- Incident Responder Release Notes
- Get Started with Incident Responder
- Configure Incident Responder Settings
- Core Settings
- Analytics Settings
- Configure Services
- Prerequisites for Configuring Incident Responder Microsoft Services with OAuth2.0 Authentication
- Configure the Amazon Elastic Compute Cloud (EC2) Service
- Configure the Anomali ThreatStream API Service
- Configure the Atlassian Jira Service
- Configure the BMC Remedy Service
- Configure the Check Point Firewall Service
- Configure the Cisco AMP for Endpoints Service
- Configure the Cisco Services Engine (ISE) Service
- Configure the Cisco Threat Grid Service
- Configure the Cisco Umbrella Enforcement Service
- Configure the Cisco Umbrella Investigate Service
- Configure the CrowdStrike Falcon Host API Service Service
- Configure the CrowdStrike Falcon Host API Service Service
- Configure the CyberArk Service
- Configure the Cylance Protect Service
- Configure the Exabeam Advanced Analytics Service
- Configure the Exabeam Cloud Search Service
- Configure the Exabeam DL Service
- Configure the FireEye HX Service
- Configure the Fortinet Service
- Configure the Google Gmail Service
- Configure the IntSights Cyber Intelligence Ltd. Service
- Configure the IRNotificationSMTPService Service
- Configure the Microsoft Active Directory (AD) (Latest) Service
- Configure the Microsoft Exchange Service
- Configure the Microsoft Outlook Office 365 Service
- Configure the Microsoft Windows Defender ATP Service
- Configure the Microsoft Windows Management Instrumentation Service
- Configure the Netskope Service
- Configure the Okta Service
- Configure the Palo Alto Networks Firewall Service
- Configure the Palo Alto Networks Wildfire Service
- Configure the Rapid7 insightVM Service
- Configure the SentinelOne Service
- Configure the SentinelOneV2 Service
- Configure the Service Now Service
- Configure the Slack Service
- Configure the SlashNext Service
- Configure the Splunk Service
- Configure the ThreatConnect API Service
- Configure the Urlscan.io API Service
- Configure the VirusTotal Service
- Configure the Zscaler Service
- Test a Service
- Edit a Service
- Disable a Service
- Upload a Custom Service
- Delete a Custom Service
- Create an Email Template for the Notify by Email Action
- Respond to Security Incidents
PrevNext
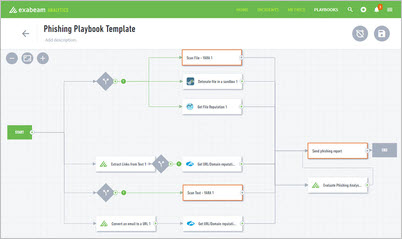
Phishing Playbook Template
Break down the logic flow of the out-of-the-box phishing playbook template.
 |
Phishing emails imitate reputable senders to fool recipients into installing malicious software or revealing personal information.
The phishing playbook sources emails ingested into Case Manager. It checks the reputation of the domain that sent the email; extracts any files, URLs, or links; and checks the reputation of these entities. Then, the playbook checks if the email recipient has any web activity related to the URL.
Based on the sender's email address, the playbook searches for other recipients. If it finds other recipients, the playbook alerts you.
