- 2026 Release Notes
- 2025 Release Notes
- December 2025
- November 2025
- October 2025
- September 2025
- August 2025
- July 2025
- June 2025
- May 2025
- April 2025
- March 2025
- February 2025
- January 2025
- Known Issues
April 2025
The New-Scale Security Operations Platform includes the following addressed features and new features for April 2025.
Attack Surface Insights
Feature | Description |
|---|---|
Default Search Enhancement | To ensure you get a blank slate to define your own search query, there is no default search query for user and device entities when you open Attack Surface Insights. |
Cloud Collectors
Feature | Description |
|---|---|
Cloudflare Cloud Collector | The Cloudflare Cloud Collector is now available as part of Cloud Collectors to facilitate data collection from the account based and zone based data sources that include Audit logs, HTTP requests, and Gateway DNS events. |
Google Workspace Cloud Collector | The Google Workspace Cloud Collector is now available as part of Cloud Collectors to facilitate data collection from the data sources: Admin, Calendar, Drive, Gplus, Groups, Login, Meet, Mobile, Rules, Saml, Token. |
LastPass Cloud Collector | The LastPass Cloud Collector is now available as part of Cloud Collectors to facilitate data ingestion from LastPass report events. |
ServiceNow Cloud Collector | The ServiceNow Cloud Collector is now available as part of Cloud Collectors to facilitate data ingestion from the data sources Sys Audit Role, Sys Attachment, Change Request, Change Task, Sys Audit, Sys Event, Syslog Transaction, Report View, Event, Request, Task, Incident, Interaction, and Problem. |
Vectra Cloud Collector | The Vectra Cloud Collector is now available as part of Cloud Collectors to facilitate data ingestion from the data sources Audit Log Events, and Detections. |
Refresh token feature for the REST API Cloud Collector | You can now set the Authentication Refresh Body Parameters, and specify JSON path expression to extract the refresh token attribute and expiry time attribute for configuring OAuth 2.0 authentication for the REST API Cloud Collector. |
Regex Filtering for Cloud Collectors | You can now add filter conditions for the CrowdStrike Falcon (via FDR) Cloud Collector, AWS S3 Cloud Collector, AWS CloudTrail (via S3) Cloud Collector, SentinelOne CloudFunnel Cloud Collector, and Cisco Umbrella Cloud Collector in addition to the Azure Event Hub Cloud Collector, using regex syntax to include and exempt logs to be sent to the New-Scale Security Operations Platform. The cloud collector processes logs based on the conditions that you specify using the regex pattern. |
Early Access Collectors | |
AWS CloudWatch Alarms Collector | The AWS CloudWatch Alarms Cloud Collector now available as part of Cloud Collectors Early Access program to facilitate ingestion of AWS CloudWatch alarms related events. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Cisco Secure Endpoint Cloud Collector | The Cisco Secure Endpoint Cloud Collector now available as part of Cloud Collectors Early Access program to facilitate ingestion of security events from Cisco Secure Endpoint V1 APIs. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Trellix Endpoint Security Cloud Collector | The Trellix Endpoint Security Cloud Collector now available as part of Cloud Collectors Early Access program to facilitate ingestion of security alerts from Trellix APIs. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Context Management
Feature | Description |
|---|---|
Expanded IOC Field Enrichment | You can now search for IOC data from both internal and external threat intelligence sources. This functionality is made possible because the Context Management service now provides threat intelligence data from both prebuilt, curated sources and from external log sources that support the STIX/TAXII framework. NoteSTIX/TAXII context tables are available as part of a Cloud Collector Early Access program. During the early access period, you can access this functionality for STIX/TAXII context tables only if you participate in the program. To participate, see Sign Up for the Early Access Program, in the Cloud Collectors Administration Guide. To facilitate this expanded functionality, a new For more information, see Context in Search and Correlation Rules in the Context Management Guide. |
Dashboards
Feature | Description |
|---|---|
Support for STIX/TAXII based Context Tables | You can now filter dashboard visualizations for threat intelligence data from both Exabeam-provided and STIX/TAXII-based sources. This functionality is made possible because the Context Management service now provides threat intelligence data from both prebuilt, curated sources and from external log sources that support the STIX/TAXII framework. NoteSTIX/TAXII context tables are available as part of a Cloud Collector Early Access program. During the early access period, you can access this functionality for STIX/TAXII context tables only if you participate in the program. To participate, see Sign Up for the Early Access Program, in the Cloud Collectors Administration Guide For more information, see Include Context Filtering in Visualizations in the Dashboards Guide. |
Updates to AI/LLM Pre-built Dashboards | The following updates have been made to AI/LLM pre-built dashboards:
For more information about the AI/LLM pre-built dashboards, see AI/LLM Dashboards in the Dashboards Guide. |
Improve Filtering a Visualization on a Context Table | Filter behavior has been improved when selecting a context table as a query filter for a visualization. You can now select a context table that contains no records and add it to the visualization query filter. However, the visualization will not display any results until at least one record is added to the context table. A new message has been added to alert you when the context table you select contains no records. 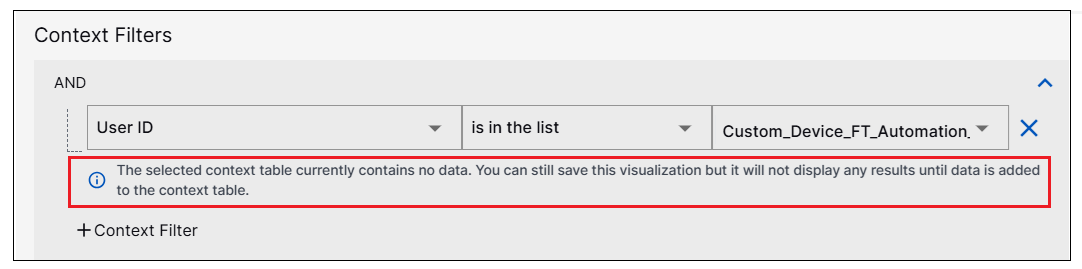 For more information, see Include Context Filtering in Visualizations in the Dashboards Guide. |
Log Sources
Feature | Description |
|---|---|
Log Source Monitoring | Using the Log Sources service you can now detect and monitor active and inactive log sources. In addition to granular monitoring of log sources, the Log Source service offers log source policy configuration and discovery, log source status visibility, and export of log sources. This feature is available as a part of the early access program. To participate, see Sign Up for the Early Access Program. |
New-Scale Platform
Feature | Description |
|---|---|
New Access Control API Endpoints | You can now programmatically retrieve lists of users, roles, and API keys that are configured in your environment. Three new Access Control endpoints are available to view this information without the need to log into the New-Scale Security Operations Platform and navigate the Settings options. For more information, see Access Control APIs in the New-Scale Security Operations Platform Administration Guide or visit the the Exabeam API Reference Guide and use the left navigation panel to find the Access Control endpoints. |
Outcomes Navigator
Feature | Description | ||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Numeric Coverage Scores | To have a more representative coverage score, better understand how the coverage score is calculated, and better track trends over time, all coverage scores are now numeric values between 0 and 100. Overall coverage scores are the average individual coverage scores across all Exabeam use cases or MITRE ATT&CK® techniques.[a] Coverage scores for individual use cases or techniques are the weighted average of coverage scores across Exabeam applications or features, like analytics rules, correlation rules, and Dashboards. | ||||||||||||||||||||||||||||||||||||||||||||||||
[a] MITRE ATT&CK and ATT&CK are trademarks of The MITRE Corporation ("MITRE"). Exabeam is not affiliated with or sponsored or endorsed by MITRE. Nothing herein is a representation of the views or opinions of MITRE or its personnel. | |||||||||||||||||||||||||||||||||||||||||||||||||
Search
Feature | Description |
|---|---|
Context Searching Using Non-key Columns | Until now, when searching for values in a context table, you could search for values only in the key column of the table. Now, the use of context tables in search includes the capability of searching in any column of a context table, including non-key columns. This expanded functionality is available in both the Basic and Advanced search modes. You can include up to two tables in a query, and a single column for each table. To facilitate the selection of non-key columns in Basic search, changes have been made in the UI for adding a context table to the query. When you choose a context table, a preview of the table is displayed. The key column is selected by default, but you can select any other column in the table. 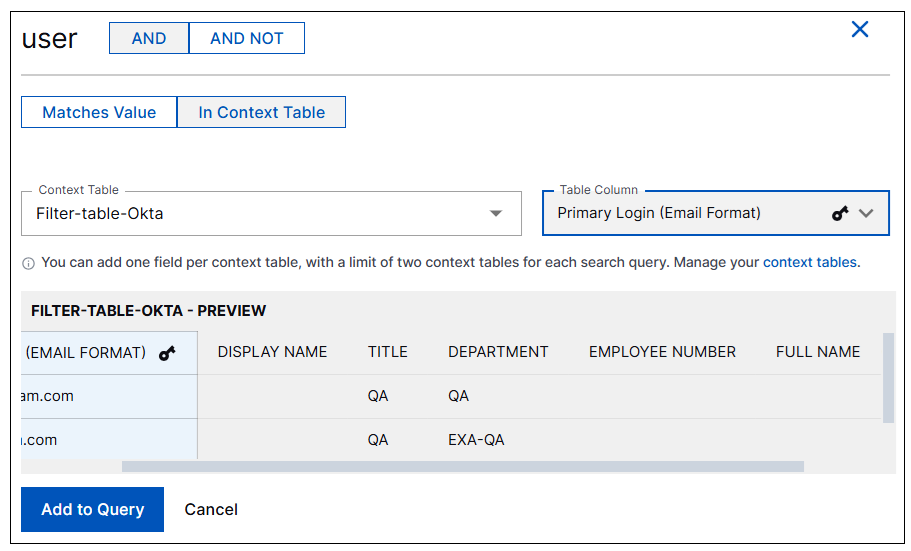 In Advanced search, additional syntax is provided to indicate the selection of both a context table and a specific column. For backwards compatibility, you can still add a context table without specifying a column. If no column is indicated, the query searches for values in the key column by default. The new syntax takes the following form: For more information, about adding context tables to Basic or Advanced search queries, see Context Tables in Search in the Search Guide. |
Advanced Search Suggestion Improvements | In the Advanced search mode, automated suggestions have been improved to display a greater variety of possible syntax options and to make those suggestions with greater context-awareness. The automated suggestions can now include key words, logical operators, fields, field values, and functions. Suggestions are only displayed if they are appropriate for the clause or syntax you are entering. For visual clarity, each different type of suggestion is accompanied by an icon that indicates what type of syntax is represents. For more information about Advanced search suggestions, see Running an Advanced Search in the Search Guide. |
Expanded IOC Field Enrichment | You can now search for IOC data from both Exabeam-provided and STIX/TAXII-based threat intelligence sources. This functionality is made possible because the Context Management service now provides threat intelligence data from both prebuilt, curated sources and from external log sources that support the STIX/TAXII framework. NoteSTIX/TAXII context tables are available as part of a Cloud Collector Early Access program. During the early access period, you can access this functionality for STIX/TAXII context tables only if you participate in the program. To participate, see Sign Up for the Early Access Program, in the Cloud Collectors Administration Guide. To facilitate this expanded functionality, a new For more information, see Threat Intelligence Enrichment in the Search Guide. |
Service Health and Consumption
Feature | Description |
|---|---|
Public API | Exabeam Public API enables you to programmatically retrieve license information for Long Term Search, Long Term Storage, and Correlation Rules. With the new public API you can now:
For more information, see the Exabeam API Reference Guide and use the left navigation panel to access the Service Health Consumption section. Additionally, navigate to the Changelog section for more details. |
Site Collectors 2.8
Feature | Description |
|---|---|
Region-specific Deployments | For Site Collector deployment, the regional endpoints will be utilized for communication with GCS instead of the generic GCS endpoints. Regional endpoints ensure that all requests and data in transit are processed and uploaded into the destination GCS only within the specified geographic region, maintaining data residency compliance. |
Automatic Scaling of Concurrency Settings for Site Collectors | Based on system load and hardware specifications such as CPU count, Site Collector is enhanced to dynamically scale its concurrency settings. This helps prevent event log accumulation in the queue and minimizes processing delays, especially when the repository disk is at full capacity. |
Threat Center
Feature | Description |
|---|---|
Exabeam Nova Case Name Enhancement | To ensure AI-generated case names help you quickly decide which cases to work on, the prompt used to generate case names has been refined to produce more concise case names. |
Increased Case and Alert List Default View | By default, you now see more cases or alerts in the case and alert lists. By default, 50 cases or alerts are displayed per page. You can also adjust the list to display 10, 25, or 100 cases or alerts per page. |
The following issues have been addressed from Threat Center in this release:
ID | Description |
|---|---|
ENG-68306 | Email notifications sent from Threat Center didn't display the case ID. Now, the case ID is displayed under the Case Number field. |
Resolved Issues
Search Resolved Issues
ID | Description |
|---|---|
ENG-67439 | An issue has been resolved so that when running an aggregated search using Advanced Query Language operators, the applicable license entitlements are enforced. You will not be able to run aggregated searches beyond your licensed time period. |
ENG-65001 | When using CIDR notations are used in queries with |
Site Collectors 2.8 Hot Fixes
Release Number | Hot Fix Description |
|---|---|
2.8.1 | Fixed a CICD issue that was preventing successful deployment of updates for Site Collectors. |
Site Collector 2.8: Security Vulnerabilities Remediations
The Site Collectors 2.8 (April 2025) release includes remediated security vulnerabilities. For more information about Exabeam’s commitment to remediating vulnerabilities for Site Collector, see the Vulnerability Remediation Policy.
There are no open known CVEs in any container image (Nifi). Toolkit has been deprecated and is no longer in use hence no security vulnerabilities update is available for that.
The following table lists the CVEs remediated for the Nifi container and their severity.
Critical | High | Medium | Low |
|---|---|---|---|
Total: 0 | Total: 0 | Total: 10 | Total: 1 |
– | – |
| CVE-2025-1153 |
