- Get Started with Threat Detection Management
- Analytics Rules
- Analytics Rule Classifications
- Create an Analytics Rule
- Manage Analytics Rules
- Tune Analytics Rules
- Find Analytics Rules
- Share Analytics Rules
- Troubleshoot Analytics Rules
- Analytics Rules Syntax
- Advanced Analytics Rule Syntax vs. Analytics Rule Syntax
- Logical Expressions in Analytics Rule Syntax'
- String Operations Using Analytics Rule Syntax
- Integer Operations Using Analytics Rule Syntax
- Time Operations Using Analytics Rule Syntax
- Network Operations Using Analytics Rule Syntax
- Context Operations Using Analytics Rule Syntax
- Entity Operations Using Analytics Rule Syntax
- Correlation Rule Operations Using Analytics Rule Syntax
- Analytics Engine Status
- Correlation Rules
- Threat Scoring
Preview Correlation Rule Details
Quickly view a summary of a correlation rule.
In Threat Detection Management, navigate to the Correlation Rules tab, click the More
 menu for a rule, then select View Details.
menu for a rule, then select View Details.View information about the rule:
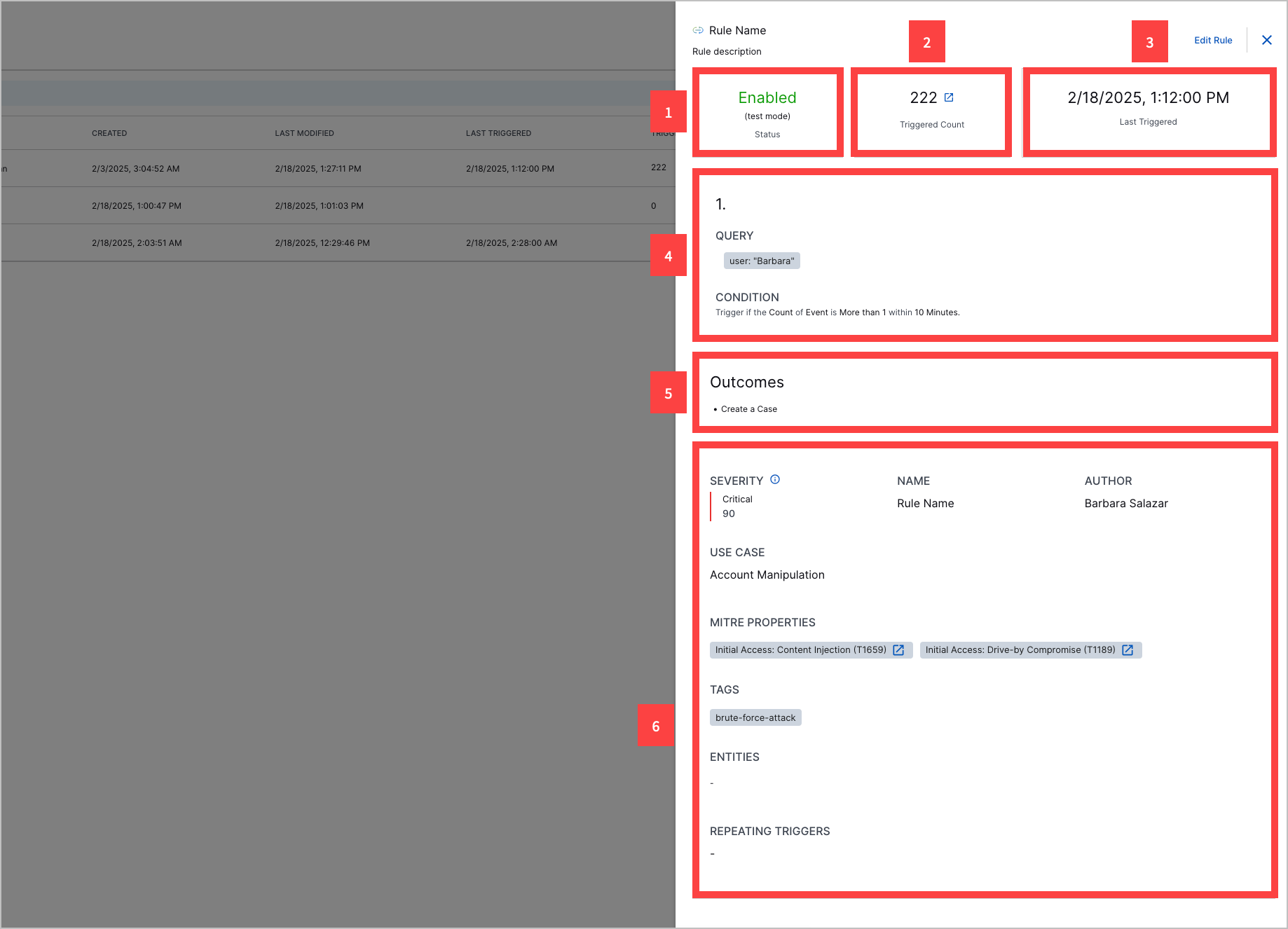
1 The rule status: Enabled, Testing, Disabled, or Stopped.
2 How many times the rule has triggered.
To view all events related to the rule in Search, click
 . You're directed to Search. The query rules.rule: "<rule name>" is automatically entered.
. You're directed to Search. The query rules.rule: "<rule name>" is automatically entered.3 The date and time the rule was last triggered.
4 The rule sequences, including the search query that defines which events the events trigger the correlation rule and the conditions that must be satisfied for the rule to trigger.
5 When the correlation rule is scheduled to trigger
6 The rule outcomes; what happens when the correlation rule triggers.
7 Other information about the rule, including:
Severity – The rule severity: None, Low, Medium, High or Critical; and the associated risk score.
Name – The correlation rule name.
Author – Who created the correlation rule.
Use Case – The Exabeam use case most relevant to the rule.
MITRE Properties – The ATT&CK techniques most relevant to the rule.
Tags – Tags associated with the rule.
Repeating Triggers – The field values by which the rule is suppressed if the rule is over-triggered.
(Optional) Edit, enable or disable, or delete the rule:
