- 2026 Release Notes
- 2025 Release Notes
- December 2025
- November 2025
- October 2025
- September 2025
- August 2025
- July 2025
- June 2025
- May 2025
- April 2025
- March 2025
- February 2025
- January 2025
- Known Issues
February 2025
The New-Scale Security Operations Platform includes the following addressed features and new features for February 2025.
Automation Management
Feature | Description |
|---|---|
New Region Support for the UK | Support for Automation Management now extends to the UK region. You can now access and use Automation Management in the UK. |
Cloud Collectors
Feature | Description |
|---|---|
Cisco Meraki Cloud Collector | The Cisco Meraki Cloud Collector is now available as part of Cloud Collectors to facilitate data collection from security events, alerts, configuration changes, and networks from Cisco Meraki APIs. |
Mimecast Cloud Collector | The Mimecast Cloud Collector is now available as part of Cloud Collectors Early Access program to facilitate data collection from the data sources Archive Search Logs, TTP Attachment Protection Logs, TTP Impersonation Protect Logs, TTP URL Logs, SIEM Logs, Archive Message View Logs, and Audit Events.. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
REST API Cloud Collector | The REST API Cloud Collector is now available as part of Cloud Collectors Early Access program to facilitate data collection from REST API endpoints from a broad range of vendors and products. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Sophos Cloud Collector | The Sophos Cloud Collector is now available as part of Cloud Collectors Early Access program to facilitate data collection from the data sources alerts and events. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Correlation Rules
Feature | Description | |
|---|---|---|
Stopped and Testing Statuses | You can now better understand the state of a correlation rule with two new statuses: Stopped and Testing. The Stopped status indicates that the rule has triggered more than 50 times in five minutes and has automatically been disabled. The Testing status indicates that the rule is enabled in test mode and its outcomes are suppressed.  You can also filter correlation rules by the new statuses.
| |
Select Outcomes Enhancements | When you create or edit a correlation rule, the step to Select Outcomes now clearly explains what happens when a rule triggers and the possible outcomes:
| |
Correlation Rule Details Severity Enhancement | When you view correlation rule details, you can now more quickly identify the rule severity: 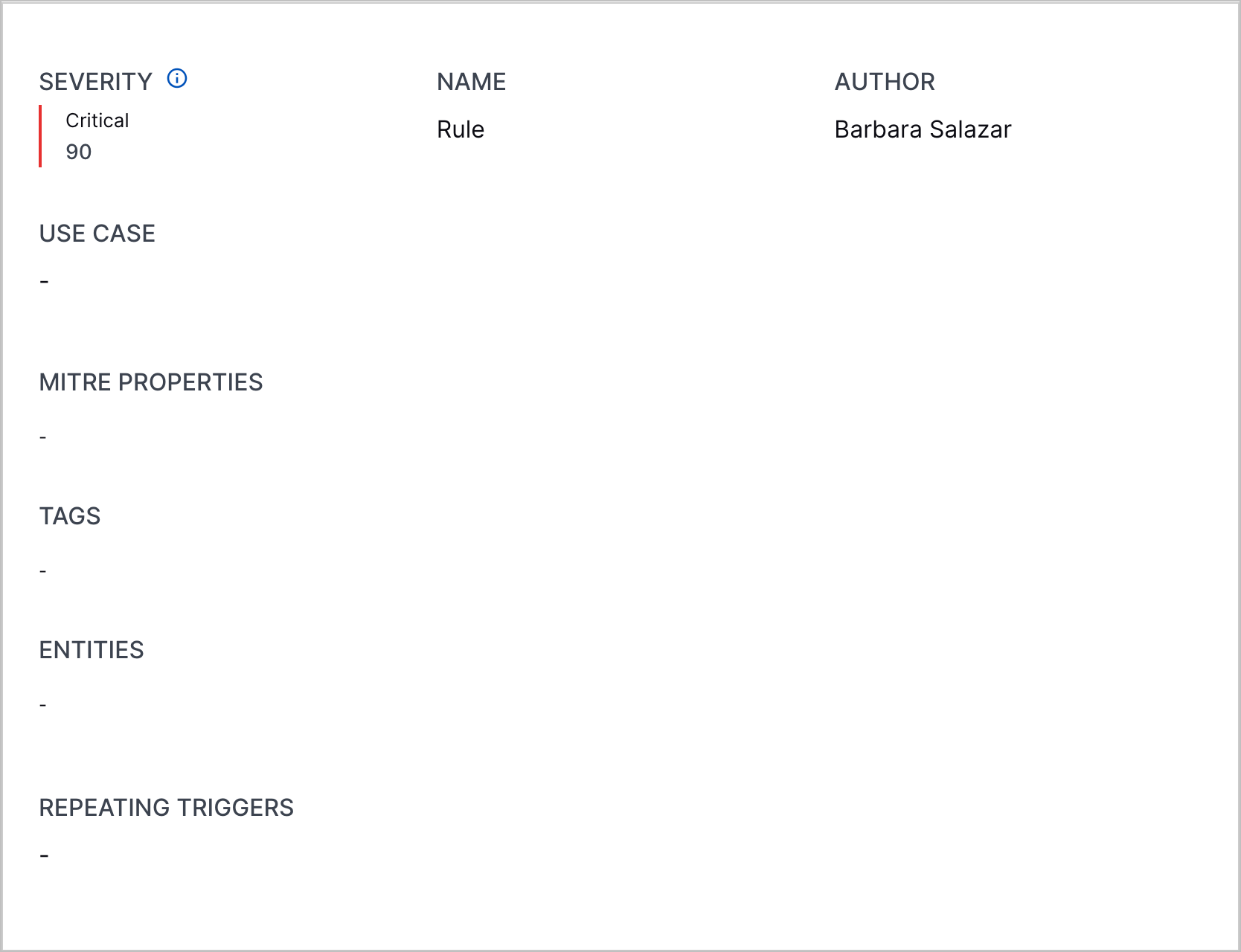
| |
Rule Evaluation Delay Explanation | When you create or edit a correlation rule, the step to configure a rule evaluation delay now clearly explains what rule evaluation delay is and that rules are delayed from evaluating events for seven minutes by default. 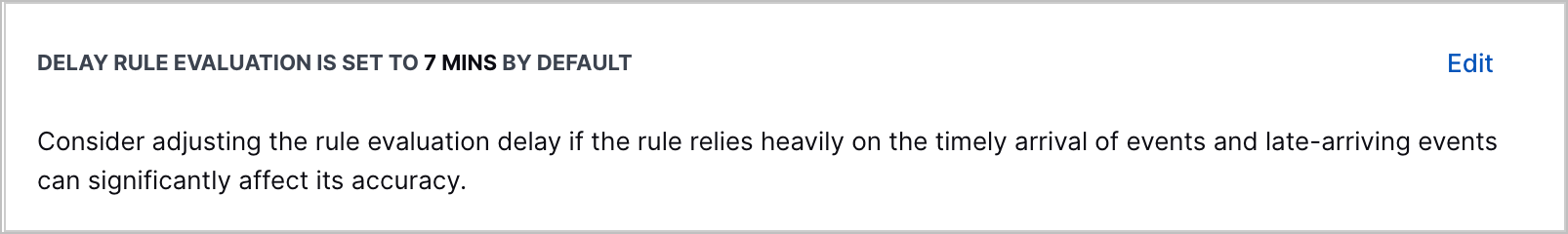
| |
Rule Description Enhancements | You can now add more information to a correlation rule with descriptions. When you create or edit a correlation rule, you can now add a description about the rule. 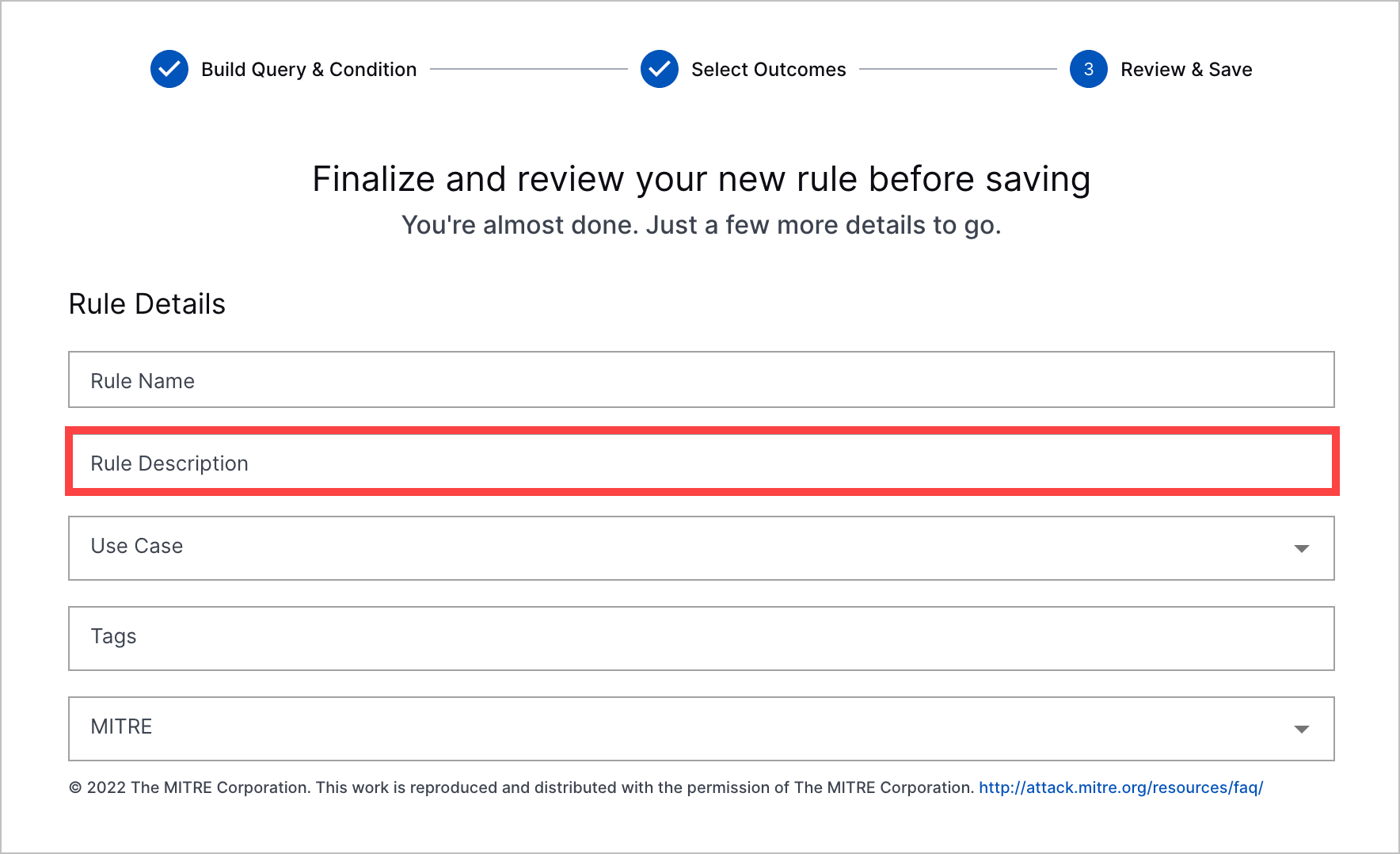 This description appears in the list of correlation rules and rule details.  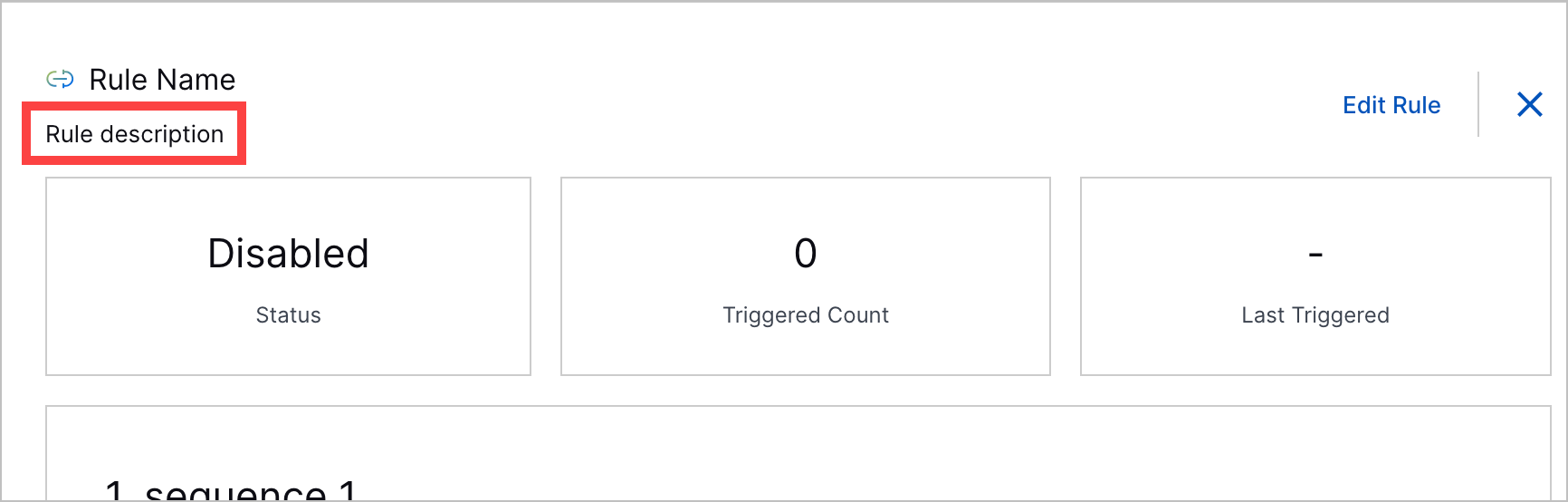 If you use a correlation rule template, the correlation rule template description is automatically reused as the description of your new correlation rule. | |
Triggered Value to Search Navigation | To view all events related to a correlation rule, you can now navigate to Search using a link next to the number times a rule has been triggered. The query automatically entered in Search is rules.rule: "<rule name>". The link appears in the list of correlation rules: 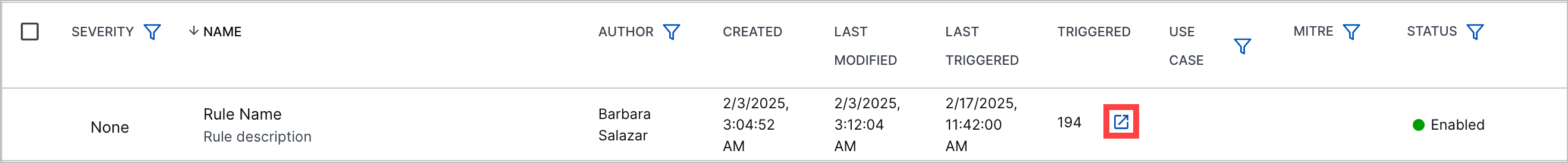 The link also appears when you view the correlation rule details: 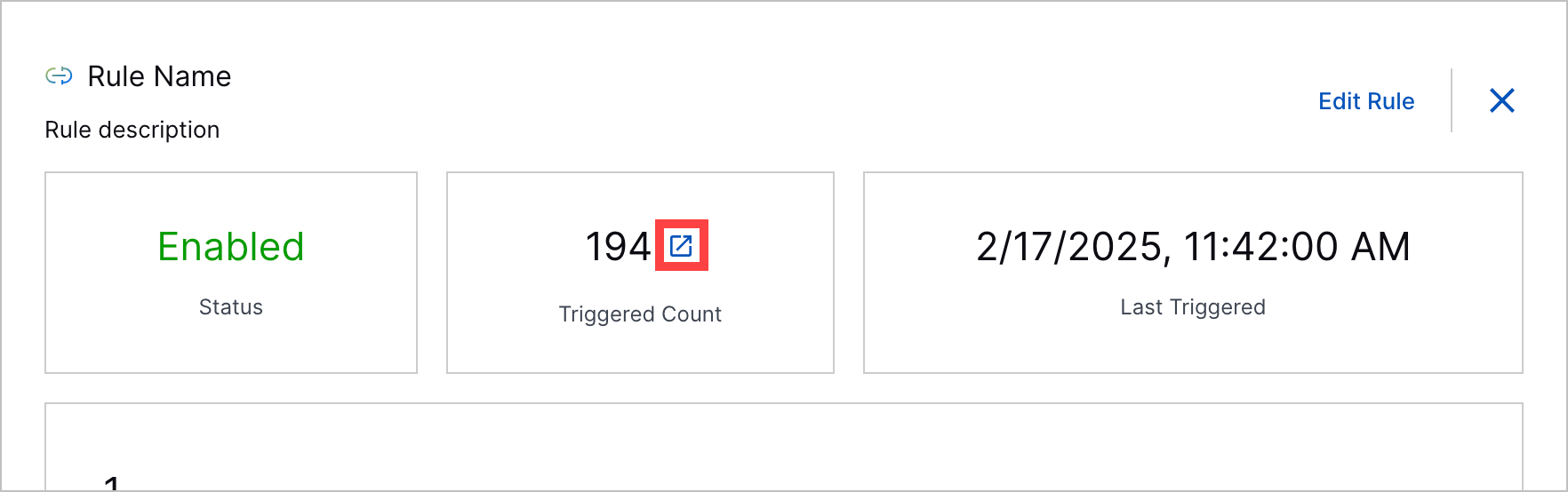 | |
Email Notification Address Change | Email notifications sent as an outcome are now sent from [email protected]. To ensure any rules for filtering emails or creating third-party tickets work properly, ensure they use the new email address. | |
New Region Support for the UK | Support for Correlation Rules now extends to the UK region. You can now access and use Correlation Rules in the UK. |
Dashboards
Feature | Description |
|---|---|
Auto-Creating a Threat Center Alert Visualization from a Natural Language Prompt | As part of Exabeam Nova and its set of AI-driven capabilities, the use of the natural language prompt for auto-creating a dashboard visualization has been expanded to an additional data model. You can now use the natural language prompt for the Threat Center Alerts data model. This enhancement means that you can leverage the natural language prompt in the Dashboard application to describe, in plain language, the Threat Center Alerts data you want to visualize. Based on this plain language prompt, the measures, dimensions, filters, and even the chart type are configured automatically. NoteThis auto-create option is currently available to create visualizations only for the Event Store Event data model and the Threat Center Alerts data model. You must be using Threat Center to access the Threat Center Alerts data model. If the automatically generated visualization does not produce the data you want to visualize, you can modify the visualization settings manually to produce exactly the desired results. For more information about auto-creating visualizations, see Auto-Create a Visualization from a Natural Language Prompt in the Dashboards Guide. |
Search
Feature | Description |
|---|---|
Support for Device Context Tables | You can now include device context tables in both Basic and Advanced search queries, allowing you to search for information about devices in your environment. Specifically, you can now search for results in the following types of device context tables:
For more information, see Context Tables in Search in the Search Guide. |
Service Health and Consumption
Feature | Description |
|---|---|
Export License View Details to PDF | The License View dashboard now includes an option to export all its details as a PDF file. |
Improvements for License View | The License View dashboard now provides you with a new section Regions Deployed that displays region name in which the New-Scale Security Operations Platform is deployed, such as US West, US East, Canada, Europe, Switzerland, Saudi Arabia, Singapore, Japan, and Australia. |
Site Collectors 2.6
Feature | Description |
|---|---|
Kafka Collector | The Kafka Collector is now available as part of Site Collectors to facilitate the collection of logs in any text format from your Kafka server. |
Archive Windows Collector | The Archive Windows Collector is now available as part of Site Collectors to facilitate the collection of log events from the following types of archived log files: *.gz, *.tar, *.tar.gz, *.gzip, *.rar, *.7z. |
Archive Linux Collector | The Archive Linux Collector is now available as part of Site Collectors to facilitate the collection of log events from archived log sources *.7z, *.arj, *.bzip2, *.cab, *.gzip, *.iso, *.lzh, *.rar, *.gz, *.tar, *.tar.gz, *.z, and *.zip. |
Windows File Collector Recovery | You can now update an agent collector from the overview page to recover the collector if it does not collect logs while running. Previously, resolving Windows File Collector log ingestion issues required manual intervention. |
Ubuntu 24.04 Support for OVA | Updated the existing Ubuntu 20.04 version to Ubuntu 24.04 for OVA, for better performance, security, and software support. |
Threat Center
Feature | Description | |
|---|---|---|
Case ID Enhancement | To ensure all cases have a human-readable identifier to which you can refer, all cases are now automatically assigned a unique number as the case ID. You can view the case ID in the list of cases, in a case, emails sent from the case, and webhook notifications sent from the case. You can also search for a case using its case ID. Case IDs for existing cases remain the same and won't have new case IDs retroactively assigned to them. | |
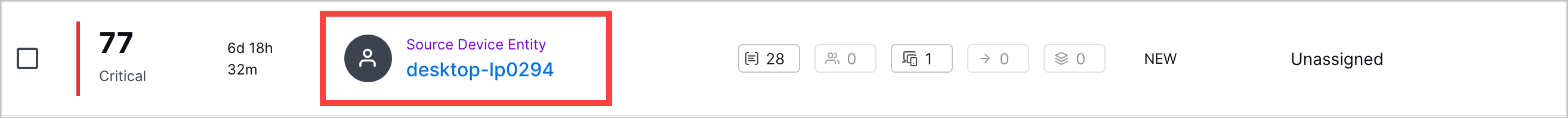
Entity Attribute Enhancements | If a case or alert contains detections grouped by entity, you can now learn more about the entity and view the entity attributes directly in Threat Center:
| |
New Region Support for the UK | Support for Threat Center now extends to the UK region. You can now access and use Threat Center in the UK. |
Threat Detection Management
Feature | Description |
|---|---|
Correlation Rules Stopped and Testing Statuses | You can now better understand the state of a correlation rule with two new statuses: Stopped and Testing. The Stopped status indicates that the rule has triggered more than 50 times in five minutes and has automatically been disabled. The Testing status indicates that the rule is enabled in test mode and its outcomes are suppressed.  You can also filter correlation rules by the new statuses. 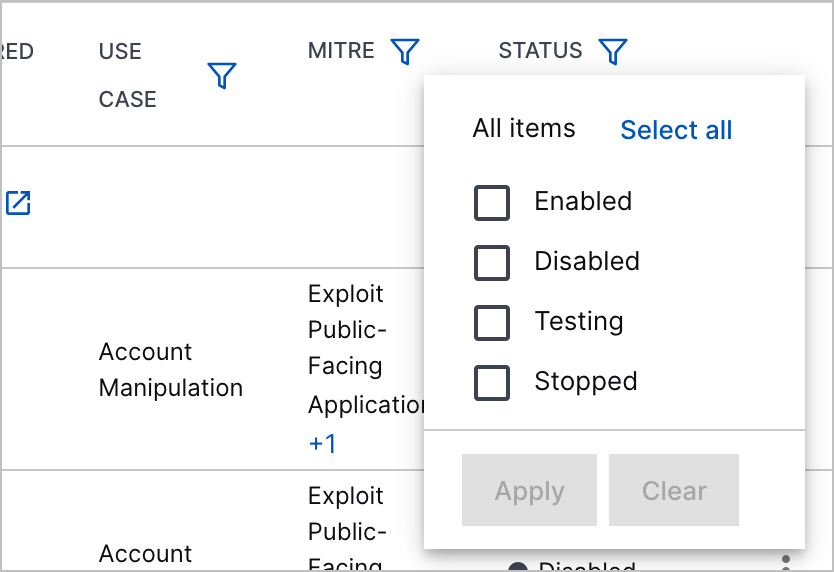 |
Apply Analytics Rule Updates Without Training | To immediately apply changes to analytics rules, minimize disruptions to other Exabeam applications, ensure the analytics engine continues to run in real time, and ensure you don't use any of your entitled training days, you can now apply analytics rules changes without training the analytics engine. When you apply changes to enabled rules in bulk, you now have the option to select Apply Changes Without Training. |
Correlation Rules Select Outcomes Enhancement | When you create or edit a correlation rule, the step to Select Outcomes now clearly explains what happens when a rule triggers and the possible outcomes:
|
Correlation Rule Details Severity Enhancement | When you view correlation rule details, you can now more quickly identify the correlation rule severity: 
|
Correlation Rule Evaluation Delay Explanation | When you create or edit a correlation rule, the step to configure a rule evaluation delay now clearly explains what correlation rule evaluation delay is and that correlation rules are delayed from evaluating events for seven minutes by default.  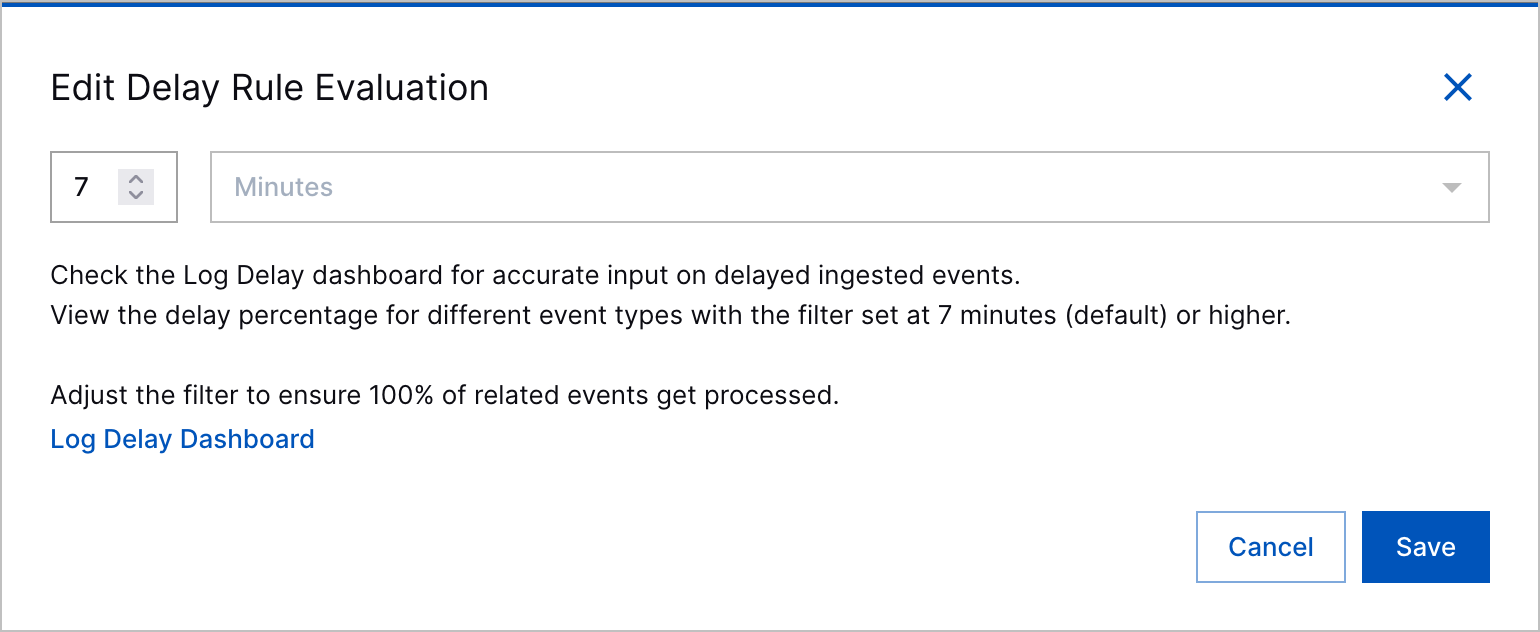 |
Correlation Rule Description Enhancements | You can now add more information to a correlation rule with descriptions. When you create or edit a correlation rule, you can now add a description about the correlation rule.  This description appears in the list of correlation rules and correlation rule details.   If you use a correlation rule template, the correlation rule template description is automatically reused as the description of your new correlation rule. |
Correlation Rule Triggered Value to Search Navigation | To view all events related to a correlation rule, you can now navigate to Search using a link next to the number times a rule has been triggered. The query automatically entered in Search is rules.rule: "<rule name>". The link appears in the list of correlation rules:  The link also appears when you view the correlation rule details:  |
Correlation Rule Email Notification Address Change | Email notifications sent as a correlation rule outcome are now sent from [email protected]. To ensure any rules for filtering emails or creating third-party tickets work properly, ensure they use the new email address. |
New Region Support for the UK | Support for Threat Detection Management now extends to the UK region. You can now access and use Threat Detection Management in the UK. |
Resolved Issues
Search Resolved Issues
ID | Description |
|---|---|
NGS-4653 | Previously, when using the Search API to retrieve events, the limit parameter accepted a value of 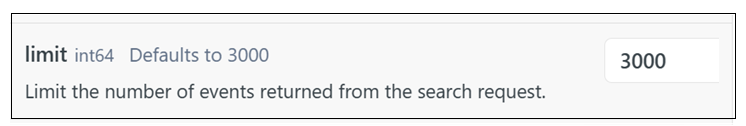 |
Site Collectors 2.6 Hot Fixes
Release Number | Hot Fix Description |
|---|---|
2.6.6 | Improved concurrency in Windows Event Log Collector to optimize overall performance. |
2.6.5 | Identified and resolved an issue to ensue the upgrade process correctly integrates the dynamic concurrency mechanism for Site Collectors. |
2.6.4 | Implemented a fix to ensure seamless functionality of multi-template configuration changes in the Windows Archive collector. |
2.6.3 | Resolved an issue that caused syslog agent collector rename failure. |
2.6.2 | Implemented enhancements for agent collectors. |
2.6.1 | Fixed an issue related to Windows management service. |
Site Collector 2.6: Security Vulnerabilities Remediations
The Site Collectors 2.6 (February 2025) release includes remediated security vulnerabilities. For more information about Exabeam’s commitment to remediating vulnerabilities for Site Collector, see the Vulnerability Remediation Policy.
There are no open known CVEs in any container image (Nifi). Toolkit has been deprecated and is no longer in use hence no security vulnerabilities update is available for that.
The following table lists the CVEs remediated for the Nifi container and their severity.
Critical | High | Medium | Low |
|---|---|---|---|
Total: 0 | Total: 0 | Total: 4 | Total: 1 |
– | – |
| CVE-2024-34459 |
Threat Center Resolved Issues
ID | Description |
|---|---|
TC-3054 | When you built a search using the Assigned to my queue quick search, the query used your role instead of your queue. |