- Get Started with Threat Center
- Threat Center
- Threat Center Permissions
- Threat Center Alerts: Read
- Threat Center Alerts: Read, Write, and Delete
- Threat Center Cases: Read
- Threat Center Cases: Read, Write, and Delete
- Threat Center Detection Grouping Rules: Read
- Threat Center Detection Grouping Rules: Read, Write, and Delete
- Threat Center Watchlist: Read
- Threat Center Watchlist: Read, Write, and Delete
- Threat Center Cases
- Threat Center Alerts
- Threat Center Detections
- Threat Center Risk Score
- Monitor Entities of Interest in Threat Center
- Group Detections
- Work on Cases
- Work on Alerts
- Edit and Collaborate in Threat Center
- Use Automation Tools in Threat Center
- Find Cases and Alerts
- Sort Cases or Alerts
- Filter Cases or Alerts
- Search for Cases or Alerts in Threat Center
- Build a Search in Threat Center
- Enter a Search Using Exabeam Query Language in Threat Center
- Enter a Search Using Natural Language in Threat Center
- Run a Recent Search in Threat Center
- Create a New Saved Search in Threat Center
- Run a Saved Search in Threat Center
- Edit a Saved Search in Threat Center
- Delete a Saved Search in Threat Center
- View Case and Alert Metrics
- Get Notified About Threat Center
- Threat Center APIs
Threat Center Detections
Get to know detections, indicators of a potential threat.
A detection represents risky activity symptomatic of a threat. A detection contains attributes from related events that define the property of the risky activity.
Detections are created when events trigger analytics rules, correlation rules, or Advanced Analytics rules. After detections are created, they're automatically grouped into cases and alerts according to detection grouping rules.
View detections and their attributes in an alert or case Threat Timeline, where they're organized in chronological order from oldest to latest.
Analytics Rules Detections
Analytics rules detections are created when an event triggers one or more analytics rules.
For an analytics rule detection, you can:
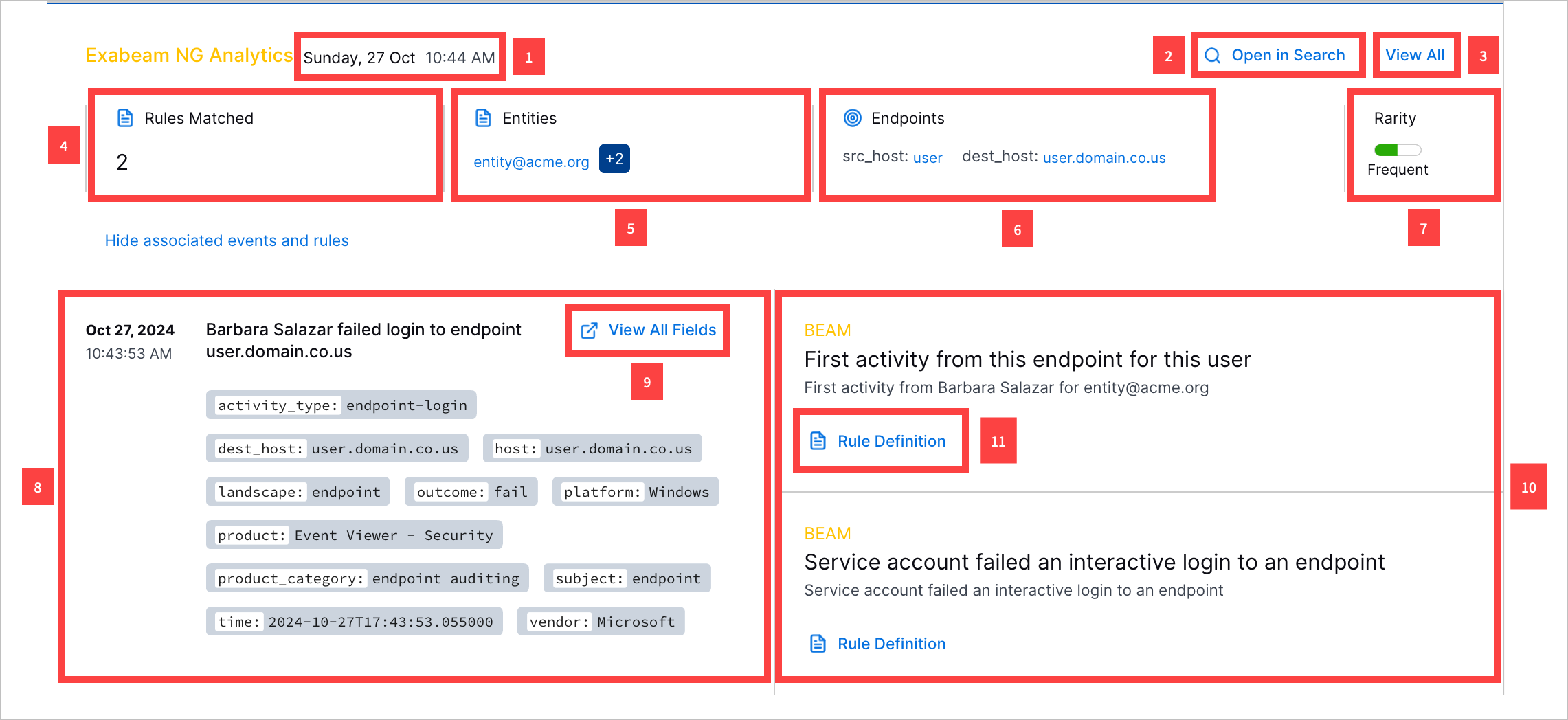
1 View the date and time the detection was created.
2 Navigate to the event in Search.
3 View all detection details, including the rarity score, MITRE ATT&CK® tactics and techniques, Exabeam use cases, tags, entities, and event fields associated with the detection.[4]
4 View the number of analytics rules associated with the detection.
5 View the entities associated with the detection.
6 View the source and destination endpoints associated with the detection.
7 View the detection rarity score.
7 View the parsed event fields associated with the detection.
8 View all event fields associated with the detection.
10 View the triggered analytics rule associated with the event.
11 View details about the triggered analytics rule:
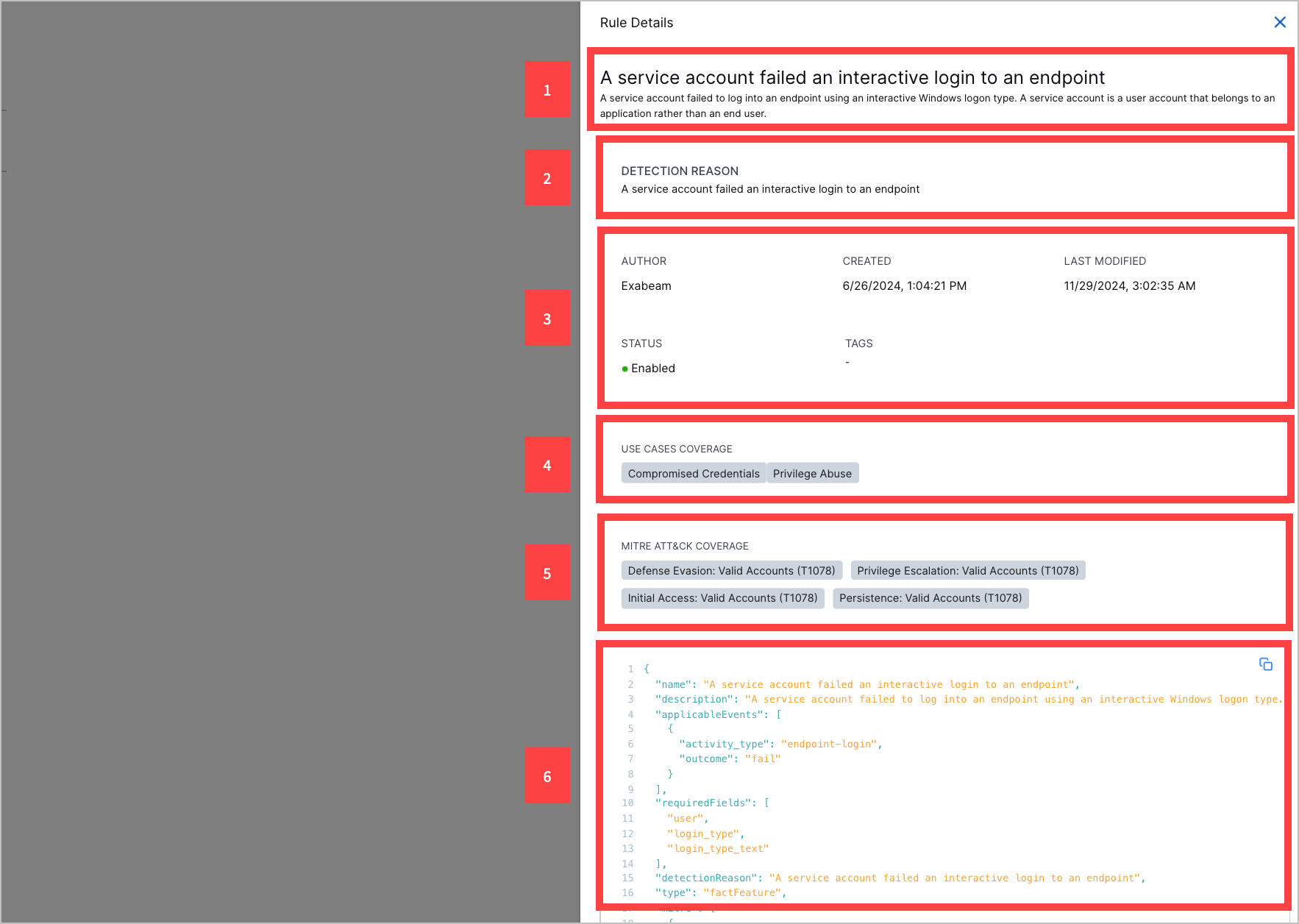
1 The triggered analytics rule name and description.
2 The reason why the event triggered the analytics rule.
3 Information about the analytics rule, including:
Author – Who created the analytics rule. If the analytics rule is pre-built, the author is Exabeam.
Created – The date and time the analytics rule was created.
Last modified – The date and time the analytics rule was last modified.
Status – Whether the analytics rule is enabled or disabled.
Tags – Tags associated with the analytics rule.
4 Exabeam use cases associated with the analytics rule.
5 ATT&CK tactics and techniques associated with the analytics rule.
6 The entire triggered analytics rule definition.
Correlation Rules Detections
Correlation rule detections function and appear differently depending on your license.
Correlation Rules Detections in the New-Scale Security Operations Portfolio Licenses
In the New-Scale Security Operations portfolio licenses, correlation rules detections are created when an event triggers one or more correlation rules. With a correlation rule detection, you can:
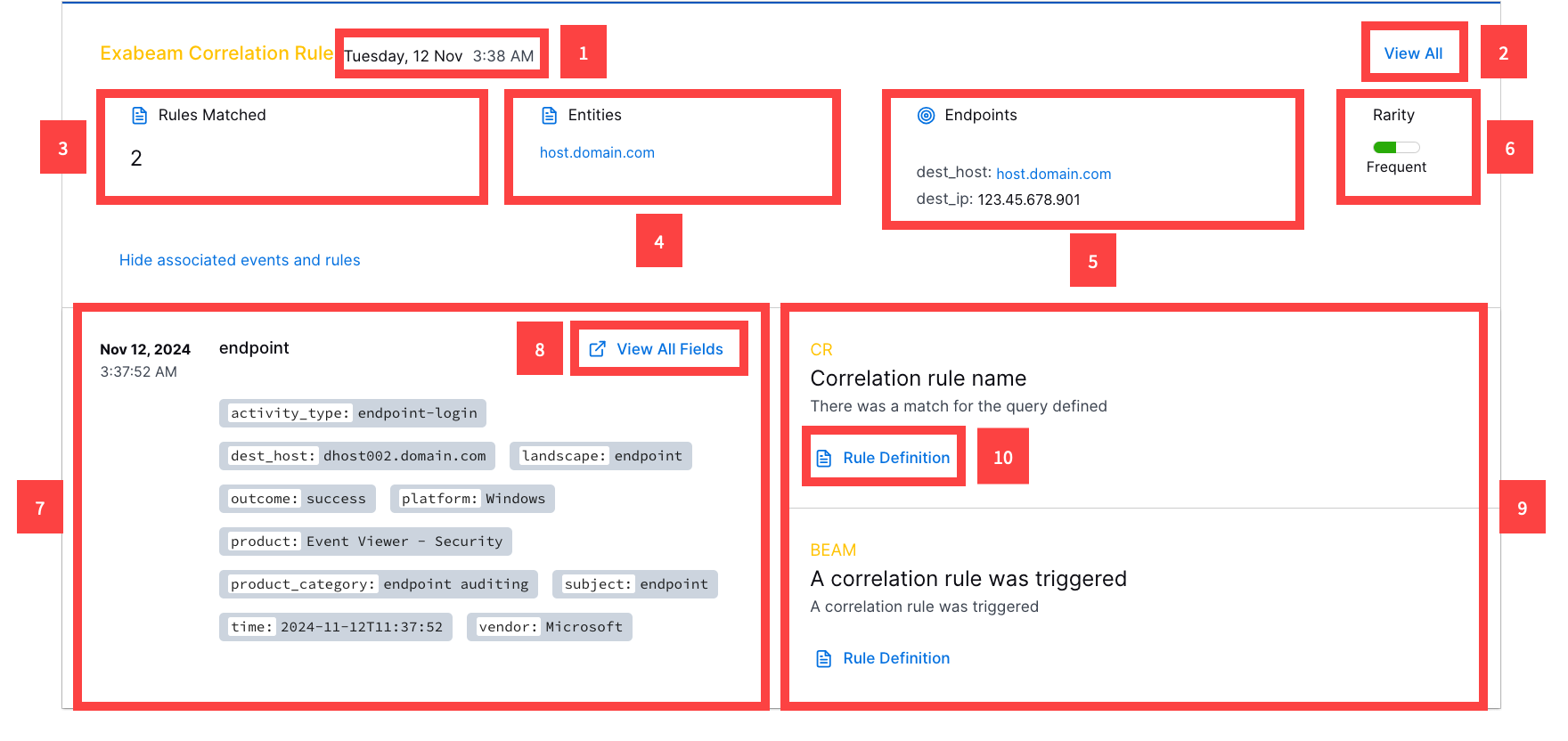
1 View the date and time the detection was created.
2 View all detection details, including the rarity score, entities, ATT&CK tactics and techniques, Exabeam use cases, tags, and event fields associated with the detection.
3 View the number of correlation rules associated with the detection.
4 View the entities associated with the detection.
5 View the endpoints associated with the detection.
6 View the detection rarity score.
7 View the parsed event fields associated with the detection.
8 View all event fields associated with the detection.
9 View the name and description of the correlation rules that created the detection.
10 View details about the triggered correlation rule:
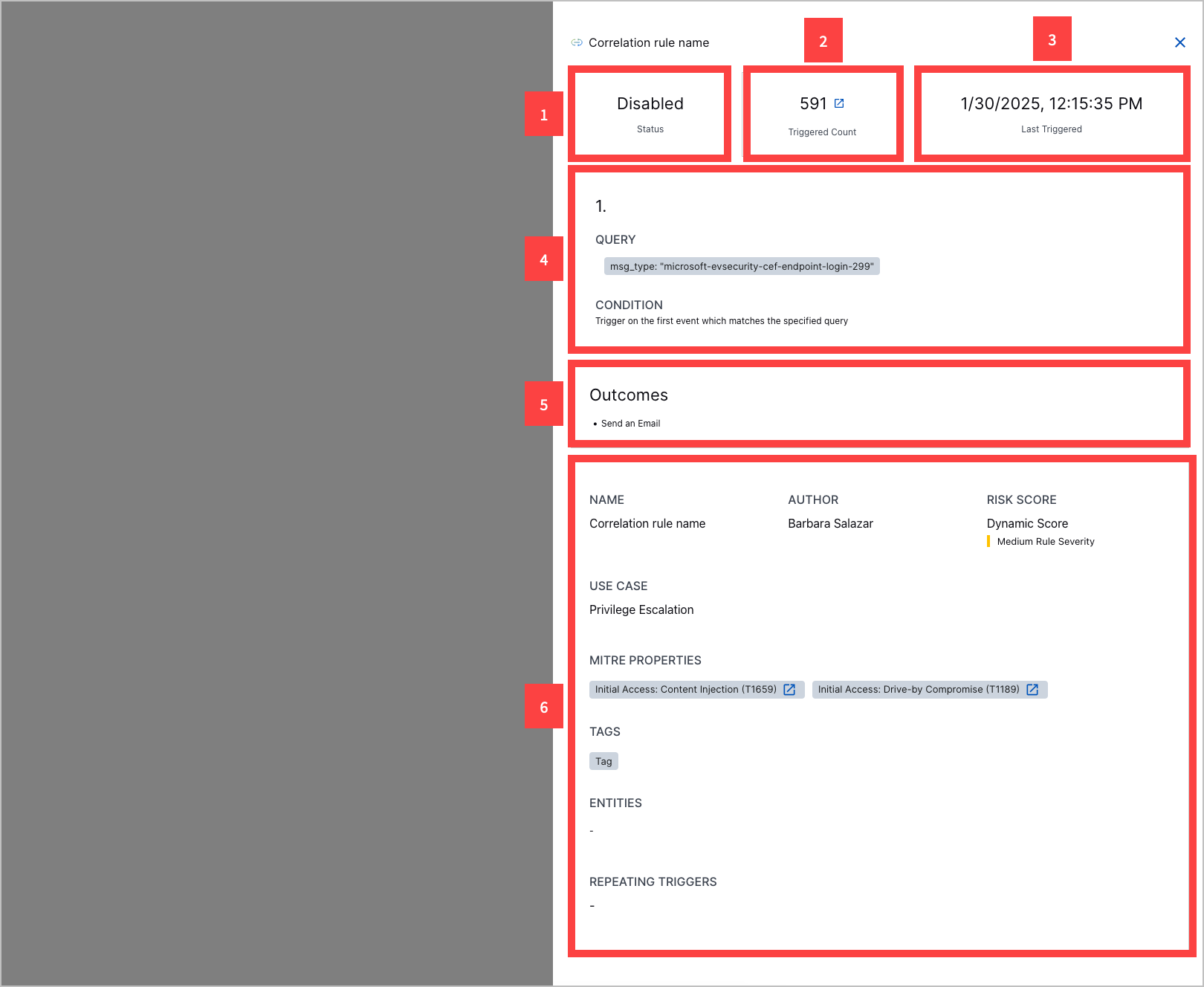
1 Whether the rule is enabled or disabled.
2 How many times the rule has triggered.
3 The date and time the rule was last triggered.
4 The rule sequences, including the search query that defines which events the events trigger the correlation rule and the conditions that must be satisfied for the rule to trigger.
5 The rule outcomes; what happens when the correlation rule triggers.
6 Other information about the rule, including:
Name – The correlation rule name.
Author – Who created the correlation rule.
Severity – The rule severity: None, Low, Medium, High or Critical.
Use Case – The Exabeam use case most relevant to the rule.
MITRE Properties – The ATT&CK techniques most relevant to the rule.
Tags – Tags associated with the rule.
Entities – Entities associated with the rule.
Repeating Triggers – The field values by which the rule is suppressed if the rule is over-triggered.
Correlation Rules Detections in the Exabeam Security Operations Portfolio and Fusion Licenses
In the Exabeam Security Operations portfolio and Fusion licenses, correlation rules create detections when the rule triggers and a Threat Center alert or case is the outcome. With a correlation rule detection, you can:
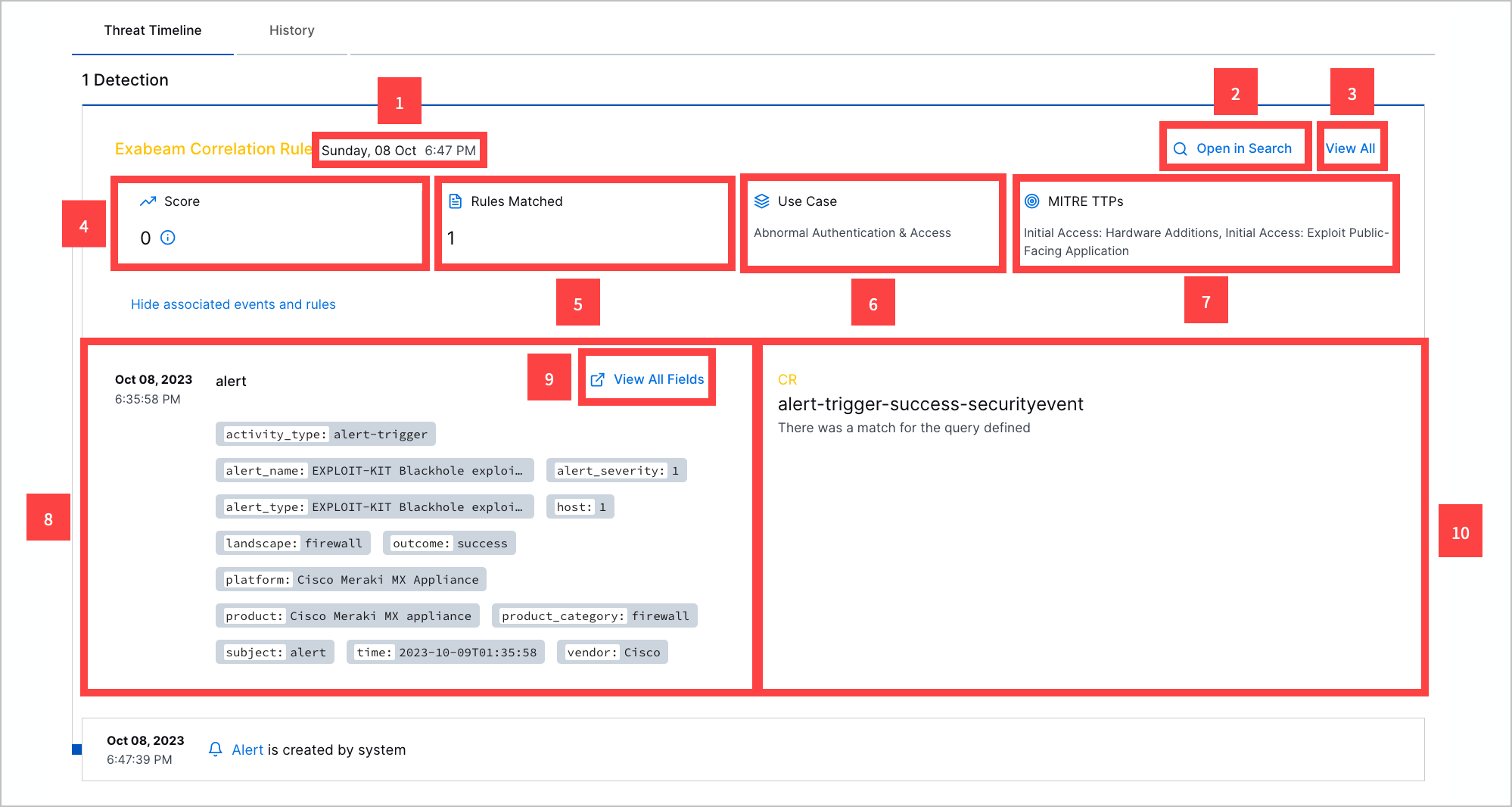
1 View the date and time the detection was created.
2 Navigate to the event in Search.
3 View all detection details, including the rarity score, entities, ATT&CK tactics and techniques, Exabeam use cases, tags, and event fields associated with the detection.
4 View the detection risk score.
5 View the number of correlation rules associated with the detection.
6 View the detection risk score.
7 View the ATT&CK tactics and techniques the detection best describes.
7 View the parsed event fields associated with the detection.
8 View all event fields associated with the detection.
10 View the name and description of the correlation rule that created the detection.
Advanced Analytics Detections
Advanced Analytics detections are created when an event triggers one or more Advanced Analytics fact-based or model-based rules.
For an Advanced Analytics detection, you can:
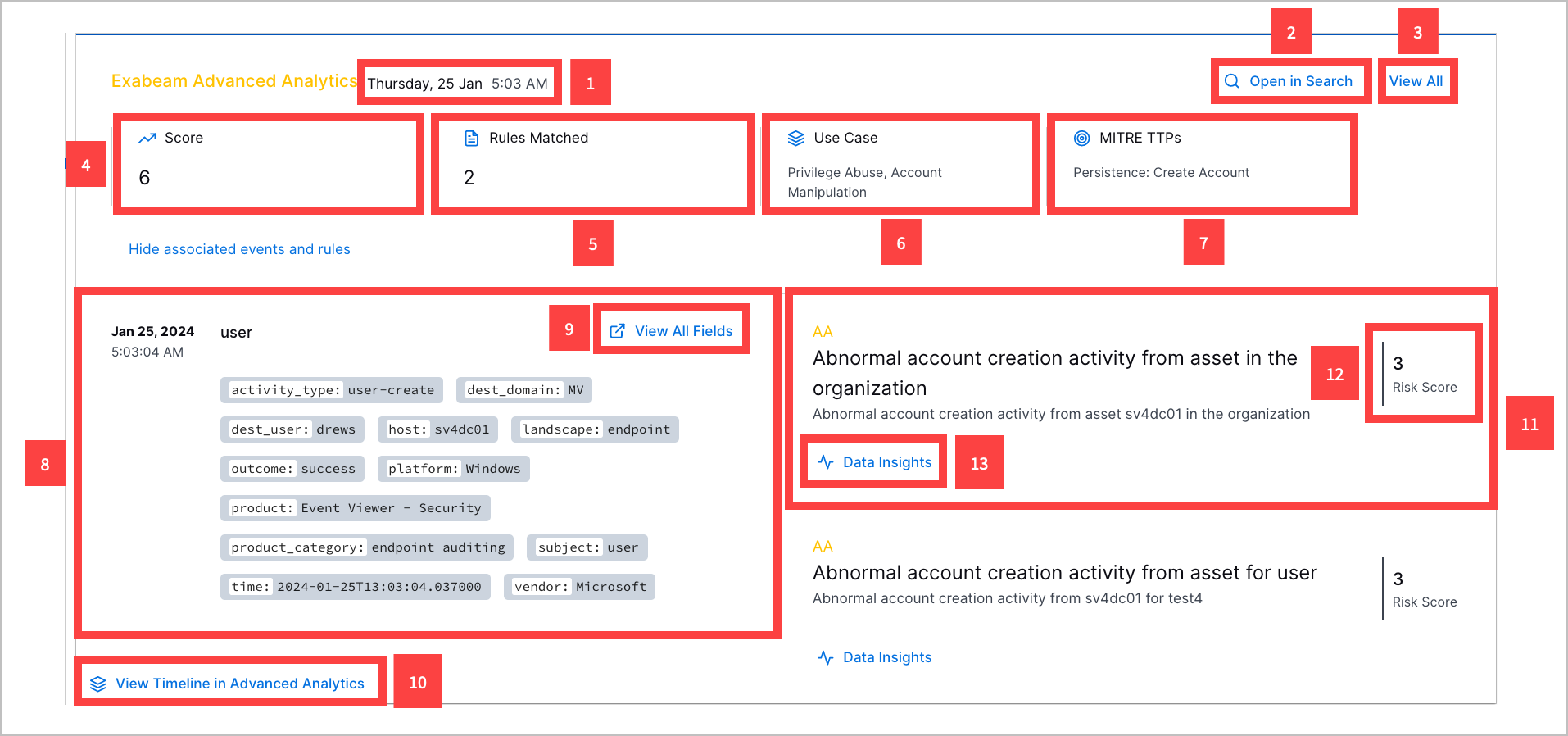
1 View the date and time the detection was created.
2 Navigate to the event in Search.
3 View all detection details, including the risk score, entities, ATT&CK tactics and techniques, Exabeam use cases, tags, and event fields associated with the detection.
4 View the number of Advanced Analytics rules associated with the detection.
5 View the endpoints associated with the detection.
6 View the detection risk score.
7 View the parsed event fields associated with the detection.
8 View all event fields associated with the detection.
9 Navigate to the Advanced Analytics Smart Timeline™ to view all user or asset events.
10 View a triggered Advanced Analytics rule associated with the event.
11 View the triggered rule risk score.
12 For model-based Advanced Analytics rules, view information about the model associated with the triggered rule:
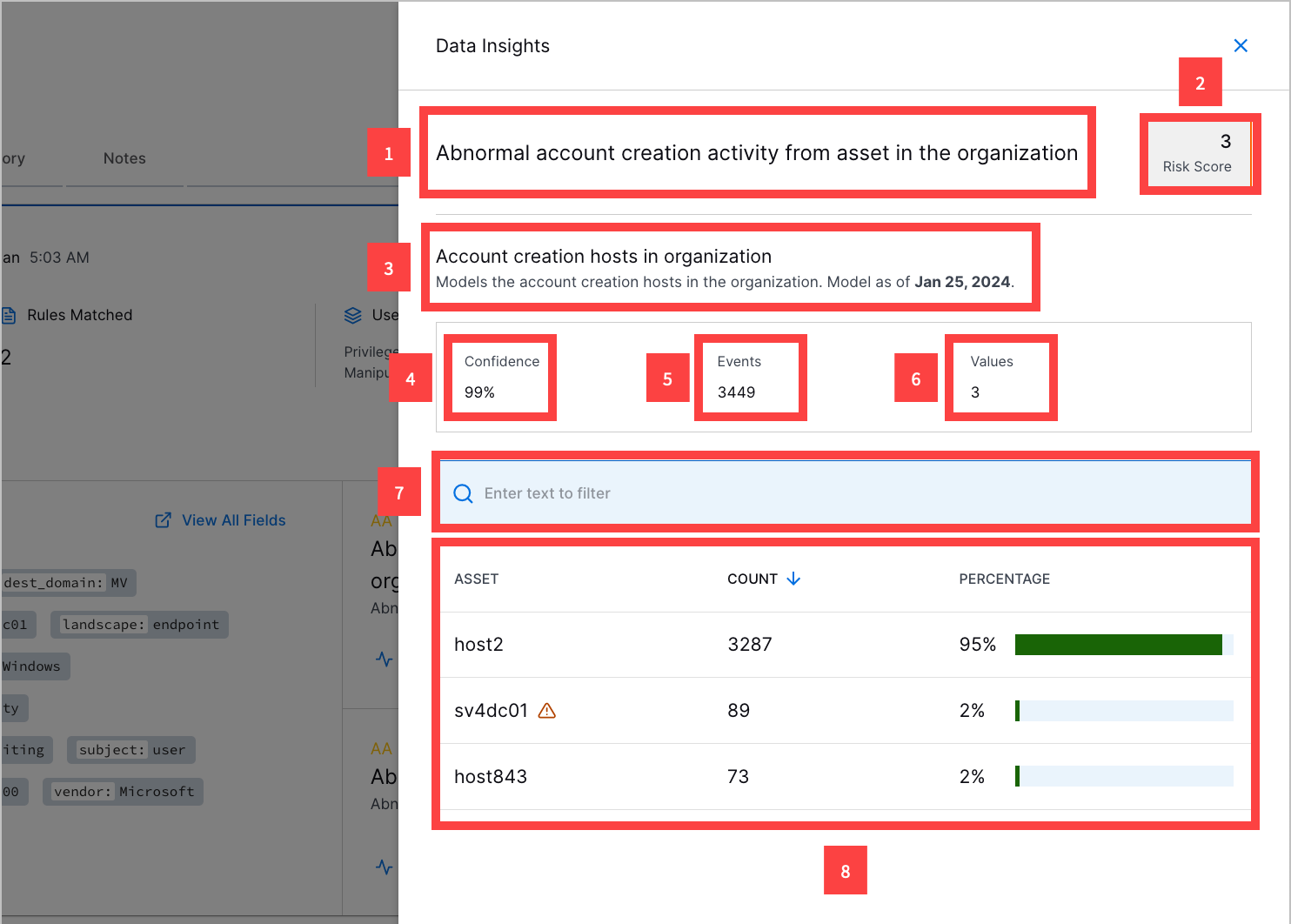
1 The triggered Advanced Analytics rule name.
2 The triggered Advanced Analytics rule risk score.
3 Name and description of the behavior modeled and the date and time the model was last updated.
4 The percentage confidence Exabeam has in the model's accuracy.
5 The number of events the model has evaluated.
6 The number of unique feature values the model has evaluated; for example, the number of unique hosts the Account creation hosts in organization model has evaluated.
7 Find a specific feature value the model has evaluated.
8 All unique feature values the model has evaluated, the number of times the model evaluated the feature value, and how often the feature value in events appears as a percentage of all events. The percentage is calculated by:
Equation 1.where P is the percentage, C is the number of number of times the model evaluated the feature value, and E is the number of event the model has evaluated.
When you restart the Advanced Analytics Analytics Engine, Threat Center automatically reprocesses Advanced Analytics detections and ensures Threat Center stays in sync with Advanced Analytics. When Threat Center starts reprocessing Advanced Analytics detections, you receive a notification. During reprocessing, Threat Center may remove obsolete Advanced Analytics detections from open cases and alerts or close cases that contain only obsolete Advanced Analytics detections. After Threat Center reprocesses Advanced Analytics detections, it groups them according to your detection grouping rules.
[4] MITRE ATT&CK and ATT&CK are trademarks of The MITRE Corporation ("MITRE"). Exabeam is not affiliated with or sponsored or endorsed by MITRE. Nothing herein is a representation of the views or opinions of MITRE or its personnel.
