- Introduction to Context Management
- Onboarding a Context Table
- Custom Context Tables
- Create a Custom Context Table by Importing a CSV File
- Create a Custom Context Table Using the Add Custom Option
- Working with Filtered Context Tables
- View and Interact with a Custom or Filtered Context Table
- View the Details Panel for a Custom or Filtered Context Table
- Edit the Configuration of Custom or Filtered Context Tables
- Active Directory Context Tables
- Prerequisites to Onboard an Active Directory Context Table
- Create an Active Directory Context Table
- View and Interact with an Active Directory Context Table
- View the Details Panel for an Active Directory Context Table
- Edit the Configuration of an Active Directory Context Table
- Default User Attribute Mapping for Active Directory
- Default Device Attribute Mapping for Active Directory
- Anomali Context Tables
- Prerequisites to Onboard an Anomali Context Table
- Create an Anomali Context Table
- View and Interact with an Anomali Context Table
- View the Details Panel for an Anomali Context Table
- Edit the Configuration of an Anomali Context Table
- Default IP Attribute Mapping for Anomali
- Default Domain Attribute Mapping for Anomali
- CrowdStrike Context Tables
- Microsoft Entra ID Context Tables
- Prerequisites to Onboard a Microsoft Entra ID Context Table
- Create a Microsoft Entra ID Context Table
- View and Interact with a Microsoft Entra ID Context Table
- View the Details Panel for a Microsoft Entra ID Context Table
- Edit the Configuration of a Microsoft Entra ID Context Table
- Default User Attribute Mapping for Microsoft Entra ID
- Default Device Attribute Mapping for Microsoft Entra ID
- Okta Context Tables
- Recorded Future Context Tables
- Prerequisites to Onboard a Recorded Future Context Table
- Create a Recorded Future Context Table
- View and Interact with a Recorded Future Context Table
- View the Details Panel for a Recorded Future Context Table
- Edit the Configuration of a Recorded Future Context Table
- Default IP Attribute Mapping for Recorded Future
- Default Domain Attribute Mapping for Recorded Future
- STIX/TAXII Context Tables
- Prerequisites to Onboard a STIX/TAXII Context Table
- Create a STIX/TAXII Context Table
- View and Interact with a STIX/TAXII Context Table
- View the Details Panel for a STIX/TAXII Context Table
- Edit the Configuration of a STIX/TAXII Context Table
- Default IP Attribute Mapping for STIX/TAXII
- Default Domain Attribute Mapping for STIX/TAXII
- Custom Context Tables
- Add Data to an Existing Context Table
- Using Context Data in Downstream Applications
- Pre-Built Context Tables
- Context Management APIs
- Troubleshooting Context Management
- Refresh Rates for Context Tables
Context in Search and Correlation Rules
In Search and Correlation Rules, context data can be looked up and used to build search queries, which can also be used to create correlation rules. Context data can be used either to look up values from context tables or to find event fields enriched with threat intelligence context data.
For information about the mechanics of creating search queries, using either the Basic Search or Advanced Search modes, see Performing Searches in the Search Guide.
For information about the different ways context data can be used in Search and Correlation Rules, see the appropriate sections below.
Context Table Lookup
In Search and Correlation Rules, context data is available by specifying a context table using the In Context Table option. You can add any type of context table, including collector-based tables, custom tables, or pre-built tables. You can also add a filtered context table.
In the Basic search mode, this option is available for any common event field that contains string or numerical data. For example, in the image below, when the dest_ip field is selected, you can click the In Context Table button to display drop down menus of available context tables and columns that can be added to the query. A preview of the first few rows of the table data is displayed. By default, the key column is selected for the search, but you can choose to search for values in any column of the selected table.
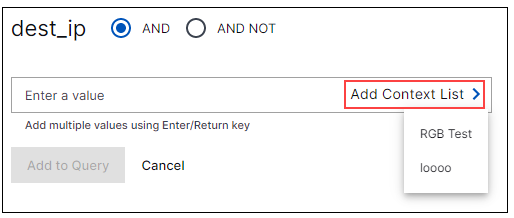
In the Advanced search mode, you can add a context table and column to a query by using syntax in the following form: dest_ip IN "table name"."column name"
When the query runs, it searches for events that include a dest_ip field and a value that is found in the specified column of the selected context table.
Note
Certain restrictions apply to query building when a context table lookup is included:
The context table can be included with an AND but not with an OR operator.
Up to two context tables can be included per query, with a single column for each table.
Context tables that contain more than 100,000 entries are not available for inclusion in a query.
An empty context table can be included in a search query but it will not generate any search results until at least one record is added to the table.
Enriched Threat Intelligence Field Lookup
In Search and Correlation Rules, context data is available by looking up events enriched with threat intelligence data. Context Management provides the following different types of threat intelligence context tables:
Pre-built context tables include Exabeam-provided, curated threat intelligence data about known malicious domains and IP addresses. For information about these context tables, see Pre-Built Threat Intelligence Context Tables. The following context tables are included:
Exabeam Threat Intelligence Domains — Collects data about known malicious domains.
Exabeam Treat Intelligence IPs — Collects data about known malicious IP addresses.
STIX/TAXII-based context tables are tables that provide external threat intelligence data from any log source that supports the STIX/TAXII framework. For more information about these context tables, see STIX/TAXII Context Tables. Pre-configured formats may be available for some external log sources in the Context Management service.
The Context Management service injects indicators of compromise (IOC) tags into event logs. When added to events, these enriched IOC fields mark the event records as having specific characteristics that may be evidence of a security breach. You can find events enriched with threat intelligence data in the following ways:
Search for any event that could be considered malicious.
As events are ingested they are validated against the threat intelligence data collected in the threat intelligence context tables. When known indicators of compromise (IOCs) are matched, the event is marked as containing malicious content. To find these events, search for
is_ioc:true.Sample query:
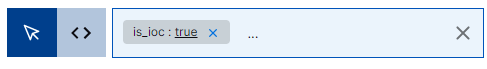
Search for events enriched with specific threat intelligence context data.
Beyond identifying malicious content, you might want to drill into your event data with more granular searches. You can search on the following event fields to find events that match specific threat intelligence data:
ioc_types— (array of strings) Populated with IOC types, such as IP_trojan, Domain_ransomware, etc.ioc_fields— (array of strings) Populated with the IOC field names whose values matched threat intelligence data, such as src_ip, host, etc.ioc_sources(array of strings) Populated with the name of the log source from which data marked as an IOC was ingested.
For example, you can create a search query that includes both
is_ioc:trueandioc_types:"botnet"to find events marked as containing malicious botnet activity.Sample query:
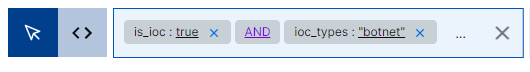
For information about the specific threat intelligence data available for use in Search, see Threat Intelligence Enrichment.
