- 2026 Release Notes
- 2025 Release Notes
- December 2025
- November 2025
- October 2025
- September 2025
- August 2025
- July 2025
- June 2025
- May 2025
- April 2025
- March 2025
- February 2025
- January 2025
- Known Issues
October 2025
The New-Scale Security Operations Platform includes the following addressed features and new features for October 2025.
Attack Surface Insights
Feature | Description |
|---|---|
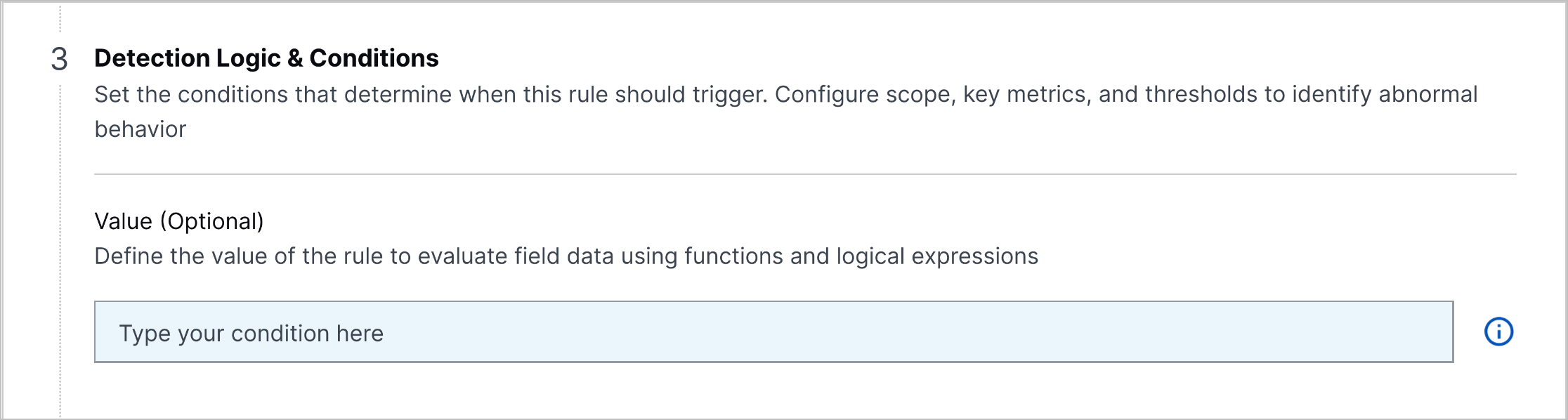
Device Entity Details IP Address Label Enhancement | This feature was released on November 4, 2025. To distinguish between static IP addresses from context and IP addresses from events, the IP address-related labels in device entity details are now updated for clarity. The IP Address field displays the static IP addresses defined in your context tables, while the IP Address History observed in events section displays the IP addresses observed in events.  |
Automation Management
Feature | Description |
|---|---|
Comments for Predefined Case Closed Reasons in Rule-Based Playbooks | To add more context to automated case closures, you can now include a custom comment with all predefined case closed reasons when the playbook action is Escalate to a case and and stage to is Closed. |
Cloud Collectors
Feature | Description |
|---|---|
Salesforce EventLog Cloud Collector | The Salesforce EventLog Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of various event types from Salesforce cloud. |
Snowflake Cloud Collector | The Snowflake Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of data from data sources Login History, Others, and Query History. |
Early Access Collectors | |
Broadcom Carbon Black Cloud Collector | The Broadcom Carbon Black Cloud Collector is now available as part of Cloud Collectors Early Access program, to facilitate ingestion of Alerts, Events, and Audit Logs from the storage bucket used by the data forwarder. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Support for Importing and Exporting Configuration Settings for the REST API Cloud Collector | The REST API Cloud Collector now supports importing and exporting configuration settings. You can import the configuration details in JSON format while configuring a new collector instance and export the configuration details in JOSN format to use it later for backup, replication, or integration. This functionality is available as part of Cloud Collectors Early Access program. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Log Stream
Feature | Description |
|---|---|
Host to IP Enrichment | Host to IP enrichment ensures that hostnames and IP addresses can be mapped to each other in order to enrich events with whichever of those fields is missing in the raw log. The system uses a dynamic host-IP mapping table to store those associations. Incoming logs are evaluated to determine if they meet the conditions necessary for host to IP enrichment. By default, host to IP enrichment takes place if the log includes one of a specific set of activity types. For more information about this type of enrichment, see Host to IP Enrichment in the Log Stream Guide. NoteEarly Access Opportunity An early access opportunity is available to customize the host to IP enrichment functionality. You may want to take advantage of this opportunity for either of the following reasons:
If you would like to take advantage of this early access customization, email the following group: [email protected]. |
New-Scale Platform
Feature | Description | |
|---|---|---|
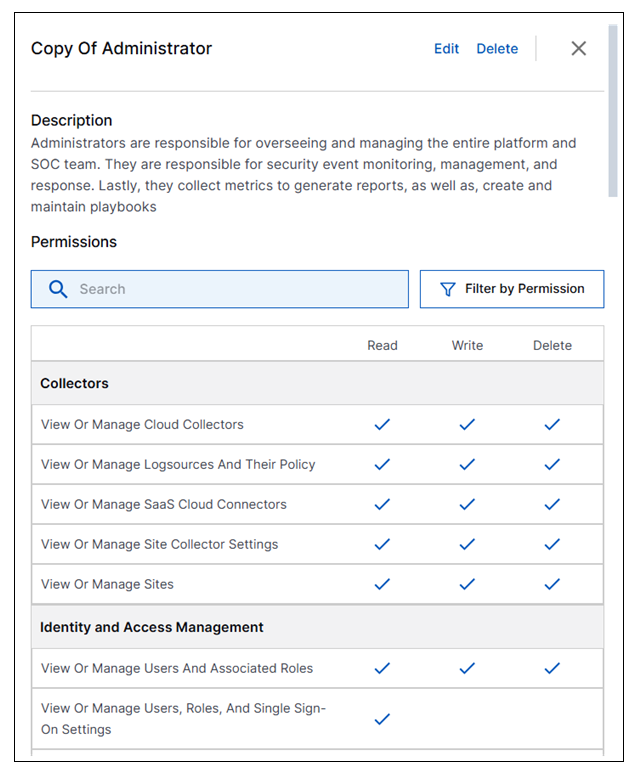
Improved Panel to View Permissions Assigned to a User Role | A new panel has been implemented to facilitate easier viewing of all the permissions assigned to a given user role in the New-Scale Security Operations Platform Settings. If the list of permissions is long, you can use the Search field to quickly locate a specific permission. Alternately, you can filter the list by types of permissions. For custom user roles, Edit and Delete options are conveniently available from the permissions panel. You can use them to edit or delete the existing custom role. For more information, see View Permissions in a User Role.
| |
Duplicate Roles | To aid in faster role creation, you can now duplicate an existing role and modify it to make it easier to create new roles.  | |
UI and API Restriction by IP | A new IP-Based Access page has been added to the New-Scale Security Operations Platform Settings. On the new page, you can manage UI and public API access to New-Scale functionality on the basis of IP addresses. You can add new IP addresses, either individually or in ranges, to create an allowed list of access and restrictions. You can also edit access for IP addresses already on the list or delete IP addresses from the list. For more information, see Manage Access by IP Addresses. |
Outcomes Navigator
Feature | Description |
|---|---|
Unsupported Status for | To improve the accuracy of coverage calculations, Advanced Analytics whose rule expressions include 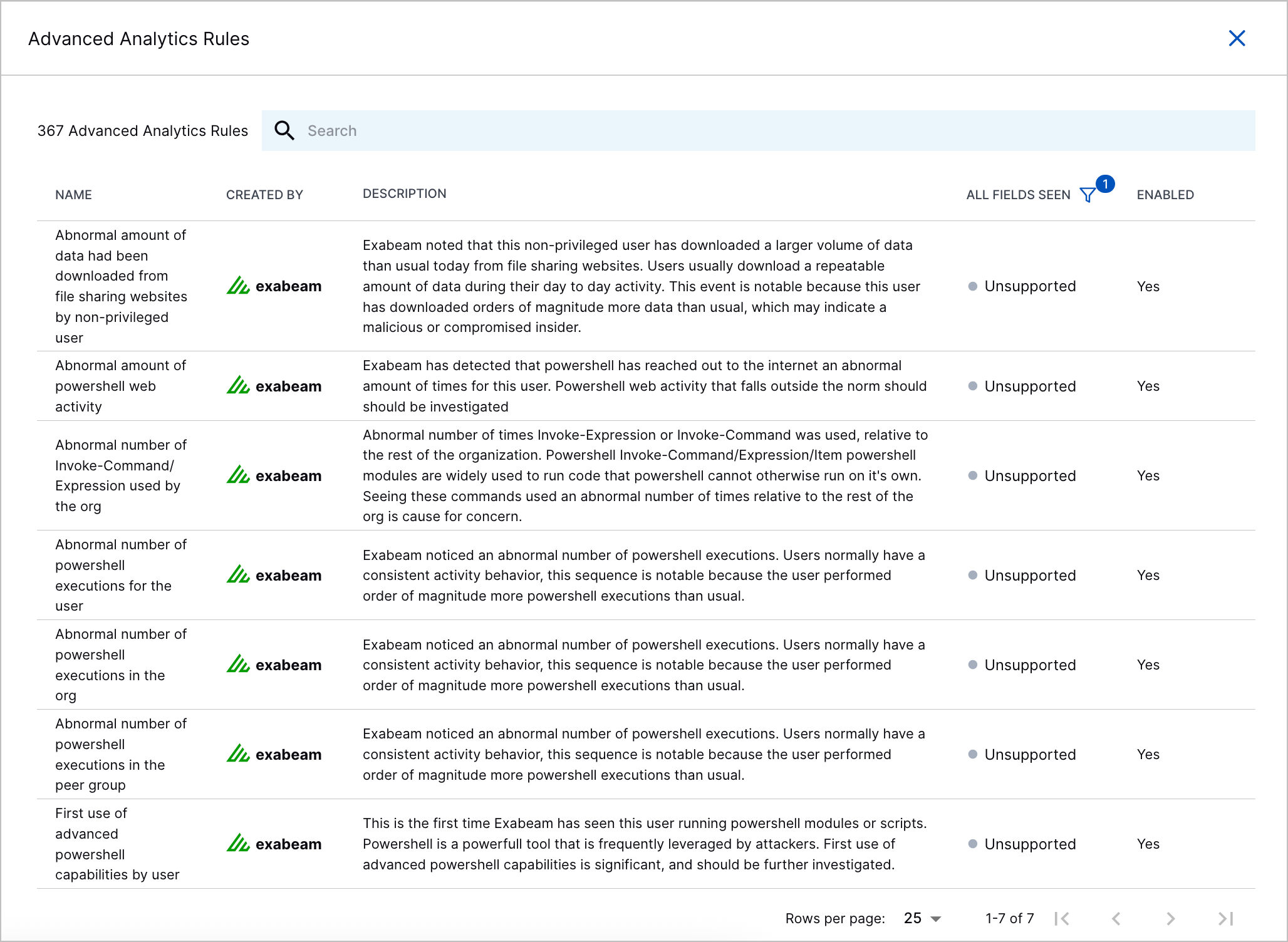 |
Search
Feature | Description | ||
|---|---|---|---|
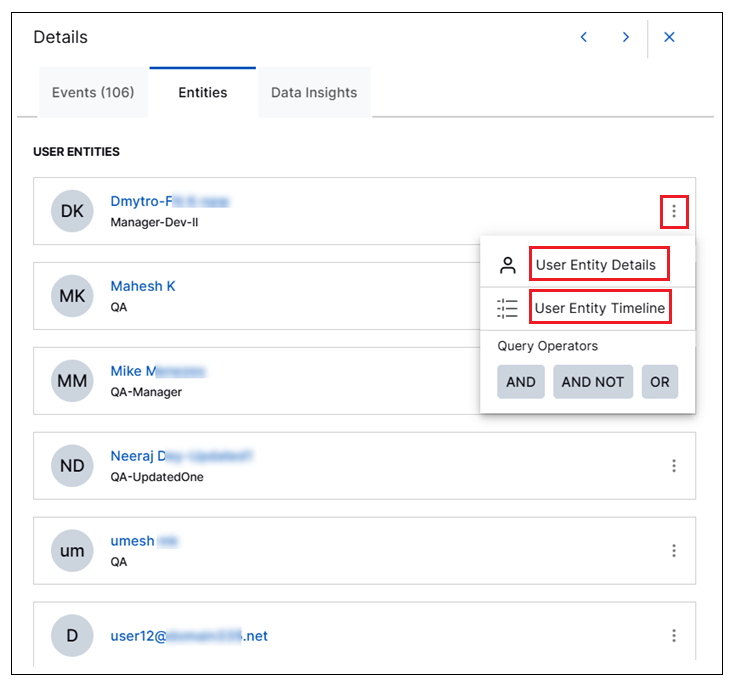
Entity Details Information Available from Search Results | A new Entities tab is now available in the Details panel for viewing user entity information when search results return events associated with parsed user entity fields. This new tab provides multiple ways to explore the user entities that may be associated with security risks or anomalous behavior associated with the events in your search results:
For more information about all of these Entities tab capabilities, see Entity Details in the Search Guide.
| ||
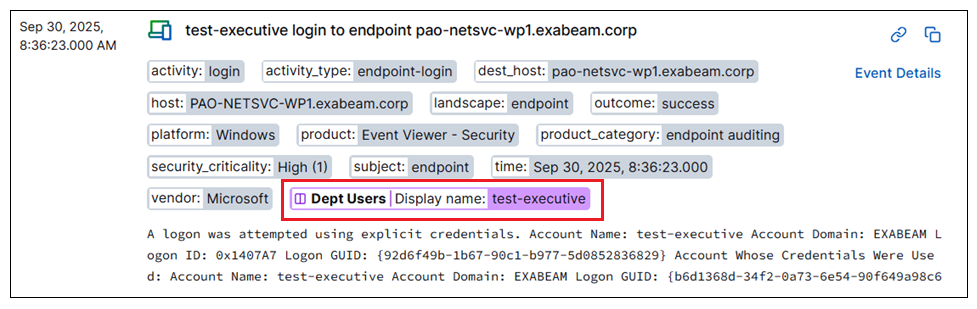
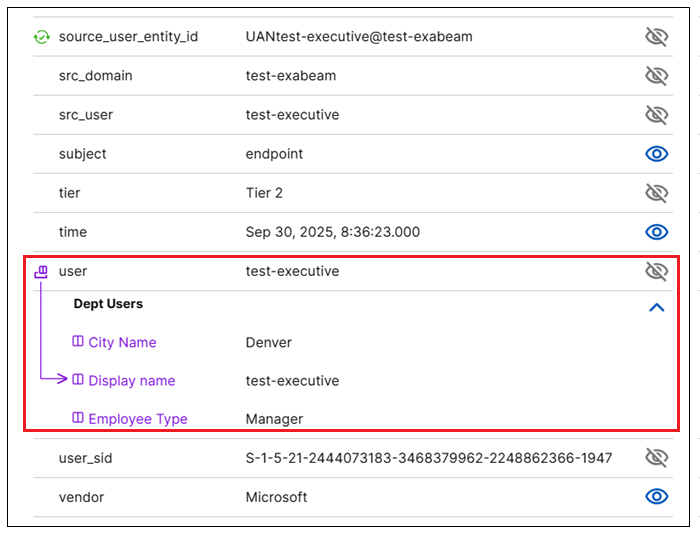
Expanded Context Table Information Displayed in Search Results | More context table information is now visible in search results when a field value is extracted from a context table record. To enhance the way context information is presented in search results, some new formats are in use:
For more information, see Context Tables in Search in the Search Guide. |
Site Collectors 2.14
Feature | Description |
|---|---|
Enhancements for the MySQL Collector | You can now enable SSL option while configuring the MySQL collector to establish a secure connection between MySQL collector and the MySQL server. |
Threat Center
Feature | Description |
|---|---|
Comments for All Predefined Case Closed Reasons | To add more context to case closures, you can now enter a comment for all predefined case closed reasons. 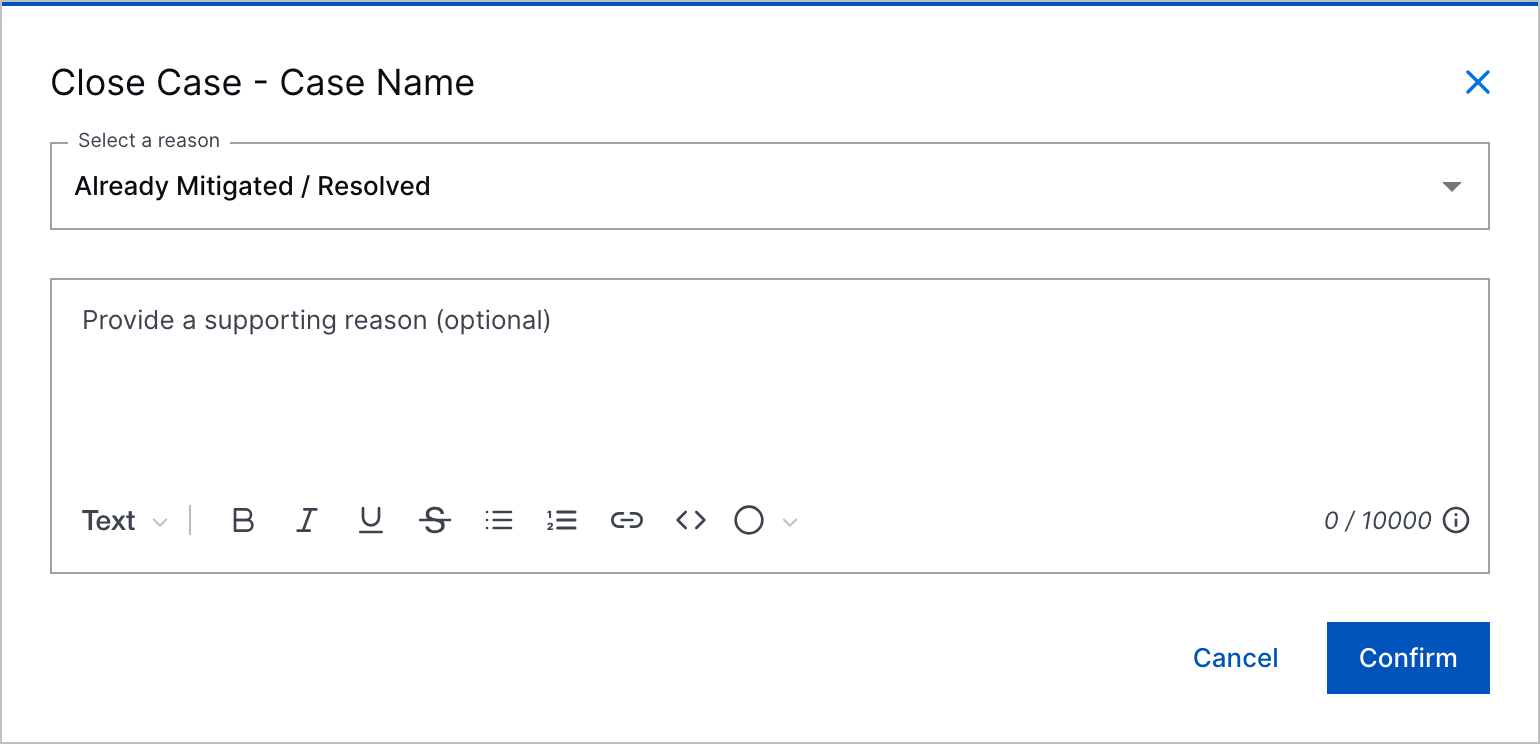 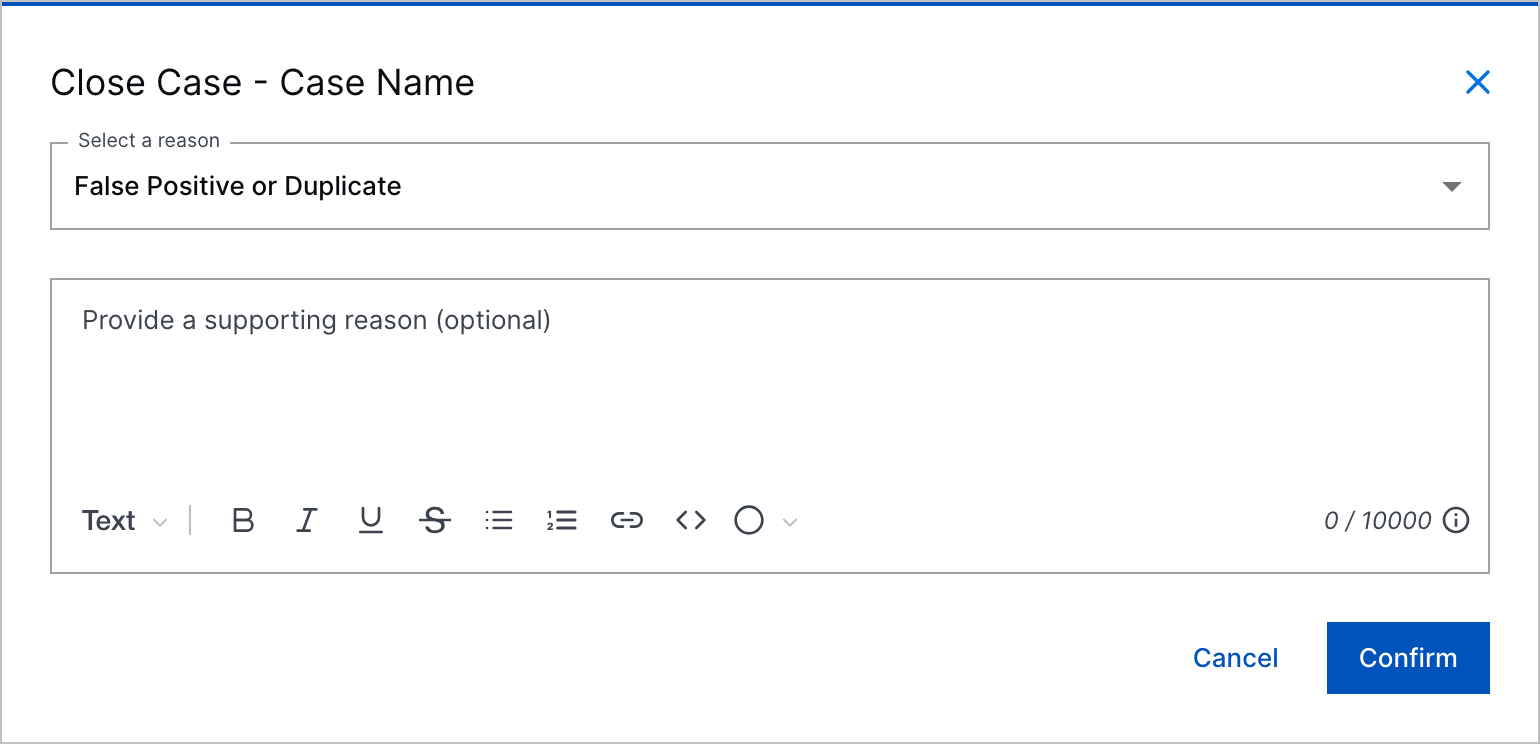 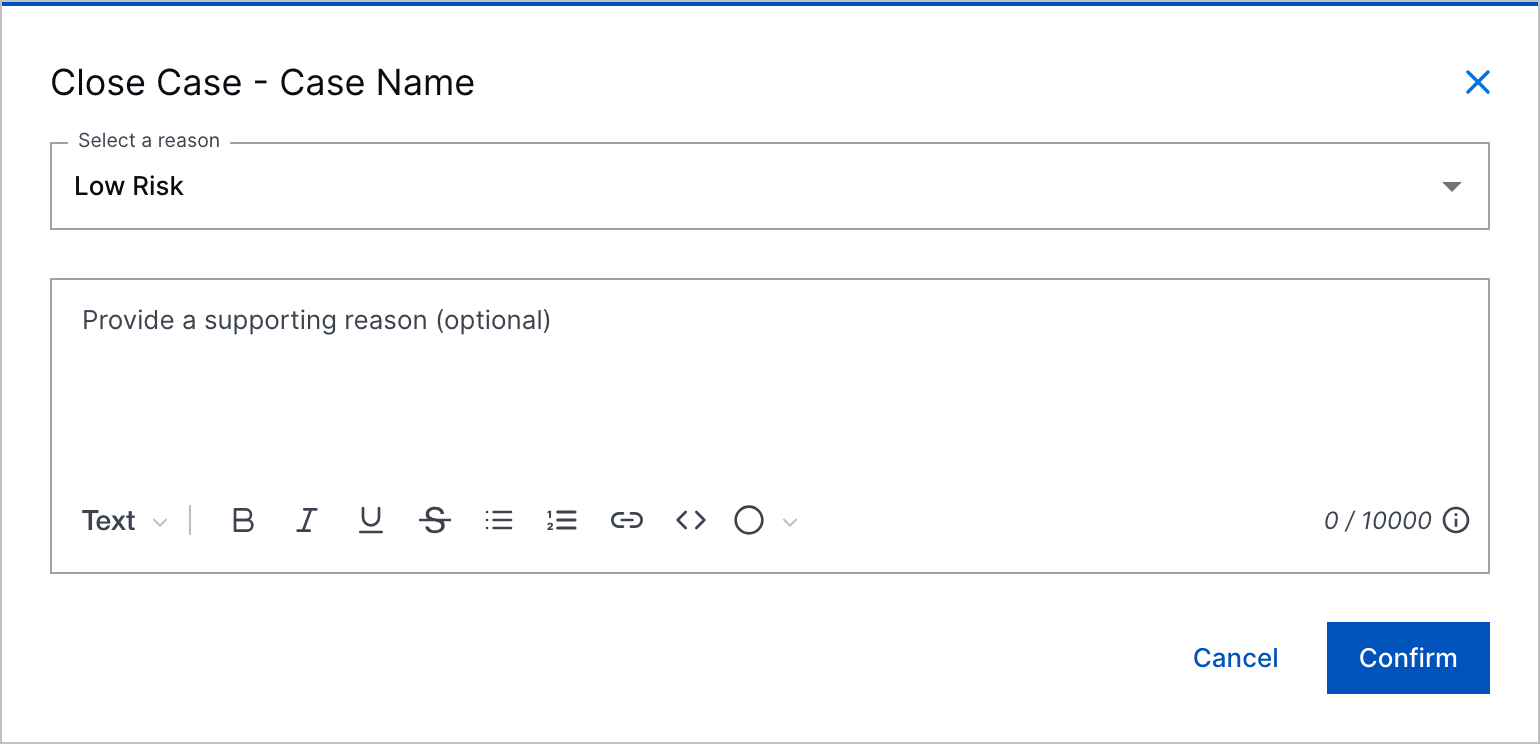 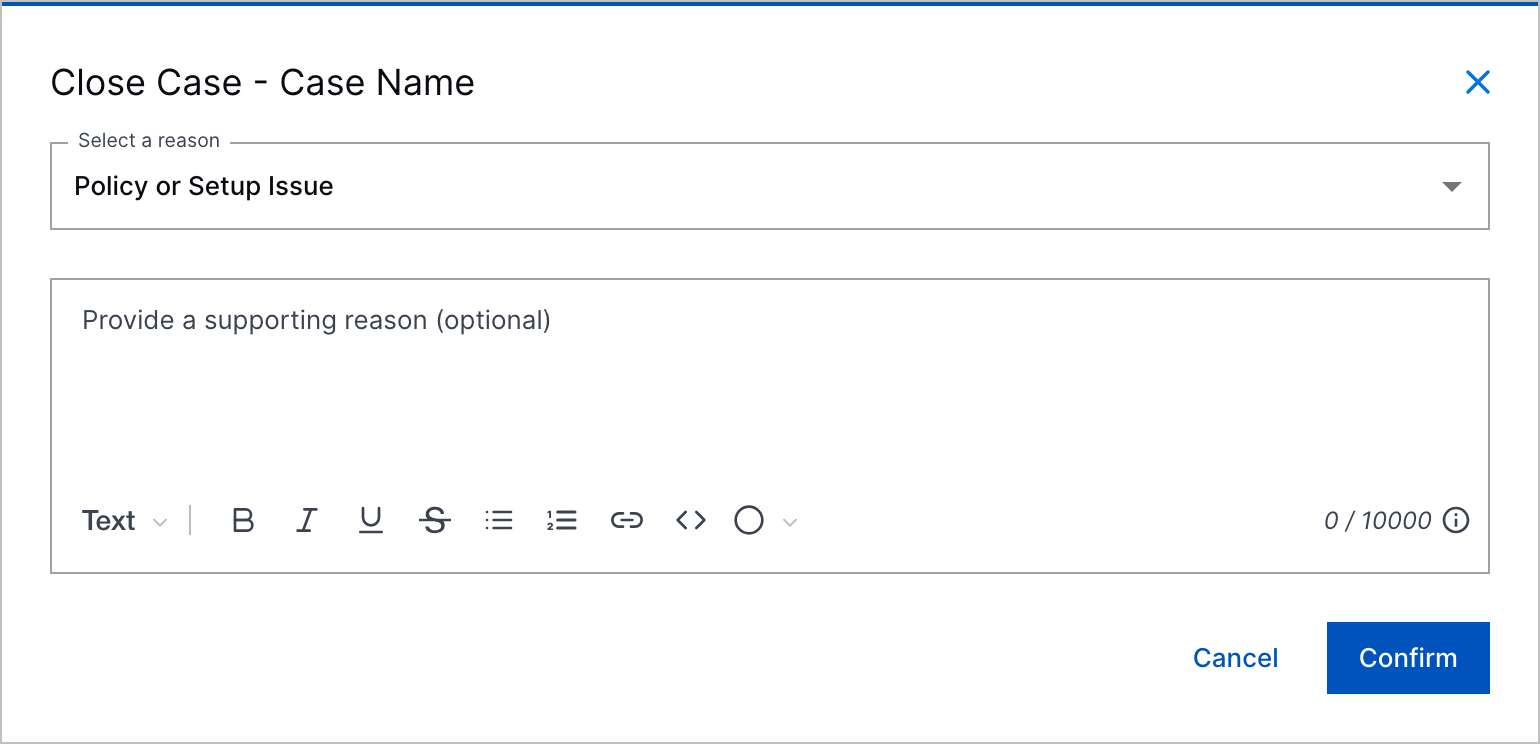 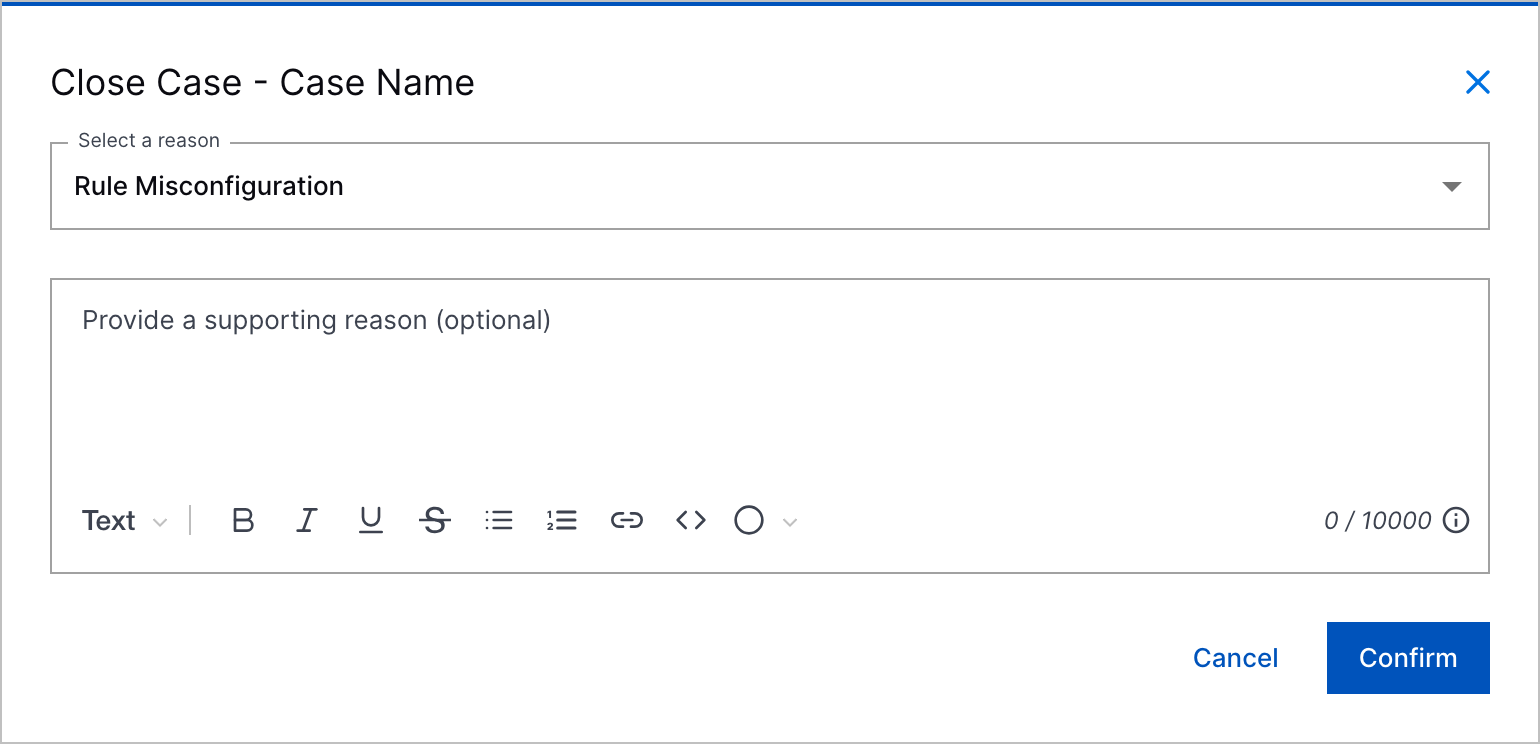 |
Threat Detection Management
Feature | Description |
|---|---|
Increased Analytics Rule Description Character Limit | To ensure you can communicate everything you want with the analytics rule description, you can now add up to 1,024 characters in the description when using the analytics rule builder. 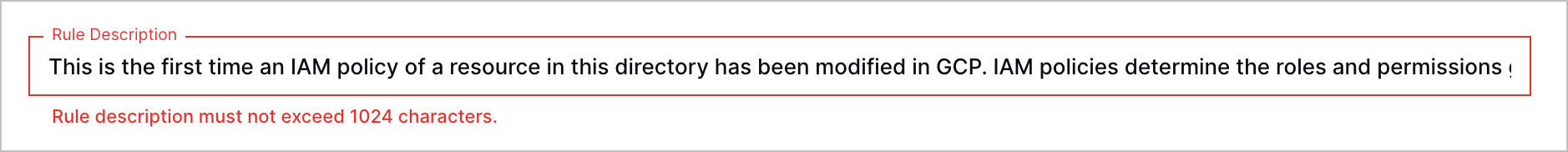 |
Analytics Rule Configuration Enhancements | To simplify and improve the consistency of analytics rule configuration, several analytics rule fields and the analytics rule builder experience have been enhanced. For factFeature rules:
For numericCountProfiledFeature, numericDistinctCountProfiledFeature, and numericSumProfiledFeature rules, the Count per field is now optional in the analytics rule builder. 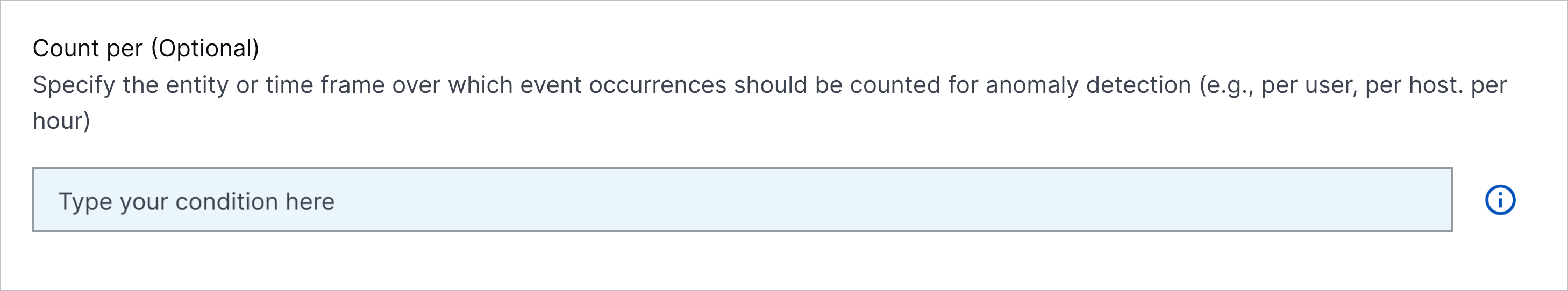 |
New and Updated Pre-Built Analytics Rules | You can now better detect registry manipulations, anomalous user and endpoint activity, and suspicious network data transfers with new and updated pre-built analytics rules. New pre-built analytics rules include:
Pre-built analytics rules for which
|
Resolved Issues
Site Collector 2.14: Security Vulnerabilities Remediations
The Site Collectors 2.14 (October 2025) release includes remediated security vulnerabilities. For more information about Exabeam’s commitment to remediating vulnerabilities for Site Collector, see the Vulnerability Remediation Policy.
There are no open known CVEs in any container image (Nifi). Toolkit has been deprecated and is no longer in use hence no security vulnerabilities update is available for that.
The following table lists the CVEs remediated for the Nifi container and their severity.
Critical | High | Medium | Low |
|---|---|---|---|
Total: 0 | Total: 1 | Total: 5 | Total: 2 |
– | CVE-2025-9900 – |
|
|