- 2026 Release Notes
- 2025 Release Notes
- December 2025
- November 2025
- October 2025
- September 2025
- August 2025
- July 2025
- June 2025
- May 2025
- April 2025
- March 2025
- February 2025
- January 2025
- Known Issues
September 2025
The New-Scale Security Operations Platform includes the following addressed features and new features for September 2025.
Automation Management
Feature | Description |
|---|---|
Automation Agent Image Version 1.532.1 Upgrade | The automation agent image is now upgraded to version 1.532.1. With the upgrade:
To take advantage of this upgrade, download the upgraded automation agent image using the following command: docker pull us-docker.pkg.dev/exa-cloud-utils/public/exabeam-automation-agent:2.0 When you create and run a container using the environment variables for your automation agent, use the following updated command: docker run --env-file ./agentworkerconfig.env us-docker.pkg.dev/exa-cloud-utils/public/exabeam-automation-agent:2.0 |
Cloud Collectors
Feature | Description |
|---|---|
GCP Cloud Logging Cloud Collector | The GCP Cloud Logging Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of logs from Google Cloud services. |
GCP Security Command Center Cloud Collector | The GCP Security Command Center Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of logs from GCP Security Command Center. |
Progress ShareFile Cloud Collector | The Progress ShareFile Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of logs from the ShareFile endpoints: AccessChange, SharesSend, Activity, and SharesRequest. |
Early Access Collectors | |
Cylance Protect (now Arctic Wolf) Cloud Collector | The Cylance Protect (now Arctic Wolf) Cloud Collector is now available as part of Cloud Collectors Early Access program, to facilitate ingestion of logs from the following data sources: Memory Protection, to collect threats related to memory vulnerabilities, Threats, to collect threat detection alerts and related information, or both. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Salesforce EventLog Cloud Collector | The Salesforce EventLog Cloud Collector is now available as part of Cloud Collectors Early Access program, to facilitate ingestion of various event types from Salesforce cloud. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Snowflake Cloud Collector | The Snowflake Cloud Collector is now available as part of Cloud Collectors Early Access program, to facilitate ingestion of data from data sources Login History, Others, and Query History. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Correlation Rules
Feature | Description |
|---|---|
Standalone Case Creation from Correlation Rules | To quickly identify Threat Center cases created as the outcome of a correlation rule, you can now create a standalone case containing the correlation rule detection using a detection grouping rule. Detection grouping rules can now group correlation rule detections into a case by the correlation rule group by field. For Threat Center to create standalones case for correlation rule detections, you must create a detection grouping rule with specific conditions and actions, and the detection grouping rule must be ordered first in the list of detection grouping rules. 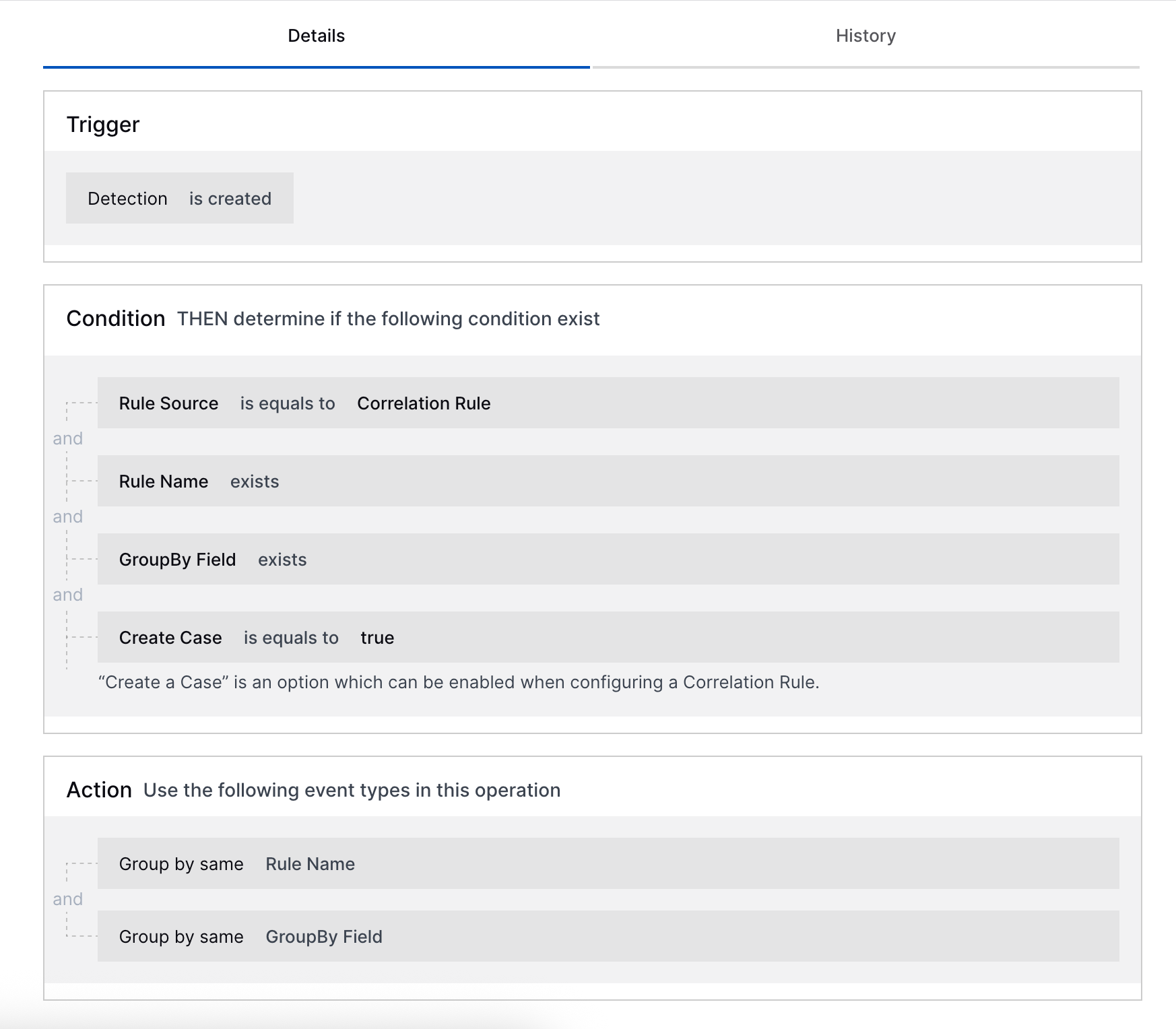 |
New and Updated Correlation Rule Templates | You can now better detect suspicious logins, exploitation of the Log4Shell vulnerability, suspicious use of system utilities, data exfiltration, firewall tampering, and common web application attacks with new correlation rule templates:
Removed obsolete correlation rule templates include:
Fields have been modified in an additional 189 correlation rule templates. |
Log Sources
Feature | Description |
|---|---|
Support for Silent Log Source Detection —from 30 Minutes of Inactivity | You can now proactively detect silent log sources before they impact operations, using the Silent Monitoring Threshold feature. You can now set the Warn After Silent For duration from 30 minutes to 72 hours to automatically detect inactivity. When a log source goes silent beyond your defined window, you are instantly notified—helping you maintain visibility and control. |
Outcomes Navigator
Feature | Description | ||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
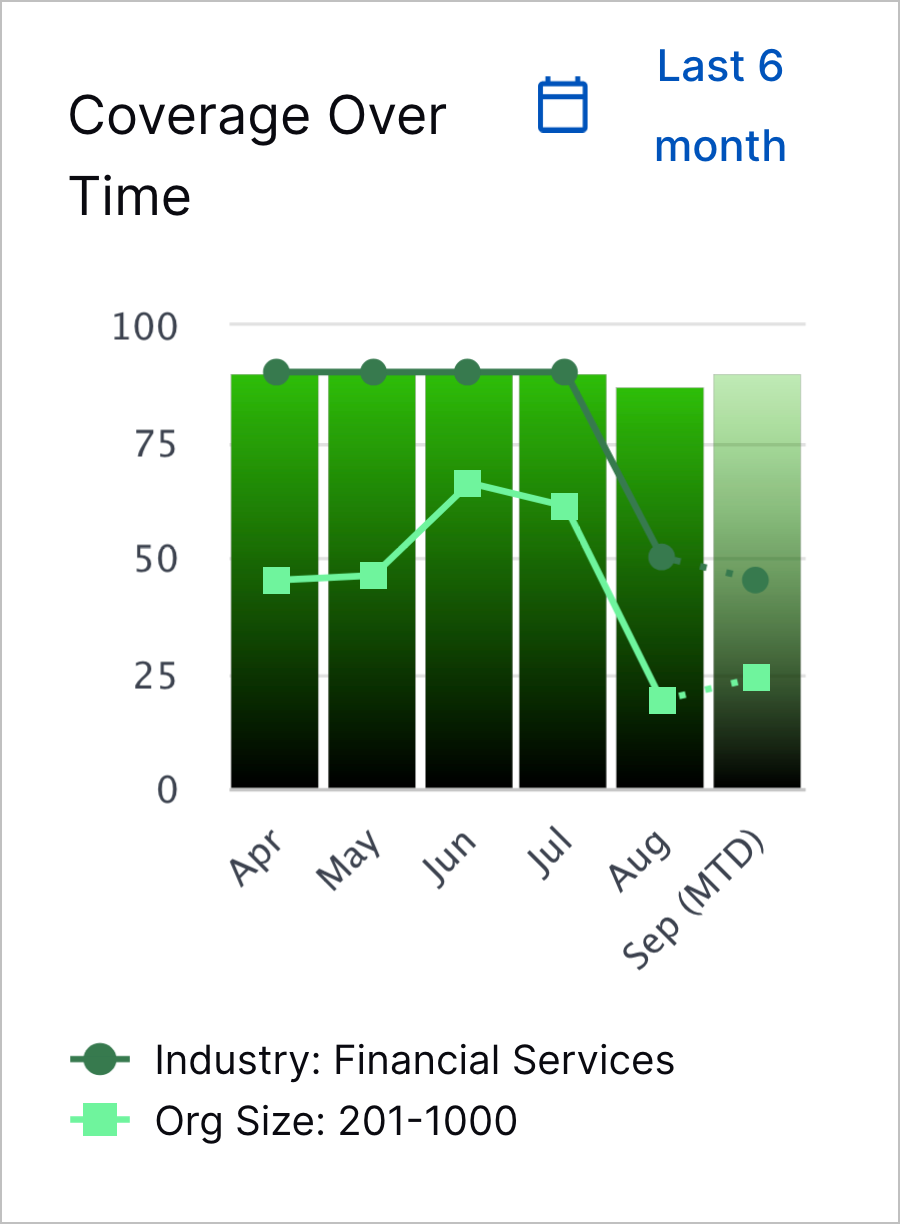
Peer Comparison | To get a better sense of how your security posture compares to that of other organizations, you can now benchmark your coverage against industry peers. Under the MITRE ATT&CK Coverage and Use Case Coverage tabs, select the organizations against which you're comparing coverage by industry and organization size: 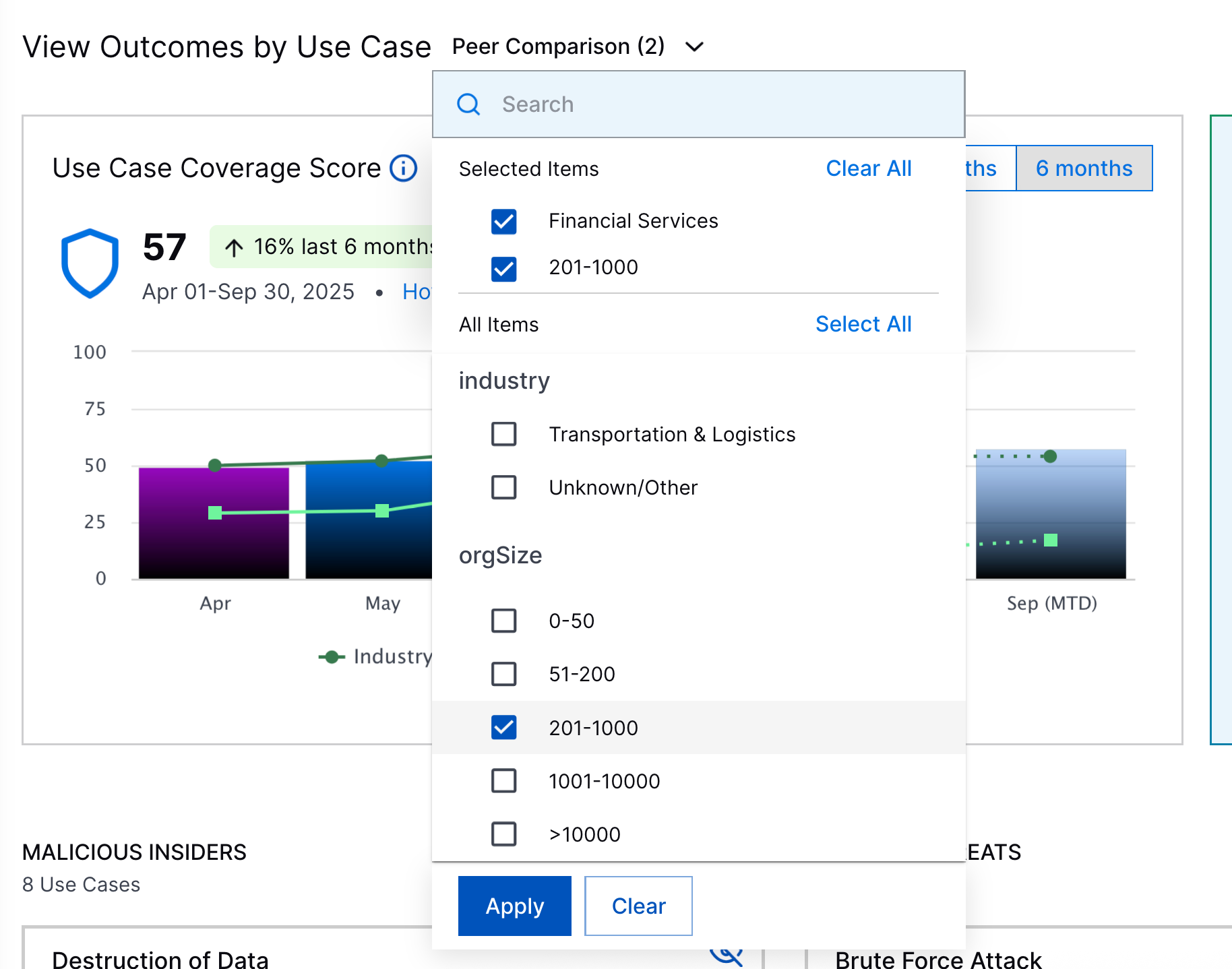 Under the overall coverage score charts, you can compare your overall coverage score against the average overall coverage score of other organizations: 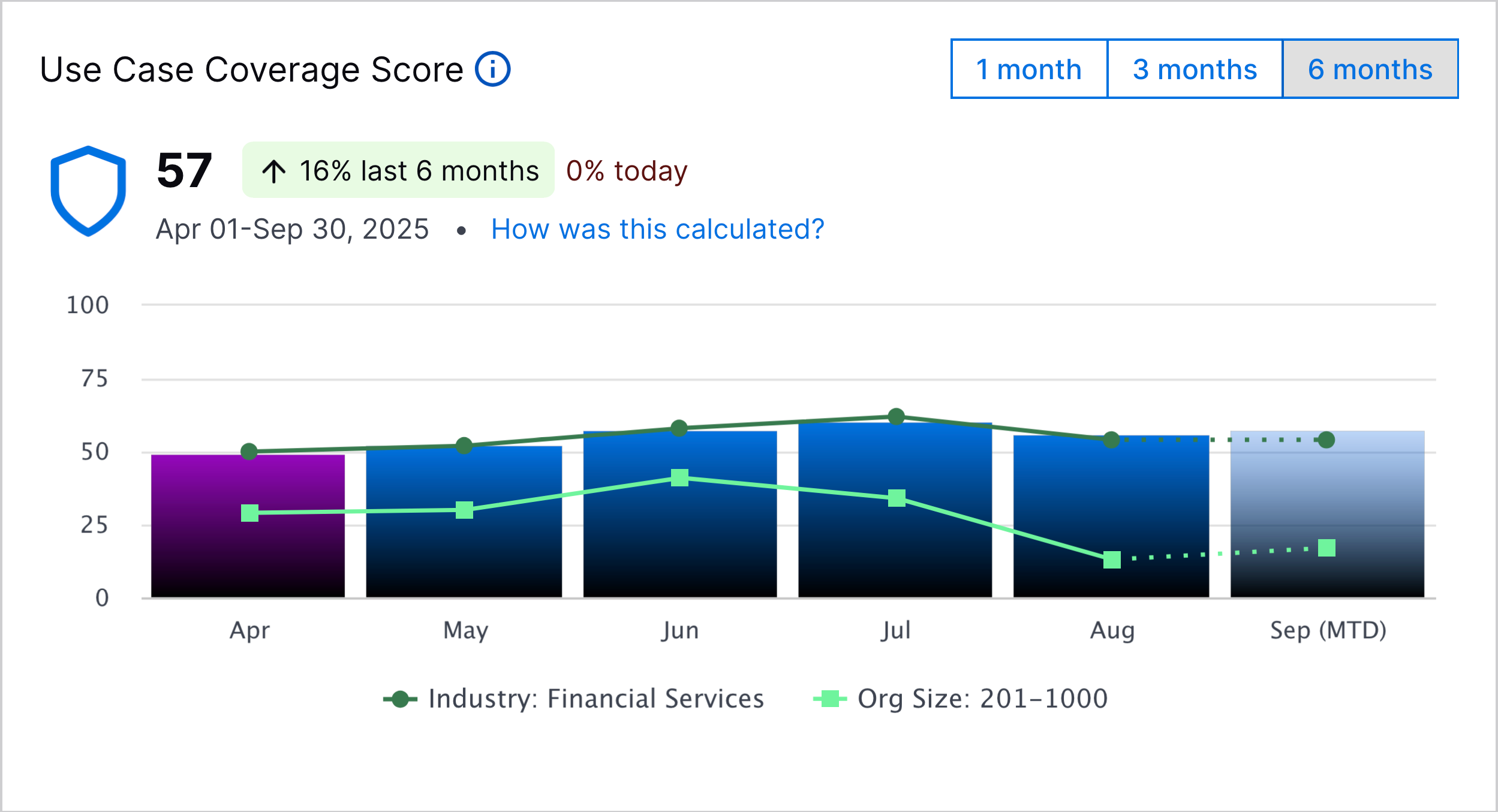 For a specific MITRE ATT&CK® technique[a] or use case, you can also use the Coverage Over Time chart to compare your coverage score for a specific technique or use case against the average coverage score of other organizations, using the same criteria for organizations you defined in the overall coverage score:
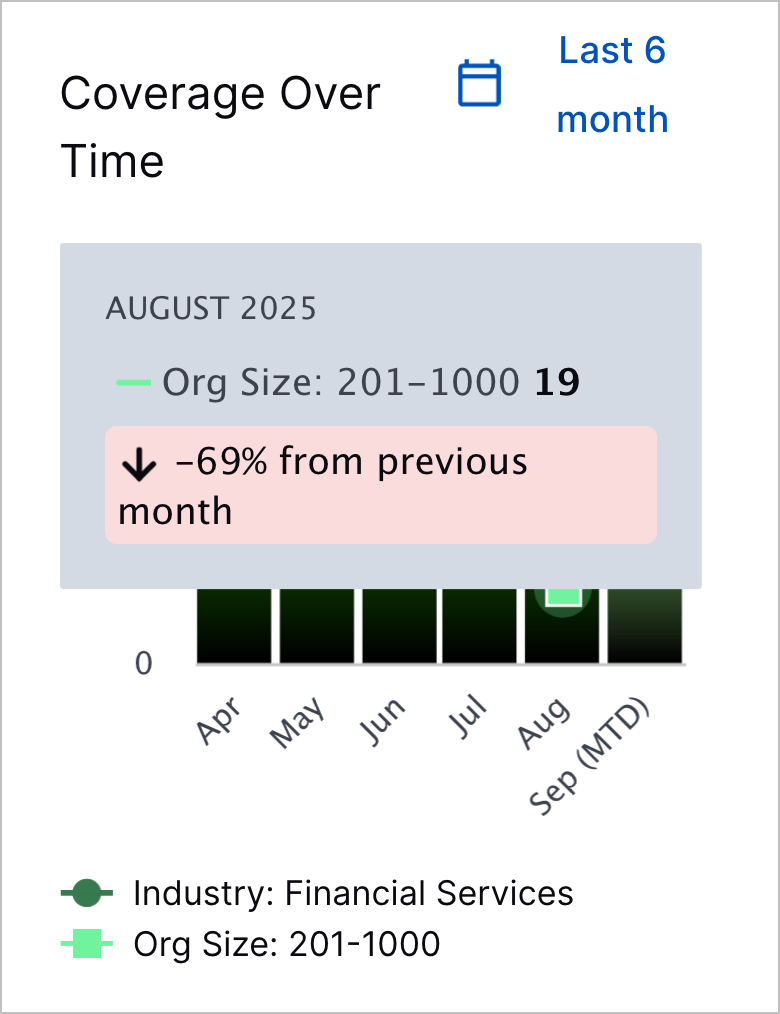
To view the relative change in the coverage score over the last month for organizations types you selected, hover over a point in the line chart: 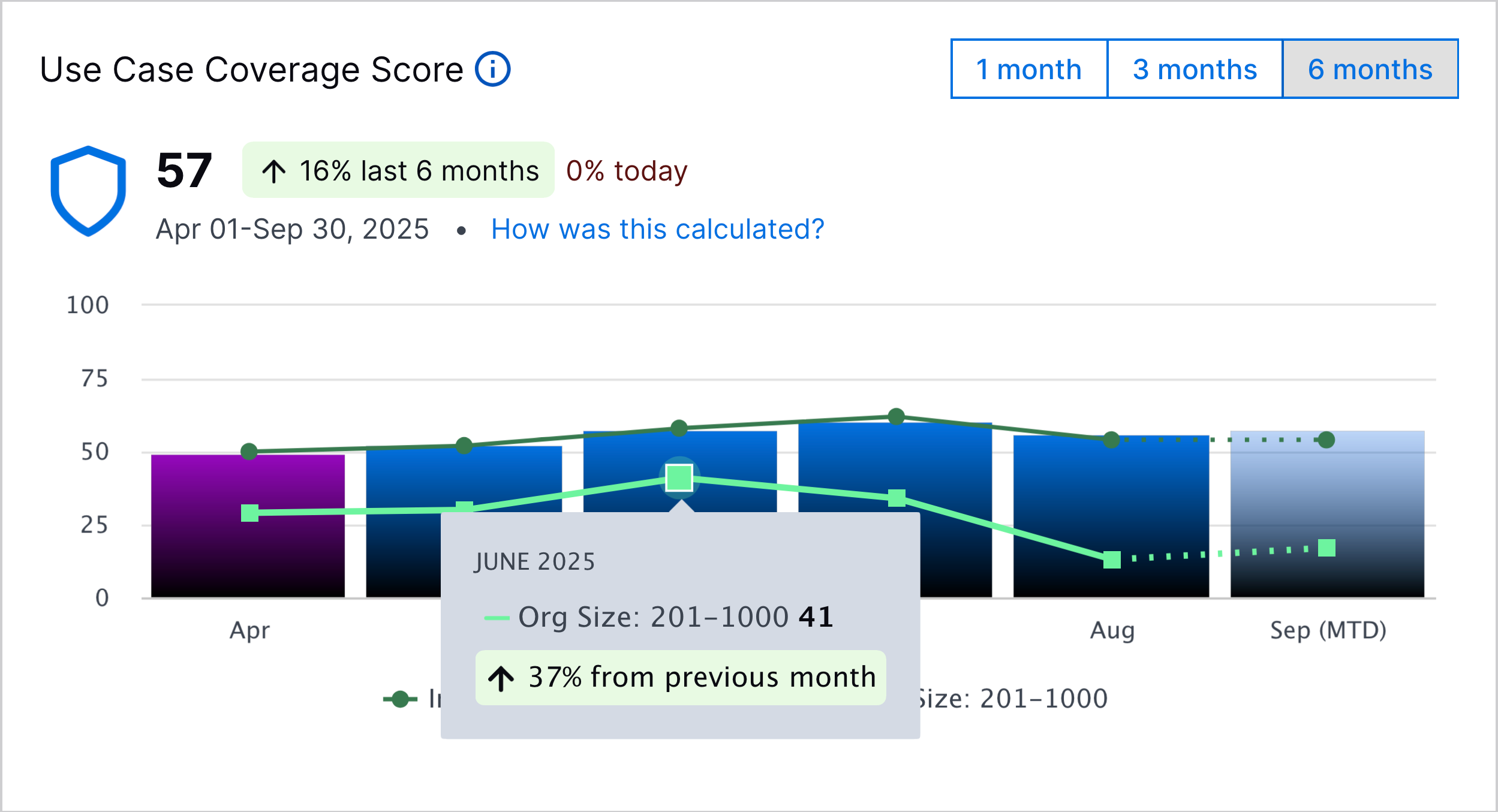
| ||||||||||||||||||||||||||||||||||||||||||||||||
[a] MITRE ATT&CK and ATT&CK are trademarks of The MITRE Corporation ("MITRE"). Exabeam is not affiliated with or sponsored or endorsed by MITRE. Nothing herein is a representation of the views or opinions of MITRE or its personnel. | |||||||||||||||||||||||||||||||||||||||||||||||||
Search
Feature | Description | |
|---|---|---|
Support for Sort Order in Exported Search Results | The sort order selector is now available when exporting search results. It includes options to sort chronologically to show the most recent or the oldest results. For more information, see Export Search Results in the Search Guide. | |
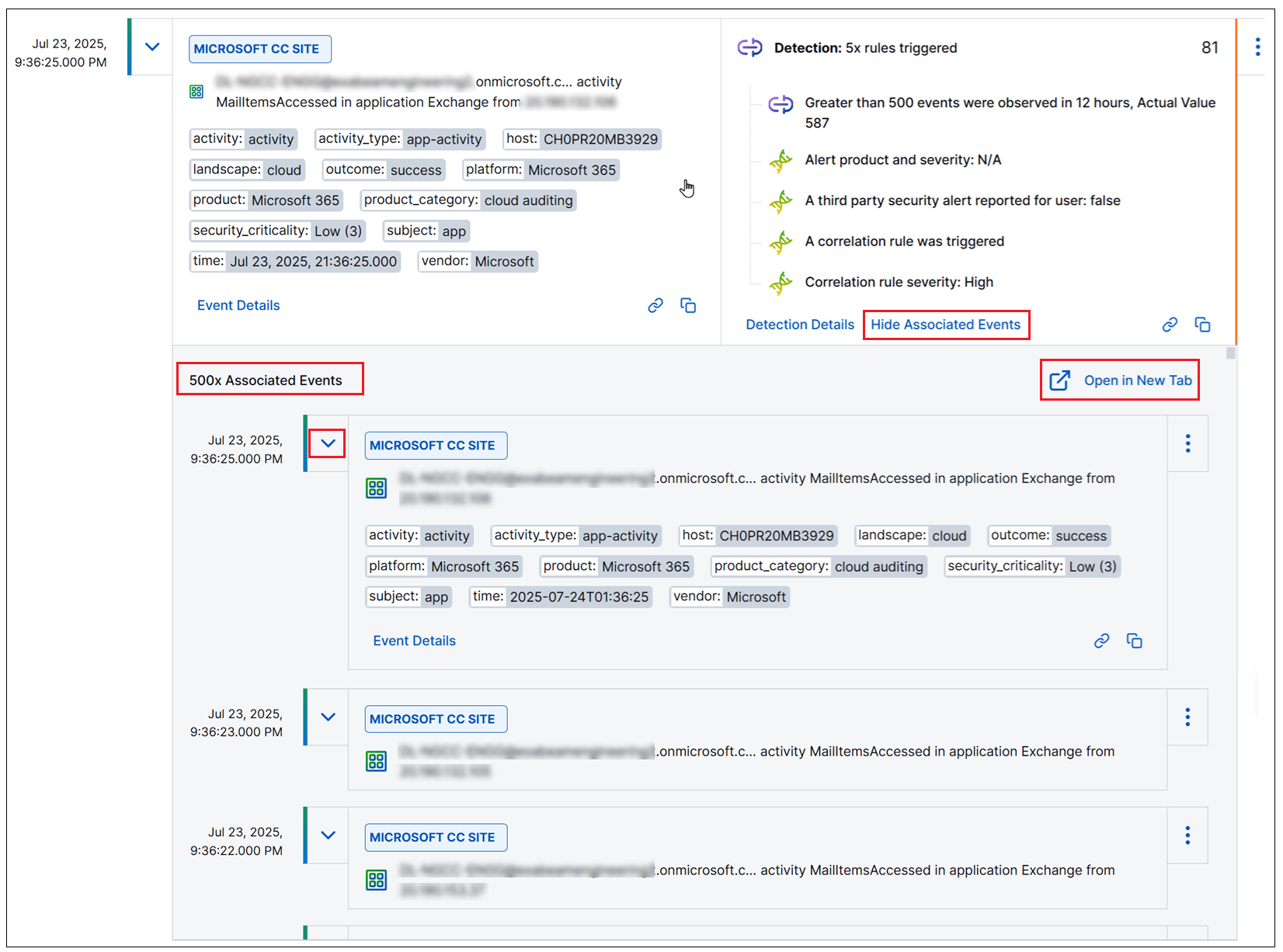
Associated Events for Detections in the Timeline View | Search has been updated to support the display of all events associated with a detection in the Timeline view. A detection event can be triggered by multiple events and, to keep the display of results in the Timeline view simple and uncluttered, the detection is shown only on the row of the latest chronological event that triggered it. Now, a new Show Associated Events option in the detection box lets you expand a full list of all the events associated with the detection. The list of associated events expands below the original event row and you can interact with the listed events in all the ways you can interact with other events. Alternately, you can opt to open the expanded set of associated events in a new Search tab.
For more information, see Detections in the Timeline in the Search Guide. |
Site Collectors 2.13
Feature | Description |
|---|---|
Upgradation to NiFi 2.5 | Based on the vulnerability remediation policy, the version of Apache NiFi is upgraded to the latest available version 2.5 for enhanced performance, security, stability, and integration capabilities. |
Enhanced Template Update Process | The updated templates now improve how agent collectors receive the latest changes, making the update process more reliable and efficient. The template types include: Windows, Windows File, Linux File, Archive Windows, and Archive Linux. To avoid errors and improve stability during bulk operations, limits on quantity and frequency of updates are added. This solution ensures smooth, time-distributed delivery of actions, prevents system overload, and maintains full control over throttling. |
Threat Center
Feature | Description |
|---|---|
Analytics Rules Severity | The ability of the Critical severity to automatically create a case was released on September 30, 2025 To manually tune Threat Center case or alert risk scores, you can now adjust the severity of analytics rules. 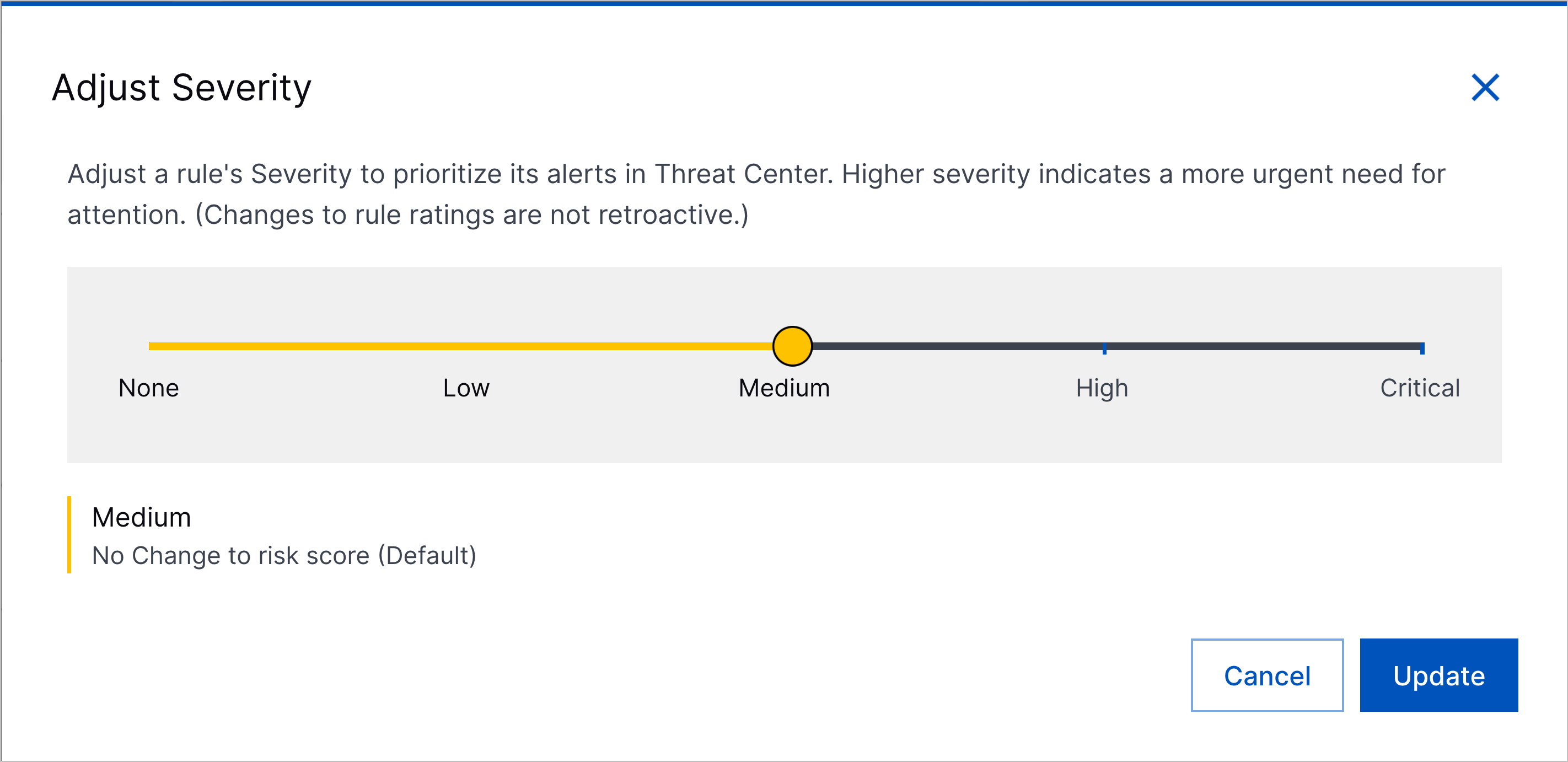 Analytics rule severity is now one of the business factors Threat Center uses when calculating a case or alert risk score. Each severity, from low to critical, has a corresponding weight that reduces or increases the risk score. The none severity doesn't affect risk scoring and can be used to test the analytics rule. When Threat Center calculates a risk score, it considers the highest severity of all analytics rule associated with detections grouped under the case or alert. You can assign an analytics rule the following severities:
Analytics rule severity doesn't affect risk scores for existing cases and alerts. To revise risk scores for existing cases and alerts, ensure that you re-train the analytics engine on past events. |
Standalone Case Creation from Correlation Rules | To quickly identify Threat Center cases created as the outcome of a correlation rule, you can now create a standalone case containing the correlation rule detection using a detection grouping rule. Detection grouping rules can now group correlation rule detections into a case by the correlation rule group by field. For Threat Center to create standalones case for correlation rule detections, you must create a detection grouping rule with specific conditions and actions, and the detection grouping rule must be ordered first in the list of detection grouping rules.  |
Case Opened in New Tab | To keep the case or alert list easily accessible while working on cases or alerts, you can now right-click on a case or alert and open it in a new browser tab.  |
Increased Case Notes Character Limit | To ensure you can communicate everything you want to with case notes, you can now add up to 10,000 characters in a single note.  |
Increase Custom Case Closed Reason Character Limit | To ensure you can communicate everything you want to when entering a custom case closed reason, you can now add up to 10,000 characters in a custom case closed reason.  |
Increased Attachment Size Limit | To ensure you can attach important evidence to a case, you can now attach a file of up to 15 MB.  |
Threat Detection Management
Feature | Description |
|---|---|
Custom Analytics Rule Builder | You can now create a custom analytics rule directly in Threat Detection Management with a point-and-click interface. The guided experience walks you through each step so you can easily create and edit analytics rules. After you create a custom analytics rule, you can also edit and delete it. 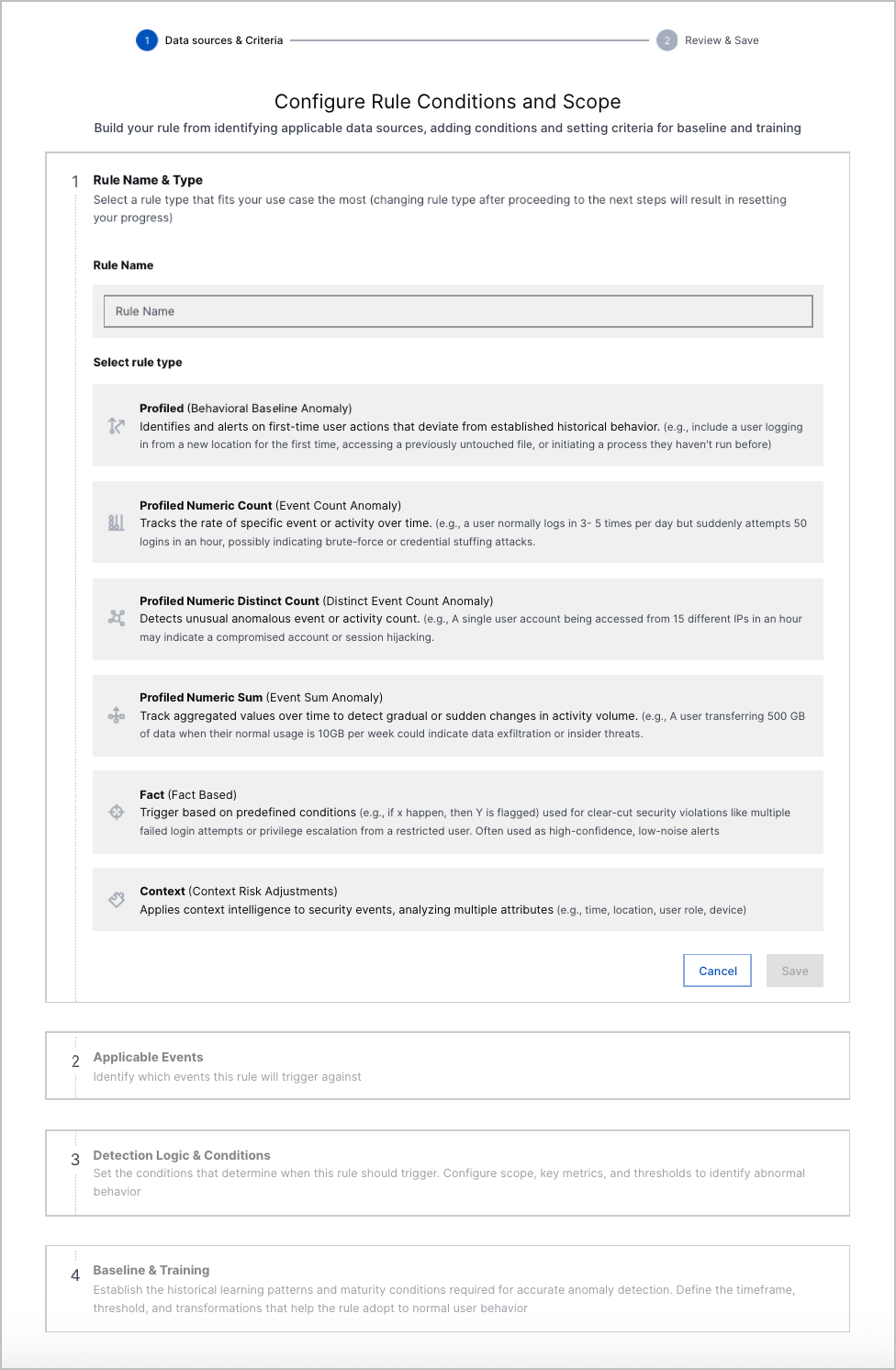 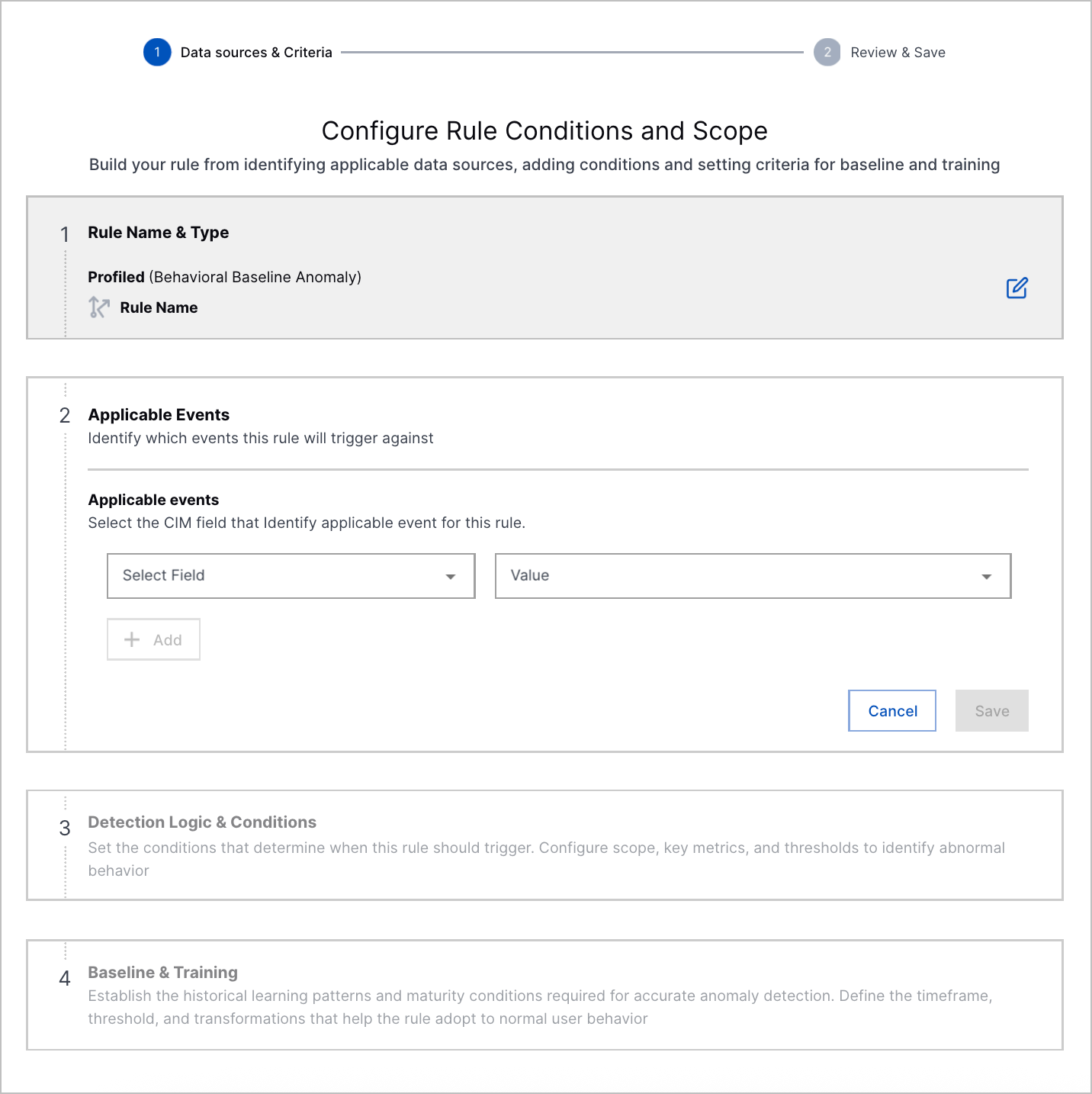 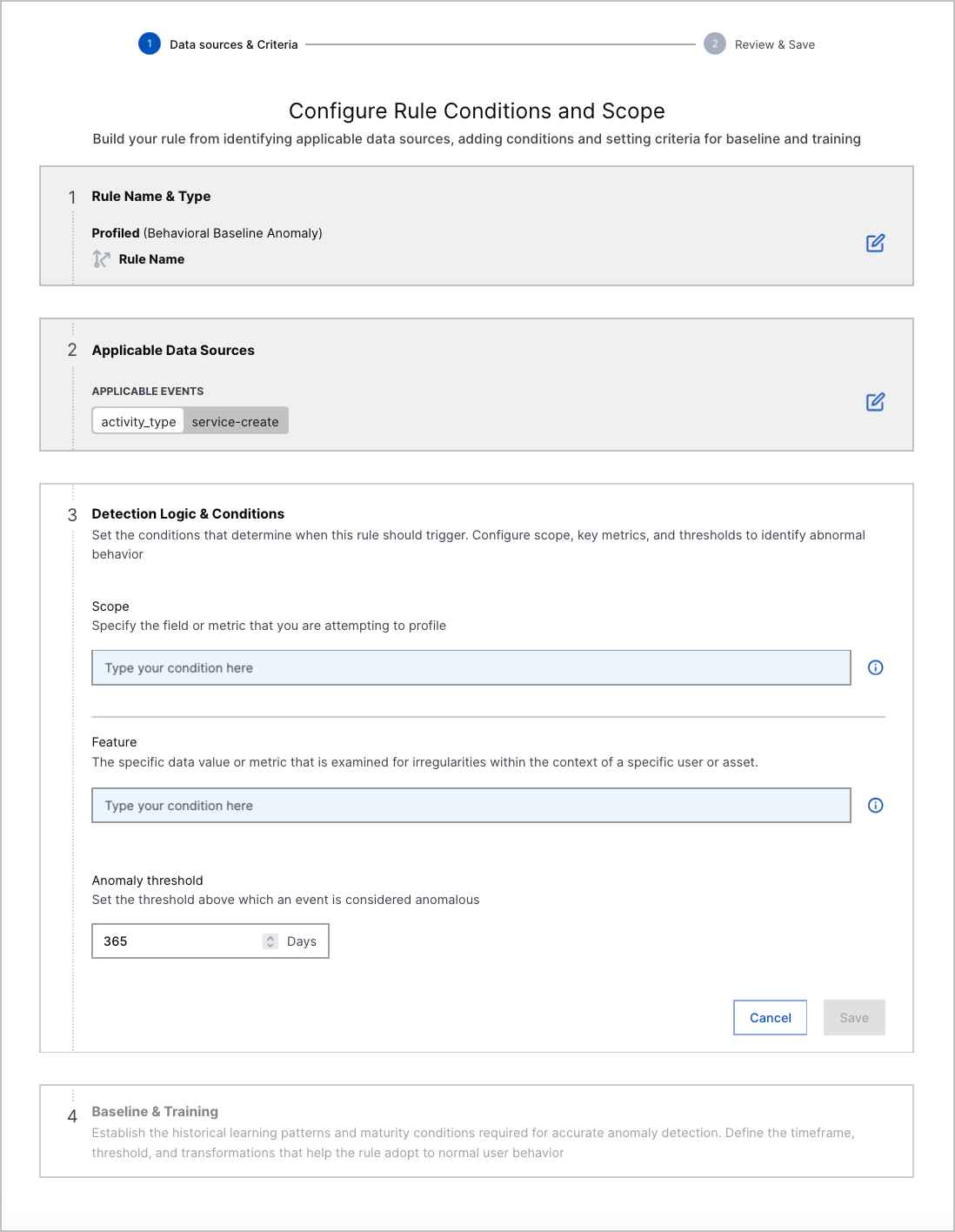 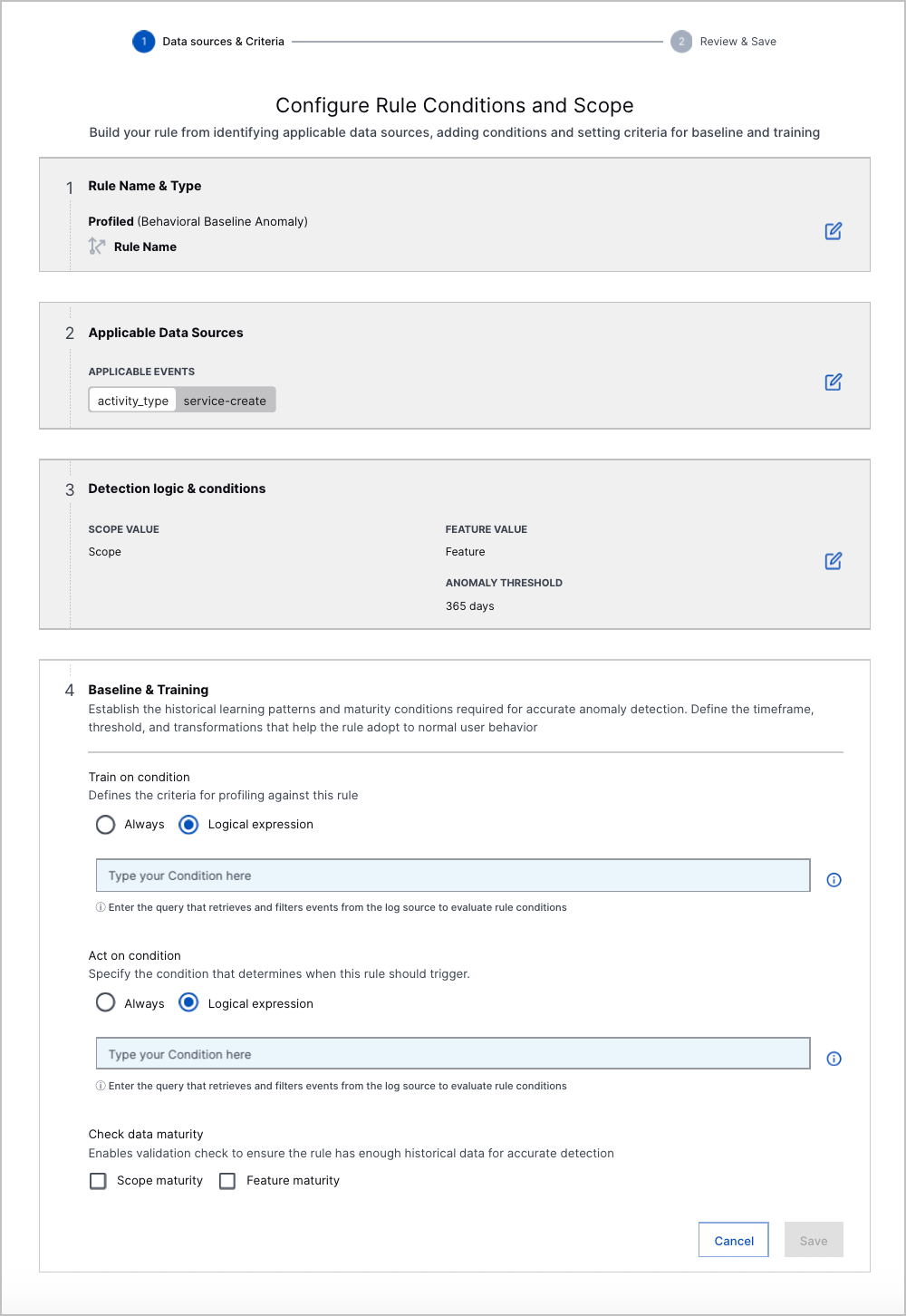 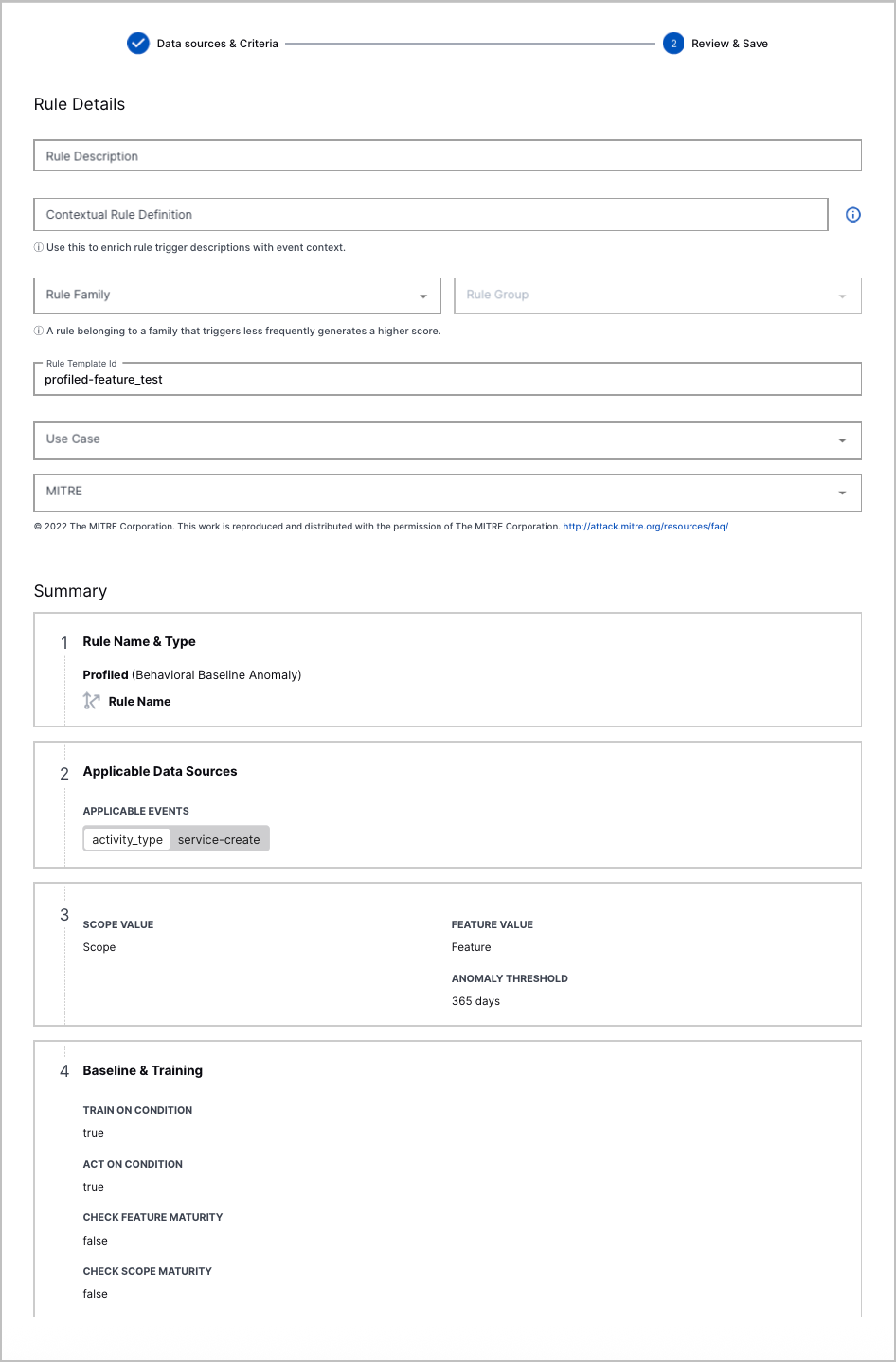 |
Analytics Rules Severity | The ability of the Critical severity to automatically create a case was released on September 30, 2025 To manually tune Threat Center case or alert risk scores, you can now adjust the severity of analytics rules.  Analytics rule severity is now one of the business factors Threat Center uses when calculating a case or alert risk score. Each severity, from low to critical, has a corresponding weight that reduces or increases the risk score. The none severity doesn't affect risk scoring and can be used to test the analytics rule. When Threat Center calculates a risk score, it considers the highest severity of all analytics rule associated with detections grouped under the case or alert. You can assign an analytics rule the following severities:
Analytics rule severity doesn't affect risk scores for existing cases and alerts. To revise risk scores for existing cases and alerts, ensure that you re-train the analytics engine on past events. When Exabeam delivers updates to pre-built analytics rules, the severity you assign to the pre-built analytics rule persists. |
Standalone Case Creation from Correlation Rules | To quickly identify Threat Center cases created as the outcome of a correlation rule, you can now create a standalone case containing the correlation rule detection using a detection grouping rule. Detection grouping rules can now group correlation rule detections into a case by the correlation rule group by field. For Threat Center to create standalones case for correlation rule detections, you must create a detection grouping rule with specific conditions and actions, and the detection grouping rule must be ordered first in the list of detection grouping rules.  |
New and Updated Pre-Built Analytics Rules | You can now better detect lateral movement, privilege escalation, suspicious command execution, unauthorized access, and data exfiltration with new pre-built analytics rules:
Removed obsolete pre-built analytics rules include:
|
New and Updated Correlation Rule Templates | You can now better detect suspicious logins, exploitation of the Log4Shell vulnerability, suspicious use of system utilities, data exfiltration, firewall tampering, and common web application attacks with new correlation rule templates:
Removed obsolete correlation rule templates include:
Fields have been modified in an additional 189 correlation rule templates. |
Analytics Engine Custom Fields Support | To tailor detection logic to specific use cases, the analytics engine can now evaluate and trigger on custom event fields. You can now use custom event fields in analytics rule expressions. |
Automated Sigma Rule Conversion | You can now easily convert Sigma rules to Exabeam analytics rules with Uncoder.io, a free, open-source marketplace for detection and investigation engineering. Uncoder.io uses artificial intelligence to automate the conversion of any Sigma and third-party SIEM rule in its comprehensive library of threat hunting content into Exabeam analytics rules. |
Resolved Issues
Site Collector 2.13: Security Vulnerabilities Remediations
The Site Collectors 2.13 (September 2025) release includes remediated security vulnerabilities. For more information about Exabeam’s commitment to remediating vulnerabilities for Site Collector, see the Vulnerability Remediation Policy.
There are no open known CVEs in any container image (Nifi). Toolkit has been deprecated and is no longer in use hence no security vulnerabilities update is available for that.
The following table lists the CVEs remediated for the Nifi container and their severity.
Critical | High | Medium | Low |
|---|---|---|---|
Total: 0 | Total: 0 | Total: 8 | Total: 1 |
– | – |
|
|