- Get Started with Threat Detection Management
- Analytics Rules
- Analytics Rule Classifications
- Create an Analytics Rule
- Manage Analytics Rules
- Tune Analytics Rules
- Find Analytics Rules
- Share Analytics Rules
- Troubleshoot Analytics Rules
- Analytics Rules Syntax
- Advanced Analytics Rule Syntax vs. Analytics Rule Syntax
- Logical Expressions in Analytics Rule Syntax'
- String Operations Using Analytics Rule Syntax
- Integer Operations Using Analytics Rule Syntax
- Time Operations Using Analytics Rule Syntax
- Network Operations Using Analytics Rule Syntax
- Context Operations Using Analytics Rule Syntax
- Entity Operations Using Analytics Rule Syntax
- Correlation Rule Operations Using Analytics Rule Syntax
- Analytics Engine Status
- Correlation Rules
- Threat Scoring
PrevNext
Edit a Correlation Rule
Change the query, conditions, and outcomes for a correlation rule.
In Threat Detection Management, navigate to the Correlation Rules tab, then select a correlation rule to edit:
Click on a correlation rule, then click Edit.
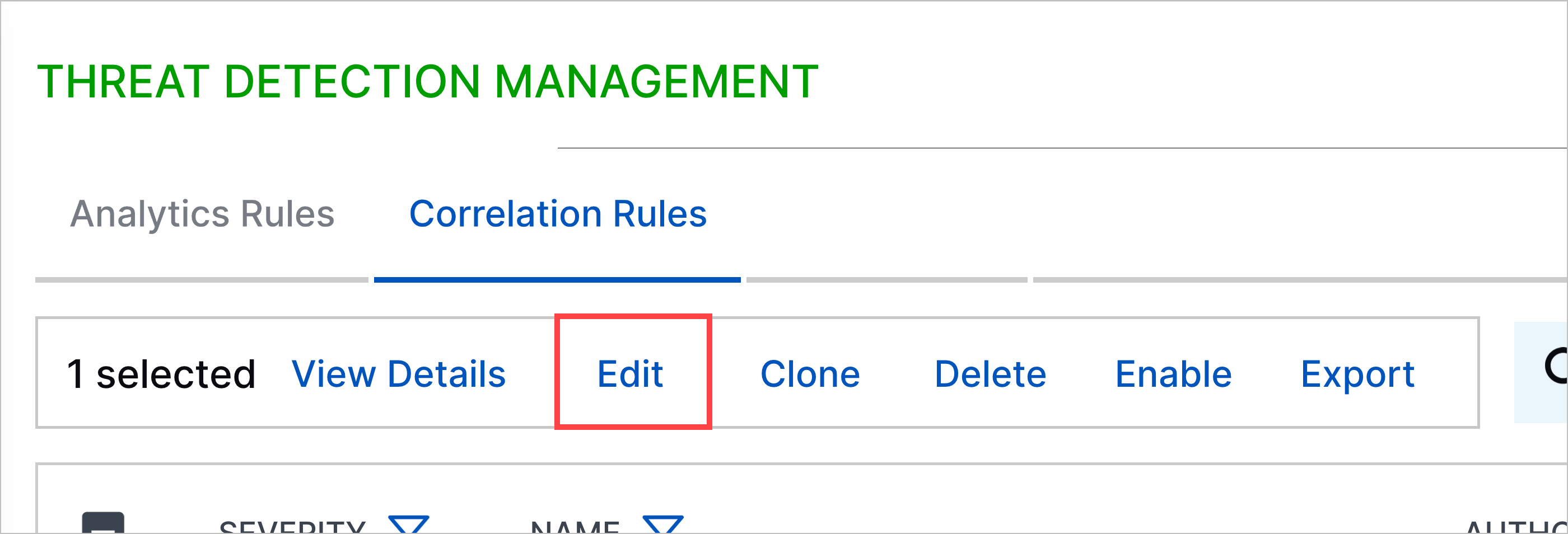
For the correlation rule you're editing, click the More menu
 , then select Edit.
, then select Edit.
Change the query, conditions, and outcomes for the correlation rule.
Review your changes, then click Save.
