- Incident Responder Release Notes
- Get Started with Incident Responder
- Configure Incident Responder Settings
- Core Settings
- Analytics Settings
- Configure Services
- Prerequisites for Configuring Incident Responder Microsoft Services with OAuth2.0 Authentication
- Configure the Amazon Elastic Compute Cloud (EC2) Service
- Configure the Anomali ThreatStream API Service
- Configure the Atlassian Jira Service
- Configure the BMC Remedy Service
- Configure the Check Point Firewall Service
- Configure the Cisco AMP for Endpoints Service
- Configure the Cisco Services Engine (ISE) Service
- Configure the Cisco Threat Grid Service
- Configure the Cisco Umbrella Enforcement Service
- Configure the Cisco Umbrella Investigate Service
- Configure the CrowdStrike Falcon Host API Service Service
- Configure the CrowdStrike Falcon Host API Service Service
- Configure the CyberArk Service
- Configure the Cylance Protect Service
- Configure the Exabeam Advanced Analytics Service
- Configure the Exabeam Cloud Search Service
- Configure the Exabeam DL Service
- Configure the FireEye HX Service
- Configure the Fortinet Service
- Configure the Google Gmail Service
- Configure the IntSights Cyber Intelligence Ltd. Service
- Configure the IRNotificationSMTPService Service
- Configure the Microsoft Active Directory (AD) (Latest) Service
- Configure the Microsoft Exchange Service
- Configure the Microsoft Outlook Office 365 Service
- Configure the Microsoft Windows Defender ATP Service
- Configure the Microsoft Windows Management Instrumentation Service
- Configure the Netskope Service
- Configure the Okta Service
- Configure the Palo Alto Networks Firewall Service
- Configure the Palo Alto Networks Wildfire Service
- Configure the Rapid7 insightVM Service
- Configure the SentinelOne Service
- Configure the SentinelOneV2 Service
- Configure the Service Now Service
- Configure the Slack Service
- Configure the SlashNext Service
- Configure the Splunk Service
- Configure the ThreatConnect API Service
- Configure the Urlscan.io API Service
- Configure the VirusTotal Service
- Configure the Zscaler Service
- Test a Service
- Edit a Service
- Disable a Service
- Upload a Custom Service
- Delete a Custom Service
- Create an Email Template for the Notify by Email Action
- Respond to Security Incidents
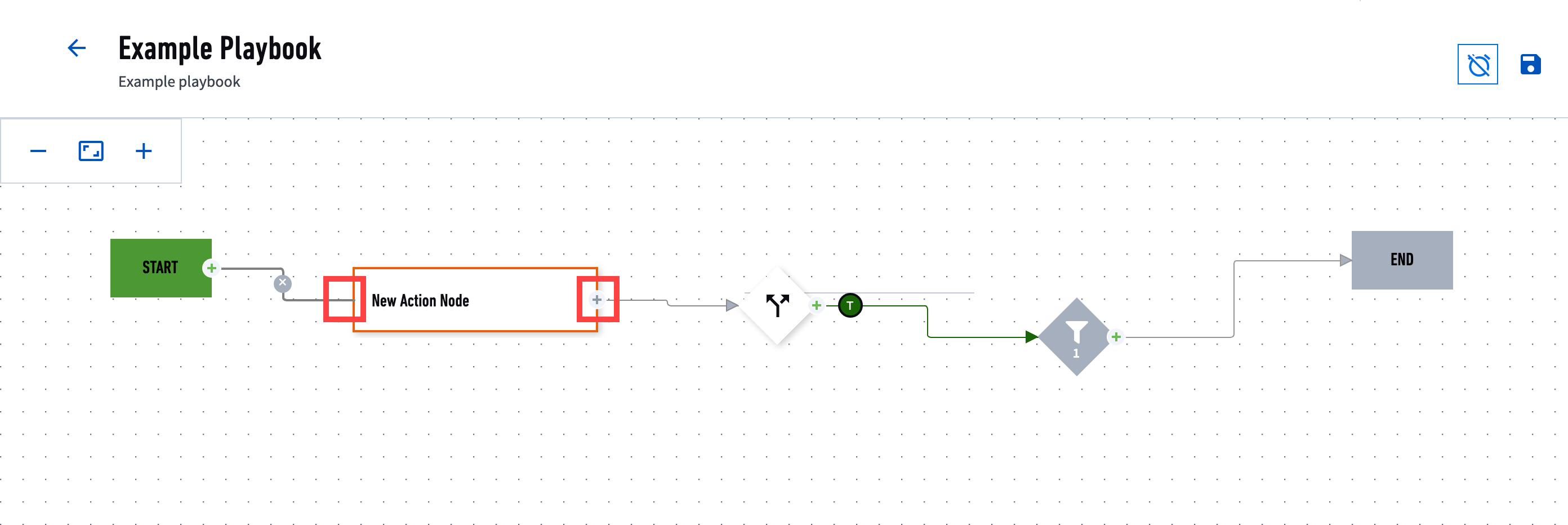
Playbook Terminology
Define all the terms you encounter when dealing with playbooks.
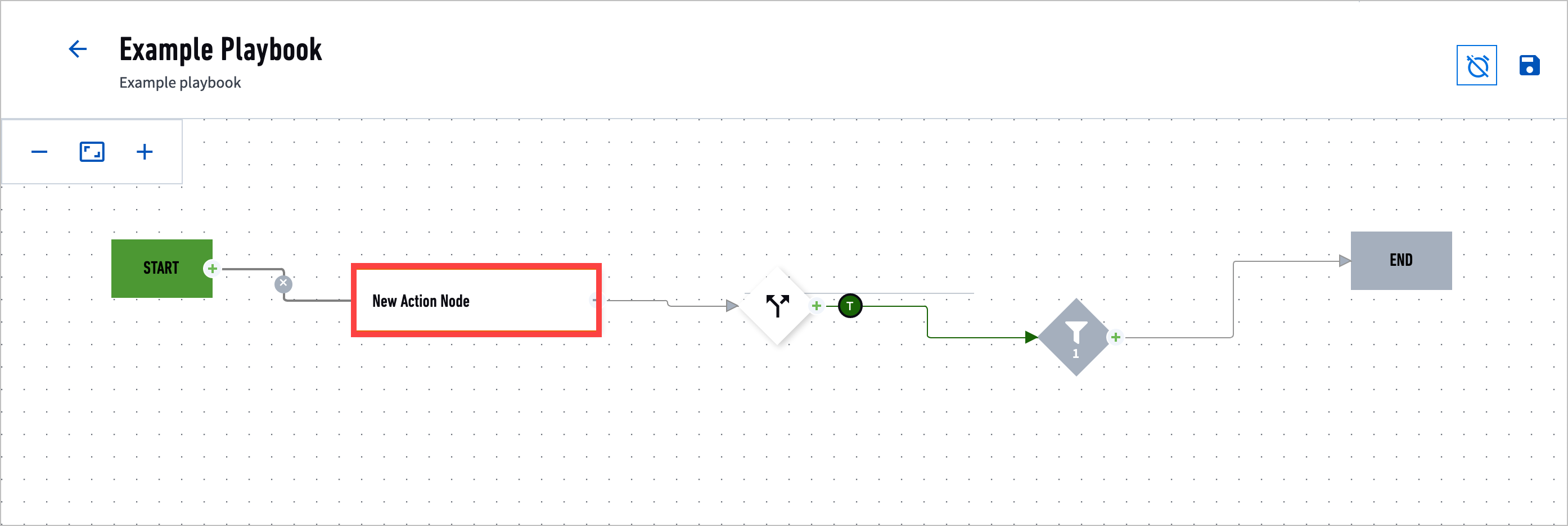
- Action
A scripted task to call a third-party API service and gather data, executed manually or automatically using playbooks; for example, retrieve the reputation information for a given URL or search emails by sender.
You use action nodes in playbooks. It has an inbound port on the left and an outbound port on the right.
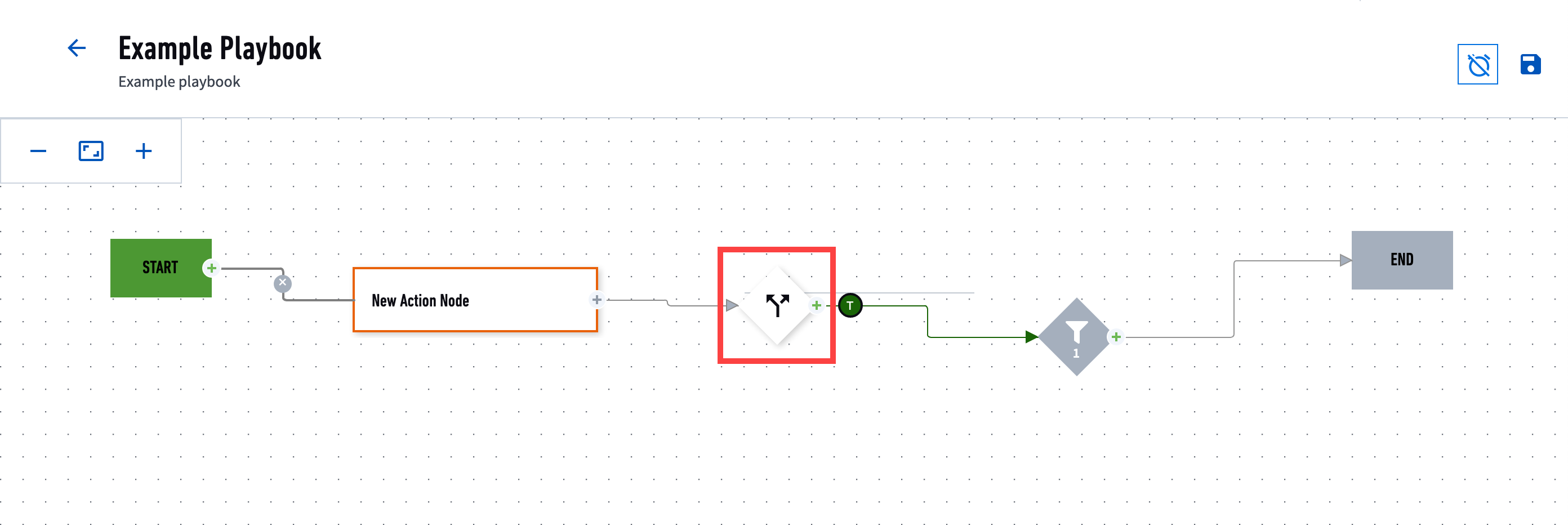
- Decision
A node that indicates a boolean (if/else) decision. It has one inbound node on the left, an if/true node on the right, and else/false nodes on the top and bottom.
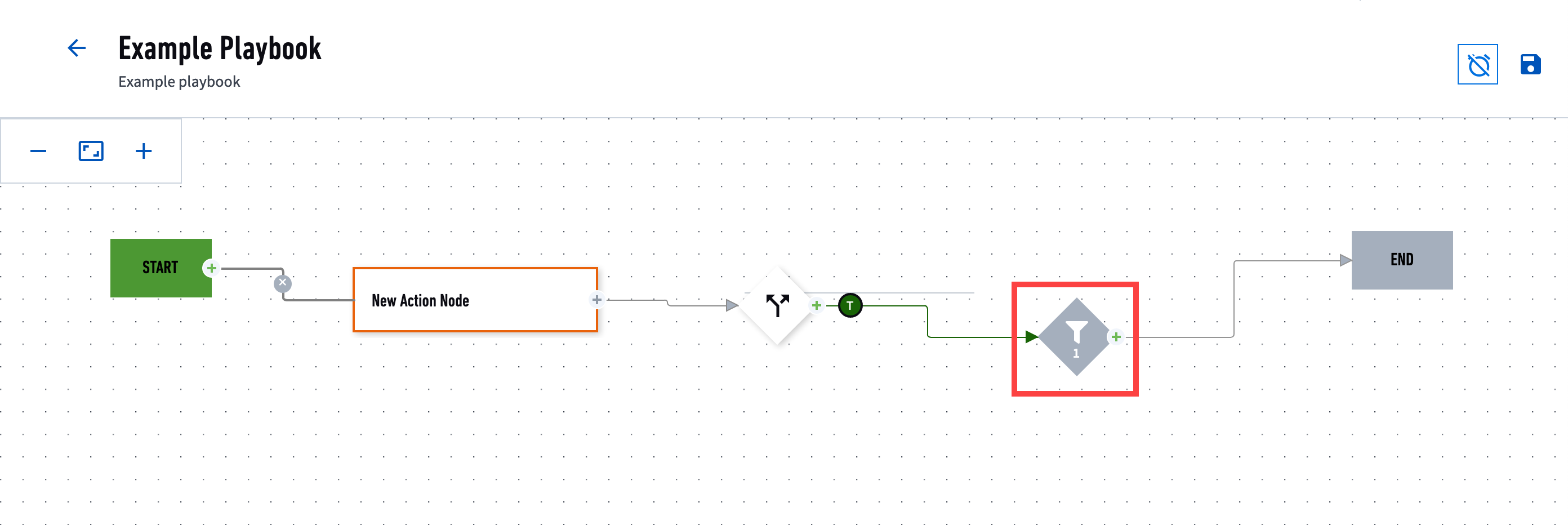
- Filter
A node that filters out a subset of the input source based on conditions you specify when you configure the node. The filter node outputs the remaining subset and passes it on to the next node. It has one inbound node on the left and an outbound port on the right.
- Input
Data passed from one node to another; data from a Case Manager incident, entity, or artifact.
- Node
The fundamental building blocks of playbooks. Each represent an action, decision, filter, start, or end.
- Operator
Compares operands and returns a logical value if the comparison is true. Operands may be numerical, string, logical, or object values. Strings are compared based on standard lexicographical ordering, using Unicode values.
- Port
Each action, decision, or filter node has at least one inbound port and one outbound port that connects it to another node. An inbound port receives data from another note. An outbound node sends data.
The only nodes that don't have one inbound and outbound port are the start and end nodes. The start node only has one outbound port. The end node has only one inbound port.
- Service
A third-party product or vendor you integrate with Incident Responder to run actions and playbooks; for example: Cisco Threat Grid and Palo Alto Networks Wildfire. You interact with multiple instances of a service from within Incident Responder. Information about a service, like how to connect to it and which actions are defined, is stored in the Incident Responder server.