- Get Started with Threat Detection Management
- Analytics Rules
- Analytics Rule Classifications
- Create an Analytics Rule
- Manage Analytics Rules
- Tune Analytics Rules
- Find Analytics Rules
- Share Analytics Rules
- Troubleshoot Analytics Rules
- Analytics Rules Syntax
- Advanced Analytics Rule Syntax vs. Analytics Rule Syntax
- Logical Expressions in Analytics Rule Syntax'
- String Operations Using Analytics Rule Syntax
- Integer Operations Using Analytics Rule Syntax
- Time Operations Using Analytics Rule Syntax
- Network Operations Using Analytics Rule Syntax
- Context Operations Using Analytics Rule Syntax
- Entity Operations Using Analytics Rule Syntax
- Correlation Rule Operations Using Analytics Rule Syntax
- Analytics Engine Status
- Correlation Rules
- Threat Scoring
Threat Detection Management Architecture
Understand how Threat Detection Management works with other applications and features on New-Scale Security Operations Platform to detect and surface threats.
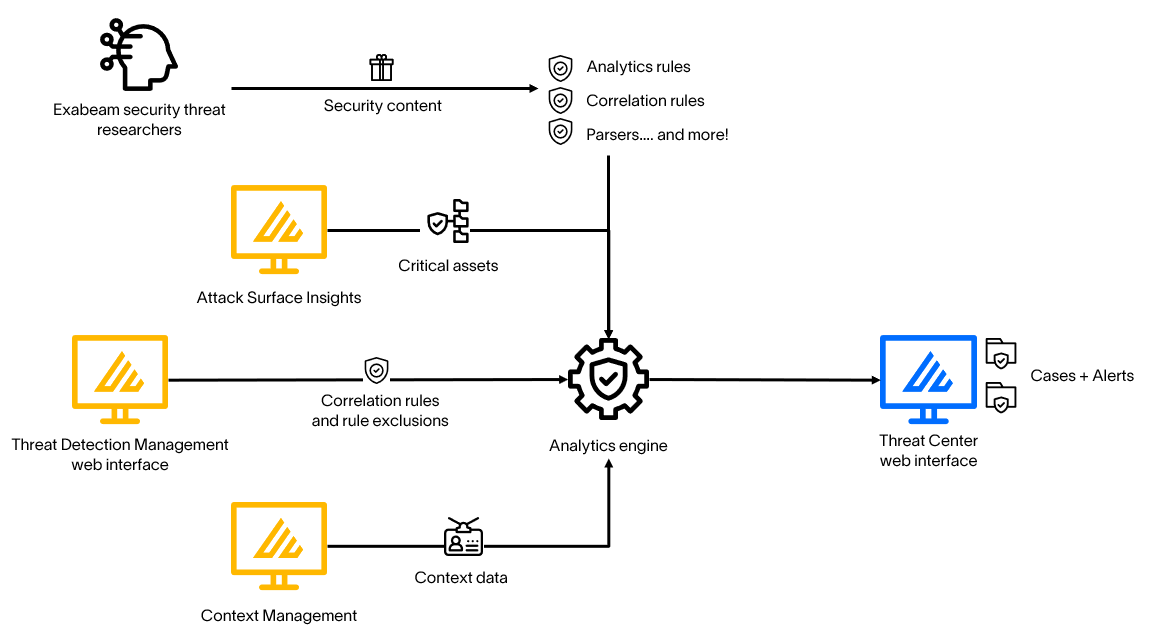
The Threat Detection Management application is available on the New-Scale Security Operations Platform. It interacts with the following services and applications:
Security content – Security content packages regularly deliver updates from Exabeam threat researchers to analytics and correlation rules in Threat Detection Management.
Analytics engine – The cloud-native analytics engine is a behavior adaptive multi-domain engine that analyzes your SIEM data. When events trigger analytics and correlation rules, the analytics engine creates detections in Threat Center.
Threat Center – When events trigger analytics and correlation rules, the analytics engine creates detections in Threat Center. Detections are grouped in alerts for you to triage. To respond to an alert, you can then escalate the alert to a case. Threat Center uses information about analytics and correlation rules as business factors when calculating a case or alert risk score.
Attack Surface Insights – The security criticality and tags assigned to an entity are referenced in some analytics rules.
Context Management – When you create a correlation rule, you can use context data to define sequences.
