- Supported Cloud Connectors
- Armis Cloud Connector
- AWS Cloud Connector
- AWS Multi-Tenant Cloud Connector
- Azure Cloud Connector
- Azure Cloud Connector Overview
- Azure Audit Source and Event Support
- Prerequisites to Configure the Azure Cloud Connector
- Configure the Azure Cloud Connector
- Collect EventHub Information for Azure EventHub Endpoints
- Collect all Microsoft Defender ATP Events
- Configure Azure to Monitor Security Center Events in Azure VMs
- Bitglass Cloud Connector
- Box Cloud Connector
- Centrify Cloud Connector
- Cisco AMP for Endpoints Cloud Connector
- Cisco Meraki Cloud Connector
- Cisco Umbrella Cloud Connector
- Citrix ShareFile Cloud Connector
- Cloudflare Cloud Connector
- Code42 Incydr Cloud Connector
- CrowdStrike Falcon Cloud Connector
- Cybereason Cloud Connector
- CylanceProtect Cloud Connector
- Dropbox Business Cloud Connector
- Duo Security Cloud Connector
- Egnyte Cloud Connector
- Fidelis Cloud Connector
- GitHub Cloud Connector
- Google Cloud Platform (GCP) Cloud Connector
- Google Cloud Pub/Sub Cloud Connector
- Google Workspace (Formerly G Suite) Cloud Connector
- LastPass Enterprise Cloud Connector
- Mimecast Email Security Cloud Connector
- Netskope Cloud Connector
- Office 365 Cloud Connector
- Okta Cloud Connector
- OneLogin Cloud Connector
- Palo Alto Networks SaaS Security Cloud Connector
- Ping Identity Cloud Connector
- Proofpoint Cloud Connector
- Rapid7 InsightVM Cloud Connector
- Salesforce Cloud Connector
- SentinelOne Cloud Connector
- ServiceNow Cloud Connector
- Slack App Cloud Connector
- Slack Classic App Cloud Connector (Formerly known as Slack Enterprise Grid Cloud Connector)
- Snowflake Cloud Connector
- Sophos Central Cloud Connector
- Symantec CloudSOC Cloud Connector
- Symantec Endpoint Protection (SEP) Mobile Cloud Connector
- Symantec Email Security.cloud Cloud Connector
- Symantec WSS Cloud Connector
- Tenable.io Cloud Connector
- VMware Carbon Black Cloud Endpoint Standard Cloud Connector
- Workday Cloud Connector
- Zoom Cloud Connector
- Custom Cloud Connector
- Webhook Cloud Connector
Centrify Cloud Connector
Centrify provides identity centric Privileged Access Management (PAM) to secure enterprise identities against cyberthreats. Centrify provides single-sign on (SSO), automates app access, secures cloud and on-premises apps via multi-factor authentication, and helps to deploy and manage mobile devices. For more information visit their website.
Prerequisites to Configure the Centrify Connector
Before you configure the Centrify connector you must complete the following prerequisites:
Obtain the Centrify tenant
Create the Centrify app to obtain application ID, application secret, scope, and suffix
Obtain the Centrify Tenant
Centrify assigns a unique customer specific identifier or tenant ID to the instance of the organization when an organization registers for the identity services. Then Centrify automatically generates a URL and prefixes the customer specific identifier to the string ‘my.centrify.com’. The customer-specific identifier in the URL is called the tenant or tenant ID. For example, if the customer-specific identifier is ABCD1234, Centrify automatically creates the URL: ABCD1234.my.centrify.com. For this URL, the tenant ID is ABCD1234.
Create a Centrify App to Obtain the Application
ID, Secret, Scope, and Suffix Centrify APIs are authenticated via application keys. You create a Centrify app and obtain the application key that you can use as a client ID while configuring the Centrify connector.
To obtain the application ID, secret, scope, and suffix you must:
Create a specific user for the Centrify app
Create a service account role for user
Create a new OAuth app
Configure the OAuth app that you created
Create a User
Log in to the Centrify admin portal by accessing https://123456.my.centrify.com/manage and replace 123456 with the specific Centrify tenant ID.
Note
If you have already logged in to the Centrify portal as a different user, to access the admin portal, click your user name in the upper right corner and click Switch to Admin Portal.
Navigate to Core Services > Users > Add User.
In the Account section, enter the appropriate information for the fields such as Log in name, Suffix, Email address, Password, Status, Description, Office Number, and Home number.
Note
Note the domain name that you specify for the suffix. For example, @mysuffix.com.
Select Is OAuth Confidential Client (Preview) in the Status field.
Click Create User.
Create the Service Account Role for the App
On the Centrify admin portal, navigate to Core Services > Roles > Add Role.
In the Description field, enter the appropriate description for the account.
Click Members and click Add.
In the Search bar, type the user name of the user that you created, select the check box for the user and click Add.
In the left pane, click Administrative Rights and click Add.
Select Read Only System Administration and click Add.
Click Save. A new role is created.
Create an OAuth App and Configure the OAuth2 Client
On the Centrify admin portal, in the left pane, navigate to Apps > Web Apps > Add Web Apps.
Click Custom.
On the Custom tab, next to the OAuth2 Client application, click Add.
To create an OAuth2 Client for the Centrify APIs, in the Add Web App page, click Yes to add the application. The admin portal adds the application.
Click Close. The Settings section for OAuth2 Client appears.
To configure the OAuth2 client, enter the required information in the fields such as Application ID, Name, Description, and Category:
Application ID Enter the user name that you specified for the new user, without spaces.
Customize Name and Description for each language: Select the check box to specify a name and description for this app.
Name: Specify a name for the application.
Description: Describe the app.
Category: Select Other.
Click Save.
On the General Usage page, enter the required information:
Click ID Type: Select Confidential to allow an OAuth2 client to send a client ID and secret.
Issuer: Enter the URL of the server issuing access tokens. Or, retain the default value.
On the Tokens page, enter the required information
Token Type: Select JwtRS256.
Auth Methods: Select Client Creds.
Token Lifetime: Specify the duration of the initial token.
Issue refresh tokens: Select this option and retain the value 365 days or change the value based on your requirement.
On the Scopes page, to add scope ,click Add.
In the Scope Definitions section, specify a name for scope. For example, QueryScope. Enter the description.
In the Allowed REST APIs section click Add and enter Redrock/Query/*.
Note
Ensure that user role for the user you created has the access to Redrock/Query API. Note the name you specified for the scope definition to use while configuring the Centrify cloud connector.
Navigate to General Usage tab, click the Click here to create one link, and save any changes.
Click Permissions.
Search for the user that you created and click Add.
Click Save.
Check if the application status changes to Deployed.
Create an OAuth App and Configure the OAuth2 Client
On the Centrify admin portal, in the left pane, navigate to Apps > Web Apps > Add Web Apps.
Click Custom.
On the Custom tab, next to the OAuth2 Client application, click Add.
To create an OAuth2 Client for the Centrify APIs, in the Add Web App page, click Yes to add the application. The admin portal adds the application.
Click Close. The Settings section for OAuth2 Client appears.
To configure the OAuth2 client, enter the required information in the fields such as Application ID, Name, Description, and Category:
Application ID Enter the user name that you specified for the new user, without spaces.
Customize Name and Description for each language: Select the check box to specify a name and description for this app.
Name: Specify a name for the application.
Description: Describe the app.
Category: Select Other.
Click Save.
On the General Usage page, enter the required information:
Click ID Type: Select Confidential to allow an OAuth2 client to send a client ID and secret.
Issuer: Enter the URL of the server issuing access tokens. Or, retain the default value.
On the Tokens page, enter the required information
Token Type: Select JwtRS256.
Auth Methods: Select Client Creds.
Token Lifetime: Specify the duration of the initial token.
Issue refresh tokens: Select this option and retain the value 365 days or change the value based on your requirement.
On the Scopes page, to add scope ,click Add.
In the Scope Definitions section, specify a name for scope. For example, QueryScope. Enter the description.
In the Allowed REST APIs section click Add and enter Redrock/Query/*.
Note
Ensure that user role for the user you created has the access to Redrock/Query API. Note the name you specified for the scope definition to use while configuring the Centrify cloud connector.
Navigate to General Usage tab, click the Click here to create one link, and save any changes.
Click Permissions.
Search for the user that you created and click Add.
Click Save.
Check if the application status changes to Deployed.
Copy the values for the login name of the user that you created, which is used as an application ID, the user password that is used as the application secret, scope, and suffix. Use these values, represented by a string of letters and numbers, to configure the Centrify cloud connector.
Configure the Centrify Connector
Centrify provides identity centric Privileged Access Management (PAM) to secure enterprise identities against cyberthreats. Centrify provides single-sign on (SSO), automates app access, secures cloud and on-premises apps via multi-factor authentication, and helps to deploy and manage mobile devices. For more information, visit their website.
To configure the Centrify connector to import data into the Exabeam Cloud Connector platform:
Complete the Prerequisites to Configure the Centrify Connector.
Log in to the Exabeam Cloud Connectors platform with your registered credentials.
Navigate to Settings > Accounts > Add Account.
Click Select Service to Add, then select Centrify from the list.
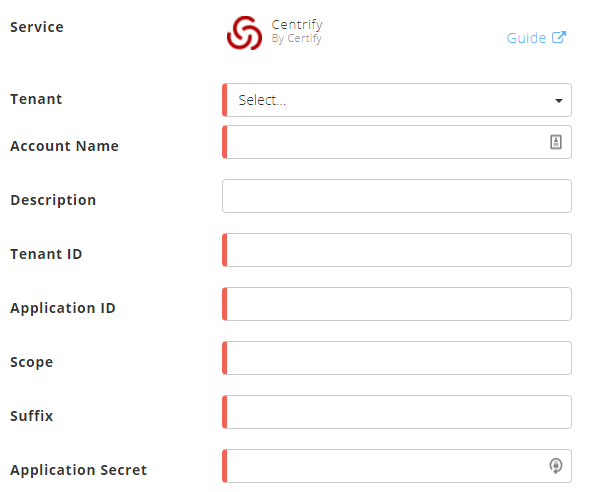
In the Accounts section, enter the required information.
Account Name – Specify a name for the Centrify connector. For example, Centrify_SSO.
(Optional) Description – Describe the Centrify connector. For example, Centrify PAM and SSO for secure cloud apps.
Tenant ID – Enter the tenant ID that you obtained from the URL while completing prerequisites.
Application ID – Enter the user name of the user you created while completing prerequisites.
Scope – Enter the value for the scope that you specified for the scope definition while completing prerequisites.
Suffix – Enter the value for suffix that you obtained while completing prerequisites.
Application Secret – Enter the password for the user that you created while completing prerequisites.
Note
Required fields are indicated with a red bar.
To confirm that the Exabeam Cloud Connector platform communicates with the service, click Test Connection.
Click Done to save your changes. The cloud connector is now set up on the Exabeam Cloud Connector platform.
To ensure that the connector is ready to send and collect data, Start the connector and check that the status shows
OK.
