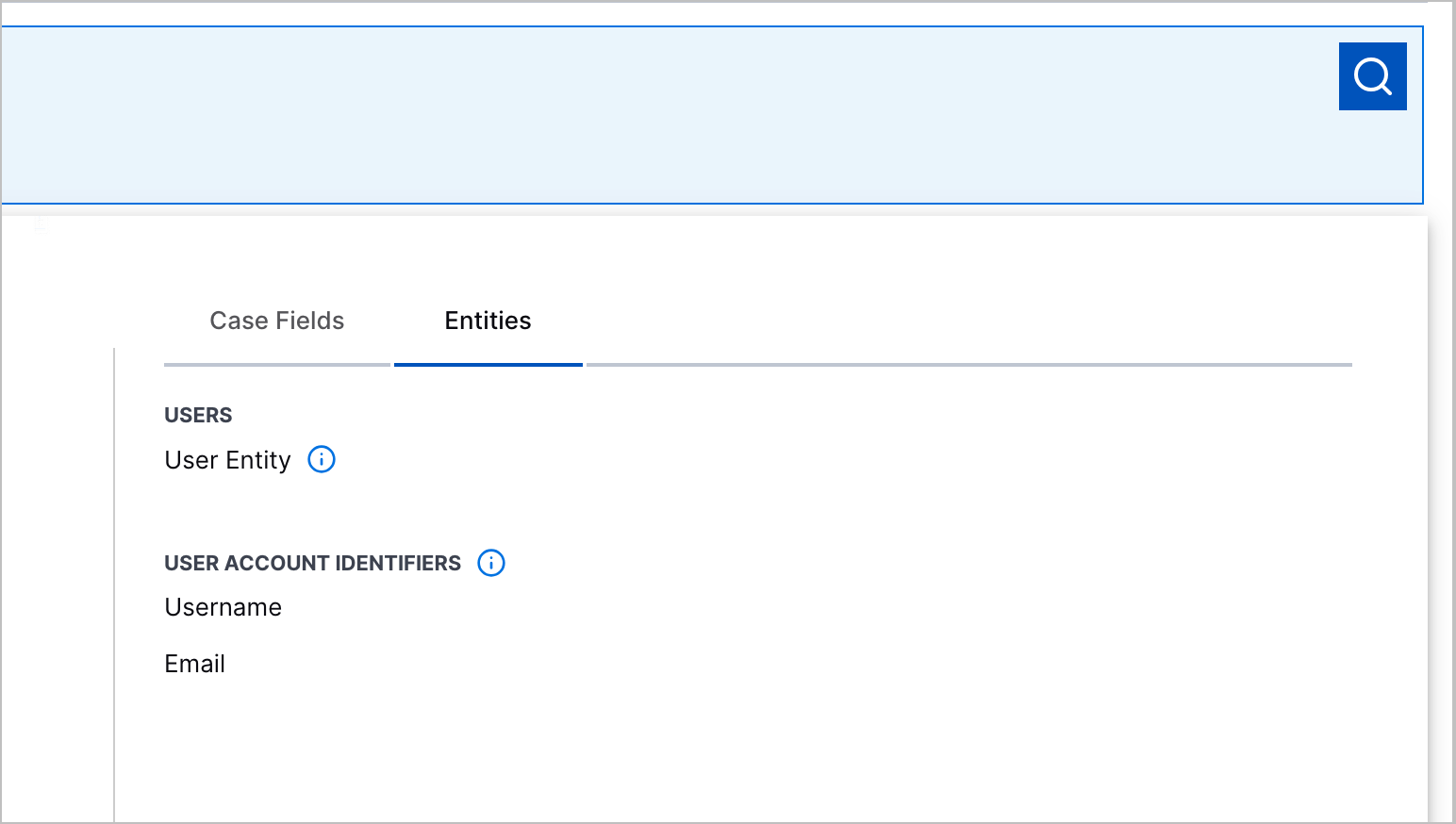
User Entity Search | To focus your investigation on a specific user entity, you can now search for cases and alerts whose detections are grouped by a specific user entity. When you build a search, you can now navigate to the Entities tab to search for a user entity by their full name or known account, like username or email.
| |
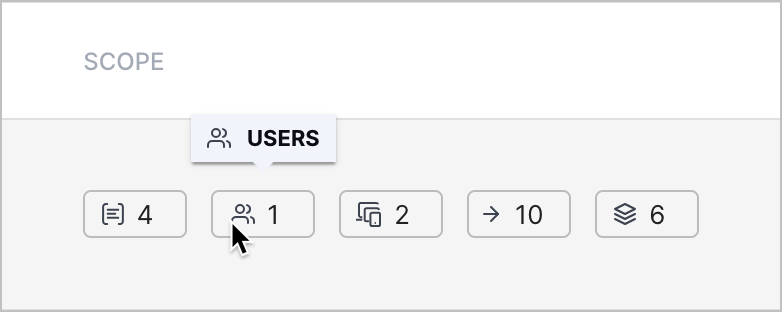
Scope Column | When you view the list of cases and alerts, you can now quickly identify the number of objects associated with a case or alert with a new SCOPE column. 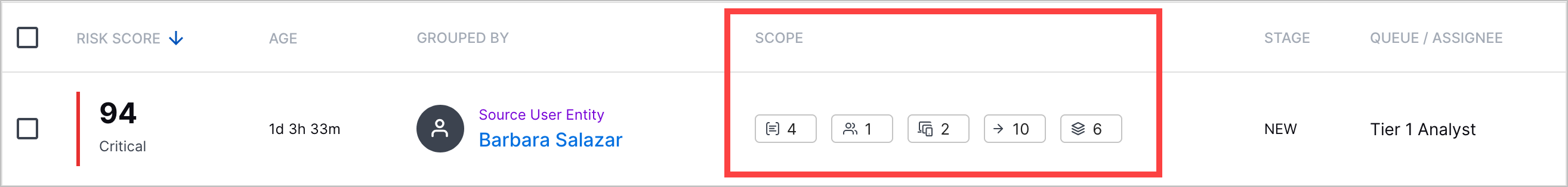 Under the SCOPE column, you can view the number of:
To view the definition of an object, hover over the object count.
| |
Open Investigation Timeline Enhancements | To investigate the most pertinent events related to a case or alert in Search, you can now click Open Investigation Timeline in a case or alert to automatically navigate to events in Search that have an assigned risk score. |