- 2026 Release Notes
- 2025 Release Notes
- December 2025
- November 2025
- October 2025
- September 2025
- August 2025
- July 2025
- June 2025
- May 2025
- April 2025
- March 2025
- February 2025
- January 2025
- Known Issues
November 2025
The New-Scale Security Operations Platform includes the following addressed features and new features for November 2025.
Attack Surface Insights
Feature | Description |
|---|---|
Attack Surface Insights Rules for Entity Types | To simplify and better manage your Attack Surface Insight rules, rule management is now separated by entity type. You now manage rules for user entities on the Users tab and rules for device entities on the Devices tab. |
Pre-Built Attack Surface Insights Rule Security Criticality Editing | To better customize pre-built Attack Surface Insight rules, you can now edit the security criticality of a pre-built Attack Surface Insights Rule. |
Entity Details Organized By Source | To clarify from where attributes are derived, entity details are now organized by source. You can now view attributes derived from context tables under Context Data and attributes derived from events under Event Data. 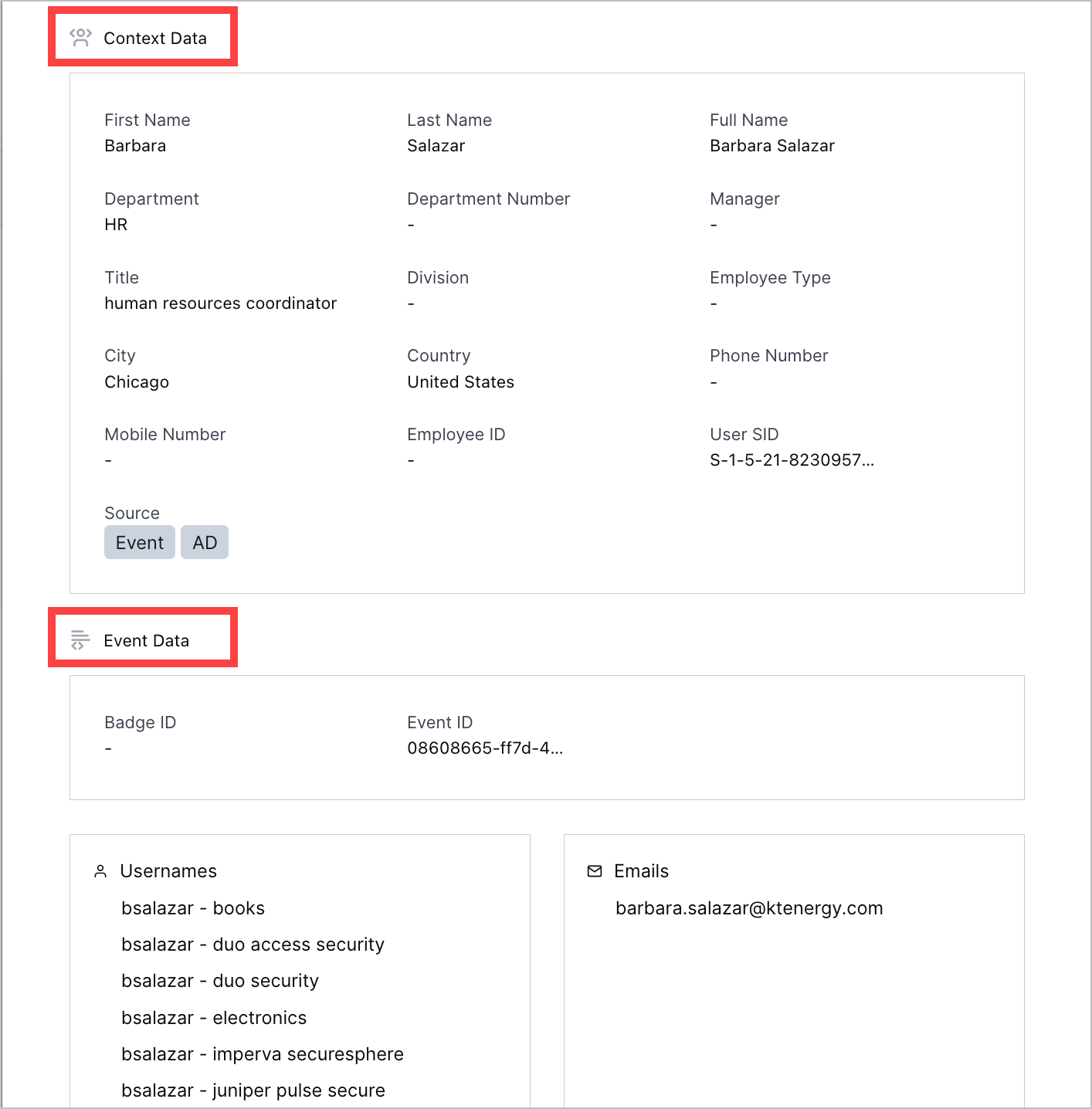 |
Default View Enhancement | To help you get started searching for entities, you can now view a list of example queries in the default view of the Users and Devices tabs. When you click on an example, the query automatically populates the search bar. 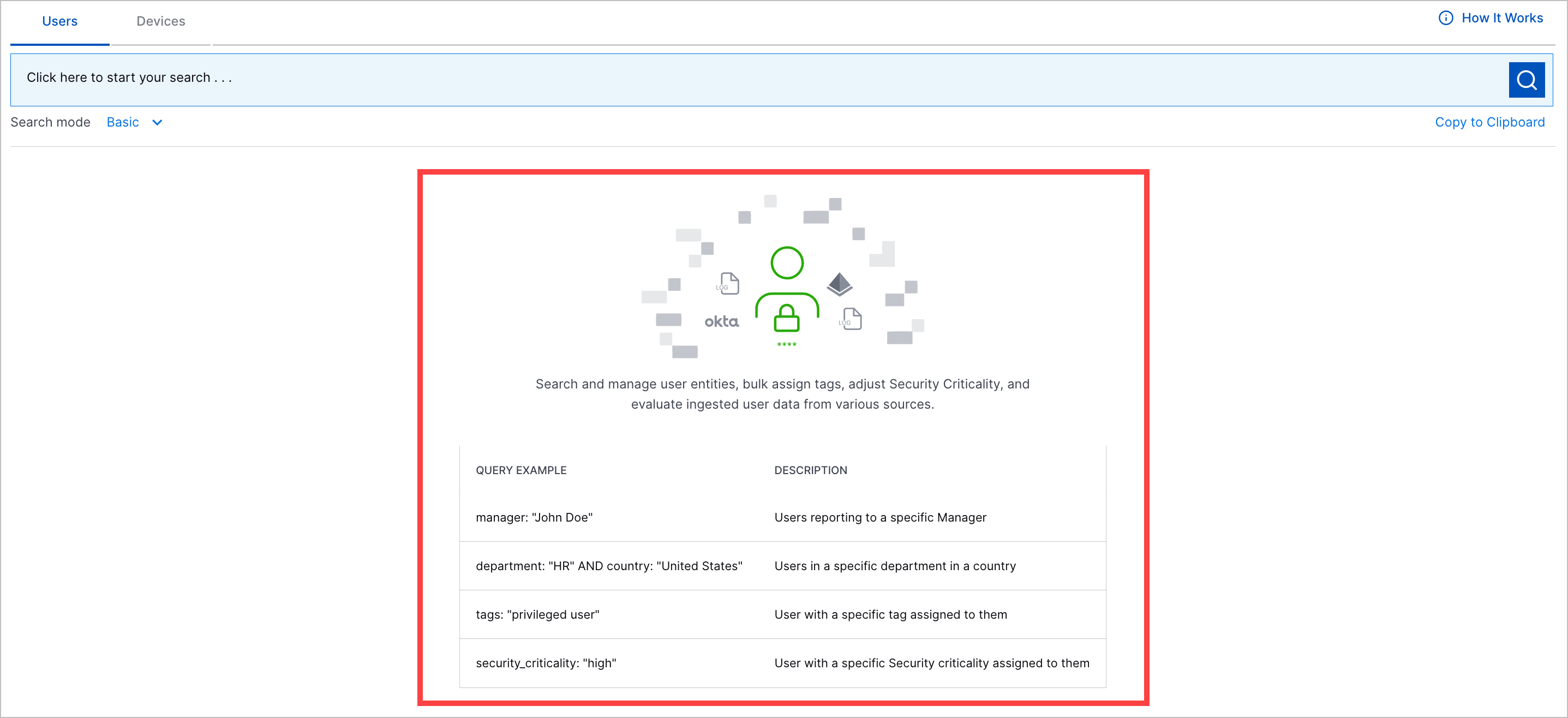 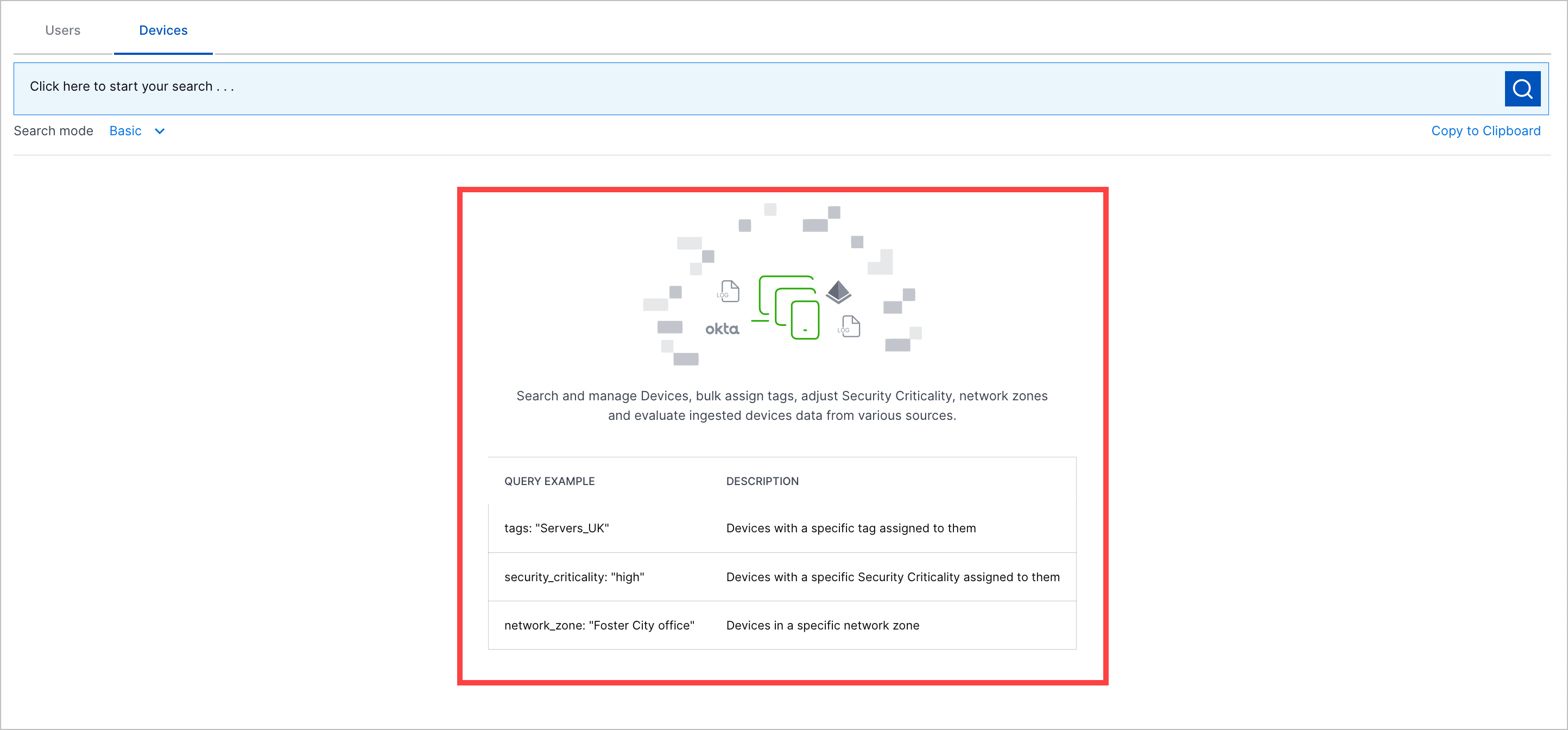 |
Security Criticality Tiers | To improve clarity and align with standard tier models, the values for security critical now include a corresponding tier number. The updated values are High (1), Medium (2), and Low (3). 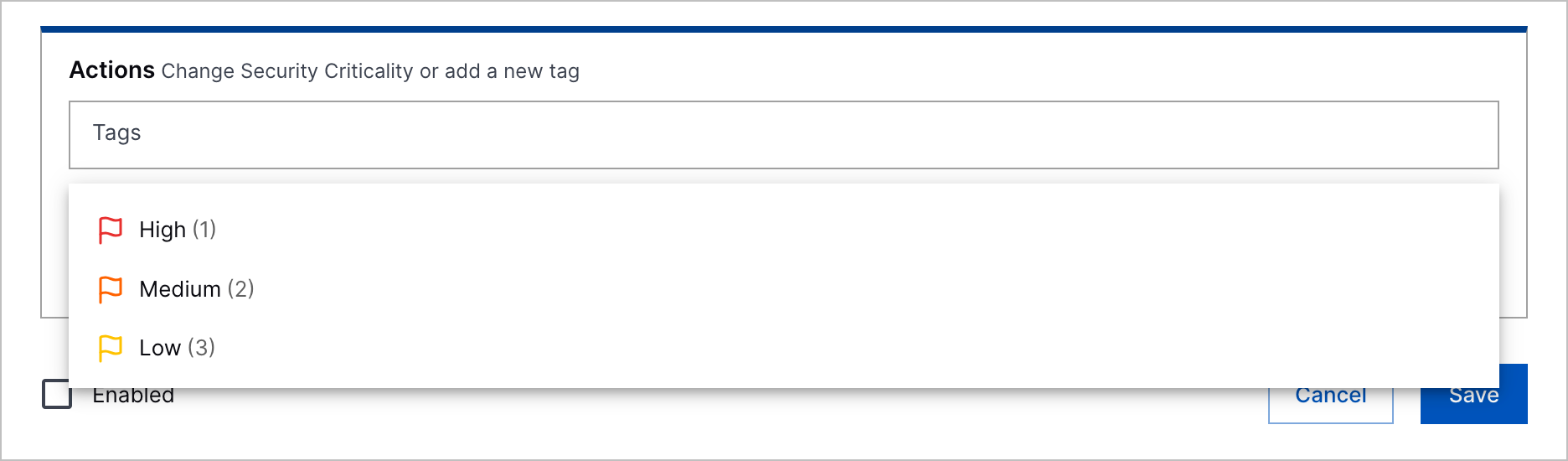 |
Automation Management
Feature | Description | |
|---|---|---|
Service and Action Deletion | To organize and maintain your automation tools, you can now delete custom services and actions. Before you delete a service or action, you must remove it from all existing playbooks. 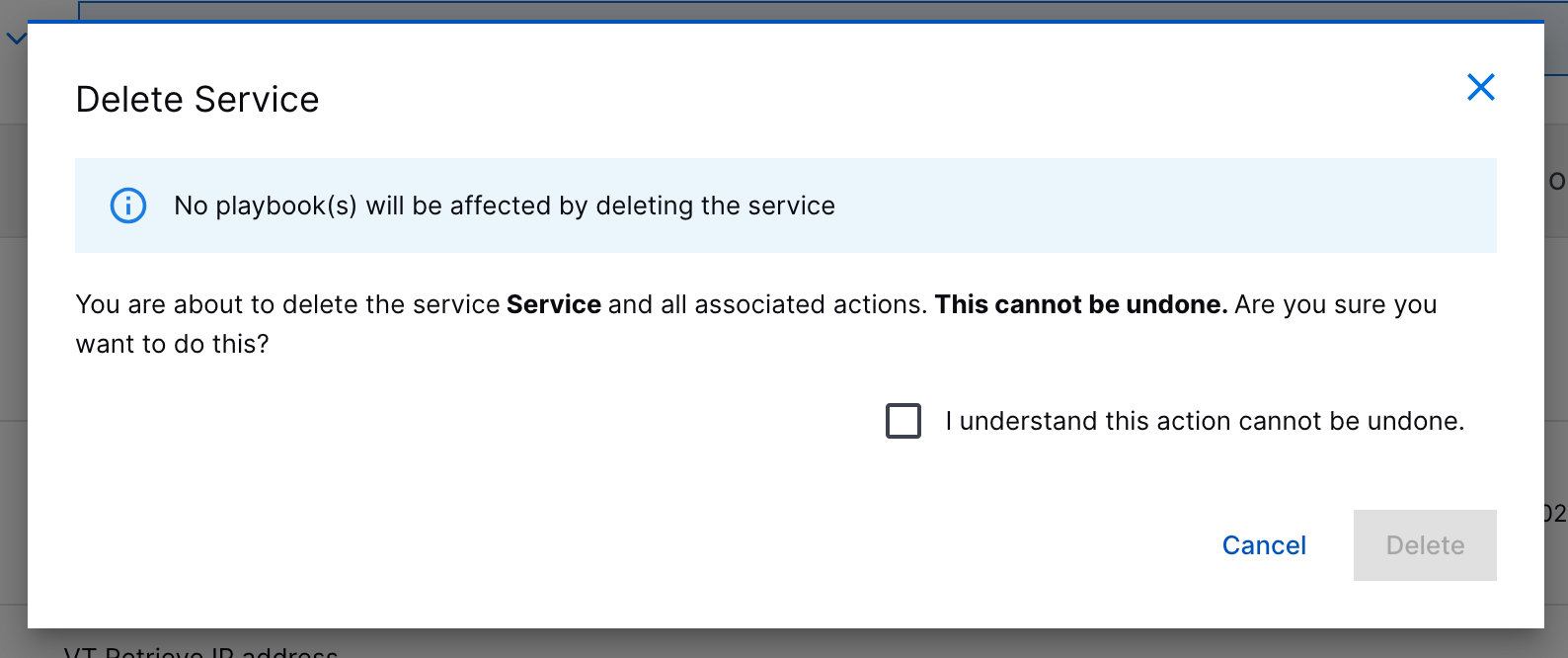 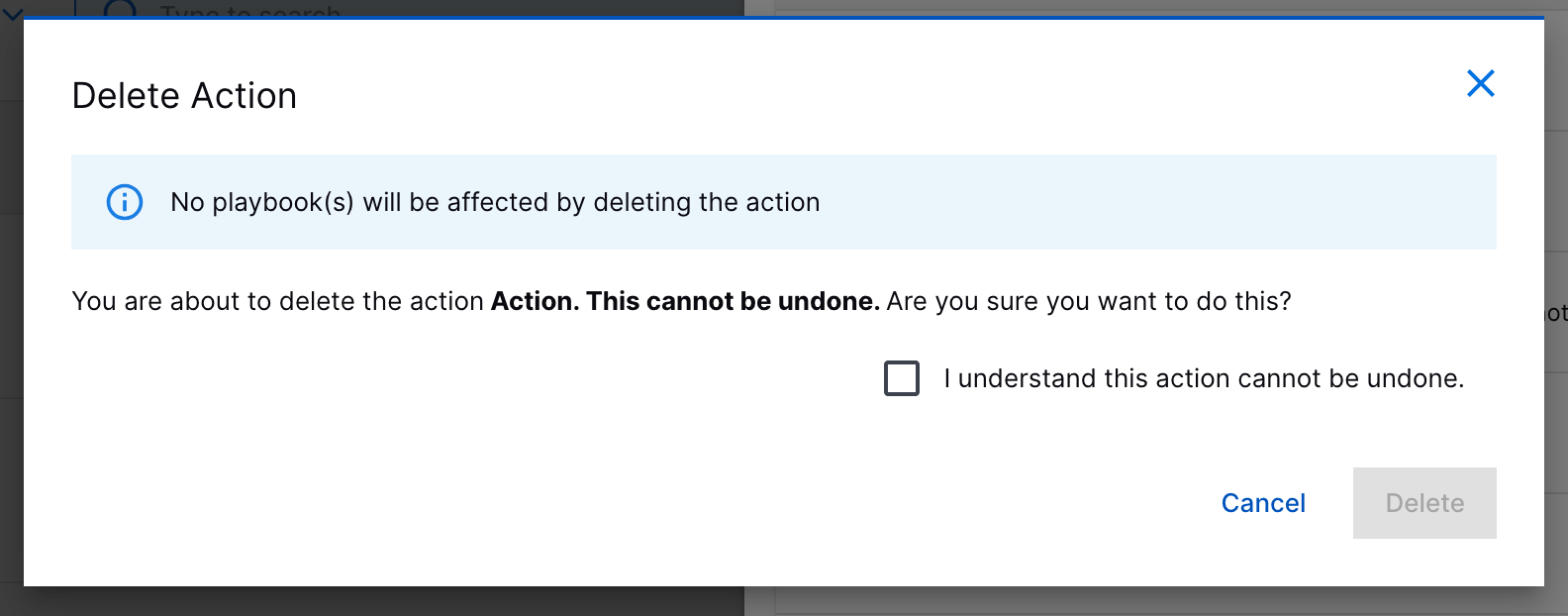 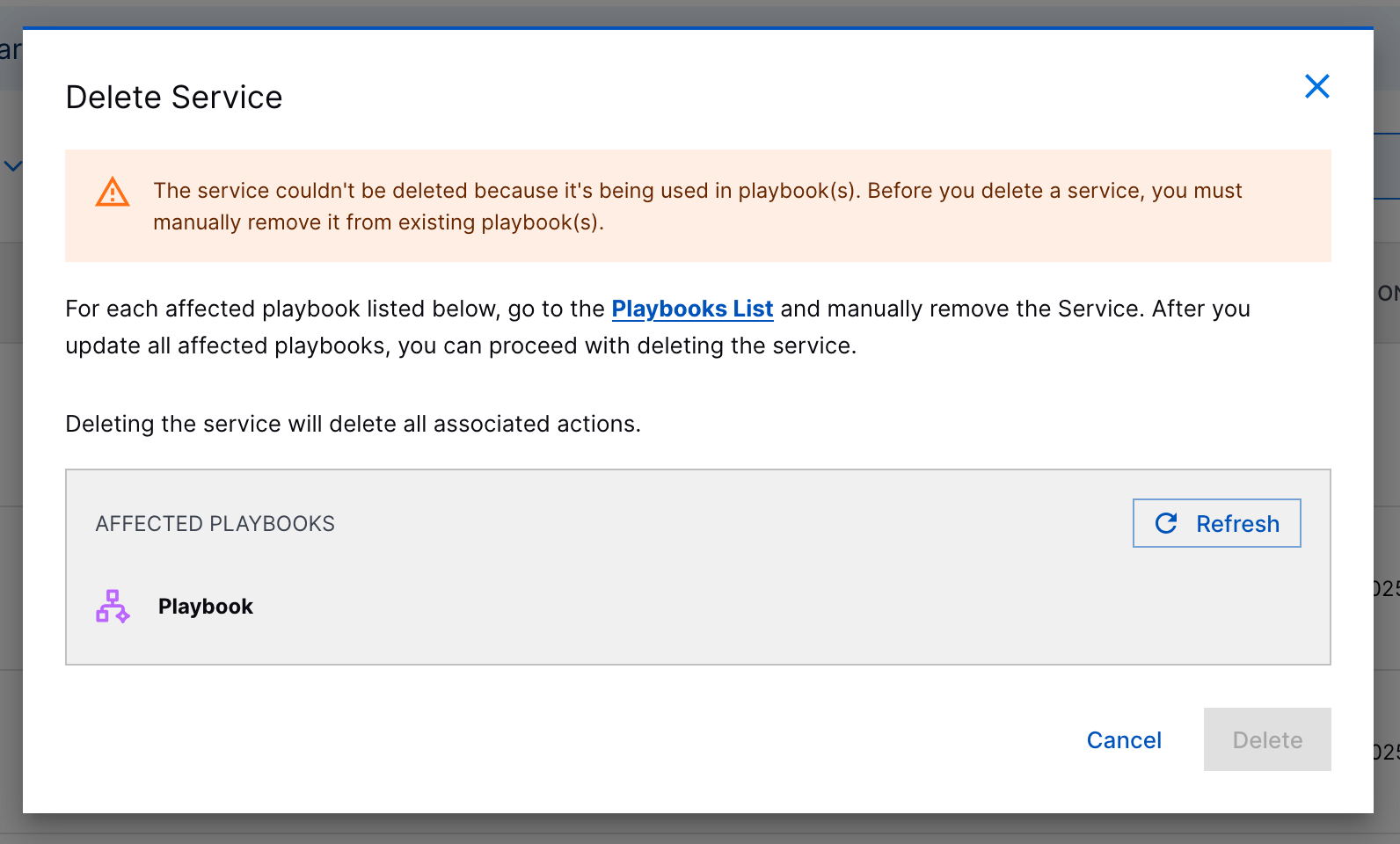 | |
Increased Playbook Name Character Limit | To allow you to create more detailed and descriptive playbook names, you can now enter up to 205 characters for the playbook name. 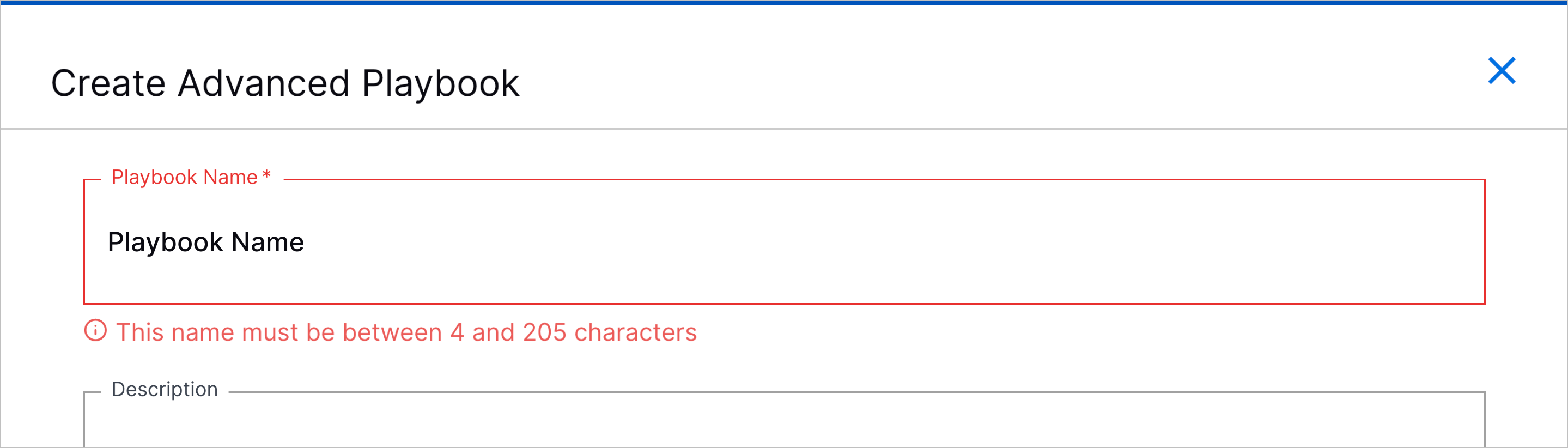 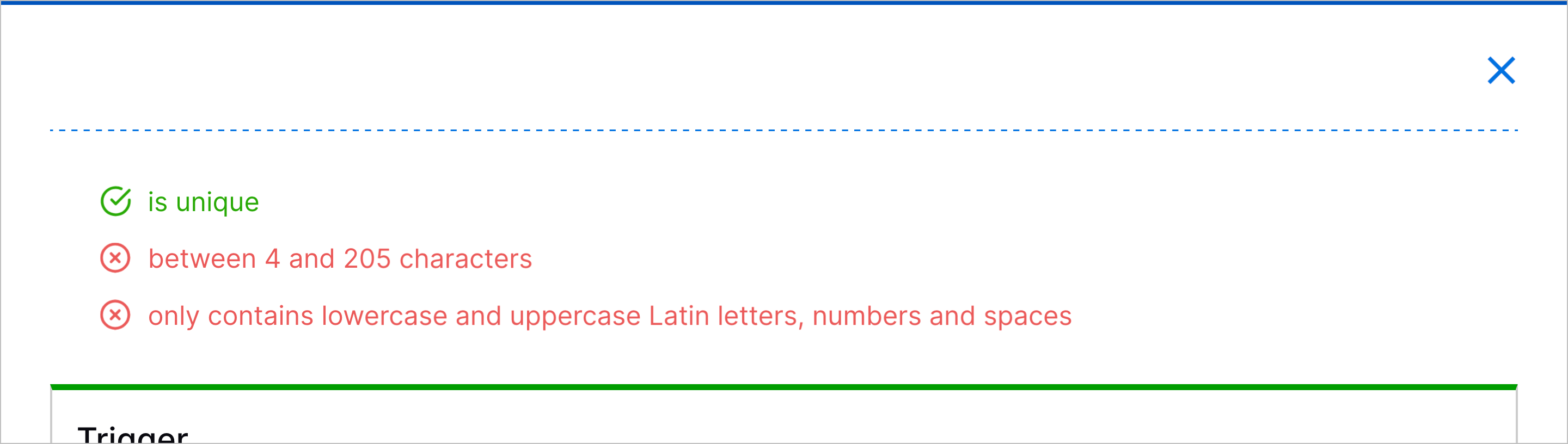 | |
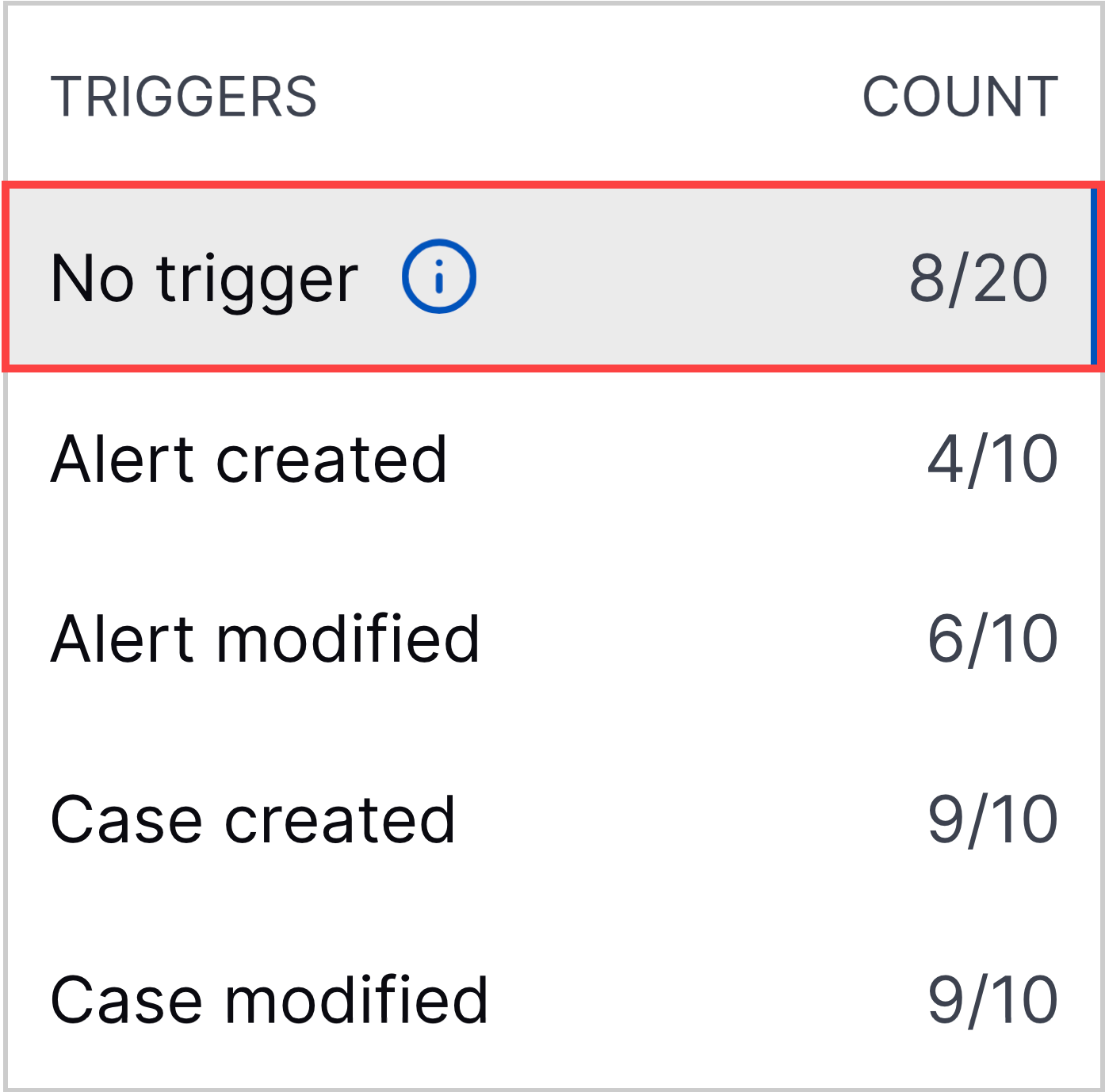
Increased No Trigger Playbook Creation Limit | To build a more comprehensive library of manual, on-demand playbooks, you can now create up to 20 advanced playbooks without a trigger.
| |
Service Created By Filter | To find a specific service, you can now filter services by creator. The searchthen applies only to those filtered results. 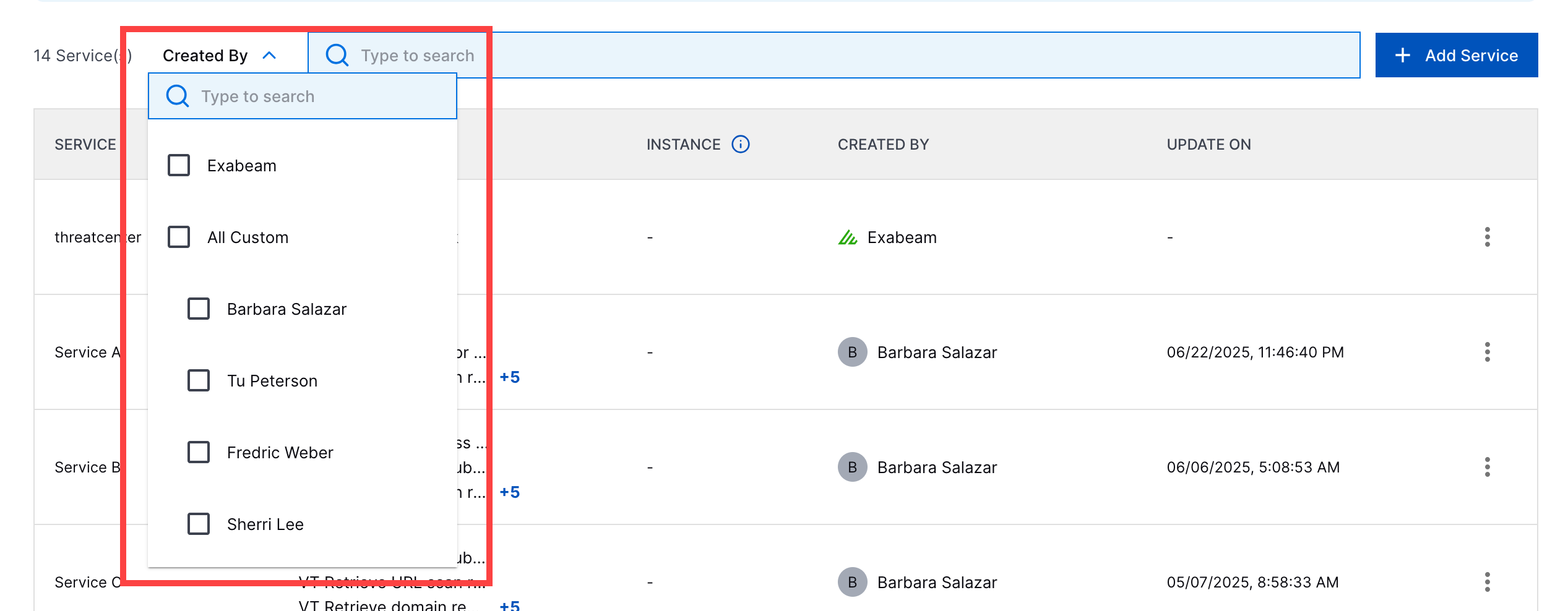 | |
Pre-Built Service Created By Enhancement | To better distinguish between pre-built and custom services, the Exabeam name and logo is now displayed under the CREATED BY column for pre-built services. 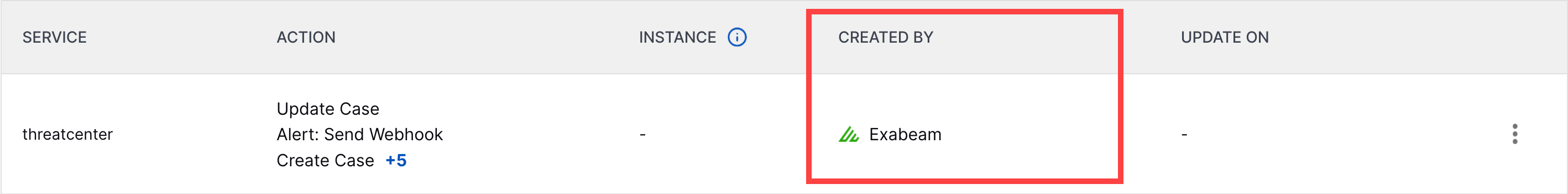 |
Cloud Collectors
Feature | Description |
|---|---|
Broadcom Carbon Black Cloud Collector | The Broadcom Carbon Black Cloud Collector is now available as part of Cloud Collectors, to facilitate ingestion of Alerts, Events, and Audit Logs from the storage bucket used by the data forwarder. |
Cylance Protect (now Arctic Wolf) Cloud Collector | The Cylance Protect (now Arctic Wolf) Cloud Collector is now available as part of Cloud Collectors, to facilitate ingestion of logs from the following data sources: Memory Protection, to collect threats related to memory vulnerabilities, Threats, to collect threat detection alerts and related information, or both. |
GitHub Cloud Collector | The GitHub Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of GitHub enterprise audit logs that include events such as repository access, authentication attempts, permission changes, and more from the GitHub Enterprise Audit API endpoint to monitor your enterprise GitHub server or cloud-based GitHub service. |
Early Access Collectors | |
Azure Blob Storage Cloud Collector | The Azure Blob Storage Cloud Collector is now available as part of Cloud Collectors Early Access program, to facilitate ingestion of the logs from Azure data sources such as threat detections, security alerts, and defender OTP logs. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Azure Virtual Network Flow Cloud Collector | The Azure Virtual Network Flow Cloud Collector is now available as part of Cloud Collectors Early Access program, to facilitate ingestion of the virtual network flow logs. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Palo Alto Networks XDR Cloud Collector | The Palo Alto Networks XDR Cloud Collector is now available as part of Cloud Collectors early access program to facilitate ingestion of the security alerts logs generated by Cortex XDR. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Correlation Rules
Feature | Description |
|---|---|
Trigger Schedules | To address specific use cases and improve correlation rule accuracy, you can schedule correlation rules to trigger on specific days or during specific periods only. When you create or edit a correlation rule, you can schedule a correlation rule to trigger daily, weekly, monthly, or during a custom time period with specific start and end times. 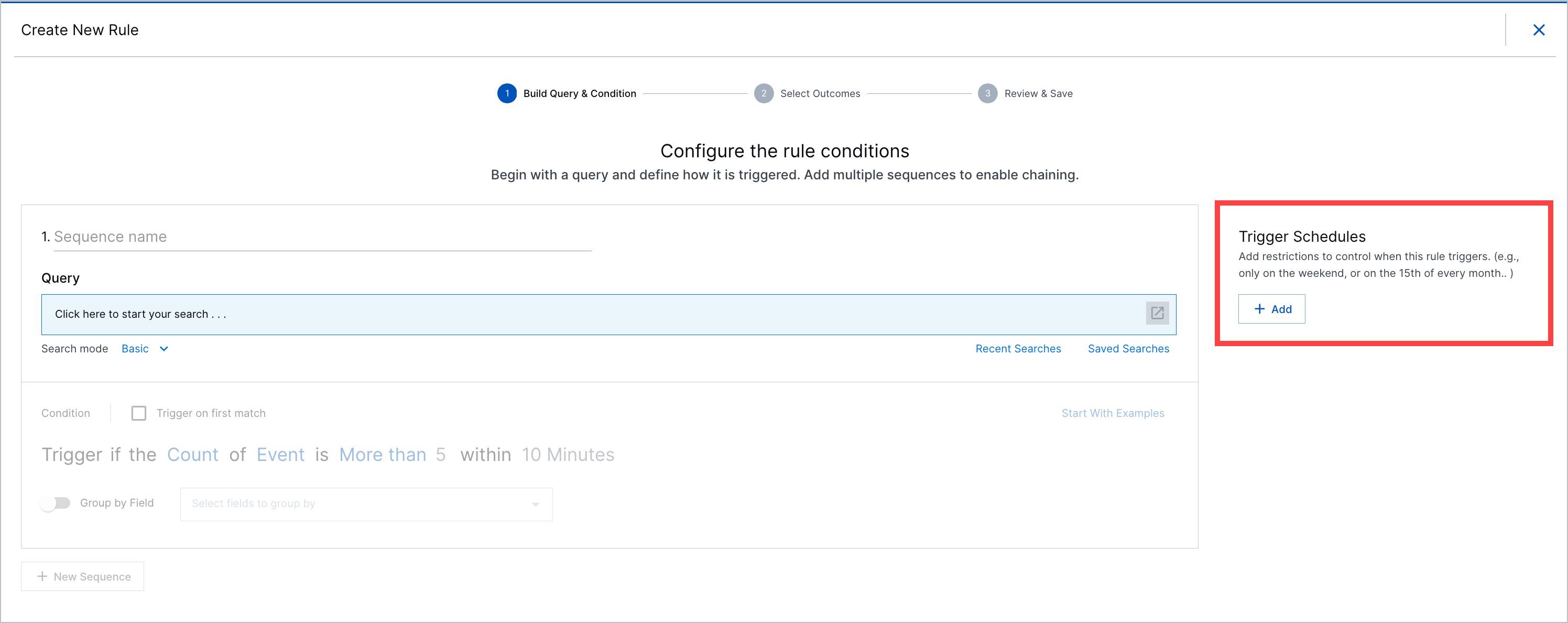 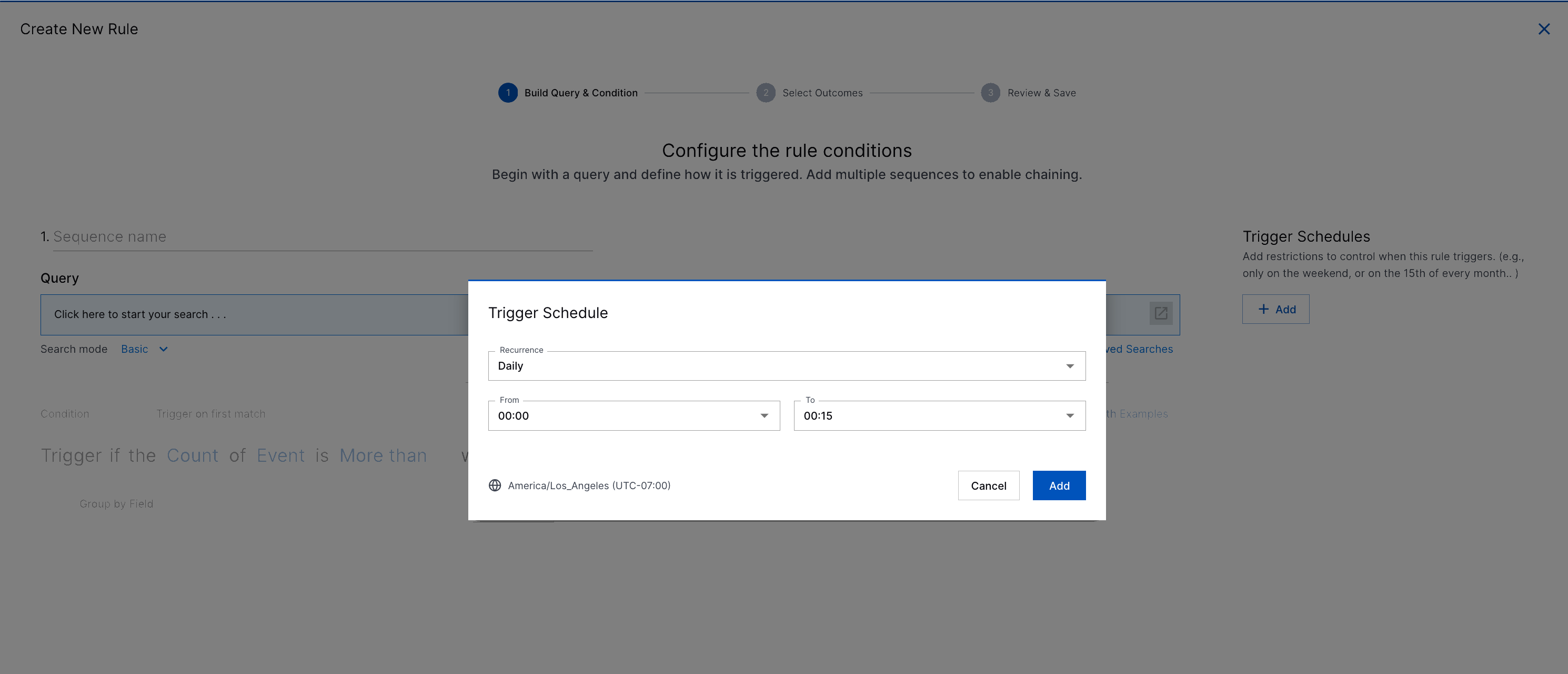 In the list of correlation rules, view the number of trigger schedules associated with the correlation rule under the SCHEDULES column. |
New Correlation Rule Templates | You can now better detect adversary reconnaissance techniques with new correlation rule templates:
|
Dashboards
Feature | Description |
|---|---|
Auto-Creating an Anomaly Fields Visualization from a Natural Language Prompt | As part of Exabeam Nova and its set of AI-driven capabilities, the use of the natural language prompt for auto-creating a dashboard visualization has been expanded to an additional data model. You can now use the natural language prompt for the Anomaly Fields data model. This enhancement means that you can leverage the natural language prompt in the Dashboard application to describe, in plain language, the Anomaly Fields data you want to visualize. Based on this plain language prompt, the measures, dimensions, filters, and even the chart type can be configured automatically. NoteThis auto-create option is also currently available to create visualizations for the Event and Alerts data models. (You must be using Threat Center to access the Alerts data model.) If the automatically generated visualization does not produce the data you want to visualize, you can modify the visualization settings manually to produce exactly the desired results. For more information about auto-creating visualizations, see Auto-Create a Visualization from a Natural Language Prompt in the Dashboards Guide. |
Log Stream
Feature | Description |
|---|---|
Planned Removal of Custom Default Parsers | The Custom Default category of parsers will be discontinued in favor of a simpler, more streamlined approach to customizing default parsers. In January of 2026, Exabeam will begin, one region at a time, removing the custom default parsers from Log Stream. As these parsers are removed, the corresponding default parsers will become enabled. Exabeam will provide notifications in each region before beginning to remove the custom default parsers. The Custom Default category is a specific set of customized parsers that were migrated from legacy products. These parsers were originally created for use in your legacy product environments when a customization was needed. Once migrated to Log Stream, custom default parsers were treated like default parsers, except they were not updated by the regular Exabeam content packages. As a result, these parsers have become out-of-date and stale but continue to be enabled and active in Log Stream. Parsers in this category have higher priority ratings than their corresponding default parsers and cause the more up-to-date default parsers to be disabled. Discontinuing the Custom Default category will help resolve these issues and simplify the overall categorization of parsers. If you rely on any of the custom default parsers in your Log Stream environment and you want to retain the customizations they contain, you need to identify them and manually add the same customizations to the corresponding default parser. For more information about this change to parser customization, and for the steps necessary to retain customizations you rely on, see Parser Types in the Log Stream Guide. |
Filtering Live Tail by Source Collectors | The filtering capabilities in Live Tail have been enhanced with an additional option. In addition to being able to filter for all logs parsed by a specific parser, you can now opt to filter the Live Tail stream based on the source collector the logs are being ingested from. For more information about filtering the Live Tail stream, see View and Filter Data in the Live Tail section of the Log Stream Guide. |
New-Scale Platform
Feature | Description |
|---|---|
Multi-factor Authentication for Local Accounts | To reduce downtime in the event of SSO interruption, you can now require Multi-factor Authentication (MFA) for all local accounts.  To activate MFA, enable it on the Single Sign-On/MFA settings page. When enabled, local accounts will require registration of a MFA token on the next login and then to authenticate on each subsequent login using a compatible TOTP authenticator. Reset a token anytime through the Users settings page, which will force new MFA on a local account.  |
Improved Query Building for Secured Resources | The query building functionality available to define secured resources has been updated to include the improved capabilities already available in the Search application. These include the option to build queries using either Basic or Advanced search modes. The Basic mode allows you to select fields from pre-built options for fast, accurate query building. The Advanced mode provides the flexibility to manually build a query and includes the following upgrades:
For more information, see Secured Resources in the New-Scale Security Operations Platform Administration Guide. |
Search
Feature | Description |
|---|---|
Improvements to the Timeline View of Search Results | The layout and functional behavior of the Timeline view of search results has been enhanced to both reduce visual noise and make the investigational workflow more intuitive. To better represent the sometimes confusing relationships between events and detections distinct Events and Detections columns have been labeled and the associations between events and detections in these columns have been clarified. For more information, see Timeline View of Search Results in the Search Guide. |
Site Collectors 2.15
Feature | Description |
|---|---|
Custom Installation Folder | Site Collector now creates a custom installation folder during the Site Collector installation process.
|
Enhancement for the Splunk Collector | Optimized performance for the Splunk collector for processing time-based conditions. |
Precheck Implementation | Implemented a precheck that verifies that only valid SSL certificate files are stored in the /opt/exabeam_prep/ssl folder, and no other files such as certificate bundles or non-certificate items are included. |
Threat Center
Feature | Description |
|---|---|
Webhook Payload Enhancements | You can now get more context for automation and better track events with enhanced webhook payloads. When case or alert information is sent to a webhook, the payload now includes key timestamps:
|
Threat Detection Management
Feature | Description |
|---|---|
Correlation Rule Trigger Schedules | To address specific use cases and improve correlation rule accuracy, you can schedule correlation rules to trigger on specific days or during specific periods only. When you create or edit a correlation rule, you can schedule a correlation rule to trigger daily, weekly, monthly, or during a custom time period with specific start and end times.   In the list of correlation rules, view the number of trigger schedules associated with the correlation rule under the SCHEDULES column. |
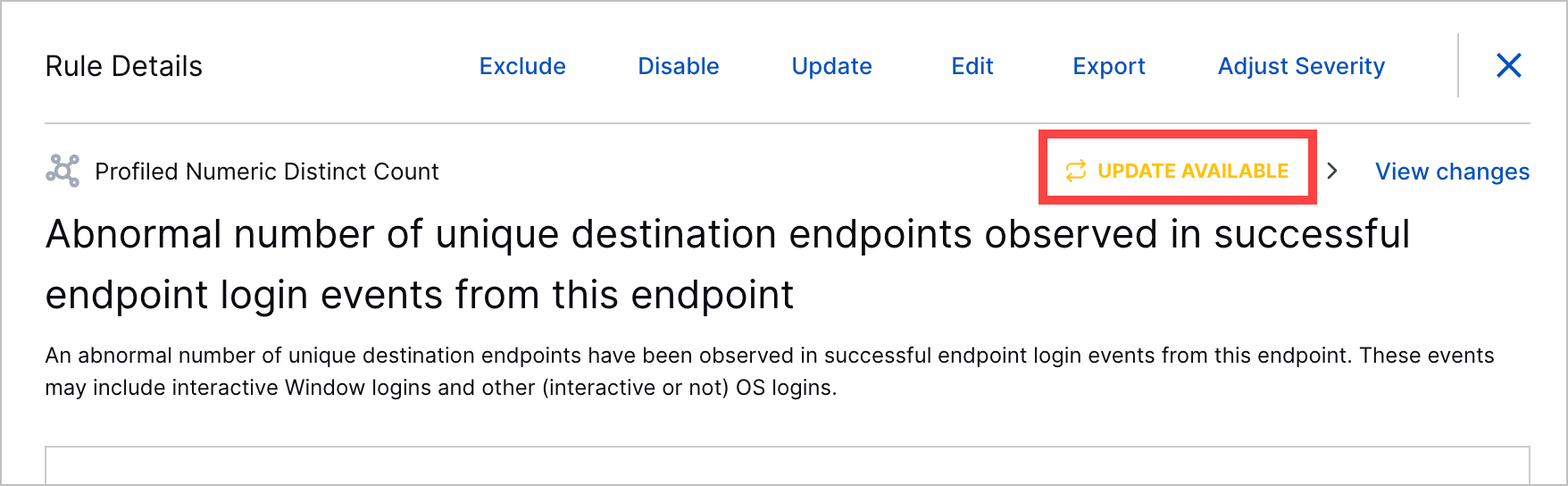
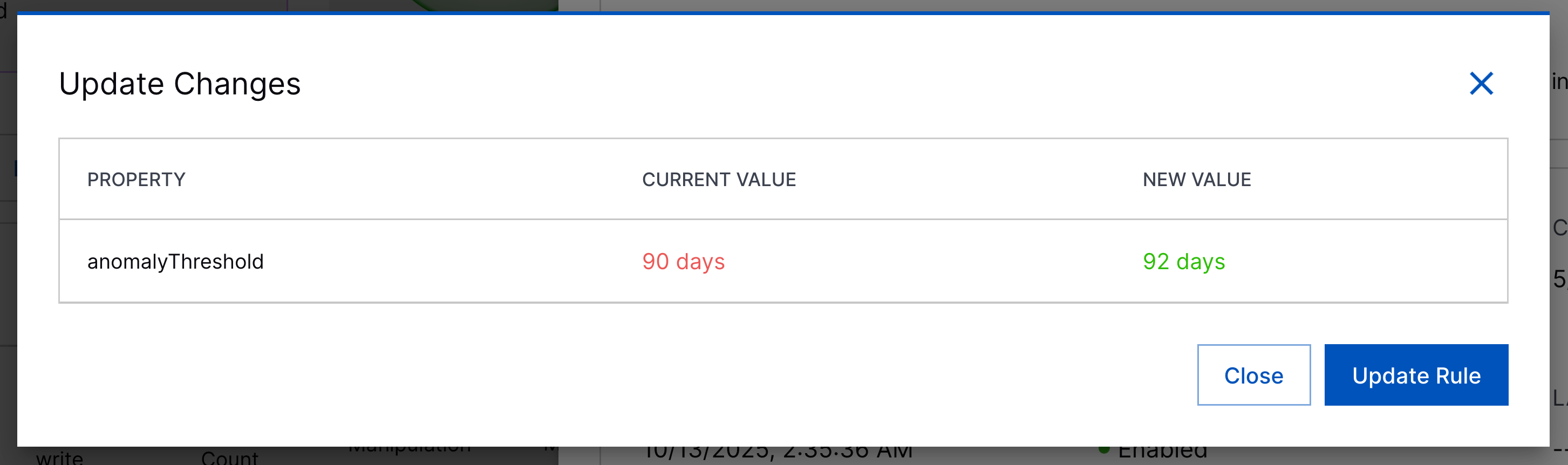
Pre-Built Analytics Rule Update Enhancement | In pre-built analytics rule details, you can now more quickly identify and understand what's changed with an analytics rule update:
|
Additional Analytics Rule Details Actions | To streamline rule management, you can now edit, export, and adjust severity from the analytics rule details. 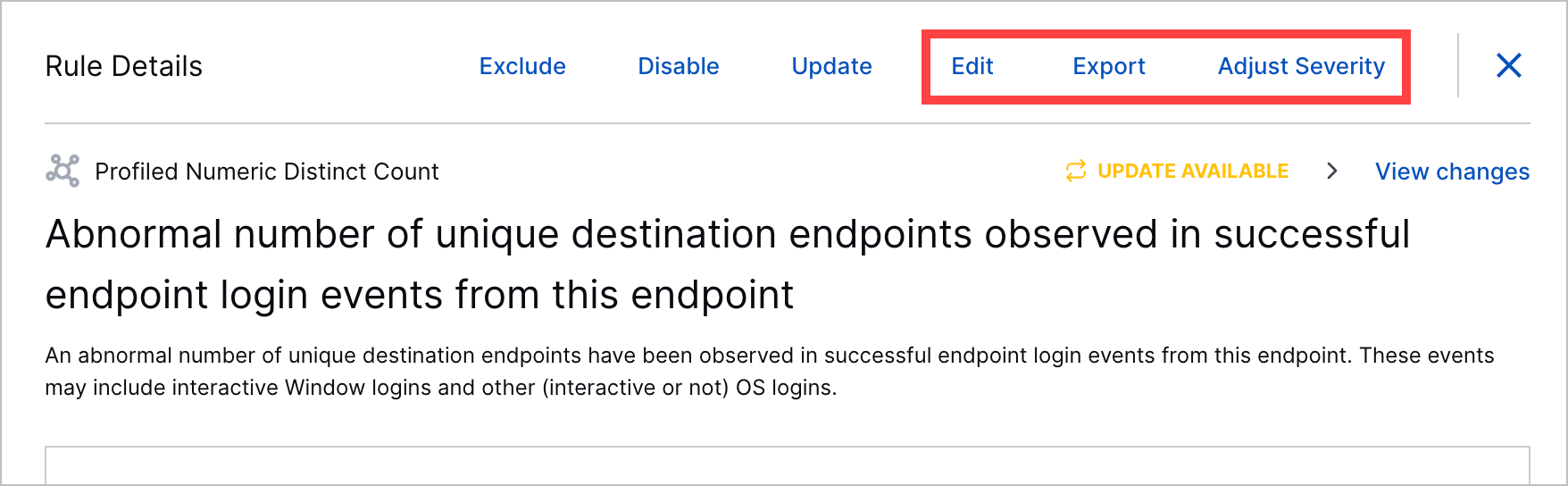 |
Analytics Rule Details Summary Enhancement | To make the configuration of an analytics rules easier to understand, you can now view its key components in a human-readable format under Summary in the analytics rule details. 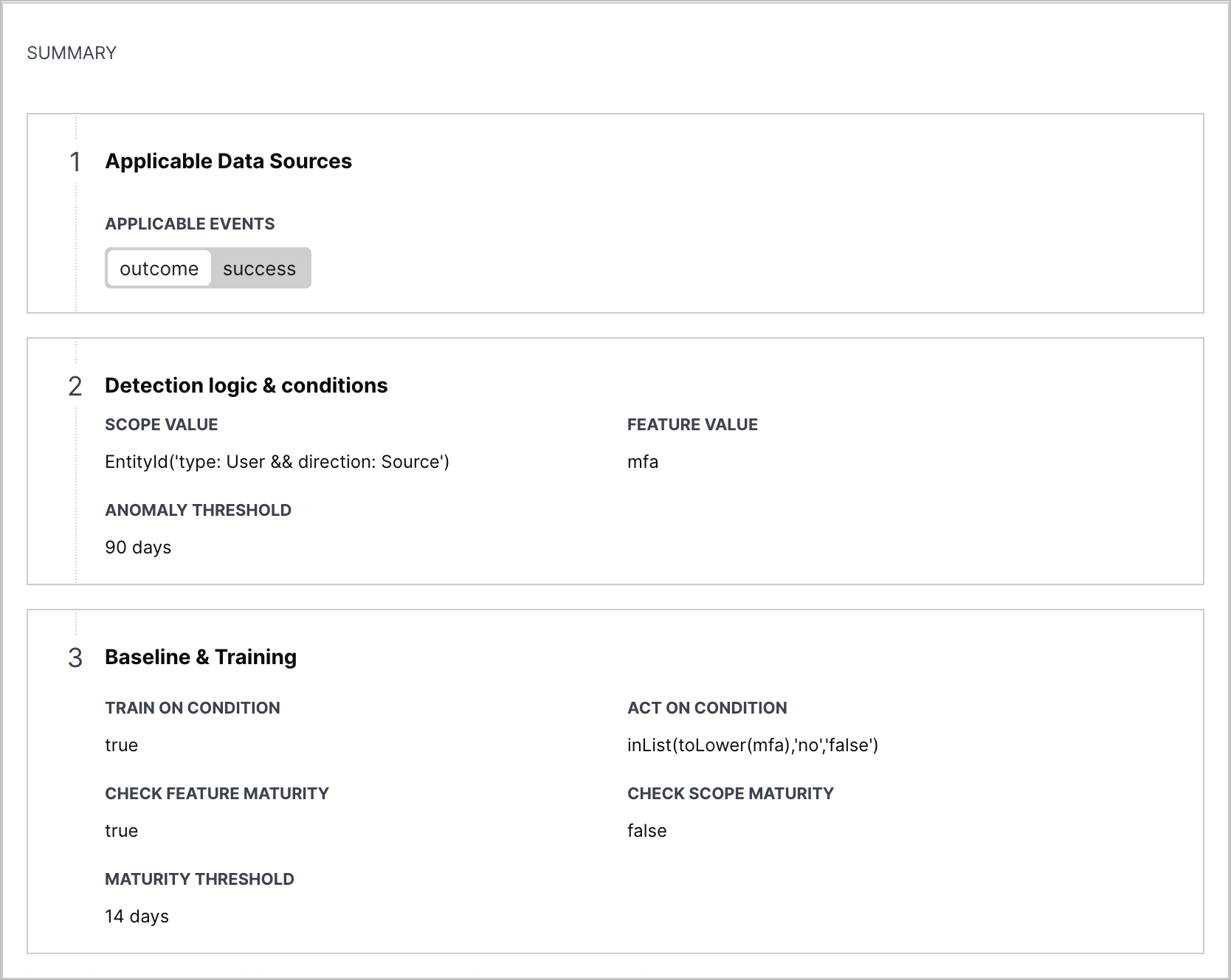 |
Analytics Rules Last Modified Column | You can now quickly identify and sort analytics rules by when they were last modified using the Last Modified column. 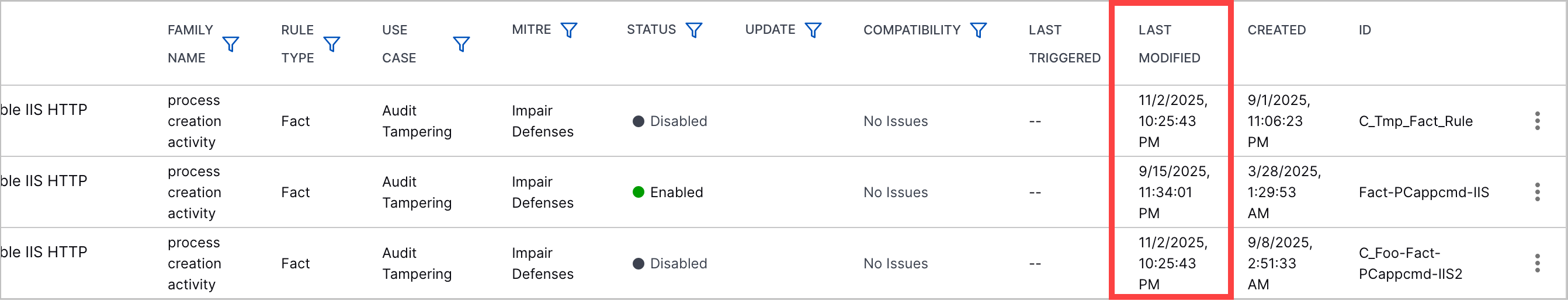 |
New and Updated Pre-Built Analytics Rules | You can now better detect adversary techniques, from initial reconnaissance and privilege escalation to defense evasion and data exfiltration, with new and updated analytics rules. New pre-built analytics rules include:
Pre-built analytics rules for which
Pre-built analytics rules for which
Pre-built analytics rules for which
Pre-built analytics rules for which
Pre-built analytics rules for which
Pre-built analytics rules for which
Pre-built analytics rules for which
Removed obsolete pre-built analytics rules include:
|
New Correlation Rule Templates | You can now better detect adversary reconnaissance techniques with new correlation rule templates:
|
Resolved Issues
Attack Surface Insights Resolved Issues
Issue ID | Description |
|---|---|
ENG-69014 | If you used a Windows operating system, country flags for user entities did not display correctly because the flag icons were based on an emoji library not supported by Windows. The flag rendering library has been updated, and country flags now display correctly. |
Search Resolved Issues
ID | Description |
|---|---|
ENG-79511 | Previously, when search results were exported, the |
Site Collector 2.15: Resolved Issues
Release Number | Description |
|---|---|
ENG-67509 | Fixed an issue in which the user interface incorrectly displayed an error—'certificate rotation failed'—meant to indicate an automatic certificate generation failure, even after the certificate is regenerated manually. After you manually regenerate the certificate using the ngsccli commands, the error— 'certificate rotation failed' automatically disappears after approximately 3 to 6 hours. |
Site Collector 2.15: Security Vulnerabilities Remediations
The Site Collectors 2.15 (November 2025) release includes remediated security vulnerabilities. For more information about Exabeam’s commitment to remediating vulnerabilities for Site Collector, see the Vulnerability Remediation Policy.
Known CVE - CVE-2025-11226
Toolkit has been deprecated and is no longer in use hence no security vulnerabilities update is available for that.
The following table lists the CVEs remediated for the Nifi container and their severity.
Critical | High | Medium | Low |
|---|---|---|---|
Total: 0 | Total: 0 | Total: 1 | Total: 0 |
– | – | CVE-2025-7425 | – |