- 2026 Release Notes
- 2025 Release Notes
- December 2025
- November 2025
- October 2025
- September 2025
- August 2025
- July 2025
- June 2025
- May 2025
- April 2025
- March 2025
- February 2025
- January 2025
- Known Issues
January 2025
The New-Scale Security Operations Platform includes the following addressed issues and new features for January 2025.
Attack Surface Insights
Feature | Description |
|---|---|
Introducing Attack Surface Insights | Welcome to Attack Surface Insights, the directory for organizational resources in your environment, also known as entities. Attack Surface Insights is supported with a New-Scale Analytics or New-Scale Fusion license. To get started with Attack Surface Insights, view the Attack Surface Insights documentation. |
Automation Management
Feature | Description |
|---|---|
Automation Management Services | To automate complex workflows across multiple third-party security services or Exabeam features, you can now integrate Automation Management with services. For a service, create or import an instance you created in Postman, Swagger, or Python, then create actions for the service. Custom services are available with an add-on to a New-Scale Security Operations portfolio license. |
Automation Management Actions | You can now interact with services you integrated with Automation Management using actions. You can use actions in advanced playbooks to call services and use the data returned to automate complex workflows. |
Advanced Playbooks | You can now automate complex workflows using advanced playbooks. With the new experience, you can: Pre-built playbooks have also been converted to advanced playbooks. Advanced playbooks are available with an add-on to a New-Scale Security Operations portfolio license. |
No Trigger Playbooks | You can now create playbooks without triggers. These playbooks can only be manually run on a specific case or alert. |
Automation Management in Threat Center | Automation Management is now more deeply integrated with Threat Center. You can now:
|
Triggered Rule-Based Playbooks for Manual Case or Alert Updates | When you manually edit an alert or case or create a case, rule-based playbooks with the Alert is modified, Case is modified, and Case is created triggers run automatically. |
Cloud Collectors
Feature | Description |
|---|---|
Box Cloud Collector | The Box Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of user events and enterprise events from Box. |
Cisco Meraki Cloud Collector | The Cisco Meraki Cloud Collector is now available as part of Cloud Collectors Early Access program to facilitate data collection from security events, alerts, configuration changes, and networks from Cisco Meraki APIs. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Recorded Future Cloud Collector | The Recorded Future Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of API Alerts. |
ServiceNow Cloud Collector | The ServiceNow Cloud Collector is now available as part of Cloud Collectors Early Access program to facilitate data ingestion from the data sources Sys Audit Role, Sys Attachment, Change Request, Change Task, Sys Audit, Sys Event, Syslog Transaction, Report View, Event, Request, Task, Incident, Interaction, and Problem. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Context Management
Feature | Description |
|---|---|
Support Context Tables for Device Data | Context Management now supports onboarding device data into the following types of context tables:
To facilitate onboarding device data to the Active Directory, CrowdStrike, and Microsoft Entra ID context tables, new tiles are available from the Context Library page in Context Management. Data in these device tables is available for use in the downstream Search application. It is not yet available for building dashboards or correlation rules. These device context tables are available with any New-Scale Security Operations or Exabeam Security Operations license. For more information, see Onboarding a Context Table and navigate to a specific context table section. |
Support Pre-Built New-Scale Analytics Context Tables | Context Management now provides new pre-built New-Scale Analytics context tables. These context tables are used to support activities by the New-Scale Analytics engine and in the Attack Surface Insights application. These New-Scale Analytics context tables are currently available only for the New-Scale Analytics license. For more information about the new context tables, see Pre-Built New-Scale Analytics Context Tables in the Context Management Guide. |
Correlation Rules
Feature | Description |
|---|---|
Threat Center Outcomes Exclusions for Test Mode | To ensure you investigate and triage only real threats in Threat Center, correlation rules in test mode no longer create Threat Center cases or alerts. Events created from a triggered correlation rules in test mode have the activity type |
Dashboards
Feature | Description | ||
|---|---|---|---|
Support for Pivoting to Search for Rule Triggered Events | To support pivoting into Search for rule-triggered events that are represented in dashboards and visualizations, the Show Results in Search option is now available for those events. Using this option allows you to click on a specific area or data point in a visualization and pivot from Dashboards to the Search application. There you can drill down further to investigate the rule-triggered event. For information, see View and Interact with a Dashboard or View and Interact with a Visualization in the Dashboards Guide. | ||
Updated Audit Log Support for Dashboards | Audit log coverage has been updated for dashboards in the New-Scale Security Operations Platform. For clarity, all activity types for dashboards have been renamed from
For information, see Dashboards in Audit Logs in the Dashboards Guide. |
Log Stream
Feature | Description |
|---|---|
Parser Dependency Visibility | A new Dependencies column has been added to the Log Stream Parsers Overview tab to provide feedback about the quality and completeness of parsers that are ingesting detection events. For easy reference, this information is available as part of the parser list so there's no need to enter individual parsers to discover missing fields or detection rules. Currently, this feature is available only if you have the New-Scale Analytics license. For more information, see Parser Dependencies in the Log Stream Guide. |
Manage Enrichment Rules | A new Enrichments tab has been added to Log Stream to provide access to view and manage enrichment rules. These enrichment rules are applied automatically as part of the process to enrich parsed event logs with contextual data. The new tab includes lifecycle information about the available enrichment rules, options to enable and disable specific rules, and the ability to view and edit the configuration details of each rule. You can also export rules and import new rules from other environments. Currently, this feature is available only if you have the New-Scale Analytics license. For more information, see Enrichments in the Log Stream Guide. |
Filter and Route Events | A new Event Filtering tab has been added to Log Stream so that you can filter which events should be routed to the New-Scale Analytics detection engine or to the Attack Surface Insights application. This filtering allow you to fine tune which events or types of data are leveraged for detection and for Attack Surface Insights. The new tab provides information at a glance about the volume and types of event data the filters are routing, either to the New-Scale Analytics detection engine or to Attack Surface Insights. The tab also provides access to define and edit the filters. Currently, this feature is available only if you have the New-Scale Analytics license. For more information, see Event Filtering in the Log Stream Guide. |
New-Scale Platform
Feature | Description |
|---|---|
Introducing the New-Scale Security Operations Platform | Introducing the New-Scale Security Operations Platform Exabeam is renaming its security operations platform with the introduction of a New -Scale Analytics detection engine that provides a sophisticated approach to threat prioritization, AI-driven automations, and seamless integrations. The New-Scale analytics engine is built as a core component of the New-Scale Platform to ensure that you can swiftly address the highest-risk threats while minimizing manual tuning and false positives. In combination with Exabeam Nova, which provides natural language interactions, you can efficiently navigate the threat landscape and boost SOC productivity. If you are using Advanced Analytics, none of your current access or functionality will be reduced. You can choose to migrate to New-Scale Analytics at your own discretion. The following new product features are available for New-Scale Analytics:
|
New-Scale Security Operations Portfolio Licenses | To support the New-Scale Security Operations Platform, the following new license offerings are available:
For more information about the licenses and for a table of features available by license type, see New-Scale Security Operations Portfolio Licenses in the Platform Administration Guide. |
Outcomes Navigator
Feature | Description |
|---|---|
UI Improvement | To reduce confusion and simplify the user interface, the Recommendations tab in Outcomes Navigator will only be displayed in environments that include Advanced Analytics. The data on the Recommendations tab is specific to the Advanced Analytics engine. This data is not relevant for customers with New-Scale licenses, which depend on the New-Scale Analytics Detection engine. |
Search
Feature | Description |
|---|---|
Support for Device Context Tables | You can now include device context tables in both Basic and Advanced search queries, allowing you to search for information about devices in your environment. Specifically, you can now search for results in the following types of device context tables:
For more information, see Context Tables in Search in the Search Guide. |
Relative Time Range Option | A new Relative time range option is now available when building your Search queries. It provides a more precise and flexible approach to searching within a relative time range. The Quick time range options are still available but with the Relative option, you are not limited to fixed choices. You can specific a relative start and end date, such as 1 to 3 months ago. The relative options are translated into specific dates, which are displayed in the time range selector box, as shown below. 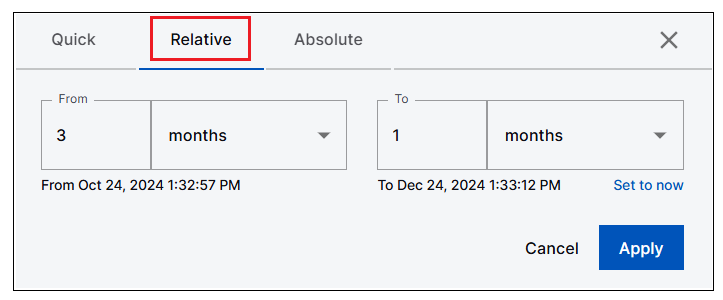 |
Guardrails for Pipe Operator Use | New guardrails have been introduced for the use of the pipe operator in the Advanced search mode. They provide warnings to help prevent overuse or misuse of pipe operators in ways that can be slow and inefficient. When you write a query with a pipe operator that could more effectively be written with an AND operator or a WHERE clause, a warning is displayed below the search bar. 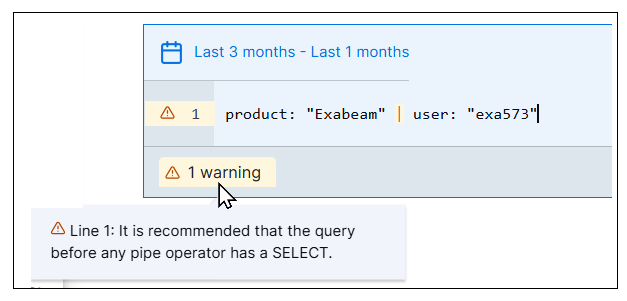 For more information, see the Pipe Operator section of Query Using Advanced Query Language Operators in the Search Guide. |
Timeline View of Search Results | Exabeam introduces a new Timeline view of search results that brings the investigational timeline experience into the Search application. Analysts and threat hunters can use the Timeline view as a starting point for investigating risky or anomalous events while still leveraging the granular filtering capabilities of the Search application. The Timeline view is designed specifically with this task in mind. It's visually organized so that detection events are easy to spot and investigate. You can drill into the detections or the associated events to find detailed information and data insights. For more information, see Timeline View of Search Results in the Search Guide. This feature is currently available only if you have one of the New-Scale licenses. For more information see New-Scale Security Operations Portfolio Licenses. |
Rule Details Panel | A new Rule Details panel is available for viewing detailed rule information when search results return detection events. This new panel facilitates interactions with events that may represent a security threat or anomalous behavior. The panel includes a raw log message, a full list of parsed fields, and an expandable list of any rules associated with the detection event. For more information see Rule Details in the Search Guide. This feature is currently available only if you have one of the New-Scale licenses. For more information see New-Scale Security Operations Portfolio Licenses. |
Data Insights | A new Insights tab is available in the Event Details panel for any search results that include parsed user or device information. The Insights tab provides a quick, easy way to drill into information related to events in your results. It lets you visualize what else is going on around a selected event, within specific time ranges. For example, if an event shows that a user triggered an alert, you can investigate which other assets the user has accessed in the past few days, which countries the user logged in from, or what files the user accessed. For more information, see Data Insights in the Search Guide. This feature is currently available only if you have one of the New-Scale licenses. For more information see New-Scale Security Operations Portfolio Licenses. |
Entity Searching | A new Entities tab has been added to the pre-built search lists in the Basic Search window. From the new tab you can search user and entity accounts using more of the enriched data than is available by searching with common event fields. For more information, see Pre-Built Basic Search Lists in the Search Guide. This feature is currently available only if you have one of the New-Scale licenses. For more information see New-Scale Security Operations Portfolio Licenses. |
Service Health and Consumption
Feature | Description |
|---|---|
Enhanced User Experience for License View | The License View now offers an improved user experience to help you seamlessly use the charts and filters. |
Site Collectors 2.5
Feature | Description |
|---|---|
Multi-template support for Windows File Collector and Linux File Collector | Site Collector now offers multi-template support for the Windows File Collector and the Linux File Collector. You can now apply multiple templates and specify different log conditions for each of the templates. |
Splunk fetch interval | The Splunk collector now provides more options for the time interval within which the collector fetches logs. |
Support Package Generation Command for Collectors | The Windows Event Log Collector, Windows File Collector and Windows Archive Collector now provide a command on the user interface to share the support package with the Exabeam support team while configuring a collector instance. By running the support package command using PowerShell, users can share the support package with the support team for troubleshooting and remediation of issues if any. |
Ubuntu 24.04 support by Site Collector | Site Collector now supports the Ubuntu 24.04 operating system for Site Collection installation. |
Early Access Feature | |
SSL Connection for the Kafka Collector | In addition to the existing SASL protocol, the Kafka collector now offers an option to connect securely via SSL protocol and add custom security certificates. This feature is now available as part of Site Collectors Early Access program. |
Threat Center
Feature | Description | |
|---|---|---|
Analytics Rules Detections | If you have a New-Scale Security Operations Portfolio license, you can now investigate triggered analytics rules in Threat Center as detections. 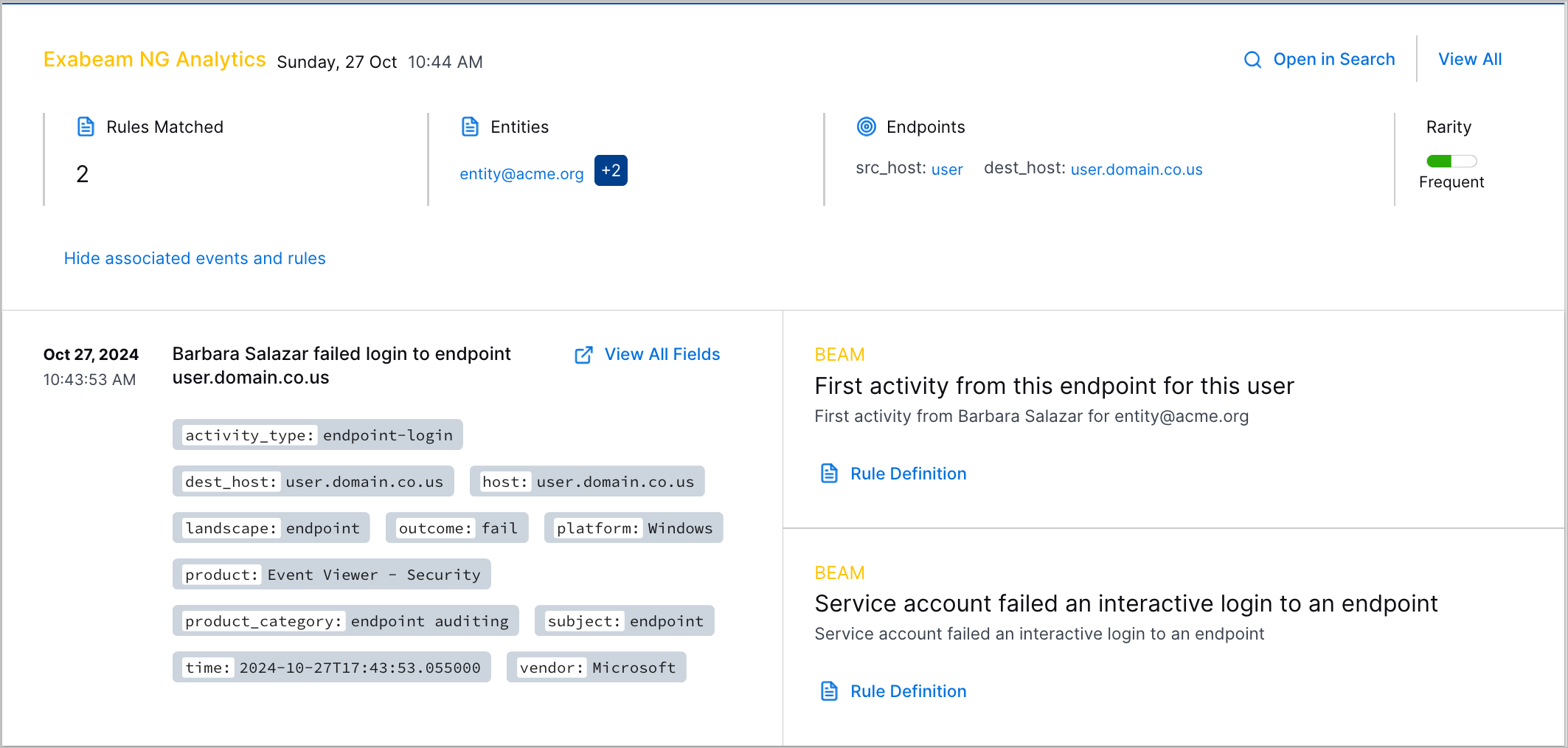 | |
Risk Score Calculation with Behavioral Analytics | With Threat Detection Management on the New-Scale Security Operations platform, risk score calculations for alerts and cases are now based on behavioral analytics insights and more accurately reflect real risk. The analytics engine assigns detections a rarity score depending on how often Threat Detection Management rules trigger in your environment. Case and alert risk scores are calculated using a combination of detection rarity scores and certain confidence factors. | |
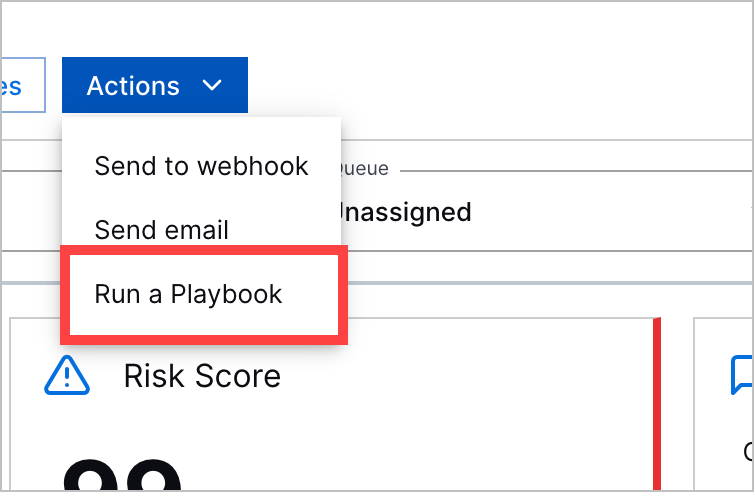
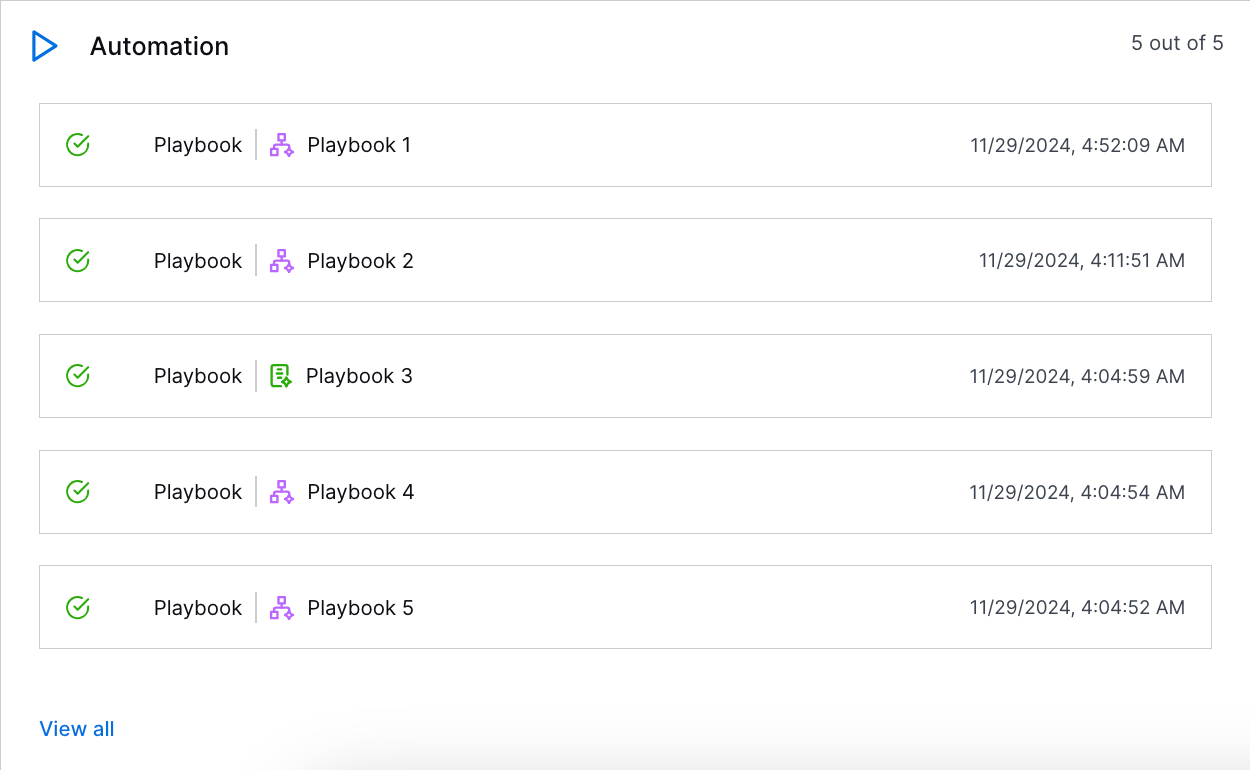
Automation Management in Threat Center | Threat Center is now more deeply integrated with Automation Management. You can now:
| |
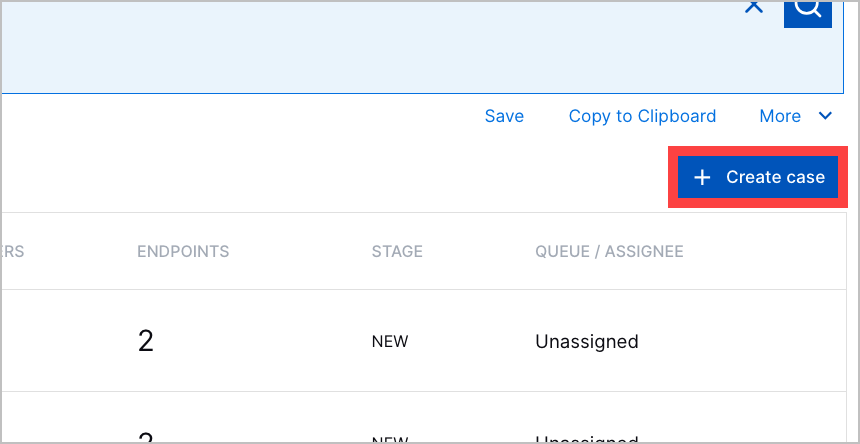
Manual Case Creation | You can now manually create a case from scratch, without associating it with an alert.
| |
Copilot Case Names | You can now better understand what a case represents and quickly decide which case to work on with AI-generated case names. Only cases converted from an alert have AI-generated case names. | |
Enhanced Entity Display | Entities are now displayed more intuitively. User entities are shown as their full name or email address. If neither information is available, user entities are shown as their username. Device entities are shown as their host name. | |
Device Entity Details | To better understand a device entity in the context of a case or alert, you can now view entity device details from Attack Surface Insights directly in Threat Center. | |
User Entity Search | To focus your investigation on a specific user entity, you can now search for cases and alerts whose detections are grouped by a specific user entity. When you build a search, you can now navigate to the Entities tab to search for a user entity by their full name or known account, like username or email.
| |
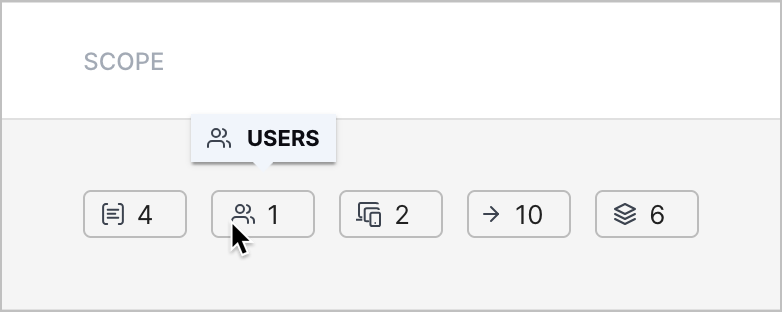
Scope Column | When you view the list of cases and alerts, you can now quickly identify the number of objects associated with a case or alert with a new SCOPE column. 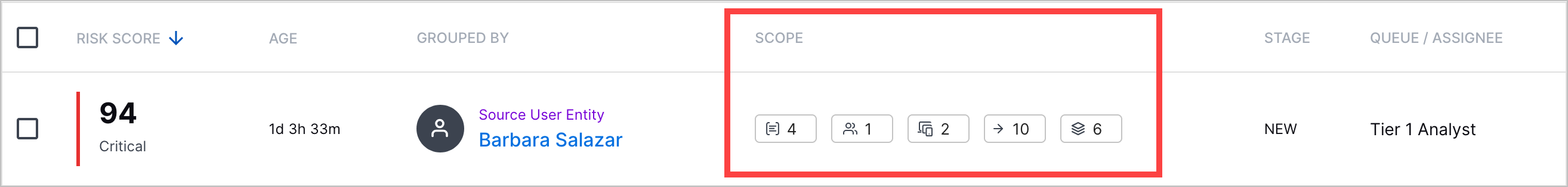 Under the SCOPE column, you can view the number of:
To view the definition of an object, hover over the object count.
| |
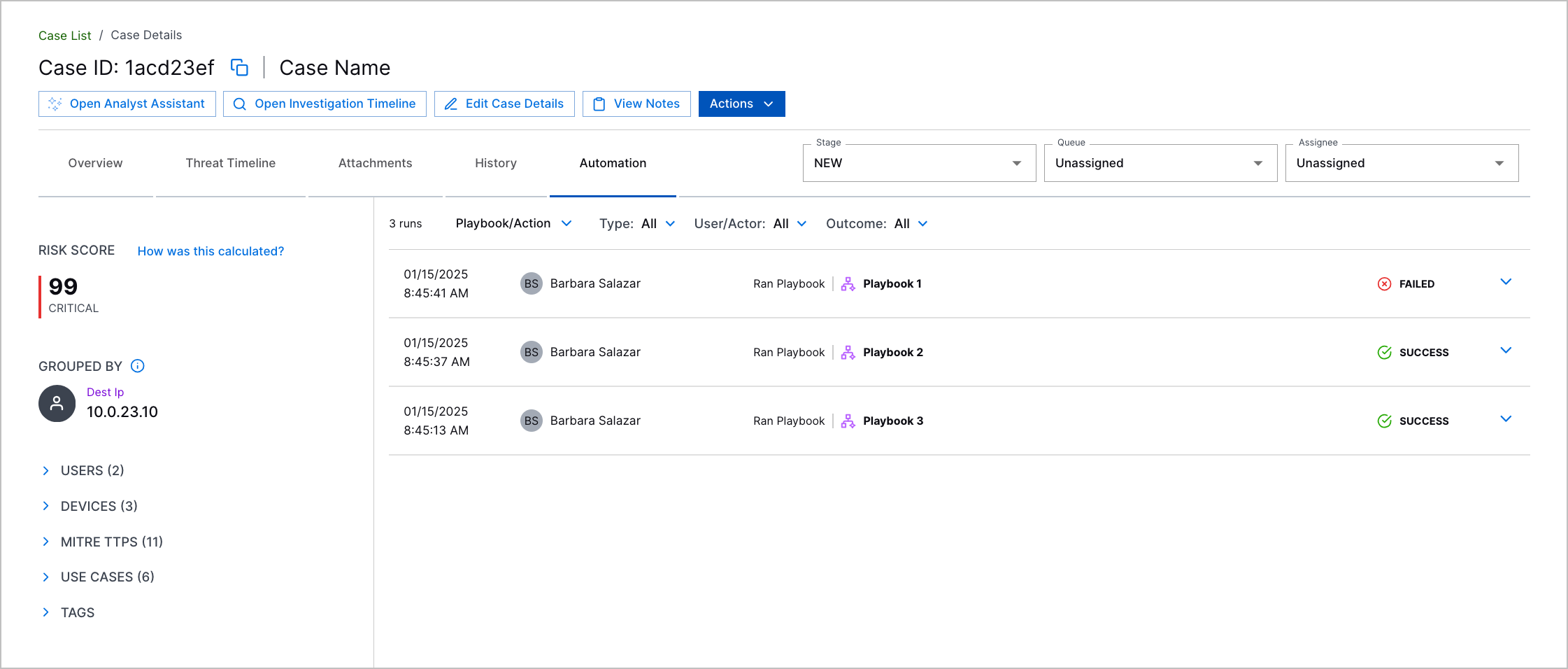
Open Investigation Timeline Enhancements | To investigate the most pertinent events related to a case or alert in Search, you can now click Open Investigation Timeline in a case or alert to automatically navigate to events in Search that have an assigned risk score. |
Threat Detection Management
Feature | Description |
|---|---|
Introducing Threat Detection Management | Welcome to Threat Detection Management, the the hub on New-Scale Security Operations Platform for the rules you use to detect threats. It centralizes all rules, including both correlation and analytics, and both pre-built and custom, so you can ensure you're surfacing what's important to your organization in one place. Threat Detection Management is supported with a New-Scale SIEM, New-Scale Analytics, or New-Scale Fusion license. To get started with Threat Detection Management, view the Threat Detection Management documentation. |
Threat Center Outcomes Exclusions for Test Mode | To ensure you investigate and triage only real threats in Threat Center, correlation rules in test mode no longer create Threat Center cases or alerts. Events created from a triggered correlation rules in test mode have the activity type |
Resolved Issues
Site Collectors 2.5 Hot Fixes
Release | Hot Fix Description |
|---|---|
2.5.8 | Resolved an issue in which messages from the syslog collector instances at high EPS lacked a delimiter, resulting in parsing issues. This issue was related to the static metadata header which is only enabled for the New-Scale Security Operations Platform customers. To prevent parsing issues and take advantage of the static metadata header for cost reduction and improved collector efficiency, upgrade to the latest Site Collectors version. |
2.5.3 | Resolved an issue related to the minifi attribute for the Windows File Collector. |
2.5.2 | Resolved an issue related to the minifi attribute for the Windows File Collector. |
2.5.1 | 0.9.1 – Fixed an issue with restoration of the Site Collector during an upgrade failure. 0.9.2 – Implemented a fix to ensure appropriate deletion of older controller services. 0.9.3 – Implemented updates for static metadata header. 0.9.4 – Implemented updates for static metadata header. |
Site Collectors 2.5 CVE Remediations
The Site Collectors 2.5 (January 2025) release includes remediated security vulnerabilities. For more information about Exabeam’s commitment to remediating vulnerabilities for Site Collector, see the Vulnerability Remediation Policy.
There are no open known CVEs in any container image (Nifi). Toolkit has been deprecated and is no longer in use hence no security vulnerabilities update is available for that.
The following table lists the CVEs remediated for the Nifi container and their severity.
Critical | High | Medium | Low |
|---|---|---|---|
Total: 0 | Total: 0 | Total: 3 | Total: 5 |
|
|