- 2026 Release Notes
- 2025 Release Notes
- December 2025
- November 2025
- October 2025
- September 2025
- August 2025
- July 2025
- June 2025
- May 2025
- April 2025
- March 2025
- February 2025
- January 2025
- Known Issues
June 2025
The New-Scale Security Operations Platform includes the following addressed features and new features for June 2025.
Attack Surface Insights
Feature | Description |
|---|---|
User Risk Trend Chart | To understand a user entity's history and identify trends in their level of risk, you can now view a line chart of a user entity's risk score over time. 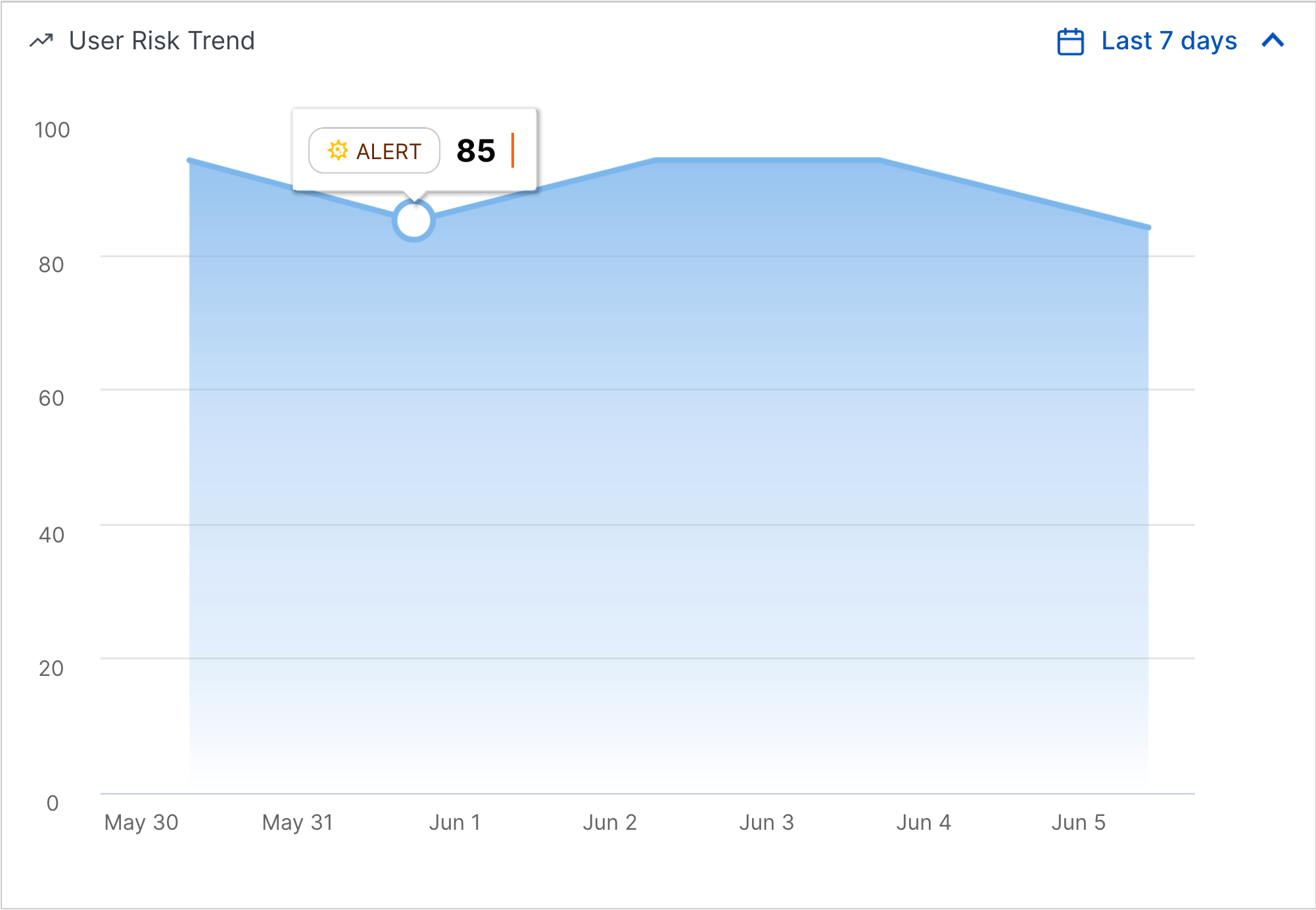 You can view the user entity's risk score over a time frame you specify: the past seven days, two weeks, one month, two months, or three months. 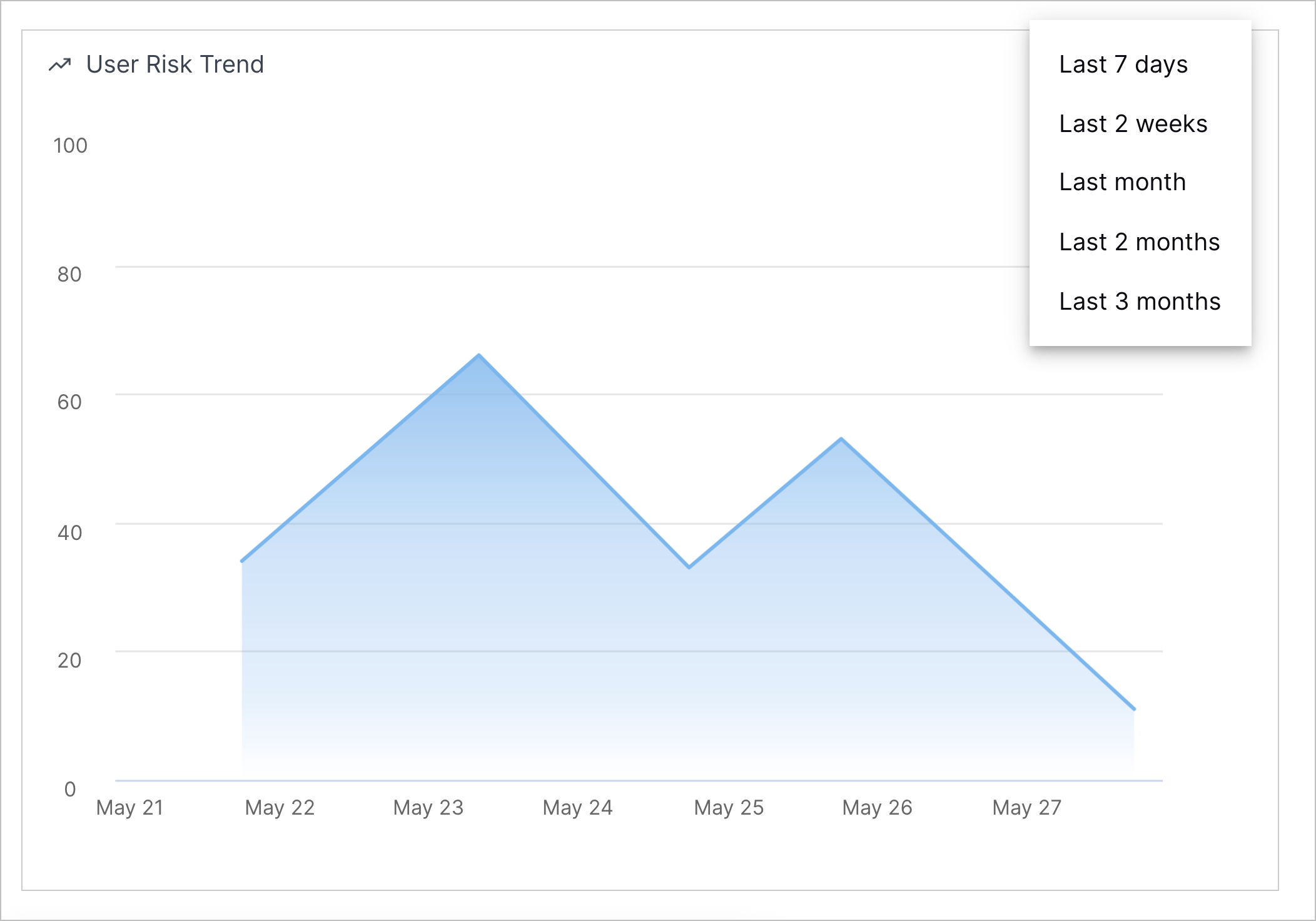 You can also navigate directly to the Threat Center case or alert associated with the risk score for a given day. |
Associated Open Threat Center Cases in User Entity Details | To start investigating a user entity from Attack Surface Insights, you can now view the number of open Threat Center cases whose detections are grouped by the user entity and created during the time frame selected in the User Risk Trend chart: 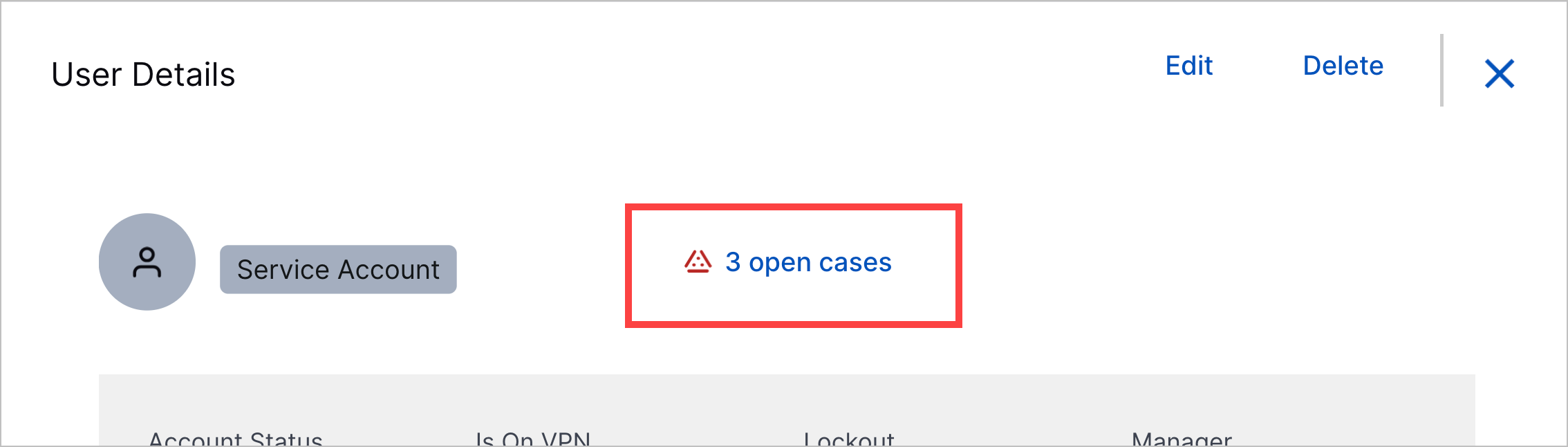 To navigate directly to those cases in the user entity details, click <#> open cases. If there are no open cases in the time frame, the information doesn't appear. |
Entity Deletion | To remove obsolete entities created due to parsing or enrichment issues, you can now delete entities.  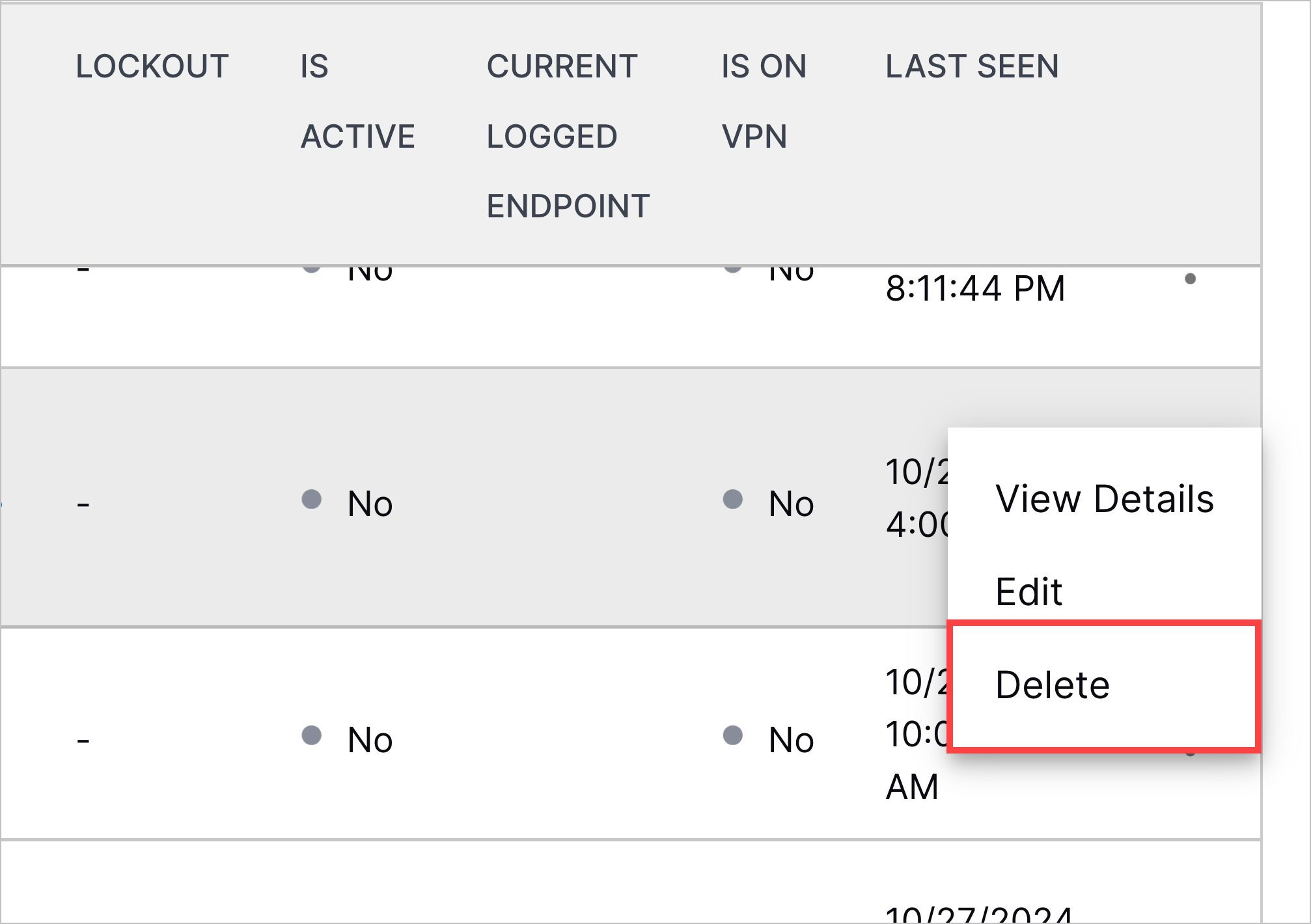 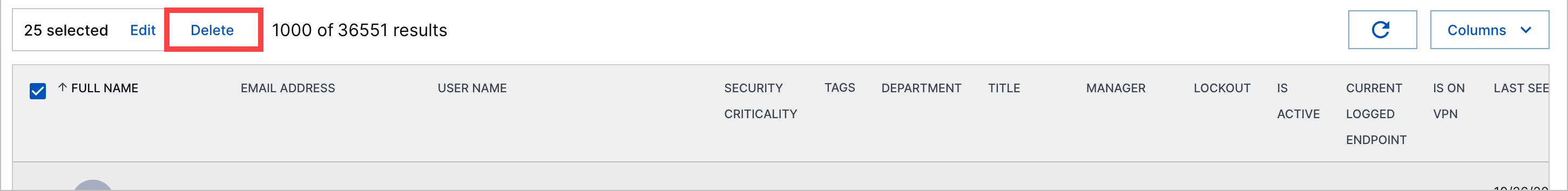 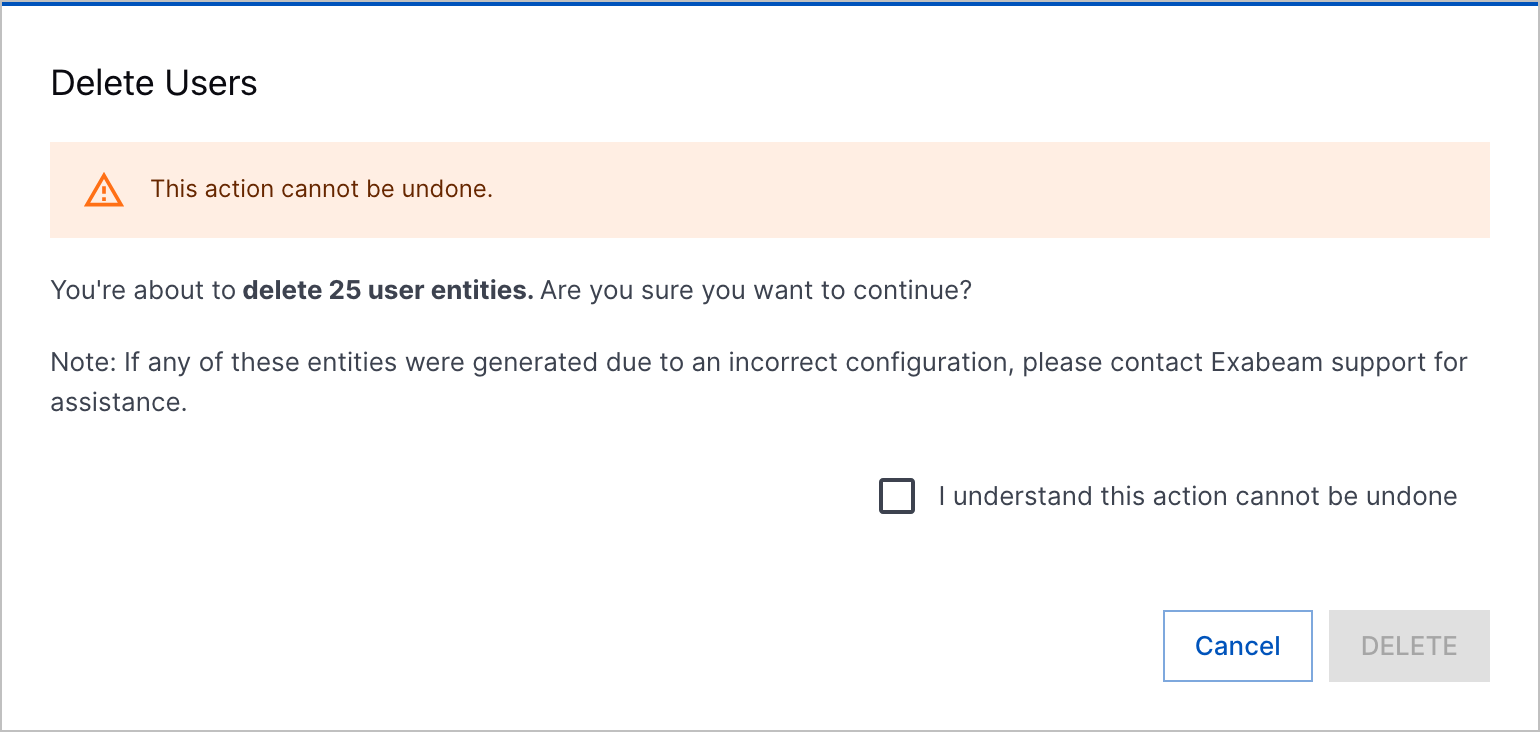 |
Cloud Collectors
Feature | Description |
|---|---|
Cisco Secure Endpoint Cloud Collector | The Cisco Secure Endpoint Cloud Collector now available as part of Cloud Collectors to facilitate ingestion of security events from Cisco Secure Endpoint V1 APIs. |
CrowdStrike Context Cloud Collector | The CrowdStrike Context Devices Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of data from a CrowdStrike source. The use of a cloud collector allows you to ingest CrowdStrike device data without the need for the Exabeam Ingester for CrowdStrike license add-on. The corresponding context table in the Context Management application will process the data and map it to a standardized set of attributes. NoteIf you opt to use the cloud collector method to ingest CrowdStrike data, the collector must be created before the context table. If you previously onboarded a CrowdStrike context table and you want to integrate with the cloud collector, you must delete the context table and recreate it after the CrowdStrike cloud collector is created and running. For information about creating the context table, see CrowdStrike Context Tables in the Context Management Guide. |
Trellix Cloud Collector | The Trellix Endpoint Security Cloud Collector now available as part of Cloud Collectors to facilitate ingestion of security alerts from Trellix APIs. |
Early Access Collectors | |
Anomali Cloud Collector | The Anomali Cloud Collector is now available is now available, as part of Cloud Collectors Early Access program, to facilitate threat intelligence data collection from an Anomali source that supports the STIX/TAXII framework. You can opt to collect data about either IP addresses or domains. You can also opt to automatically generate a corresponding Anomali context table in the Context Management application that will process the data and map it to a standardized set of attributes. The context table will have the same name as the cloud collector. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
AWS GuardDuty Cloud Collector | The AWS GuardDuty Cloud Collector is now available as part of Cloud Collectors Early Access program to facilitate ingestion of GuardDuty Findings from AWS S3 bucket. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
AWS Security Lake Cloud Collector | The AWS Security Lake Cloud Collector is now available as part of Cloud Collectors Early Access program to facilitate ingestion of security events from AWS S3 Security Lake bucket. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Tenable Cloud Collector | The Tenable Cloud Collector is now available as part of Cloud Collectors Early Access program to facilitate ingestion of vulnerability events from Tenable APIs. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Zoom Cloud Collector | The Zoom Cloud Collector is now available as part of Cloud Collectors Early Access program to facilitate ingestion of events from the sign-in/sign-out activity and operational logs endpoints. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Context Management
Feature | Description |
|---|---|
Anomali Context Tables | Context Management now supports a preconfigured onboarding experience for Anomali context tables. These tables process data that is ingested by a corresponding Anomali cloud collector that supports the STIX/TAXII framework. By default these context tables process a predetermined set of IP or domain attributes from the source collector and then map these attributes to a set of standardized Exabeam target attributes. The Anomali context table onboarding via cloud collector is available as part of the Early Access program. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program, in the Cloud Collectors Administration Guide. For more information, see Anomali Context Tables in the Context Management Guide. |
CrowdStrike Device Context Table via Cloud Collector | Context Management now supports onboarding a CrowdStrike device context table with data ingested by a cloud collector, without the need for the Exabeam Ingester for CrowdStrike license add-on. The context table processes data that is ingested by a corresponding CrowdStrike Context cloud collector from a CrowdStrike source. By default the context table processes a predetermined set of device attributes from the source collector and maps them to a set of standardized Exabeam target attributes. For more information and prerequisites, see CrowdStrike Context Tables in the Context Management Guide. NoteIf you opt to use the cloud collector method to ingest CrowdStrike data, the collector must be created before the context table. If you previously onboarded a CrowdStrike context table and you want to integrate with the cloud collector, you must delete the context table and recreate it after the CrowdStrike cloud collector is created and running. For information about creating the cloud collector, see CrowdStrike Context Cloud Collector in the Cloud Collectors Administration Guide. |
Correlation Rules
Feature | Description |
|---|---|
New and Updated Correlation Rule Templates | You can now better identify insider threats with new and updated correlation templates. New correlation rule templates include:
Updated correlation rule templates include:
|
Dashboards
Feature | Description |
|---|---|
Increased Count Maximum for the Anomalies Dashboard | The maximum end of the Trigger Count filter has been increased to a value of 10,000 in the pre-built Anomalies dashboard. This increase allows more accurate anomaly trigger rate reporting.  For more information, see Anomalies Dashboard in the Dashboards Guide. |
New Compliance Dashboards Available | The following pre-built dashboards are available so that analysts and management can monitor compliance-focused activity on a recurring basis. These dashboards can be used to look for anomalous behavior, system health, and environmental trends. They can also be used to produce reports and provide evidence to assessors and auditors as needed.
For more information about the pre-built compliance dashboards, see Compliance Dashboards in the Dashboards Guide. |
New Bulk Actions Available for Scheduled Reports | The following new bulk actions are now available for the Scheduled Reports tab:
For more information, see Configure and Manage Scheduled Reports in the Dashboards Guide. |
Log Stream
Feature | Description |
|---|---|
Expanded Out-of-the-Box Access to Creating Custom Enrichment Rules | Access to creating custom rules has been expanded. Previously, this capability was available out-of-the-box only to those with the New-Scale Analytics license. Access is now available with any New-Scale license in the Exabeam portfolio: New-Scale SIEM, New-Scale Fusion, or New-Scale Analytics. The Enrichments tab provides access to define enrichment rules inside the Log Stream application. You can configure both the conditions an event must meet for a specific enrichment to be applied and the mapping that the enrichment rule will perform. This functionality provides access to do the following:
For more information, see Enrichments in the Log Stream Guide. |
Improvements to Defining Custom Enrichment Rules | The following new functionality has been added to the process of defining a custom enrichment rule:
For more information about these capabilities, see Define an Enrichment Rule in the Log Stream guide. |
Multi-Org Management
Feature | Description |
|---|---|
Support for Custom User Roles in Multi-Org Management | You can now create custom user roles for Multi-Org Management. If the available default user roles do not provide the permissions you need, you can create custom roles and configure them with permissions tailored to your specific need. You can then assign the custom role to users in the parent or child organizations. For more information, see User Roles for Multi-Org Management. |
Outcomes Navigator
Feature | Description |
|---|---|
Exabeam Nova Analyst Assistant | You can now quickly learn and get answers to questions about your overall security posture using a security-trained AI assistant. Prompt Exabeam Nova Analyst Assistant with a message or query, and it interprets information from the MITRE ATT&CK Coverage Summary or Use Case Coverage Summary to generate a natural language response. 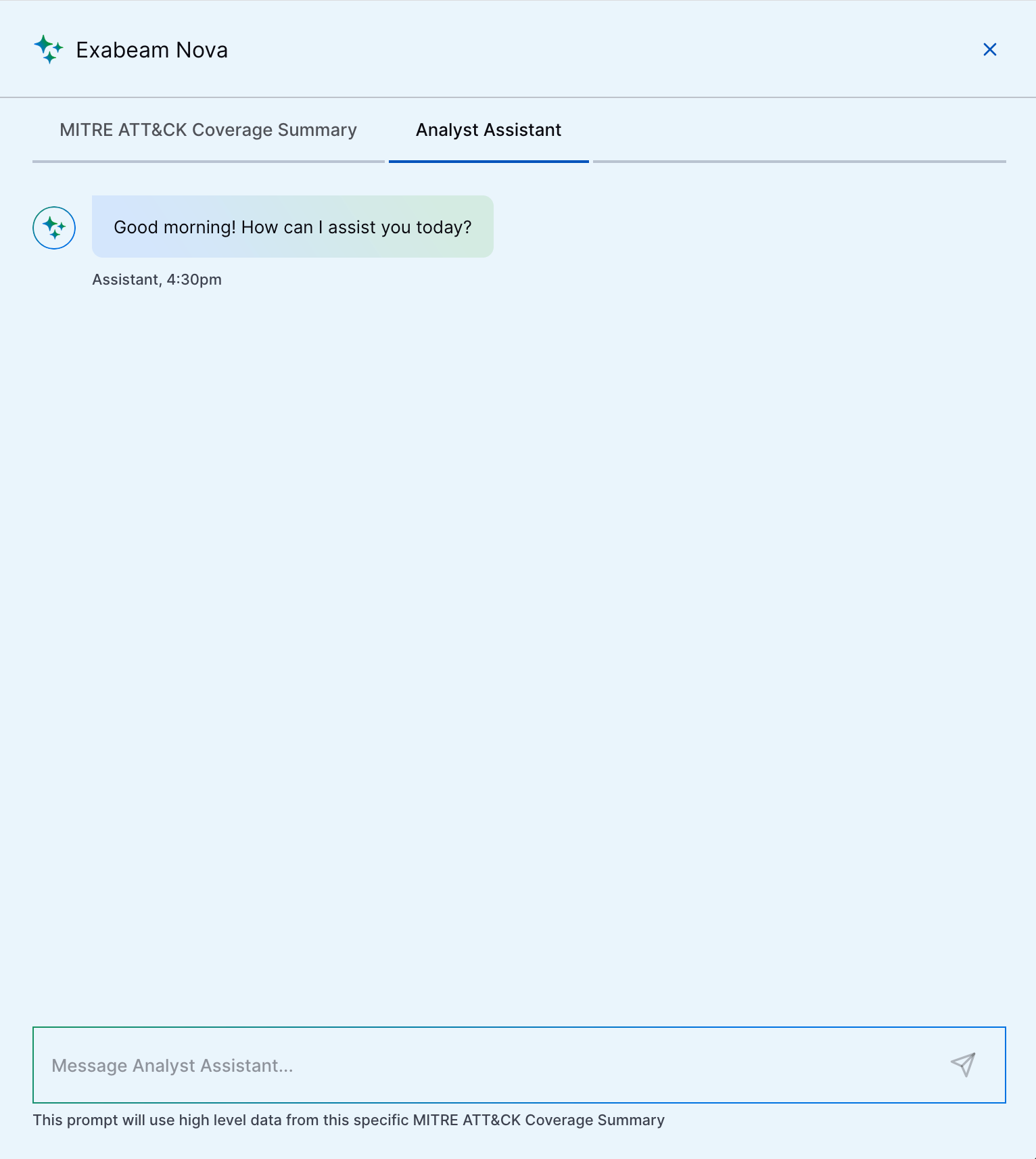 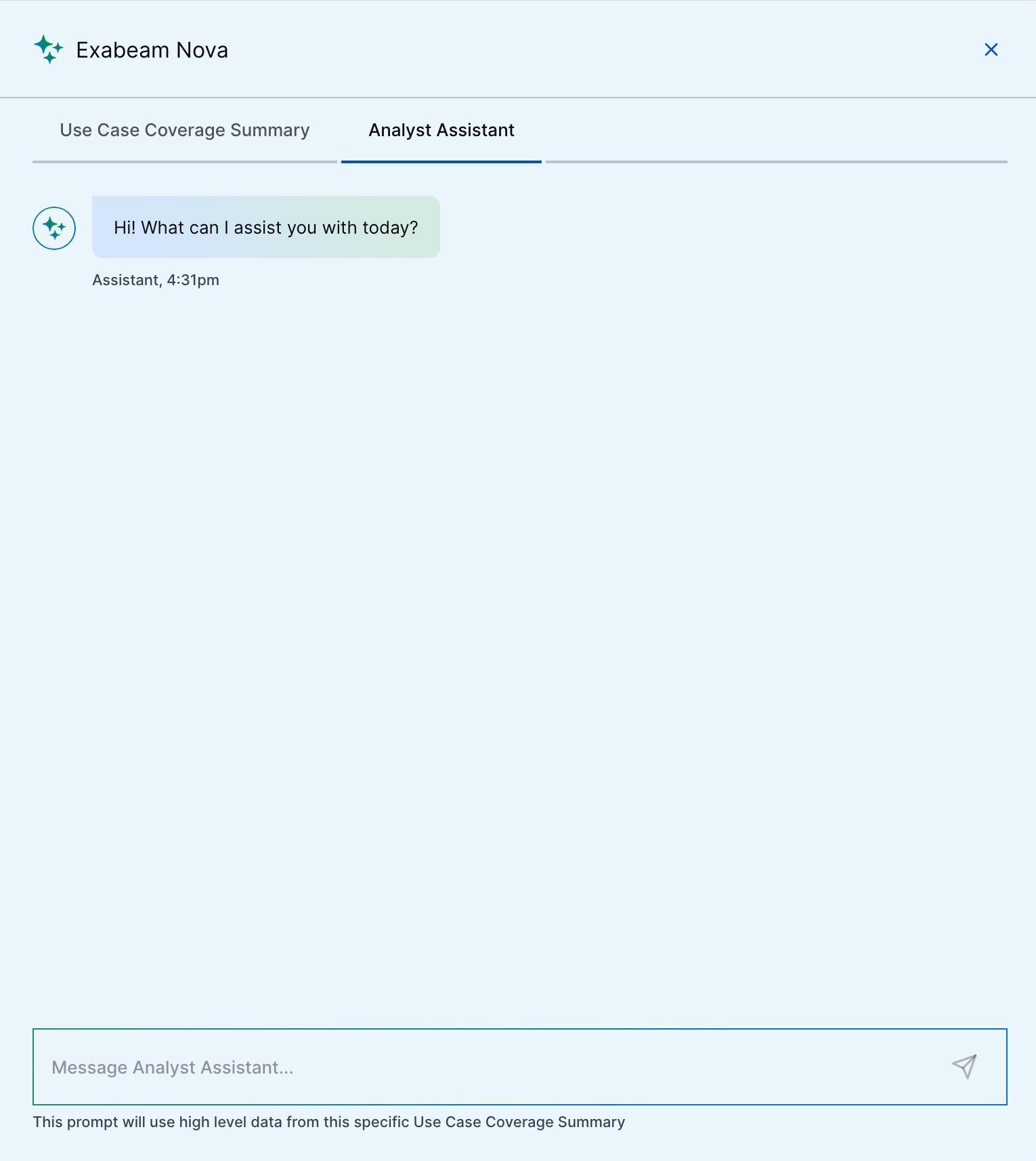 |
Search
Feature | Description |
|---|---|
Expanded Access to Timeline View of Search Results | Exabeam has expanded access to the Timeline view of search results. Previously, this view of results was available only to those with one of the New-Scale licenses. Access is now available with any license in the Exabeam portfolio of licenses. The Timeline view brings the investigational timeline experience into the Search application. Analysts and threat hunters can use the Timeline view as a starting point for investigating risky or anomalous events while still leveraging the granular filtering capabilities of the Search application. The Timeline view is designed specifically with this task in mind. It's visually organized so that detection events are easy to spot and investigate. You can drill into the detections or the associated events to find detailed information and data insights. For more information, see Timeline View of Search Results in the Search Guide. |
Support for Sort Order Selection of Search Results | A configurable sort order option is now available for search results. The new sort order selector is located in the search bar for Basic, Advanced, and Natural Language modes. It includes options to sort chronologically to show the most recent or the oldest results. The sort happens on the server-side when you run your search, so results display the newest or oldest results from the entire set of results. For more information, see Search Bar in the Search Guide. |
Updates to the Display of Detections in the Timeline View of Results | To enhance the chronological aspect of the Timeline view in Search, detections listed on the right-hand side of the view are now shown only on the row of the latest associated event. Detections can be triggered by multiple events and, previously, they were displayed in association with each triggering event. This led to a confusing view of the chronology of detections. To resolve this confusion and simplify the view, a detection is now displayed only on the chronologically latest associated event. For more information about the Timeline view, see Timeline View of Search Results in the Search Guide. |
Improved Visibility for Site Tags in Search Results | Site tags are now more easily visible in both the Timeline View and the List View of search results. If you use unique site names to manage access to data from specific collector sources in your environment, tags with site names are now clearly visible on each event ingested by a tagged cloud or site collector. You can also toggle the display of the tags on or off in the search results. For more information, see either Timeline View of Search Results or List View of Search Results in the Search Guide. |
Context Searching Using Any Table Type | When searching context values, you can now add any type of context table to a search query. You can search for data in collector-base context tables, in custom or filtered context tables, or in pre-built context tables. For more information, about adding context tables to Basic or Advanced search queries, see Context Tables in Search in the Search Guide. |
Service Health and Consumption
Feature | Description |
|---|---|
Notification for Exceeding Long Term Search Quota | The Long-Term Consumption Details page now displays notifications when you reach 100% of your long-term search quota or exceed the allowed quota, based on your Long Term Search and Long Term Storage licenses. The notifications inform you about following cases with the recommended action.
|
Enhancements for Public API | The new set of Public APIs are introduced for License Consumption endpoint to read license consumption information, including:
|
Site Collectors 2.10
Feature | Description |
|---|---|
Upgradation to NiFi 2.4 | Based on the vulnerability remediation policy, the version of Apache NiFi is upgraded to the latest available version 2.4. |
Threat Detection Management
Feature | Description |
|---|---|
New and Updated Correlation Rule Templates | You can now better identify insider threats with new and updated correlation templates. New correlation rule templates include:
Updated correlation rule templates include:
|
Resolved Issues
Site Collectors 2.10 Resolved Issues
ID | Description |
|---|---|
ENG-68402 | Implemented mandatory Kafka topic selection while configuring the Kafka Collector to enable log retrieval from the specified topic. |
Site Collector 2.10: Security Vulnerabilities Remediated in June 2025
The Site Collectors 2.10 (June 2025) release includes remediated security vulnerabilities. For more information about Exabeam’s commitment to remediating vulnerabilities for Site Collector, see the Vulnerability Remediation Policy.
Known CVE - CVE-2025-48734. This is a NiFi CVE. Site Collector uses the latest NiFi version 2.4.0 and will update to the new version after NiFi provides a fix in an upcoming NiFi release.
Toolkit has been deprecated and is no longer in use hence no security vulnerabilities update is available for that.
The following table lists the CVEs remediated for the Nifi container and their severity.
CVEs for NiFi
Critical | High | Medium | Low |
|---|---|---|---|
Total: 0 | Total: 0 | Total: 9 | Total: 1 |
– | – |
| CVE-2024-58237 |
