- 2026 Release Notes
- 2025 Release Notes
- December 2025
- November 2025
- October 2025
- September 2025
- August 2025
- July 2025
- June 2025
- May 2025
- April 2025
- March 2025
- February 2025
- January 2025
- Known Issues
August 2025
The New-Scale Security Operations Platform includes the following addressed features and new features for August 2025.
Attack Surface Insights
Feature | Description |
|---|---|
Pre-Built Attack Surface Insights Rules Criticality Enhancement | To prevent inflated risk scores for Threat Center cases and alerts, all pre-built Attack Surface Insights rules now automatically apply the Low criticality to entities. Review all pre-built rules and ensure they accurately reflect your environment. If not, disable the pre-built rule. You can then duplicate the pre-built rule and change the criticality it applies to entities or create a new rule that better reflects your needs. |
User Risk Trend Enhancement | You can now get more information about alerts and cases associated with a user entity with the User Risk Trend chart. In the minimized User Risk Trend chart, you can now view the number of open cases and alerts associated with a user entity during the selected time frame. To view details about the cases and alerts, click <#> cases or <#> alerts. 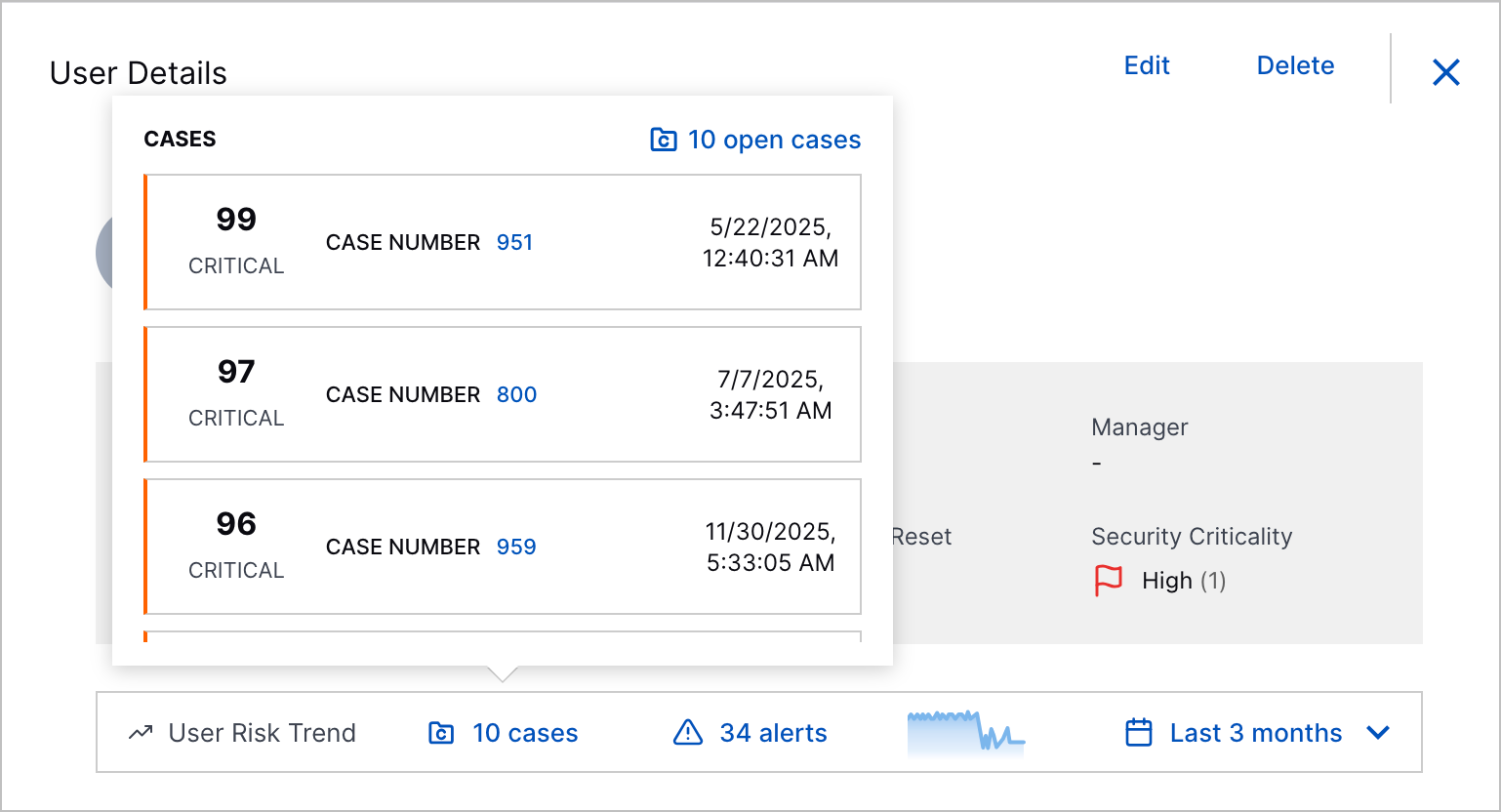 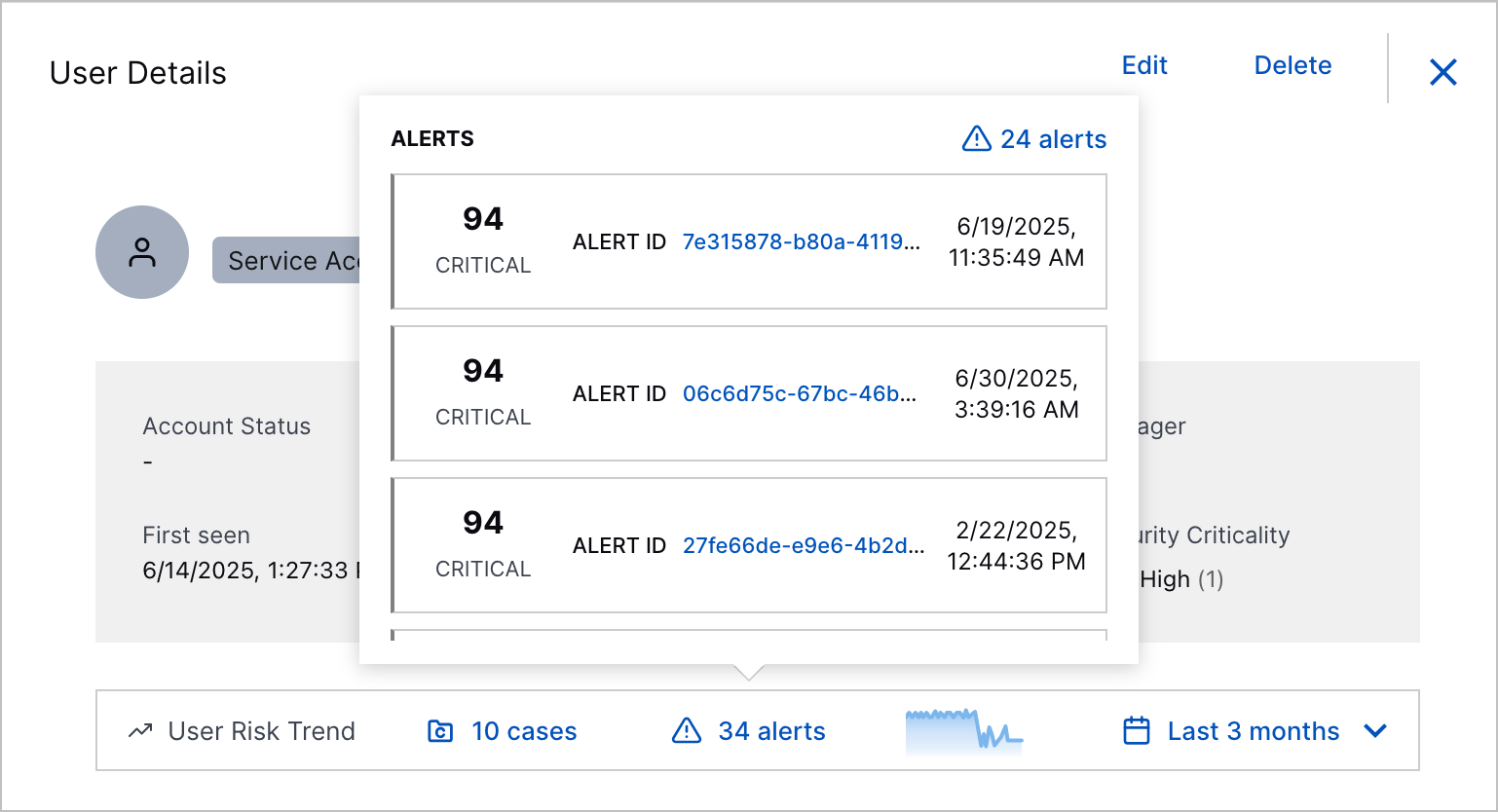 In the expanded User Risk Trend chart, you now view more detail about the case or alert with the highest risk score on a specific day when you hover over a point in the chart. 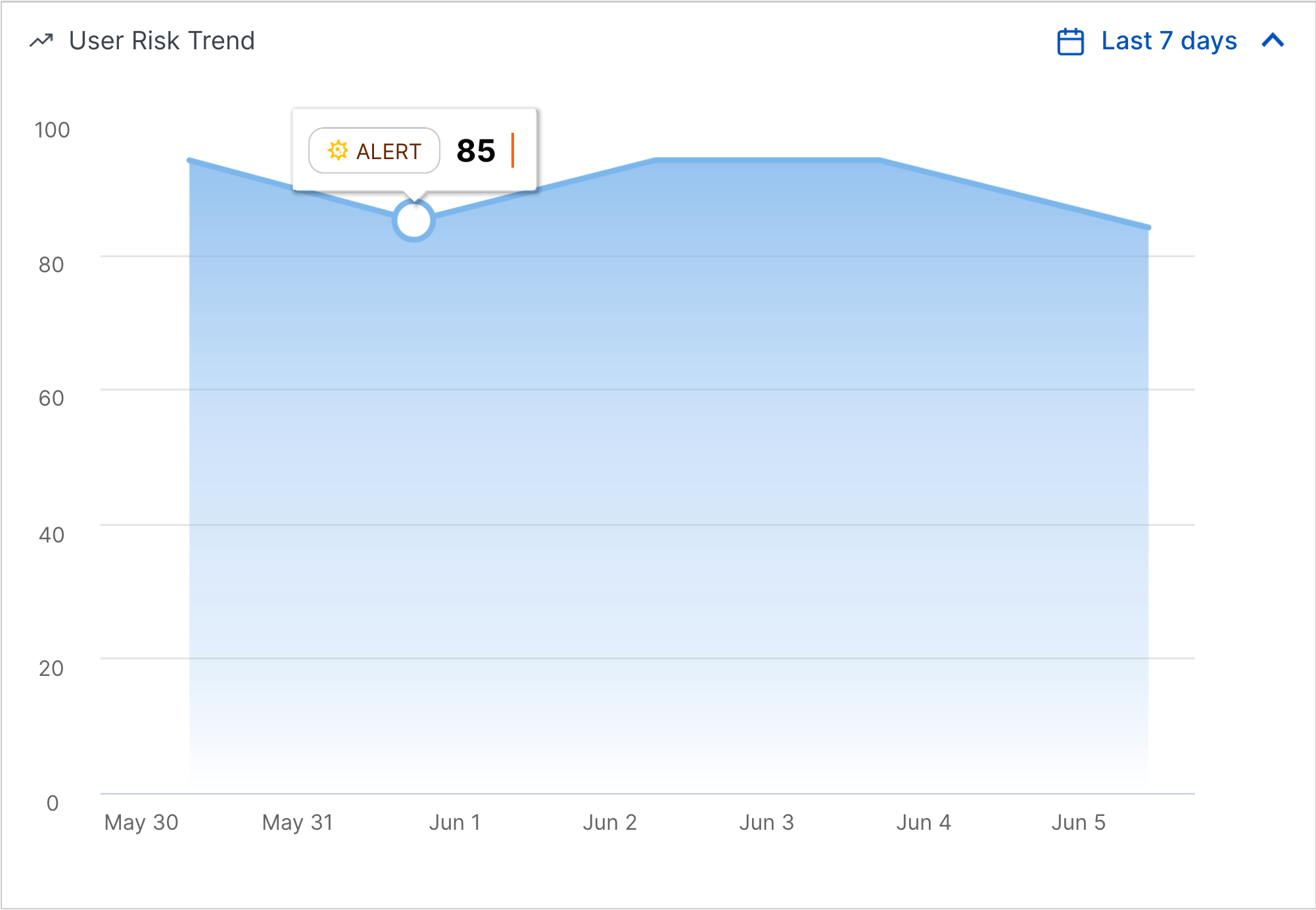 |
Automation Management
These features were released on August 22, 2025.
Feature | Description | |
|---|---|---|
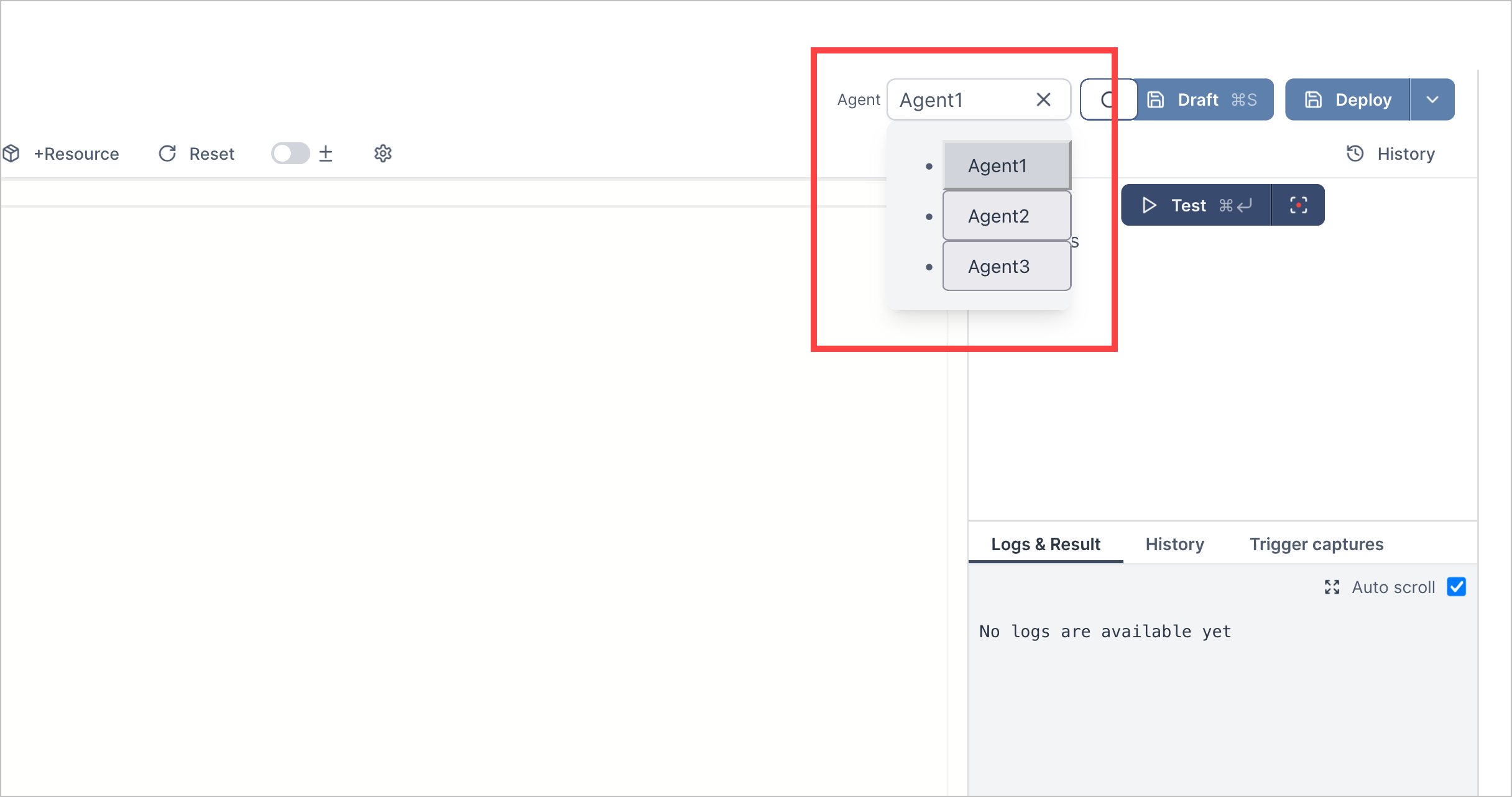
Automation Agents | You can now securely connect Automation Management to segmented networks using automation agents. An automation agent is a process that securely connects Automation Management to on-premises or network-segmented systems so you can run advanced playbooks and actions remotely on those systems. To connect Automation Management to a segmented network, you create an automation agent, then run the automation agent using Docker. When you run an automation agent, it's assigned a JSON Web Token (JWT) for authenticating HTTP requests to your network.The JWT is valid for 365 days, after which it expires. When the JWT is deleted, revoked, or expired, you can delete the automation agent. View all automation agents in the Automation Agents tab. 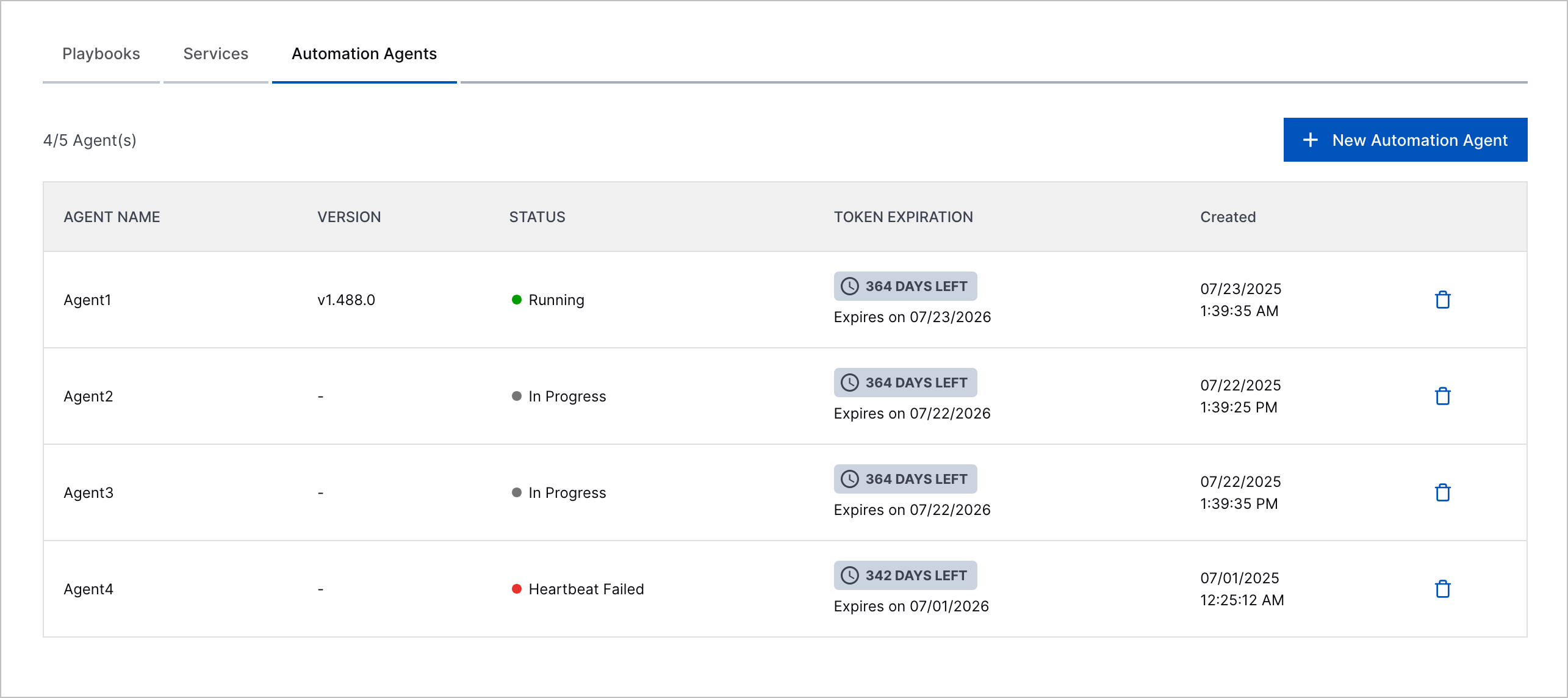 After you create an automation agent, you assign a given action the specific automation agent it uses to connect to your network.
| |
Pre-Defined Case Closed Reasons in Rule-Based Playbooks | To better track and report Threat Center case closures, you can now select a pre-defined reason for why cases were closed if you use rule-based playbooks to change the case stage to Closed. You can select a pre-defined case closed reason when the playbook action is Escalate to a case and and stage to is Closed: 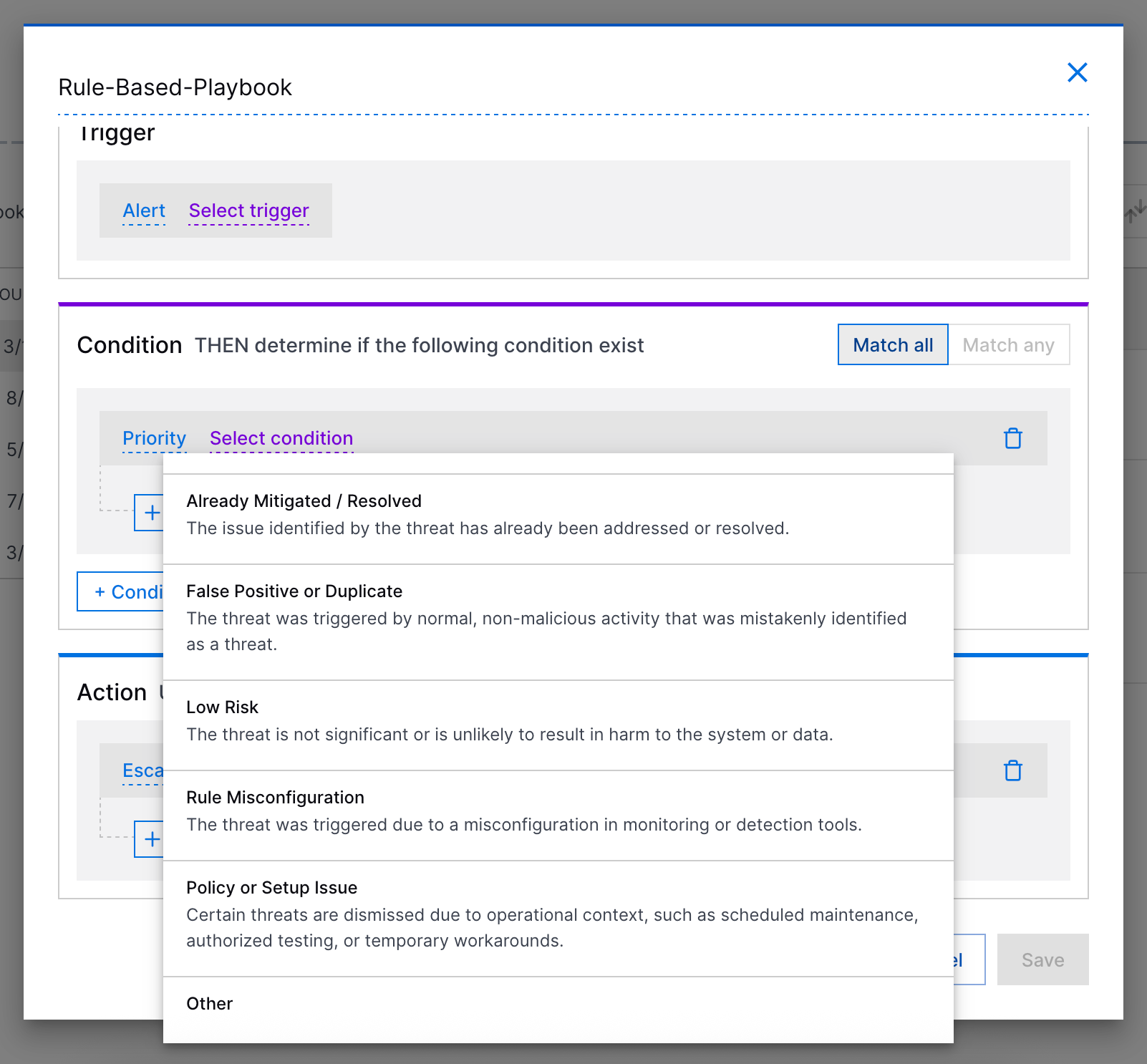 |
Cloud Collectors
Feature | Description |
|---|---|
AWS CloudWatch Alarms Cloud Collector | The AWS CloudWatch Alarms Cloud Collector now available as part of Cloud Collectors to facilitate ingestion of AWS CloudWatch alarms related events. |
AWS GuardDuty Cloud Collector | The AWS GuardDuty Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of GuardDuty Findings from AWS S3 bucket. |
AWS Security Lake Cloud Collector | The AWS Security Lake Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of security events from AWS S3 Security Lake bucket. |
DataBahn Cloud Collector | The DataBahn Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of events from DataBahn sources. |
Dropbox Cloud Collector | The Dropbox Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of team activity logs from Dropbox. |
Qualys Cloud Collector | The Qualys Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of Activity Logs, and Vulnerabilities including VM host detection events from Qualys sources. |
Slack Cloud Collector | The Slack Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of events from the Audit Logs API endpoints. |
Tenable Cloud Collector | The Tenable Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of vulnerability events from Tenable APIs. |
Zoom Cloud Collector | The Zoom Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of events from the sign-in/sign-out activity and operational logs endpoints. |
Early Access Collectors | |
GitHub Cloud Collector | The GitHub Cloud Collector is now available as part of Cloud Collectors Early Access program, to facilitate ingestion of GitHub enterprise audit logs that include events such as repository access, authentication attempts, permission changes, and more from the GitHub Enterprise Audit API endpoint to monitor your enterprise GitHub server or cloud-based GitHub service. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
GCP Cloud Logging Cloud Collector | The GCP Cloud Logging Cloud Collector is now available as part of Cloud Collectors Early Access program, to facilitate ingestion of logs from Google Cloud services. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
GCP Security Command Center Cloud Collector | The GCP Security Command Center Cloud Collector is now available as part of Cloud Collectors Early Access program, to facilitate ingestion of logs from GCP Security Command Center. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Progress ShareFile Cloud Collector | The Progress ShareFile Cloud Collector is now available as part of Cloud Collectors Early Access program, to facilitate ingestion of logs from the ShareFile endpoints: AccessChange, SharesSend, Activity, and SharesRequest. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Context Management
Feature | Description |
|---|---|
Pre-Built Vulnerability Scanners Context Table | Context Management now provides new pre-built correlation rules context tables. The first of these to be made available is the Vulnerability Scanners context table. The correlation rules context tables support the detection activities of correlation rules and are documented along with pre-built New-Scale Analytics and Attack Surface Insights context tables. For more information, see Pre-Built Detection Context Tables. |
Log Stream
Feature | Description |
|---|---|
Standardize Usage of bytes_in and bytes_out Fields | The definition of
These fields have become inconsistent in some cases because of an attempt to match vendor definitions, which may use reverse logic. Historically, enrichment rules have been created to handle exceptions, adding further confusion to the definitions. After a thorough content review, it has been decided to standardize the use of It is recommended that you check any enrichment rules or downstream correlation rules that leverage the
|
Search
Feature | Description | ||||
|---|---|---|---|---|---|
Improvements to Search Results Views and Detail Panels | Search includes the following improvements to certain aspects of the way search results are displayed:
For more information about any of these views or Details panel tabs, see the Search Results section of the Search Guide. | ||||
Support for Sort Order in Saved and Exported Searches | The selected sort order information is now persisted in a new Sorting column for both recent and saved searches lists. The column shows which sort order options was selected when the search query ran. For more information, see Saved Searches in the Search Guide. | ||||
Improved Titles for Detection Events | The Search Timeline view is using new logic to display more meaningful titles for detection events. To make the detection titles more useful for understanding why a detection was triggered, the titles will now be derived from critical triggering logic. This change ensures that titles are not based on context rule information, which is less useful for understanding the cause of a detection. Rather they will be based on triggering rule information so the reason for the detection is more obvious. |
Site Collectors 2.12
Feature | Description |
|---|---|
Windows Event Log Collector Auto-Restart (version 2.11.0 +). | The Auto-Restart feature for the Windows Event Log Collector automatically restarts exabeam-welc-collector-service and exabeam-welc-management if they fail unexpectedly, except when stopped by you via the user interface (UI) or API. The Auto-Restart feature restores collectors, improves reliability, reduces downtime, and minimizes manual recovery. |
Advance Configuration Settings for the Windows Template | For Windows Event Log Collector, while creating a Windows template, you can now use advanced configuration options. Using these options you can set the number of records to commit per batch, the number of events to read per batch, and the percentage for item substitution. You can enable or disable Security Identifiers (SID) lookup and caching SID. |
Windows Event Log Collector Upgrade | Site Collector now provides improved stability, and speed for Windows Event Log Collector (WELC) upgrades. To take advantage of these improvements, upgrade to the latest Site Collector version 2.12. Then, upgrade the Windows Event Log Collector instances for the new WELC management service to finalize configuration. If you use Windows Event Log Collectors version 2.9 or earlier, after upgrading to Site Collector version 2.12, follow the two-step upgrade process. First, Windows Event Log Collector is upgraded to version 2.11.2 irrespective of your current version. The next upgrade provides you with an option to move to the latest version. |
Threat Center
Feature | Description |
|---|---|
Pre-Defined Case Closed Reasons | This feature was released on August 22, 2025. To better track and report case closures, you can now select a pre-defined reason for why a case was closed. 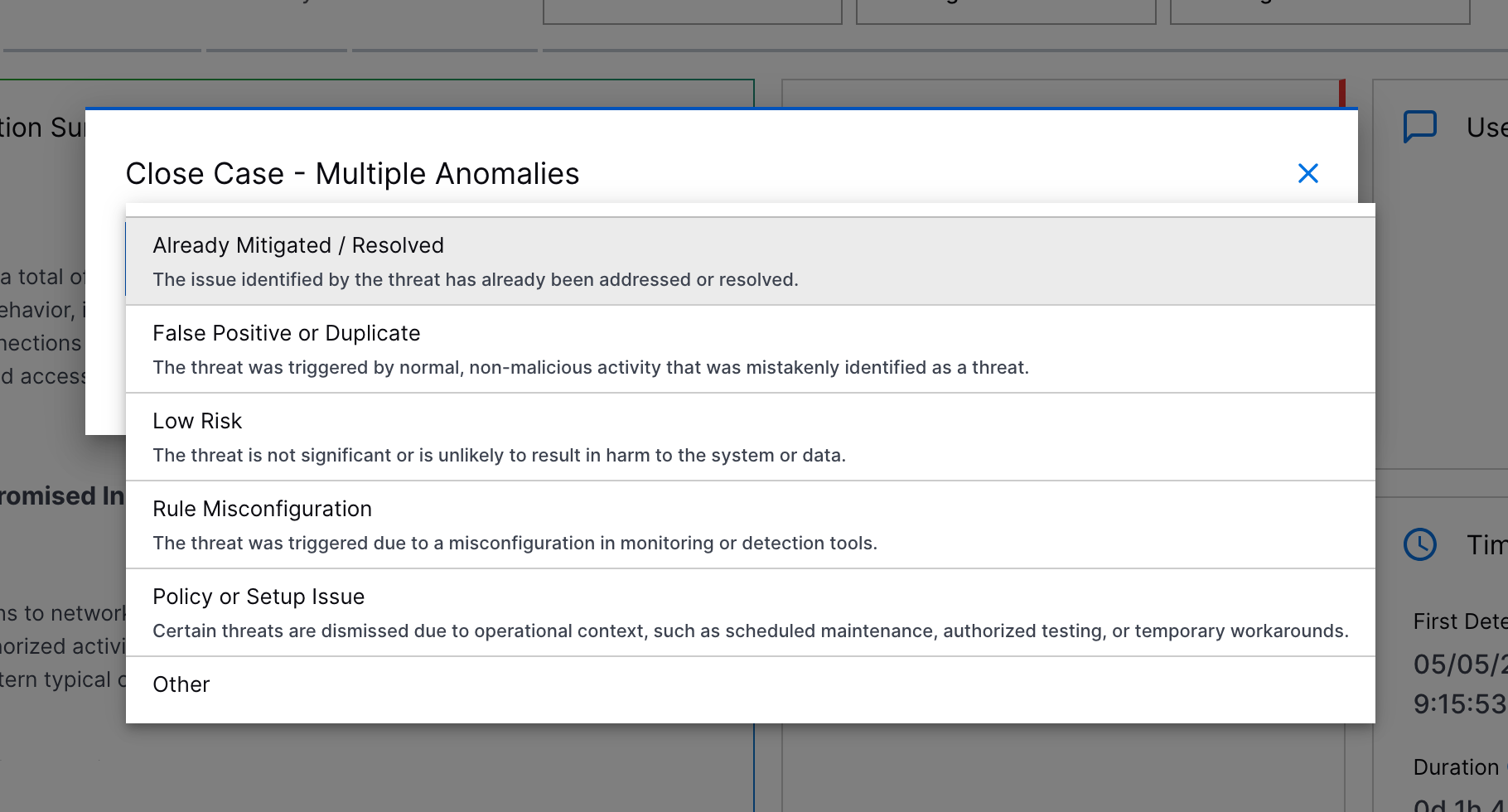 You can select between:
In the case Overview tab, review the reason why the case was closed, the queue and assignee assigned to the case when it was closed, and the date and time the case was closed under Case Closed. 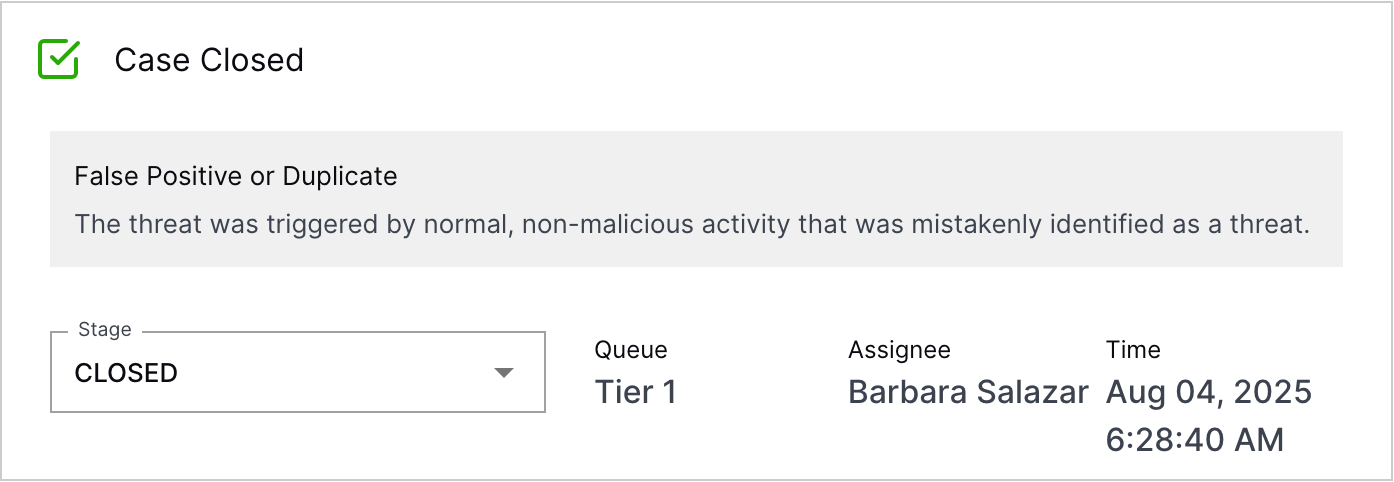 |
Threat Detection Management
Feature | Description |
|---|---|
Analytics Rules Reduced anomalyThreshold Minimum | To track anomalies over smaller intervals, the minimum valid value for the anomalyThreshold field is now 1 day for the following analytics rule types: |
Analytics Rules Limit Chart Enhancement | To better track how many custom analytics rules have been created in your environment, you can now view the number of custom analytics rules enabled compared to the maximum your entitlement allows in the Limit chart under Custom Rules. 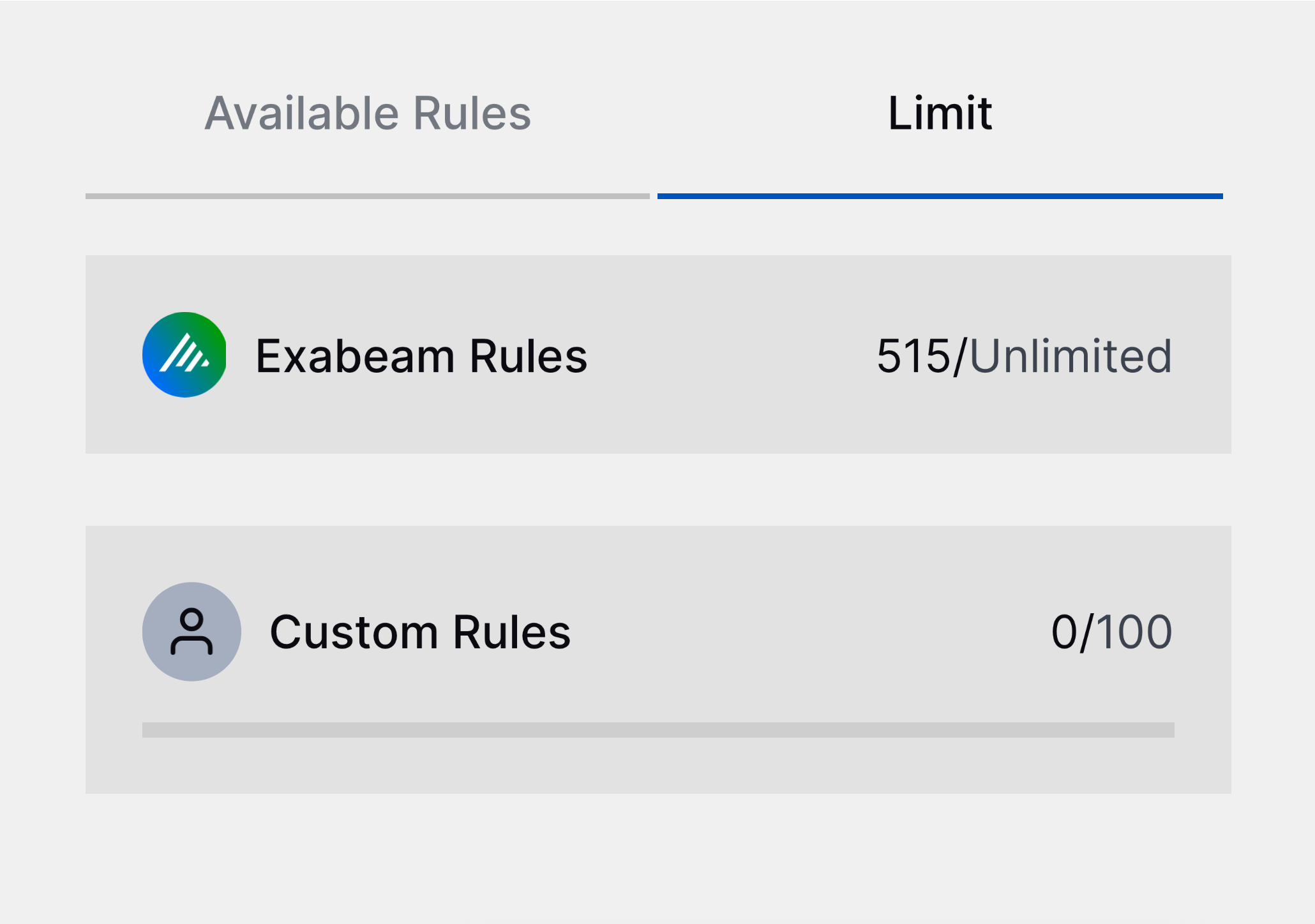 |
Resolved Issues
Search Resolved Issues
ID | Description |
|---|---|
ENG-74006 | An issue has been fixed so that when you save a search with a relative time range, the time range remains relative when the saved search is run on subsequent days. Previously, if you defined a query with a relative time range from 10 days ago to now, and you ran the saved search two days later, it returned results from 12 to 2 days ago. This issue is resolved so that a relative search remains relative whenever you run it. |
Site Collector 2.12: Security Vulnerabilities Remediations
The Site Collectors 2.12 (August 2025) release includes remediated security vulnerabilities. For more information about Exabeam’s commitment to remediating vulnerabilities for Site Collector, see the Vulnerability Remediation Policy.
There are no open known CVEs in any container image (Nifi). Toolkit has been deprecated and is no longer in use hence no security vulnerabilities update is available for that.
The following table lists the CVEs remediated for the Nifi container and their severity.
Critical | High | Medium | Low |
|---|---|---|---|
Total: 0 | Total: 0 | Total: 14 | Total: 2 |
– | – |
|
|