- 2026 Release Notes
- 2025 Release Notes
- December 2025
- November 2025
- October 2025
- September 2025
- August 2025
- July 2025
- June 2025
- May 2025
- April 2025
- March 2025
- February 2025
- January 2025
- Known Issues
May 2025
The New-Scale Security Operations Platform includes the following addressed features and new features for May 2025.
Attack Surface Insights
Feature | Description |
|---|---|
Attack Surface Insights Entity Tags in Threat Center | You can now find Threat Center cases or alerts related to groups of entities. When the detections of a case or alert are grouped by entity, the tags of that entity are automatically added to the tags of the case or alert. You can then use the tags to search for cases or alerts involving certain kinds of entities. Entity tags are copied to the case or alert. If you remove a tag from the entity, the tag remains in the case or alert. If you remove a tag from the case or alert, it remains in the entity. |
Cloud Collectors
Feature | Description |
|---|---|
CrowdStrike Context Devices Cloud Collector | The CrowdStrike Context Devices Cloud Collector is now available as part of Cloud Collectors Early Access program to facilitate ingestion of data from a CrowdStrike source. The use of a cloud collector to ingest CrowdStrike device data eliminates the need for the Exabeam Ingester for CrowdStrike license add-on. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
STIX/TAXII Cloud Collector | The STIX/TAXII Cloud Collector is now available to facilitate threat intelligence data collection from external sources that support the STIX/TAXII framework. You can opt to collect data about either IP addresses or domains. You can also opt to automatically generate a corresponding context table in the Context Management application that will process the data and map it to a standardized set of attributes. The context table will have the same name as the cloud collector. |
Recorded Future Context Cloud Collector | The Recorded Future Context Cloud Collector is now available to facilitate threat intelligence data collection from a Recorded Future Context source that supports the STIX/TAXII framework. You can opt to collect data about either IP addresses or domains. You can also opt to automatically generate a corresponding Recorded Future context table in the Context Management application that will process the data and map it to a standardized set of attributes. The context table will have the same name as the cloud collector. |
Context Management
Feature | Description |
|---|---|
STIX/TAXII Context Tables | Context Management now supports onboarding STIX/TAXII context tables. These tables process data that is ingested by a corresponding STIX/TAXII cloud collector from an external threat intelligence source that supports the STIX/TAXII framework. By default these context tables process a predetermined set of IP or domain attributes from the source collector and they map these attributes to a set of standardized Exabeam target attributes. For more information, see STIX/TAXII Context Tables in the Context Management Guide. |
Recorded Future Context Tables | Context Management now supports a preconfigured onboarding experience for Recorded Future context tables. These tables process data that is ingested by a corresponding Recorded Future Context cloud collector that supports the STIX/TAXII framework. By default these context tables process a predetermined set of IP or domain attributes from the source collector and they map these attributes to a set of standardized Exabeam target attributes. For more information, see Recorded Future Context Tables in the Context Management Guide. |
CrowdStrike Device Context Table via Cloud Collector | Context Management now supports onboarding a CrowdStrike device context table via a cloud collector, without the need for the Exabeam Ingester for CrowdStrike license add-on. The context table process es data that is ingested by a corresponding CrowdStrike Context cloud collector from a CrowdStrike source. By default the context table processes a predetermined set of device attributes from the source collector and maps them to a set of standardized Exabeam target attributes. The CrowdStrike context table onboarding via cloud collector is available as part of the Early Access program. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program, in the Cloud Collectors Administration Guide. For more information and prerequisites, see CrowdStrike Context Tables in the Context Management Guide. |
Correlation Rules
Feature | Description |
|---|---|
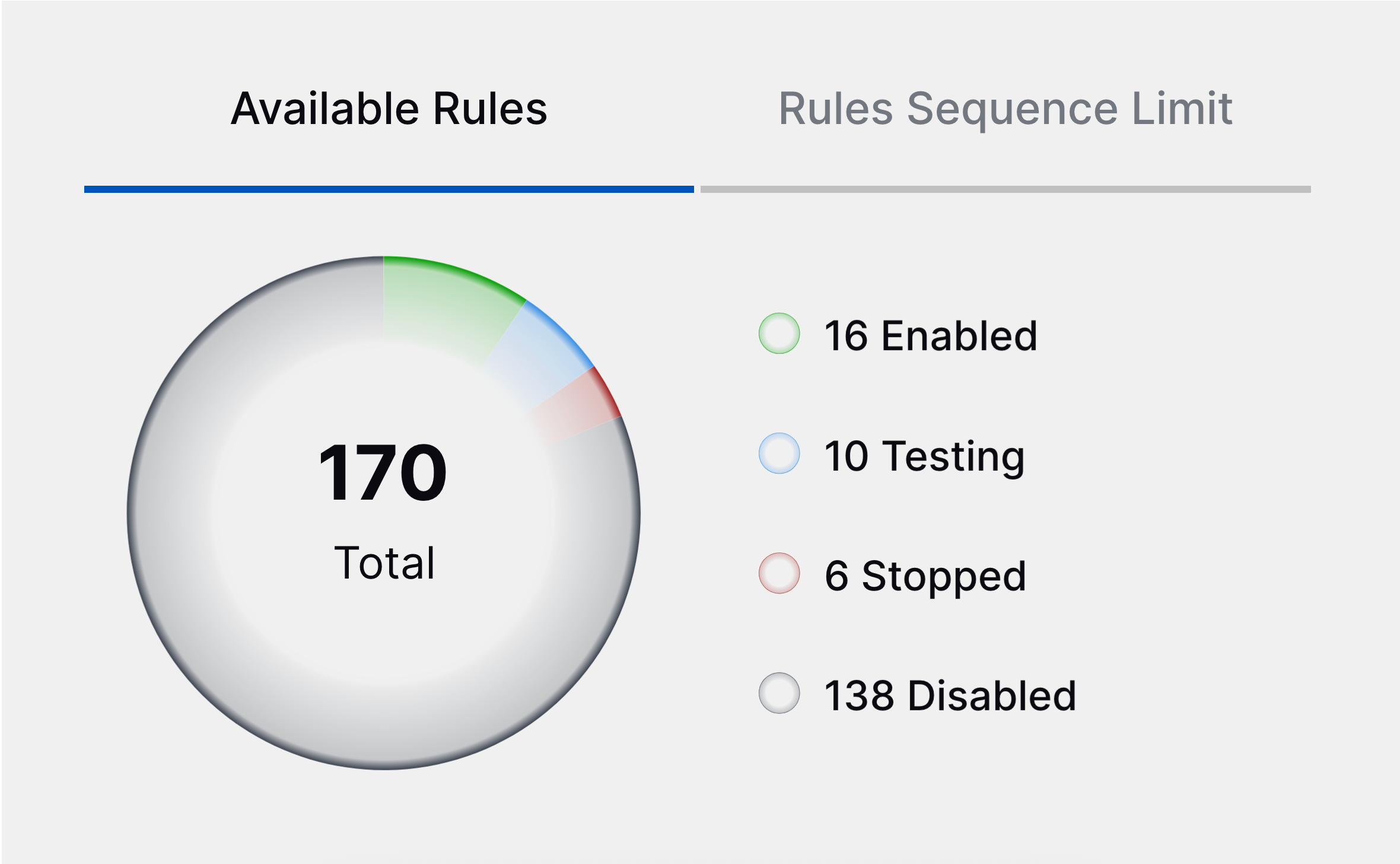
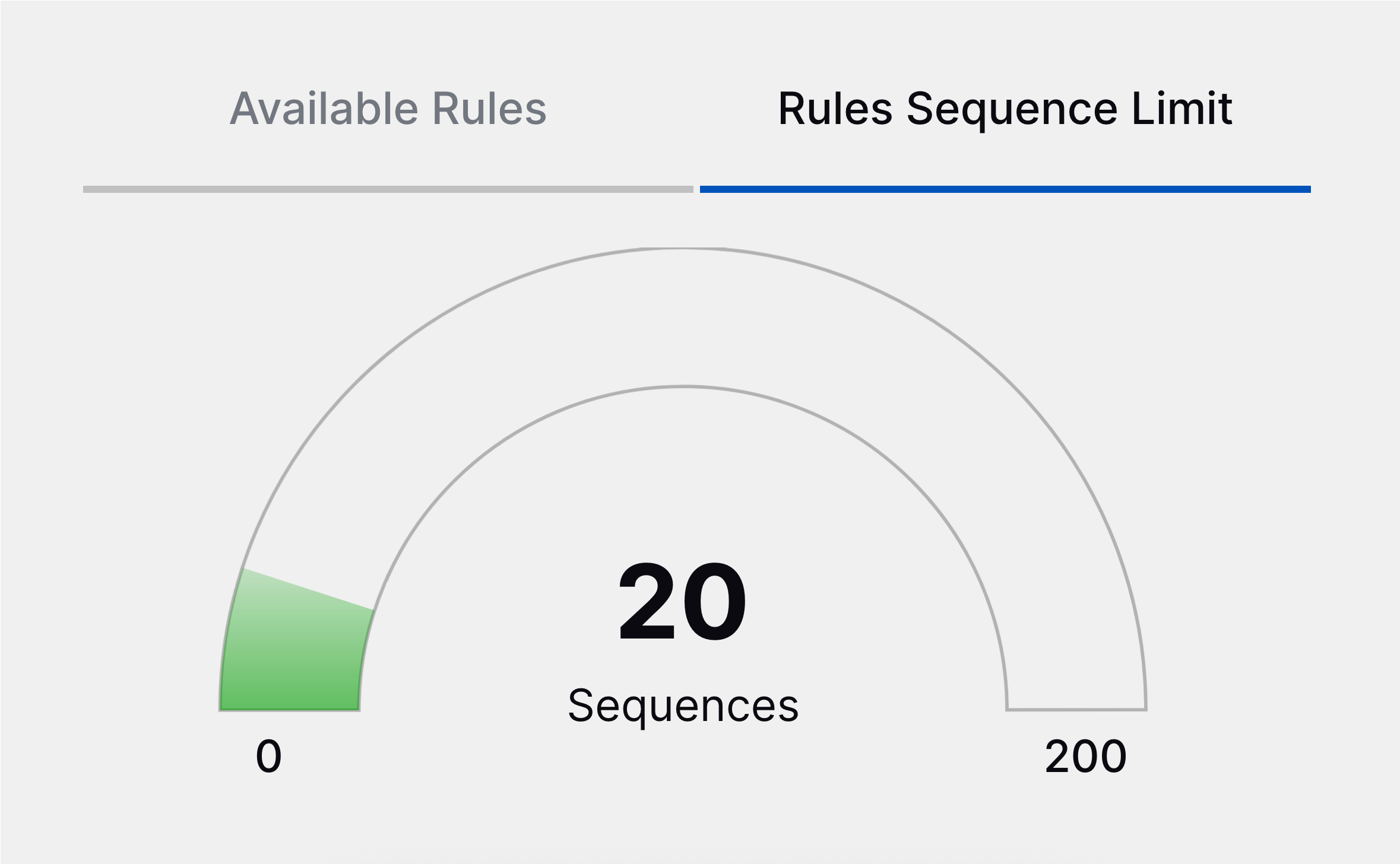
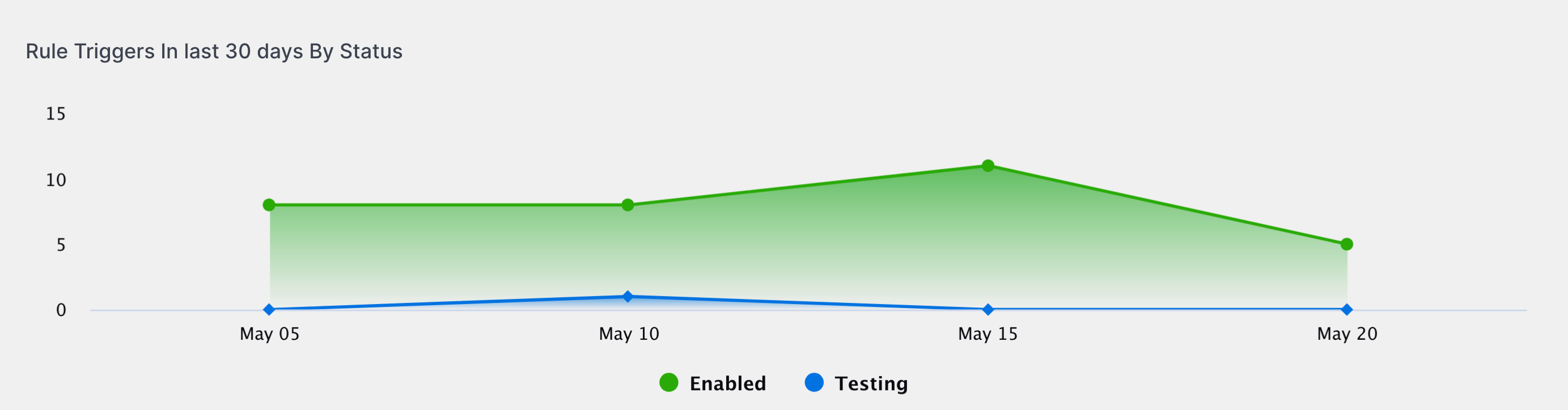
Correlation Rules Insights | To make informed decisions about authoring and tuning rules, you can now view insights about your correlation rules directly in Correlation Rules, including:
|
Log Stream
Feature | Description |
|---|---|
Creating Custom Enrichment Rules | New workflows have been introduced for the Enrichments tab in Log Stream. The new functionality provides access to define enrichment rules inside the Log Stream application. You can configure both the conditions an event must meet for a specific enrichment to be applied and the mapping that the enrichment rule will perform. This functionality provides access to do the following:
Currently, this feature is available out-of-the-box only if you have the New-Scale Analytics license. If you have another Exabeam license, this feature can be made available through an Early Access program. To sign up for this program, email the following group: [email protected]. For more information, see Enrichments in the Log Stream Guide. |
New-Scale Platform
Feature | Description |
|---|---|
Documentation of Supported Regions for Data Residency | A table of supported regions and their base URLs has been added to the New-Scale Security Operations Platform Guide and is available from the New-Scale landing page in the Exabeam Documentation portal. For more information, see Supported Regions for Data Residency. |
Outcomes Navigator
Feature | Description | ||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Exabeam Nova MITRE ATT&CK Coverage Summary | To get a high-level view of your overall security posture, you can now view an AI-generated summary of your overall MITRE ATT&CK® coverage.[a]  The summary identifies:
| ||||||||||||||||||||||||||||||||||||||||||||||||
[a] MITRE ATT&CK and ATT&CK are trademarks of The MITRE Corporation ("MITRE"). Exabeam is not affiliated with or sponsored or endorsed by MITRE. Nothing herein is a representation of the views or opinions of MITRE or its personnel. | |||||||||||||||||||||||||||||||||||||||||||||||||
Threat Center
Feature | Description | |||
|---|---|---|---|---|
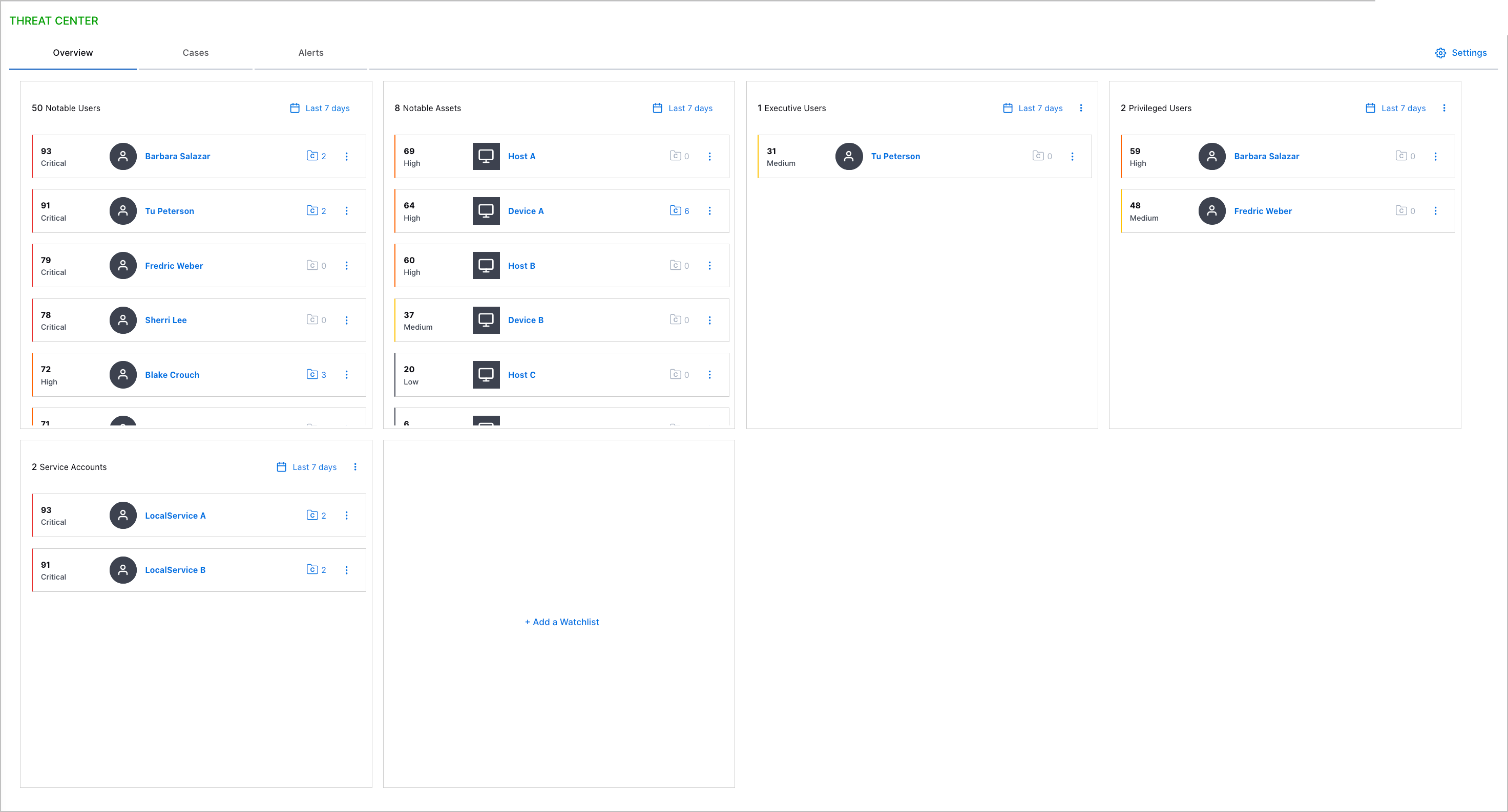
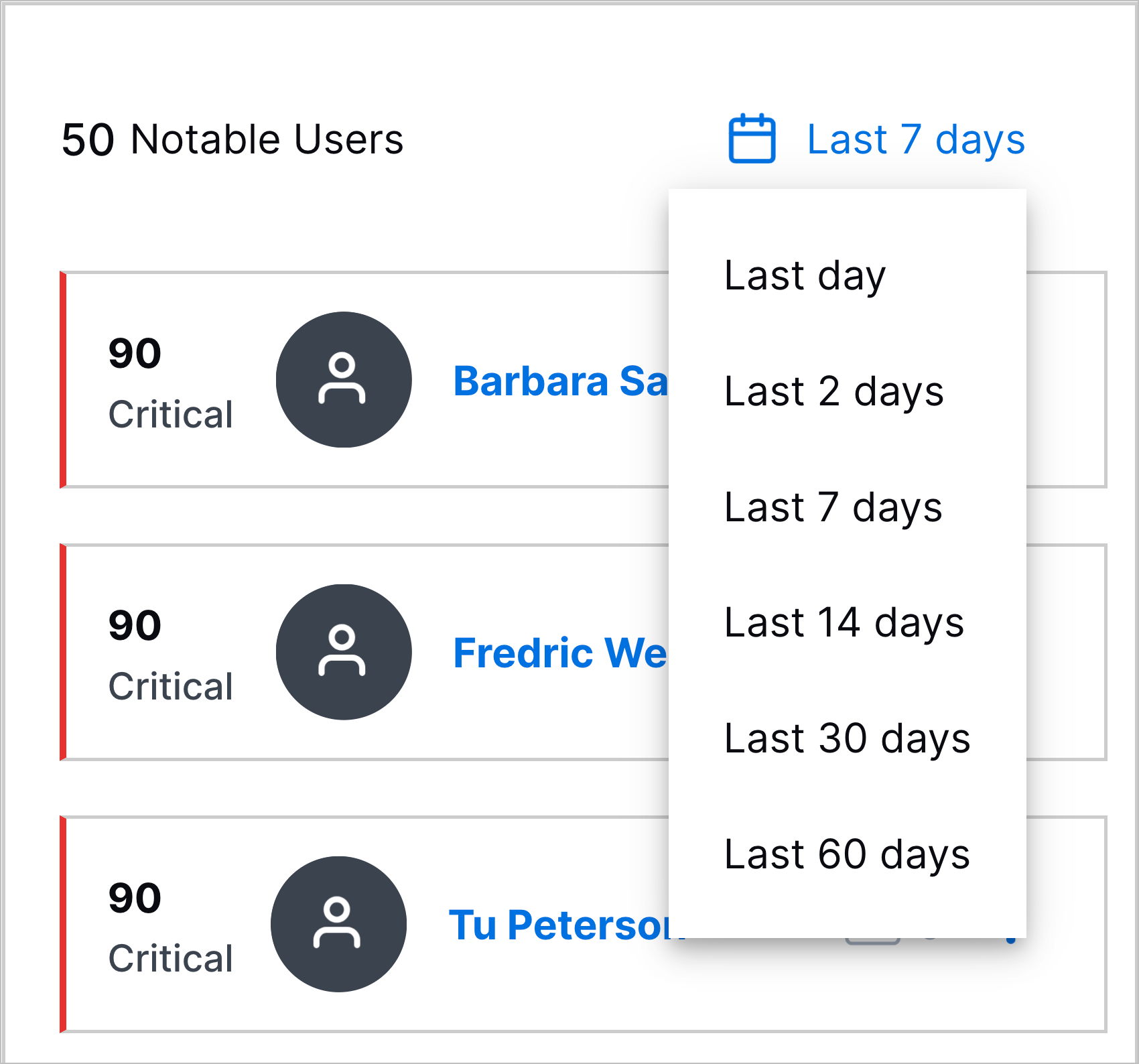
Watchlists | You can now monitor and quickly get an overview of entities of interest using watchlists.
Watchlists dynamically rank entities from highest to lowest risk score over a time frame you specify: the past day, two days, seven days, 14 days, 30 days, or 60 days.
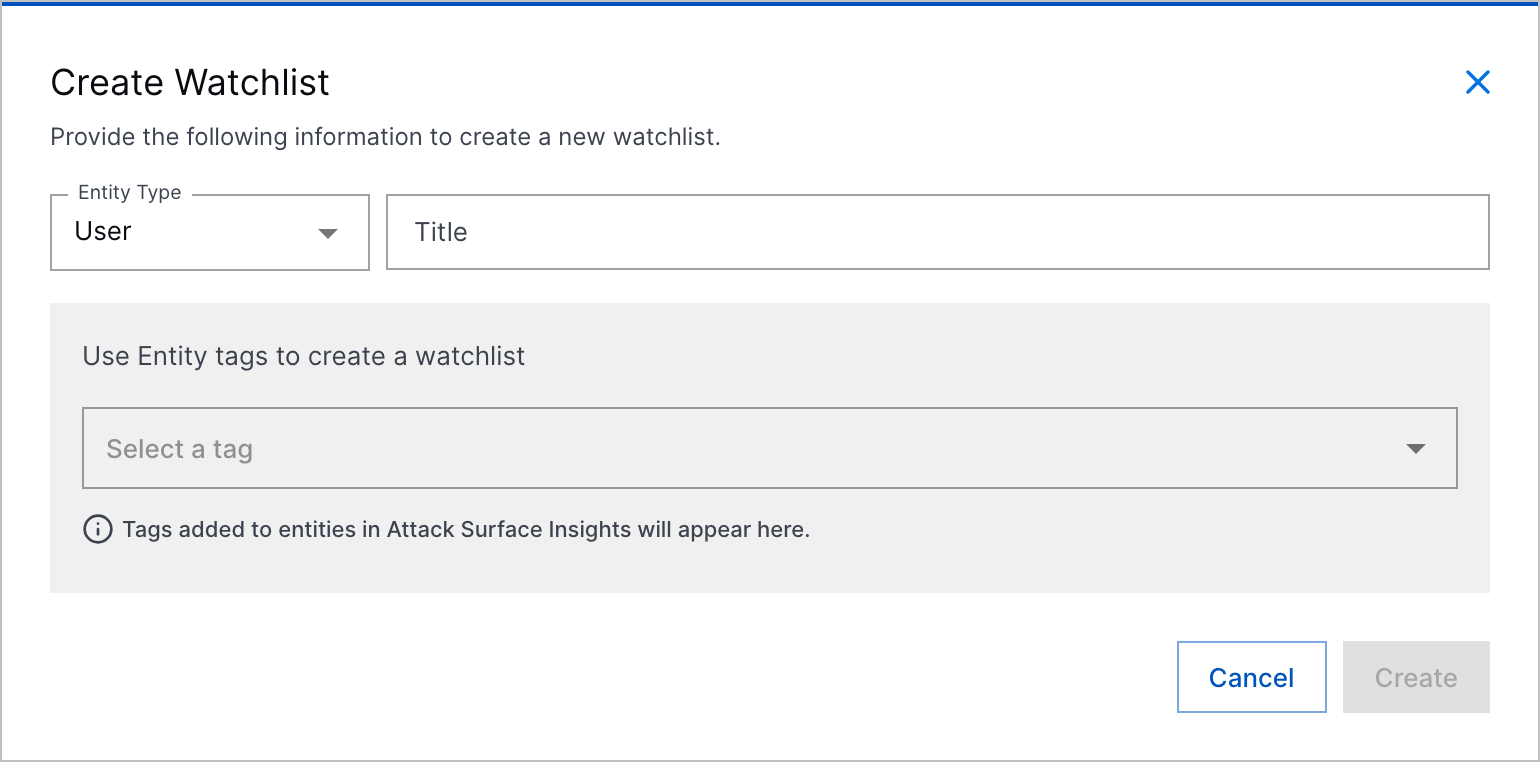
There are five pre-built watchlists for notable users, notable assets, executive users, privileged users, and service accounts. You can also create your custom watchlists based on tags applied to entities in Attack Surface Insights. After you create a watchlist, you can edit and delete it.
Watchlists are available only with a New-Scale Security Operations portfolio license. | |||
Attack Surface Insights Entity Tags in Threat Center | You can now find Threat Center cases or alerts related to groups of entities. When the detections of a case or alert are grouped by entity, the tags of that entity are automatically added to the tags of the case or alert. You can then use the tags to search for cases or alerts involving certain kinds of entities. Entity tags are copied to the case or alert. If you remove a tag from the entity, the tag remains in the case or alert. If you remove a tag from the case or alert, it remains in the entity. This feature is available only with a New-Scale Security Operations portfolio license. | |||
Alert Dismissal | To indicate that you reviewed an alert and other team members don't need to review it, you can now dismiss alerts. You can dismiss an individual alert or multiple alerts at once. 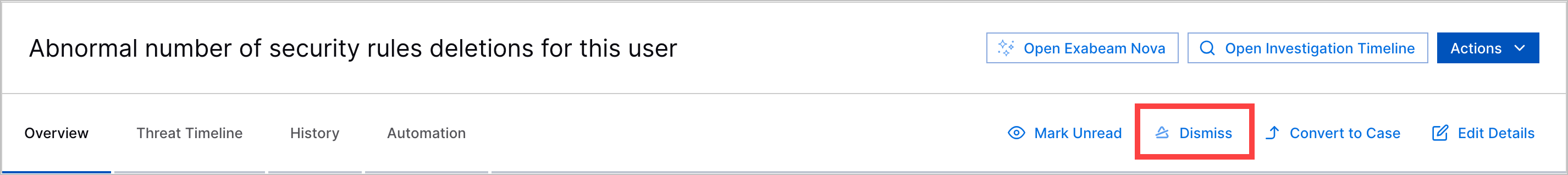 When an alert is dismissed, the dismissed reason, who dismissed the alert, and the date and time they dismissed the alert appears in the alert Overview tab. It is also recorded in the alert history. | |||
Alert Read and Unread Statuses | To track your alert triage workflow, you can now mark an alert as read and unread. An alert is automatically marked as read when you open it. After an alert is read, you can manually mark it as unread. 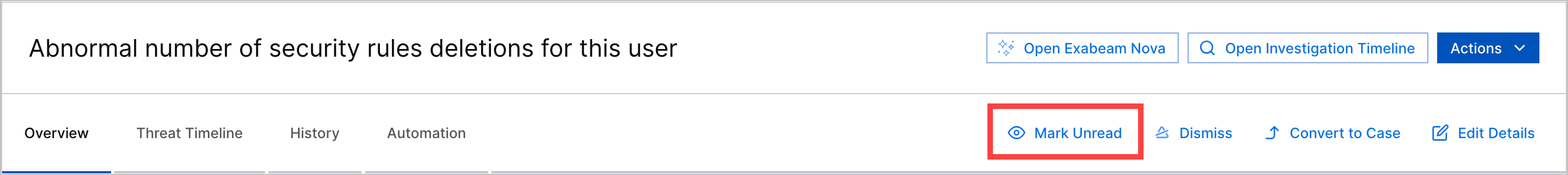 Dismissed alerts are automatically reverted to unread status when their risk scores increase by a percentage you specify. By default, the percentage is 10 percent. Any time an alert is marked as read or unread, it is recorded in the alert history. | |||
Alert Status Column | You can now view whether an alert is read, unread, or dismissed in the Alerts tab, under the STATUS column. 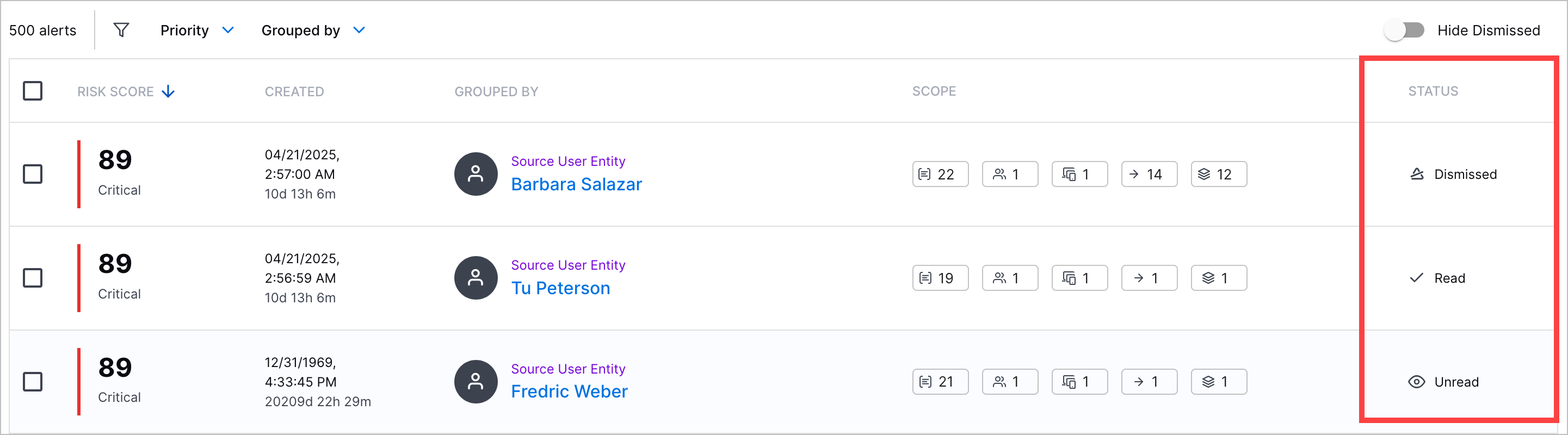 You can also search for alerts by status. To filter dismissed alerts from the list, toggle Hide Dismissed on. 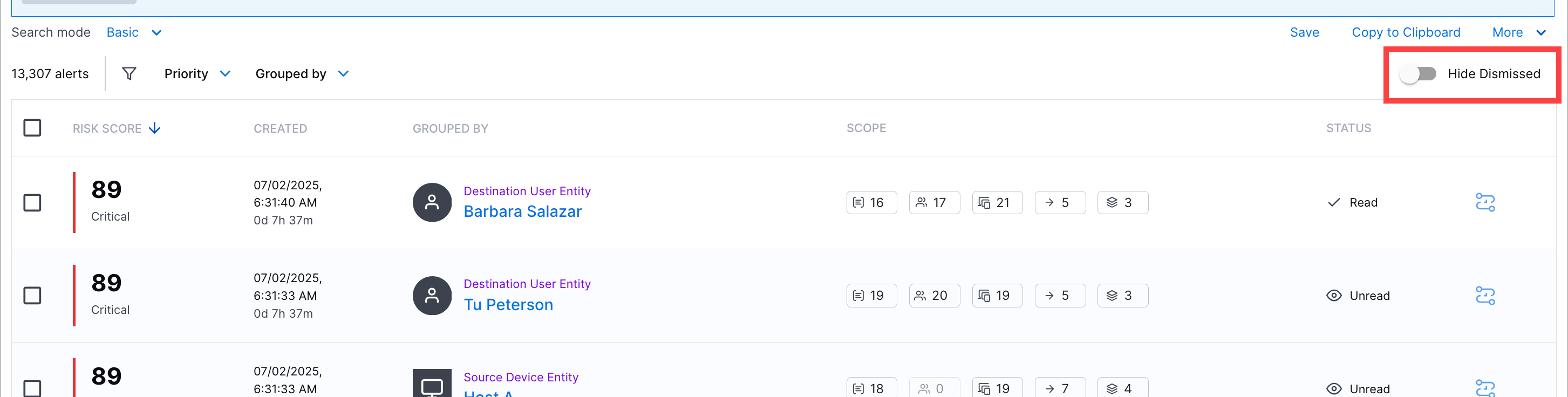 | |||
Permission for Sending Information to Webhooks | To send case or alert information to a webhook, you must have the Manage webhooks: Read, Write and Delete permission. |
Threat Detection Management
Feature | Description |
|---|---|
Correlation Rules Insights | To make informed decisions about authoring and tuning rules, you can now view insights about your correlation rules directly in the Correlation Rules tab, including:
|
Optional Exclusion Descriptions | When you create an exclusion, the description field is now optional. |
Resolved Issues
Site Collectors 2.9 Hot Fixes
Release Number | Hot Fix Description |
|---|---|
2.9.3 | Fixed an issue for MySQL, MSSQL, Oracle, and QRadar collectors to ensure accurate initialization of collector setup. |
2.9.2 | Fixed an issue for ngscd health check for backward compatibility for operating systems. |
2.9.1 | Addressed an issue to ensure more robust and consistent observability in Site Collectors. |
Site Collector 2.9: Security Vulnerabilities Remediated in May 2025
The Site Collectors 2.9 (May 2025) release includes remediated security vulnerabilities. For more information about Exabeam’s commitment to remediating vulnerabilities for Site Collector, see the Vulnerability Remediation Policy.
There are no open known CVEs in any container image (Nifi). Toolkit has been deprecated and is no longer in use hence no security vulnerabilities update is available for that.
The following table lists the CVEs remediated for the Nifi container and their severity.
Critical | High | Medium | Low |
|---|---|---|---|
Total: 0 | Total: 0 | Total: 3 | Total: 0 |
– | – |
|