- 2026 Release Notes
- 2025 Release Notes
- December 2025
- November 2025
- October 2025
- September 2025
- August 2025
- July 2025
- June 2025
- May 2025
- April 2025
- March 2025
- February 2025
- January 2025
- Known Issues
July 2025
The New-Scale Security Operations Platform includes the following addressed features and new features for July 2025.
Cloud Collectors
Feature | Description |
|---|---|
Anomali Cloud Collector | The Anomali Cloud Collector is now available is now available, as part of Cloud Collectors to facilitate threat intelligence data collection from an Anomali source that supports the STIX/TAXII framework. You can opt to collect data about either IP addresses or domains. You can also opt to automatically generate a corresponding Anomali context table in the Context Management application that will process the data and map it to a standardized set of attributes. The context table will have the same name as the cloud collector. |
Authentication Method options to Authenticate via Microsoft Entra ID for Azure EventHub Cloud Collector | In addition to the existing Shared Access Signature (SAS) based connection string authentication method, the Azure EventHub Cloud Collector now supports authentication via Microsoft Entra ID Account for more secure, and centralized identity and access management. |
Early Access Collectors | |
Dropbox Cloud Collector | The Dropbox Cloud Collector is now available as part of Cloud Collectors Early Access program, to facilitate ingestion of team activity logs from Dropbox. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Qualys Cloud Collector | The Qualys Cloud Collector is now available as part of Cloud Collectors Early Access program, to facilitate ingestion of Activity Logs, and Vulnerabilities including VM host detection events from Qualys sources. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Slack Cloud Collector | The Slack Cloud Collector is now available as part of Cloud Collectors Early Access program, to facilitate ingestion of events from the Audit Logs API endpoints. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Context Management
Feature | Description |
|---|---|
Anomali Context Tables | Context Management now supports a preconfigured onboarding experience for Anomali context tables. These tables process data that is ingested by a corresponding Anomali cloud collector that supports the STIX/TAXII framework. By default these context tables process a predetermined set of IP or domain attributes from the source collector and then map these attributes to a set of standardized Exabeam target attributes. For more information, see Anomali Context Tables in the Context Management Guide. For information about onboarding an Anomali context table via a cloud collector, see Anomali Cloud Collector in the Cloud Collectors Administration Guide. |
Delete Records via a New Public API | You can now delete one or more records directly from a custom context table via a new public API. To indicate the records to be deleted, specify the values from the primary key column of the table in the API request body. Note that this API can be used to remove records only from custom context tables. For more information, see Context Management APIs and look for the following API: |
Log Sources
Feature | Description |
|---|---|
Log Source Monitoring | Using the Log Source service you can now detect and monitor active and inactive log sources. In addition to granular monitoring of log sources, the Log Source service offers log source policy configuration and discovery, log source status visibility, and export of log sources. |
Support for New Log Source Identifiers | While creating a log source policy you can now select unique log source identifiers from a wide range of options to detect and monitor active and inactive log sources. |
New-Scale Platform
Feature | Description |
|---|---|
Global Email Notifications | To extend the ability of notifications for system events, you can now send email notifications to a specific user or a shared distribution list. For more information, see Manage Global Notifications Preferences in the New-Scale Security Operations Platform Administration Guide. |
Outcomes Navigator
Feature | Description |
|---|---|
Exabeam Nova Advisor Agent Renaming | The Exabeam Nova Analyst Assistant is now renamed Exabeam Nova Advisor Agent. |
Site Collectors 2.11 (July 2025)
Feature | Description |
|---|---|
Support for Additional Ports for Syslog Collector Configuration | In addition to the supported port range 1024 - 49151, the port numbers 514 and 515 of the Syslog server are now supported for configuration of Syslog and Fortinet Collectors. |
Threat Center
Feature | Description |
|---|---|
Enhanced Search Timeline Navigation | You can more easily navigate to the Search timeline view from Threat Center to view all detections related to the attribute or entity by which they are grouped. From the cases and alerts lists, you can now navigate directly to the Search timeline view by clicking   In cases and alerts, you can now navigate directly to the Search timeline view by clicking Timeline: 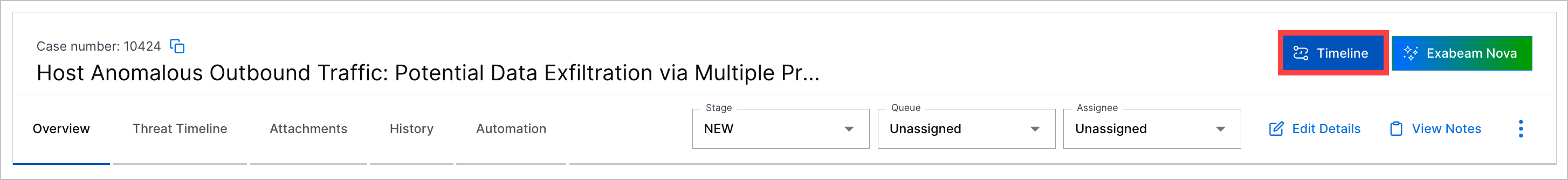 The query automatically generated in Search has been enhanced to show detections only and in the same time range applied in Threat Center search. |
Threat Detection Management
Feature | Description |
|---|---|
Custom Analytics Rules | To detect unique security threats not addressed with pre-built analytics rules or correlation rules, you can now create your own analytics rule. To create an analytics rule, you define the analytics rule in JSON format, then import the JSON file into Threat Detection Management. An imported analytics rule is initially disabled. To activate it and allow it to trigger in your environment, you must enable it and apply the change to your environment. After you create a custom analytics rule, you can export and delete it. Custom analytics rules are available with an add-on to a New-Scale Security Operations porfolio license. |
New and Updated Pre-Built Analytics Rules | This analytics rule update was released on July 23, 2025. You can now better detect remote access abuse, suspicious process execution, and first time login activities with new and updated pre-built analytics rules. New pre-built analytics rules include:
Pre-built analytics rules for which
Pre-built analytics for which
Removed pre-built analytics rule include:
|
Resolved Issues
Attack Surface Insights Resolved Issues
Issue ID | Description |
|---|---|
ENG-73607 | When you selected all entities matching a search query, the action to edit all selected entities was incorrectly made available. You could edit the entities displayed on the page only, not all entities matching the search query. Now, when you select all entities matching a search query, the ability to edit those entities is disabled. |
Site Collector 2.11: Security Vulnerabilities Remediated in July 2025
The Site Collectors 2.11 (July 2025) release includes remediated security vulnerabilities. For more information about Exabeam’s commitment to remediating vulnerabilities for Site Collector, see the Vulnerability Remediation Policy.
Known CVE - CVE-2025-48734. This is a NiFi CVE. Site Collector uses the latest NiFi version 2.4.0 and will update to the new version after NiFi provides a fix in an upcoming NiFi release.
Toolkit has been deprecated and is no longer in use hence no security vulnerabilities update is available for that.
The following table lists the CVEs remediated for the Nifi container and their severity.
Critical | High | Medium | Low |
|---|---|---|---|
Total: 0 | Total: 0 | Total: 11 | Total: 1 |
– | – |
| CVE-2024-47081 |

