- Get Started with Threat Detection Management
- Analytics Rules
- Analytics Rule Classifications
- Create an Analytics Rule
- Manage Analytics Rules
- Tune Analytics Rules
- Find Analytics Rules
- Share Analytics Rules
- Troubleshoot Analytics Rules
- Analytics Rules Syntax
- Advanced Analytics Rule Syntax vs. Analytics Rule Syntax
- Logical Expressions in Analytics Rule Syntax'
- String Operations Using Analytics Rule Syntax
- Integer Operations Using Analytics Rule Syntax
- Time Operations Using Analytics Rule Syntax
- Network Operations Using Analytics Rule Syntax
- Context Operations Using Analytics Rule Syntax
- Entity Operations Using Analytics Rule Syntax
- Correlation Rule Operations Using Analytics Rule Syntax
- Analytics Engine Status
- Correlation Rules
- Threat Scoring
Tune Analytics Rules
To further tune analytics rules, exclude events or event field values from triggering an analytics rule using exclusions.
Exclusions exclude certain analytics rules from triggering on specific event field value or context tables that match conditions you specify; for example, you might want to exclude routine administrative logins from being flagged as suspicious or exclude specific IP ranges commonly used by internal systems from being considered as potential attack vectors. Exclusions can apply to all analytics rules, specific analytics rules, or certain analytic rule families.
To create an exclusion, you define two properties: the conditions events or event field values must match for it to be excluded from triggering an analytics rule; and the scope of the rules to which the exclusion applies. After you create an exclusion, you can edit, enable, disable, and delete it.
View the total number of enabled exclusions under Rule Exclusions:
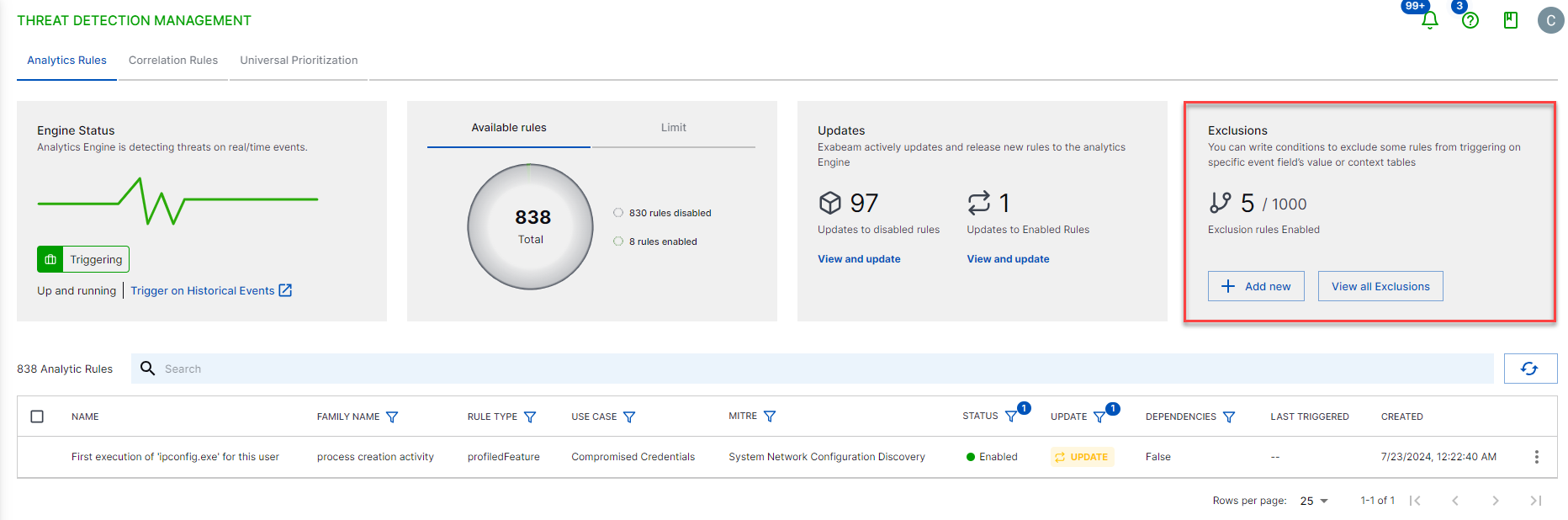 |
To view all exclusions, click View all Exclusions:
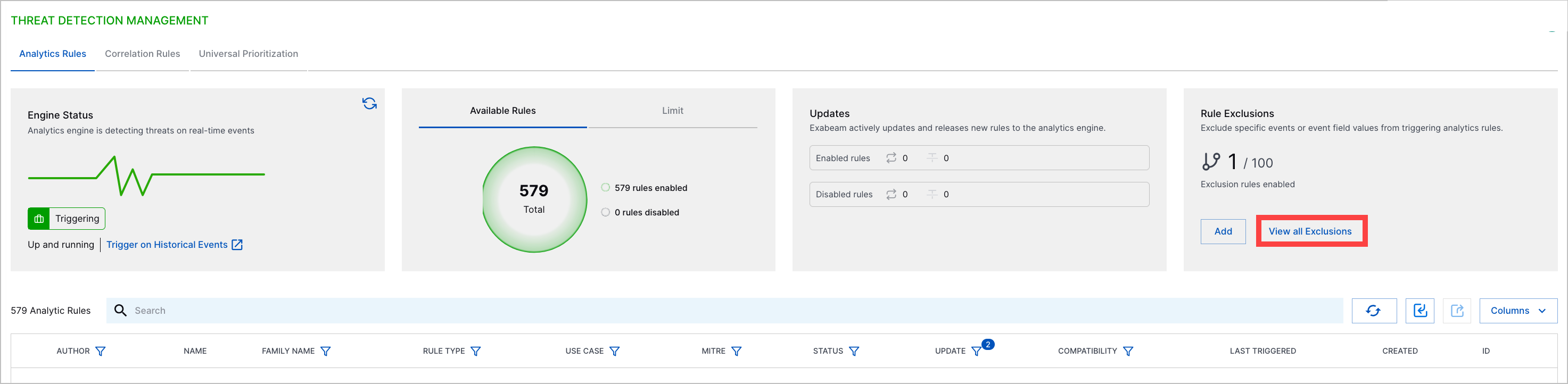
For each exclusion, view:
Title – The exclusion name and description.
Scope – The number of rules to which the exclusion applies. To view the list of rules to which the exclusion applies, hover over the column value.
Created by – Who created the exclusion.
Created – The date and time the exclusion was created.
Last modified – The date and time the exclusion was edited.
Status – Whether the exclusion is enabled or disabled.
To view more details about an exclusion, click the More menu  , then select View.
, then select View.
