- 2026 Release Notes
- 2025 Release Notes
- December 2025
- November 2025
- October 2025
- September 2025
- August 2025
- July 2025
- June 2025
- May 2025
- April 2025
- March 2025
- February 2025
- January 2025
- Known Issues
March 2025
The New-Scale Security Operations Platform includes the following addressed features and new features for March 2025.
Cloud Collectors
Feature | Description |
|---|---|
Mimecast Cloud Collector | The Mimecast Cloud Collector is now available as part of Cloud Collectors to facilitate data collection from the data sources Archive Search Logs, TTP Attachment Protection Logs, TTP Impersonation Protect Logs, TTP URL Logs, SIEM Logs, Archive Message View Logs, and Audit Events. |
REST API Cloud Collector | The REST API Cloud Collector is now available as part of Cloud Collectors to facilitate data collection from REST API endpoints from a broad range of vendors and products. |
Sophos Cloud Collector | The Sophos Cloud Collector is now available as part of Cloud Collectors to facilitate data collection from the data sources alerts and events. |
Event Exploration on Search via Cloud Collectors | Now with the Open in Search option, you can open the Search application in a new tab to view a prepopulated Search query that displays details of logs related to the selected Cloud Collector instance. You can modify the Search query with parameters and timeframe to filter logs to see details specific to a Collector instance. |
Early Access Collectors | |
Cloudflare Cloud Collector | The Cloudflare Cloud Collector is now available as part of Cloud Collectors Early Access program to facilitate data collection from the account based and zone based data sources that include Audit logs, HTTP requests, and Gateway DNS events. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Google Workspace Cloud Collector | The Google Workspace Cloud Collector is now available as part of Cloud Collectors Early Access program to facilitate data collection from the data sources: Admin, Calendar, Drive, Gplus, Groups, Login, Meet, Mobile, Rules, Saml, Token. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
LastPass Cloud Collector | The LastPass Cloud Collector is now available as part of Cloud Collectors Early Access program to facilitate data ingestion from LastPass report events. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Vectra Cloud Collector | The Vectra Cloud Collector is now available as part of Cloud Collectors Early Access program to facilitate data ingestion from the data sources Audit Log Events, and Detections. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
STIX/TAXII Cloud Collector | The STIX/TAXII Cloud Collector is now available as part of Cloud Collectors Early Access program to facilitate threat intelligence data collection from external sources that support the STIX/TAXII framework. You can opt to collect data about either IP addresses or domains. You can also opt to automatically generate a corresponding context table in the Context Management application that will process the data and map it to a standardized set of attributes. The context table will have the same name as the cloud collector. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Recorded Future Context Cloud Collector | The Recorded Future Context Cloud Collector is now available as part of Cloud Collectors Early Access program to facilitate threat intelligence data collection from a Recorded Future Context source that supports the STIX/TAXII framework. You can opt to collect data about either IP addresses or domains. You can also opt to automatically generate a corresponding STIX/TAXII context table in the Context Management application that will process the data and map it to a standardized set of attributes. The context table will have the same name as the cloud collector. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Context Management
Feature | Description |
|---|---|
STIX/TAXII Context Tables | Context Management now supports onboarding STIX/TAXII context tables. These tables process data that is ingested by a corresponding STIX/TAXII cloud collector from an external threat intelligence source that use the STIX/TAXII framework. By default these context tables process a predetermined set of IP or domain attributes from the source collector and maps them to a set of standardized Exabeam target attributes. The STIX/TAXII context tables are available as part of the Early Access program. During the early access period, STIX/TAXII context tables can be created from either a STIX/TAXII or a Recorded Future Context cloud collector. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program, in the Cloud Collectors Administration Guide. For more information, see STIX/TAXII Context Tables in the Context Management Guide. |
Dashboards
Feature | Description |
|---|---|
New Scheduled Reports Tab | A new Scheduled Reports tab has been introduced in the Dashboards application. The new tab provides a centralized view of all the dashboard reports you have currently scheduled for delivery via email. From the new Scheduled Reports tab you can see which dashboards are scheduled for delivery, which recipients are scheduled to receive them, and on what schedule they will be delivered. You can also control the scheduled reports, with options to Run Now, Edit, Duplicate, or Delete. For more information about the new tab, see Navigate the Scheduled Reports Tab in the Dashboards Guide. |
Multi-Org Management
Feature | Description |
|---|---|
Add Descriptive Child Names in the Multi-Org Console | If you are managing multiple organizations in a Multi-Org console, you can now add descriptive banner names to your child organizations. You can enter user-friendly, identifiable names that help reflect the way you refer to your customers or environments. For more information, see the Get Started section of the Multi-Org Management Guide. |
New-Scale Platform
Feature | Description |
|---|---|
Introducing Exabeam Nova | Exabeam Nova, a transformative new agentic AI tool, is now available as part of the New-Scale Security Operations Platform. Exabeam Nova is built directly into the platform and requires no additional cost or extra complexity. Exabeam Nova is designed to augment SOC team efforts by automating routine investigative tasks. It can intelligently process vast amounts of event and alert data to provide targeted insights. And it is flexible enough to generate actionable investigation summaries for analysts of different experience levels. For more information, see Exabeam Nova in the New-Scale Security Operations Platform Administration Guide. |
Outcomes Navigator
Feature | Description | ||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Coverage Summaries | To get a high-level view of your overall security posture, you can now view a summary of your coverage across all MITRE ATT&CK® techniques and use cases.[a] To quickly understand your security posture at a glance, you can now view an overall Use Case Coverage Score and MITRE ATT&CK Coverage Score. The overall coverage scores represent the average coverage score across all use cases or ATT&CK techniques. It is calculated once per day. 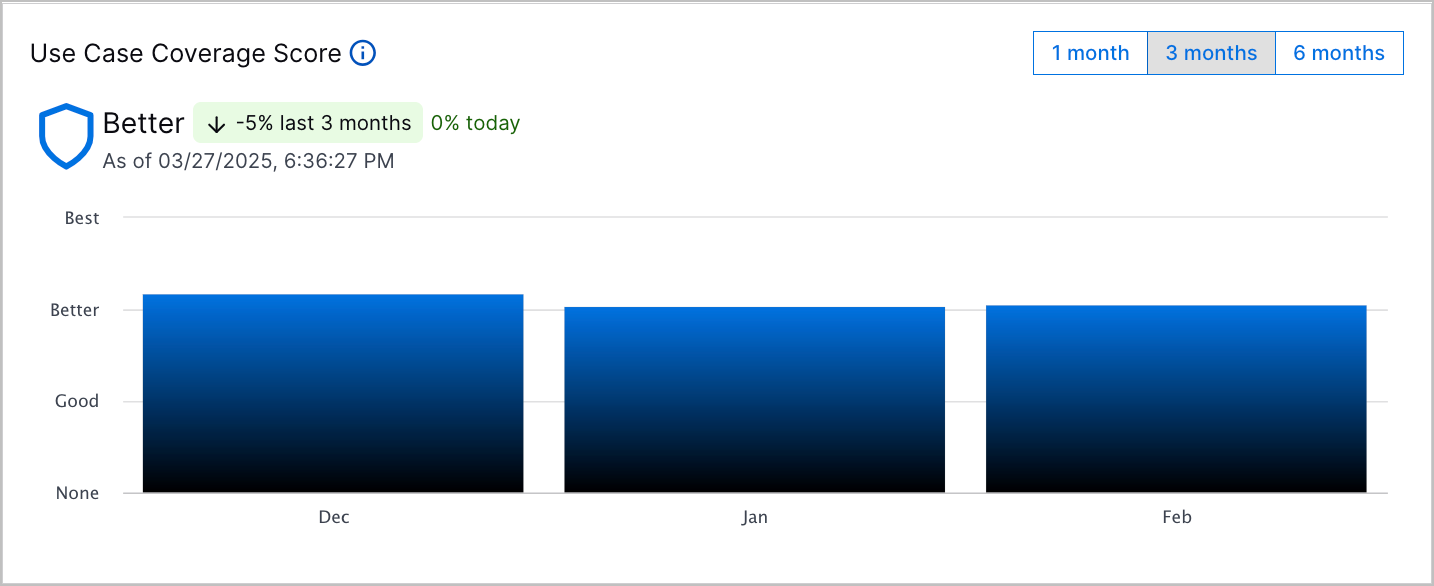 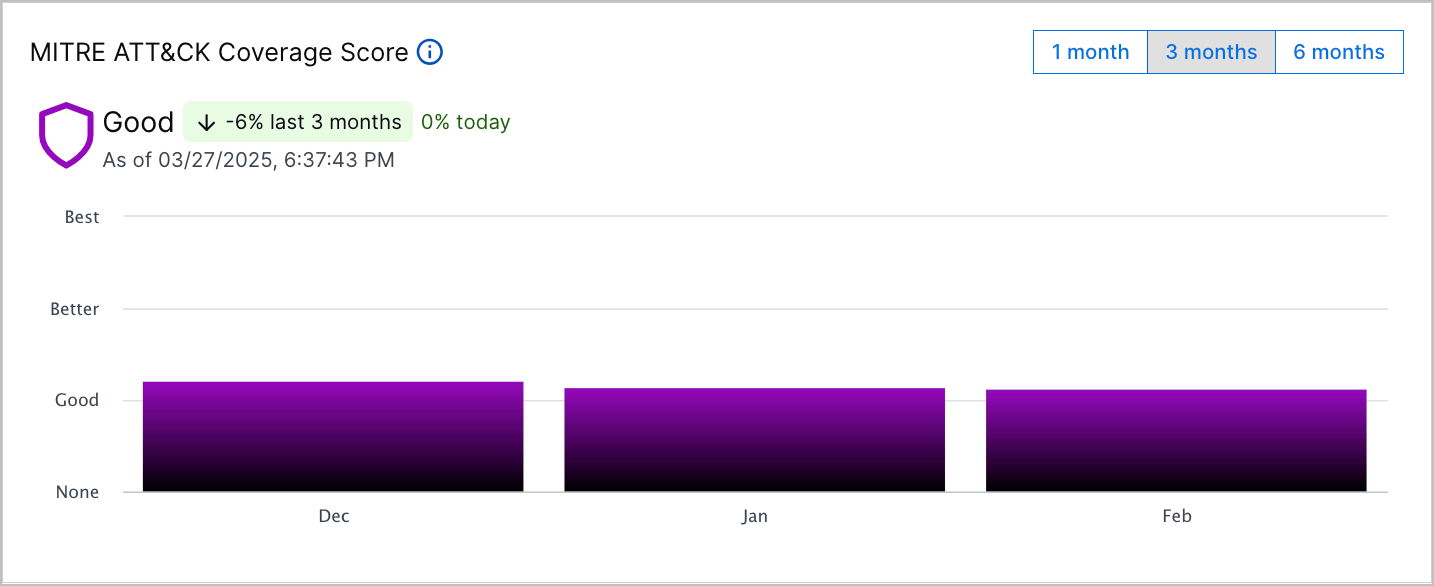 To identify trends in the overall coverage score, you can view a bar chart depicting the overall coverage score over one month, three months, or six months. You can also view the relative change of the overall coverage score over the given period and the relative change since the last time the score was calculated. Exabeam Nova Use Case Coverage Summary is an AI-generated summary of your overall use case coverage.
The summary identifies:
For ATT&CK techniques, this summary is under development and will be delivered in the coming months.  | ||||||||||||||||||||||||||||||||||||||||||||||||
[a] MITRE ATT&CK and ATT&CK are trademarks of The MITRE Corporation ("MITRE"). Exabeam is not affiliated with or sponsored or endorsed by MITRE. Nothing herein is a representation of the views or opinions of MITRE or its personnel. | |||||||||||||||||||||||||||||||||||||||||||||||||
Search
Feature | Description |
|---|---|
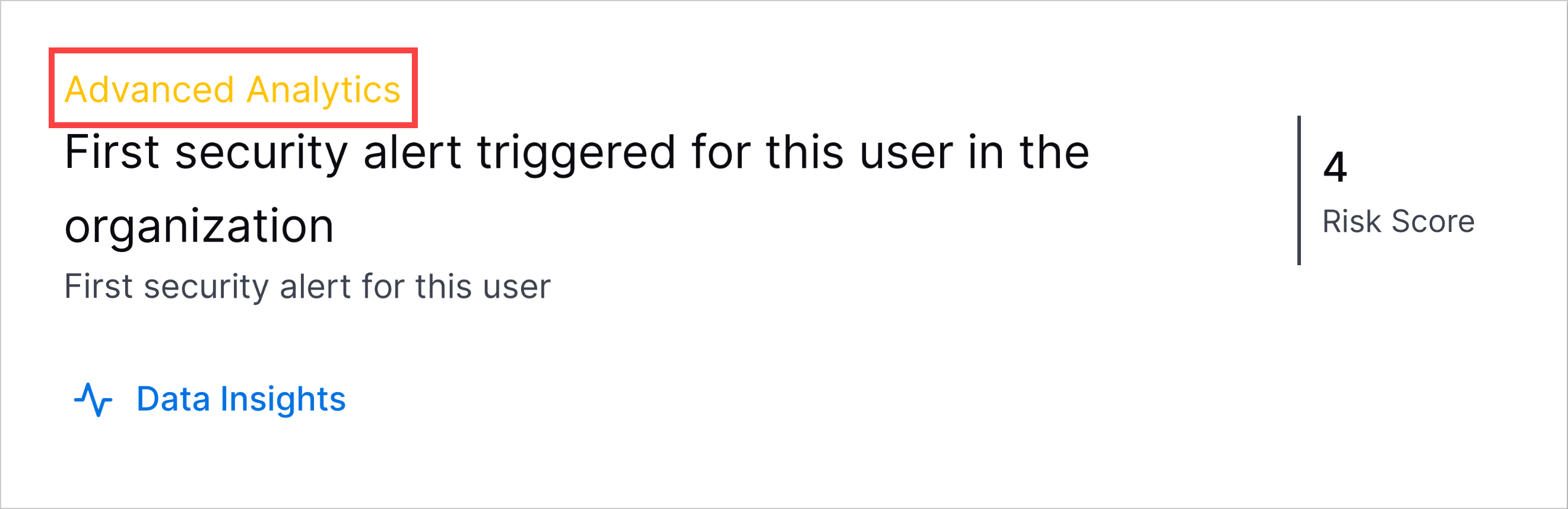
Data Insights | Data Insights functionality was previously only available to users with one of the New-Scale licenses. It is now also available to users with any Exabeam Security Operations licenses. The Insights tab is available in the Event Details panel for any search results that include parsed user or device information. The Insights tab provides a quick, easy way to drill into information related to events in your results. It lets you visualize what else is going on around a selected event, within specific time ranges. For example, if an event shows that a user triggered an alert, you can investigate which other assets the user has accessed in the past few days, which countries the user logged in from, or what files the user accessed. For more information, see Data Insights in the Search Guide. |
Entity Search Enhancements | The Entities tab in the Basic Search mode has been enhanced for more intuitive use and to display an increased level of detail. As part of the Exabeam True Identity functionality, the User Entity search consolidates all of the identifiers associated with a user account in your environment. In this way you can efficiently search across all the user identifiers with a single query. The process has been improved so that you can search by a user's full name or by any username or email address associated with the user account. Tooltips have been added so that you can view all of the associated names and addresses that will be included in the search results. 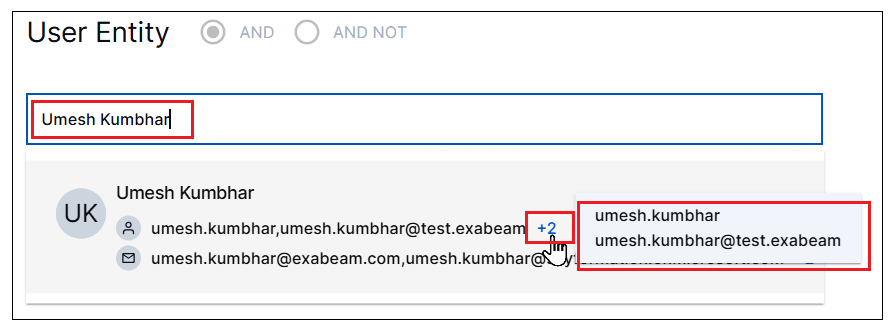 Options are still available to search by specific user account identifiers, including username or email address. For more information, about user entity searching, see Pre-Built Basic Search Lists in the Search Guide. This feature is currently available only if you have either the New-Scale Analytics license or the New-Scale Fusion license. For more information about these licenses, see New-Scale Security Operations Portfolio Licenses. For more information about managing and viewing entities in your environment, see the Attack Surface Insights guide. |
Site Collectors 2.7
Feature | Description |
|---|---|
Performance Optimization for Windows and Linux File Collector | Implemented performance enhancements for Windows and Linux File Collector to facilitate processing of extra large files exceeding 20GB. |
Site Collector Upgrade Options | After you upgrade to the Site Collector 2.7 version, the next releases will show options to upgrade the current Site Collector version to the latest and the most recent stable version. |
Windows Server 2025 and Windows Server 2025 Core Support for Agent Collectors | The Windows Event Log Collector, Windows File Collector and Windows Archive Collector now support the Windows Server 2025 and Windows Server 2025 Core operating system. |
Threat Center
Feature | Description | ||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Threat Center Exabeam Nova Enhancement | If you have a license that includes Advanced Analytics, Exabeam Nova Analyst Assistant and Exabeam Nova Threat Summary now have a better understanding of a case or alert, considering the 50 most recently grouped detections when generating a response.[a] If you have a New-Scale Security Operations portfolio license, you can now get more accurate and trustworthy responses with minimal hallucinations from Exabeam Nova Analyst Assistant and Copilot Threat Summary. Exabeam Nova now has a better understanding of a case or alert, considering associated entity information and all associated detections when generating a response. | ||||||||||||||||||||||||||||||||||||||||||||||||
Created Column | To ensure you're investigating the right case or alert, you can now view the date and time a case or alert was created and time elapsed since the case or alert was created under the Created column. 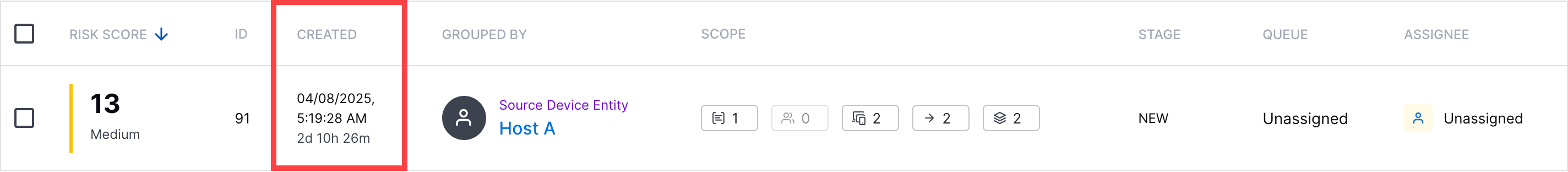 | ||||||||||||||||||||||||||||||||||||||||||||||||
Queue and Assignee Columns | To support sorting by queue and assignee, cases now have separate queue and assignee columns. 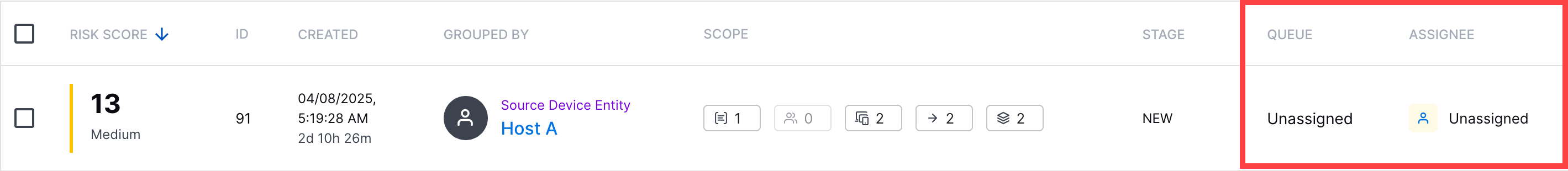 | ||||||||||||||||||||||||||||||||||||||||||||||||
Sorting Enhancements | To help you quickly find a case or alert, you can now sort cases and alerts by three additional columns: Grouped By, Stage, Queue, and Assignee. | ||||||||||||||||||||||||||||||||||||||||||||||||
Filters | To view only certain kinds of cases or alerts, you can now filter cases and alerts. For cases, you can filter by priority, grouped by value, stage, queue, and assignee.
For alerts, you can filter by priority and grouped by value.
| ||||||||||||||||||||||||||||||||||||||||||||||||
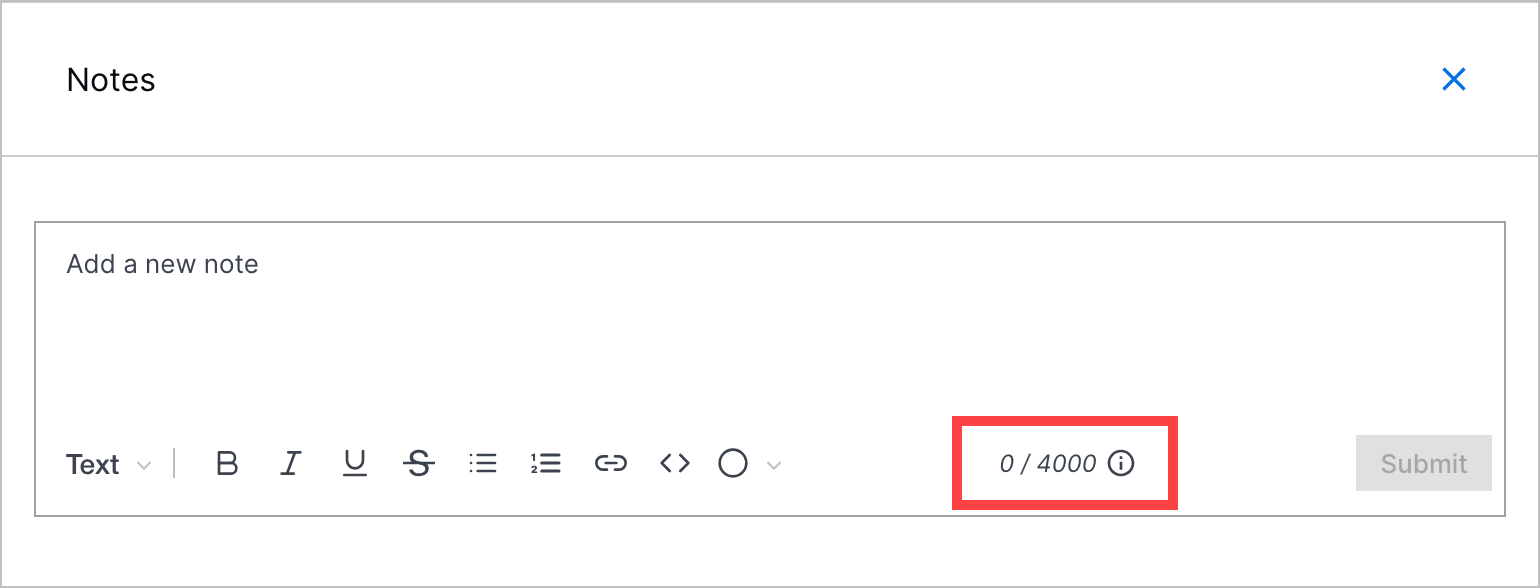
Increased Notes Character Limit | To ensure you can communicate everything you want with case notes, you can now add up to 4,000 characters in a single note.
| ||||||||||||||||||||||||||||||||||||||||||||||||
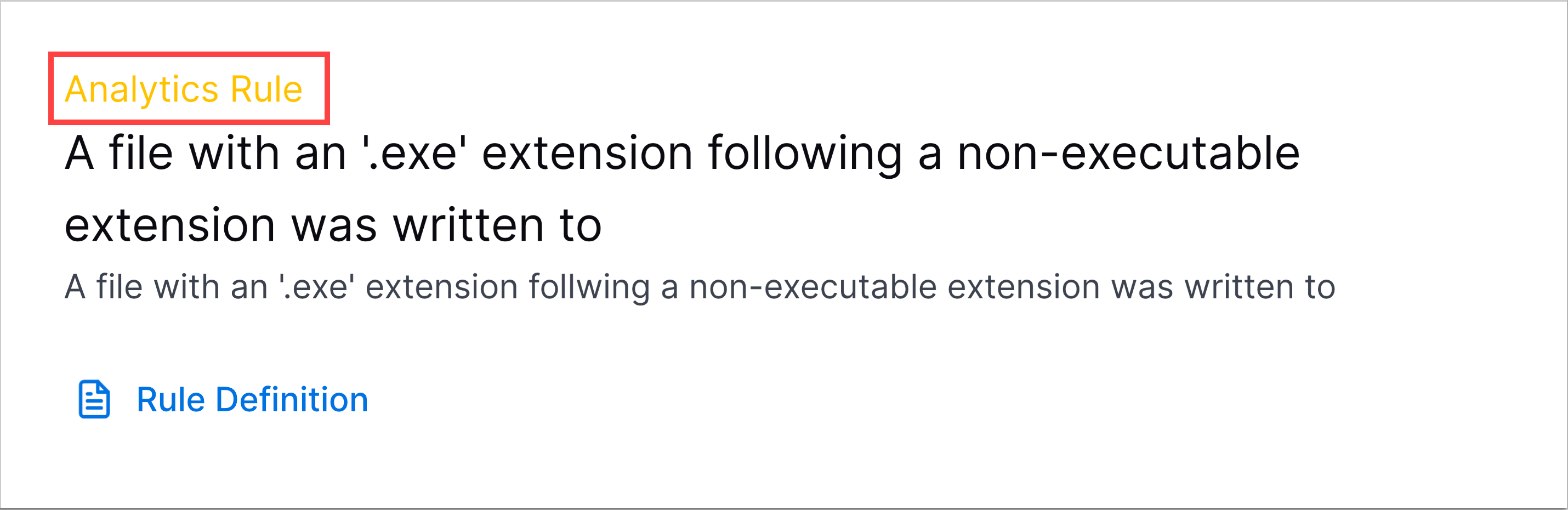
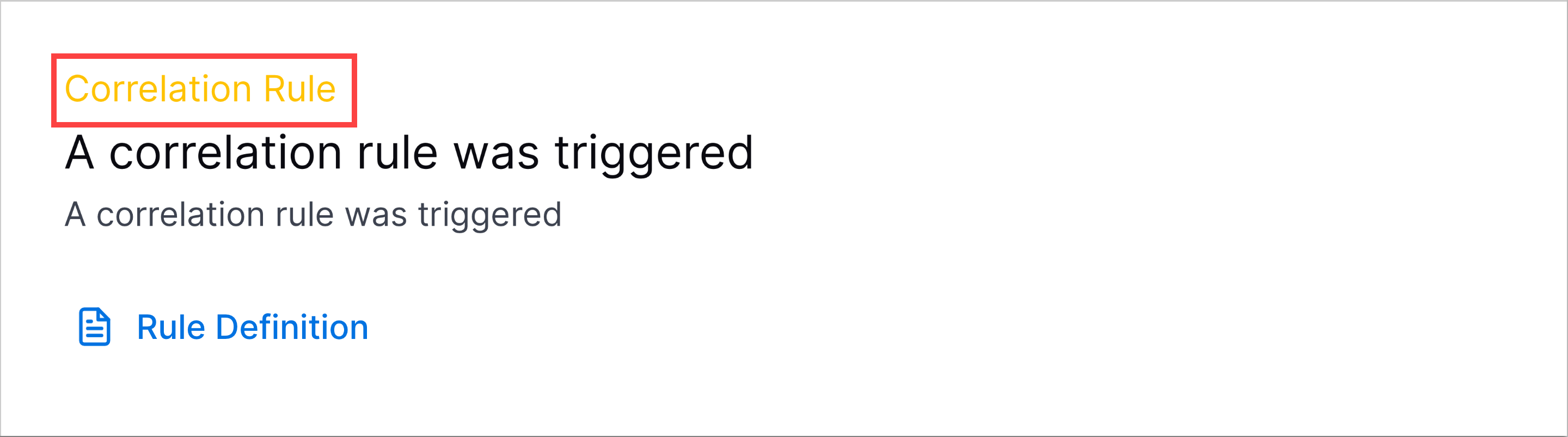
Threat Timeline Rule Name Enhancement | To better discern the type of rule associated with a detection, you can now see the full name of the rule type in the Threat Timeline.
| ||||||||||||||||||||||||||||||||||||||||||||||||
[a] This tool is designed to condense security event data into easy-to-understand language, focusing on important security details. It can also answer follow-up questions and discuss security tech topics, but its accuracy might vary outside these areas. Always double-check responses for crucial decisions. Your queries and data will only be retained temporarily and won't be used for AI training. Exabeam is actively improving this tool and welcomes feedback. | |||||||||||||||||||||||||||||||||||||||||||||||||
Threat Detection Management
Feature | Description |
|---|---|
Incompatible Analytics Rule Disablement | To ensure the analytics engine runs normally, the analytics engine monitors rule training and evaluation processes and prevents you from enabling analytics rules that are incompatible with your data or are highly likely to generate false positive results. Under the Compatability, column, these analytics rules are marked as Incompatible. |
Resolved Issues
Service Health and Consumption Resolved Issues
ID | Description |
|---|---|
NGT-1887 | The Health Alerts & Thresholds notification section under the App Config tab now continues to display Cribl cloud collector instances even after getting decommissioned either from Exabeam Cloud Collectors page or from Cribl console. The Cribl collector instances listed in the App Config section now have a prefix exa-cribl-logs- before the name of the collector configured from Cribl console. Fixed the associated issue in which the Cribl cloud collector instances were not listed in the Health Alerts & Thresholds notification section. |
Site Collectors 2.7 Hot Fixes
Release Number | Hot Fix Description |
|---|---|
2.7.3 | Fixed an issue for collectors to ensure accurate initialization of collectors in ngscd. |
2.7.2 | Resolved a monitoring issue triggered by the presence of the invalid nifi components. |
2.7.1 | Resolved an issue that impacted the successful setup of the eStreamer collector. |
Site Collectors 2.7 CVE Remediations
The Site Collectors 2.7 (March 2025) release includes remediated security vulnerabilities. For more information about Exabeam’s commitment to remediating vulnerabilities for Site Collector, see the Vulnerability Remediation Policy.
There are no open known CVEs in any container image (Nifi). Toolkit has been deprecated and is no longer in use hence no security vulnerabilities update is available for that.
The following table lists the CVEs remediated for the Nifi container and their severity.
Critical | High | Medium | Low |
|---|---|---|---|
Total: 0 | Total: 0 | Total: 12 | Total: 4 |
– | – |
|
|