- Supported Cloud Connectors
- Armis Cloud Connector
- AWS Cloud Connector
- AWS Multi-Tenant Cloud Connector
- Azure Cloud Connector
- Azure Cloud Connector Overview
- Azure Audit Source and Event Support
- Prerequisites to Configure the Azure Cloud Connector
- Configure the Azure Cloud Connector
- Collect EventHub Information for Azure EventHub Endpoints
- Collect all Microsoft Defender ATP Events
- Configure Azure to Monitor Security Center Events in Azure VMs
- Bitglass Cloud Connector
- Box Cloud Connector
- Centrify Cloud Connector
- Cisco AMP for Endpoints Cloud Connector
- Cisco Meraki Cloud Connector
- Cisco Umbrella Cloud Connector
- Citrix ShareFile Cloud Connector
- Cloudflare Cloud Connector
- Code42 Incydr Cloud Connector
- CrowdStrike Falcon Cloud Connector
- Cybereason Cloud Connector
- CylanceProtect Cloud Connector
- Dropbox Business Cloud Connector
- Duo Security Cloud Connector
- Egnyte Cloud Connector
- Fidelis Cloud Connector
- GitHub Cloud Connector
- Google Cloud Platform (GCP) Cloud Connector
- Google Cloud Pub/Sub Cloud Connector
- Google Workspace (Formerly G Suite) Cloud Connector
- LastPass Enterprise Cloud Connector
- Mimecast Email Security Cloud Connector
- Netskope Cloud Connector
- Office 365 Cloud Connector
- Okta Cloud Connector
- OneLogin Cloud Connector
- Palo Alto Networks SaaS Security Cloud Connector
- Ping Identity Cloud Connector
- Proofpoint Cloud Connector
- Rapid7 InsightVM Cloud Connector
- Salesforce Cloud Connector
- SentinelOne Cloud Connector
- ServiceNow Cloud Connector
- Slack App Cloud Connector
- Slack Classic App Cloud Connector (Formerly known as Slack Enterprise Grid Cloud Connector)
- Snowflake Cloud Connector
- Sophos Central Cloud Connector
- Symantec CloudSOC Cloud Connector
- Symantec Endpoint Protection (SEP) Mobile Cloud Connector
- Symantec Email Security.cloud Cloud Connector
- Symantec WSS Cloud Connector
- Tenable.io Cloud Connector
- VMware Carbon Black Cloud Endpoint Standard Cloud Connector
- Workday Cloud Connector
- Zoom Cloud Connector
- Custom Cloud Connector
- Webhook Cloud Connector
CrowdStrike Falcon Cloud Connector
CrowdStrike provides cloud delivered services that include endpoint protection, antivirus, endpoint detection and response (EDR). Using machine learning and behavioral-based analytics, CrowdStrike also provides managed threat hunting for constant breach and threat prevention. The CrowdStrike Falcon platform stops breaches by preventing and responding to all types of malware attacks. Using the CrowdStrike Threat Graph, CrowdStrike Falcon analyzes and correlates billions of events in real time to provide complete protection and visibility across all endpoints. For more information see the CrowdStrike product information.
Audit Source API and Security Event Support
The following table displays the audit source API and security events supported by the CrowdStrike connector.
Audit Source: API | Service or Module Covered | Events Types | Notes |
|---|---|---|---|
Full audit events and alerts | Administrative actions and alerts | All | |
The raw Threat Graph event also called Falcon platform | CrowdStrike forwards events to AWS S3 bucket and Exabeam collects the events from AWS S3 bucket. |
Prerequisites to Configure the CrowdStrike Falcon Connector
CrowdStrike supports two APIs to retrieve events:
Falcon Streaming API – Streaming API provides detections and audit events. Contact CrowdStrike support to enable this option because by default the Streaming API option is disabled.
Falcon Data Replicator (FDR) – FDR provides raw event data. Contact CrowdStrike support to obtain a managed AWS S3 bucket for storage for a short duration and Simple Queue Service (SQS) for notifications about newly created files. CrowdStrike support will provide you with Access Key, Access Secret, SQS region, and SQS URL.
Select the API that suits your requirements. FDR supports larger volume of events; however, it is a little complex to set up and requires relevant CrowdStrike configurations.
Before you configure the CrowdStrike Falcon connector you must complete the following prerequisites:
Ensure that the https://*.crowdstrike.com service is open for communication with the Exabeam Cloud Connectors platform.
Make sure that you have Admin privileges for the Falcon platform and paid membership for Falcon Insight and Falcon Prevent products.
Contact CrowdStrike support to obtain the cloud endpoint API gateway assigned to your API client.
Note
CrowdStrike assigns a cloud endpoint, also called an API gateway, to each API client. For example: https://api.crowdstrike.com or https://api.us-2.crowdstrike.com.
If you want to use streaming API, obtain the client ID and client secret for the OAuth2 authentication method.
If you want to use FDR, obtain Access Key, Access Secret, SQS region, and SQS URL.
Obtain your Exabeam CrowdStrike Ingestor Client ID.
Obtain the Client ID and Client Secret for Streaming API
CrowdStrike APIs are authenticated via application keys. You must obtain the client ID and client secret to use while configuring the CrowdStrike connector.
To obtain an application key:
Log in to the CrowdStrike console as an administrator.
In the left pane, navigate to Support and Resources > API Clients and Keys.
In the upper right corner of the page that displays existing clients, click Create API Client.
In the Create API Client dialog box, specify a name and enter description for the new client that will need access to the detection API in read-only mode.
In the API Scopes, select Read for Event Streams to define the required API capabilities.
Click Create. A table displays the values for Client ID and Client Secret. Record these values represented by a string of letters and numbers, to use while configuring the CrowdStrike cloud connector.
Click Done.
Obtain Access Key, Access Secret, SQS region, and SQS URL for FDR
Contact CrowdStrike support to request a managed AWS S3 bucket for short-term storage and an SQS for new file notifications. Obtain the Access Key, Access Secret, SQS region, and SQS URL by contacting the CrowdStrike support team.
Configure the CrowdStrike Falcon Connector
CrowdStrike provides cloud delivered services that include endpoint protection, antivirus, endpoint detection and response (EDR), and managed threat hunting for constant breach prevention, and threat prevention via machine learning and behavioral-based analytics. The CrowdStrike Falcon platform stops breaches by preventing and responding to all types of malware attacks. Using the CrowdStrike Threat Graph, CrowdStrike Falcon analyzes and correlates billions of events in real time to provide complete protection and visibility across all endpoints. For more information see the product information.
To configure the CrowdStrike connector to import data into the Exabeam Cloud Connector platform:
Complete the Prerequisites to Configure the CrowdStrike Falcon Connector.
Log in to the Exabeam Cloud Connectors platform with your registered credentials.
Navigate to Settings > Accounts > Add Account.
Click Select Service to Add, then select CrowdStrike from the list.
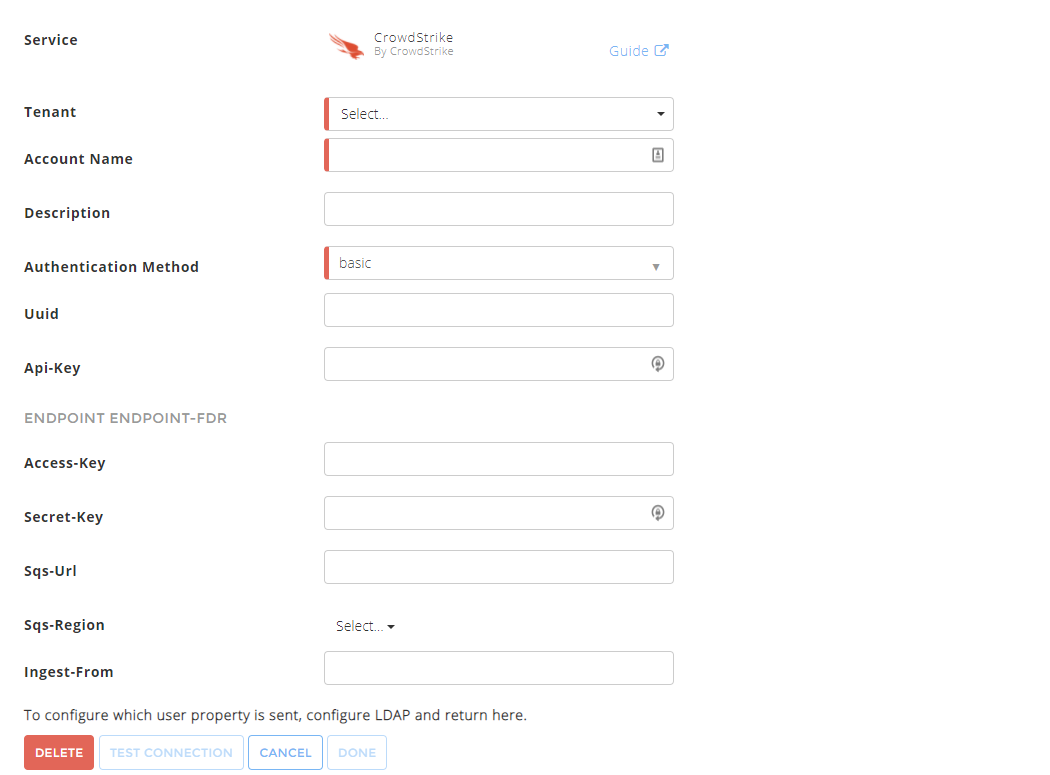
In the Accounts section, enter the required information. Required fields are indicated with a red bar.
Tenant – Select a tenant to attach to the connector if you are using a multi-tenant edition of Exabeam. Otherwise, select default.
Account Name – Specify a name for the CrowdStrike connector. For example, CrowdStrike corporate endpoint protection solution.
Description – (Optional) Describe the CrowdStrike connector. For example, CrowdStrike for endpoint protection, endpoint detection and response (EDR), and threat prevention.
Authentication Method – Use the default option oauth2.
Client-ID – Enter the client ID that you obtained while completing prerequisites.
Client-Secret – Enter the client secret that you obtained while completing prerequisites.
Note
If you want to use FDR, enter the values in the Endpoint Endpoint-FDR section for Access Key, Access Secret, SQS region, and SQS URL that you obtained while completing prerequisites.
Cloud Endpoint – Enter the API gateway URL that you obtained while completing prerequisites. For example: https://api.crowdstrike.com or https://api.us-2.crowdstrike.com.
Ingest-From – Use this field to provide a threshold before which the connector will exclude events. The options are:
Now– (Default) When you specifyNow(ornow) in this field, the CrowdStrike connector calculates the date and time associated with the saved configuration as the threshold for event filtering. This means any previous events are dropped and excluded from ingestion.mm-dd-yyyy hh:mm:ss timezone– If you want to set a different threshold for log ingestion, enter a date and time in the specified format (for example02-07-2022 09:22:00 PST).""/empty – If no threshold is provided, all logs are ingested.
To confirm that the Exabeam Cloud Connector platform communicates with the service, click Test Connection.
Click Done to save your changes. The cloud connector is now set up on the Exabeam Cloud Connector platform.
To ensure that the connector is ready to send and collect data, Start the connector and check that the status shows
OK.
Troubleshoot the CrowdStrike Cloud Connector
Refer to the following table of commonly encountered issues and possible solutions.
Scenario | Solution |
|---|---|
The FDR item explorer endpoint gave the following error: AmazonSQSException: The request signature we calculated does not match the signature you provided. Check your AWS Secret Access Key and signing method. | This error message indicates that the credentials you entered are incorrect. To verify if the credentials containing the secret and access key in the cloud connector UI are correct, use the the following workflow and review the message from the SQS queue using the AWS CLI docker container.
|
Events are not pulled using FDR after configuring the connector. | Ensure that the FDR explorer endpoint is active because the FDR endpoint depends on the FDR item explorer endpoint. |
You receive an HTTP error 403 from the connector for streaming API. | The HTTP error occurs if the streaming API is not enabled. Contact CrowdStrike support to enable the streaming API. |
