- Supported Cloud Connectors
- Armis Cloud Connector
- AWS Cloud Connector
- AWS Multi-Tenant Cloud Connector
- Azure Cloud Connector
- Azure Cloud Connector Overview
- Azure Audit Source and Event Support
- Prerequisites to Configure the Azure Cloud Connector
- Configure the Azure Cloud Connector
- Collect EventHub Information for Azure EventHub Endpoints
- Collect all Microsoft Defender ATP Events
- Configure Azure to Monitor Security Center Events in Azure VMs
- Bitglass Cloud Connector
- Box Cloud Connector
- Centrify Cloud Connector
- Cisco AMP for Endpoints Cloud Connector
- Cisco Meraki Cloud Connector
- Cisco Umbrella Cloud Connector
- Citrix ShareFile Cloud Connector
- Cloudflare Cloud Connector
- Code42 Incydr Cloud Connector
- CrowdStrike Falcon Cloud Connector
- Cybereason Cloud Connector
- CylanceProtect Cloud Connector
- Dropbox Business Cloud Connector
- Duo Security Cloud Connector
- Egnyte Cloud Connector
- Fidelis Cloud Connector
- GitHub Cloud Connector
- Google Cloud Platform (GCP) Cloud Connector
- Google Cloud Pub/Sub Cloud Connector
- Google Workspace (Formerly G Suite) Cloud Connector
- LastPass Enterprise Cloud Connector
- Mimecast Email Security Cloud Connector
- Netskope Cloud Connector
- Office 365 Cloud Connector
- Okta Cloud Connector
- OneLogin Cloud Connector
- Palo Alto Networks SaaS Security Cloud Connector
- Ping Identity Cloud Connector
- Proofpoint Cloud Connector
- Rapid7 InsightVM Cloud Connector
- Salesforce Cloud Connector
- SentinelOne Cloud Connector
- ServiceNow Cloud Connector
- Slack App Cloud Connector
- Slack Classic App Cloud Connector (Formerly known as Slack Enterprise Grid Cloud Connector)
- Snowflake Cloud Connector
- Sophos Central Cloud Connector
- Symantec CloudSOC Cloud Connector
- Symantec Endpoint Protection (SEP) Mobile Cloud Connector
- Symantec Email Security.cloud Cloud Connector
- Symantec WSS Cloud Connector
- Tenable.io Cloud Connector
- VMware Carbon Black Cloud Endpoint Standard Cloud Connector
- Workday Cloud Connector
- Zoom Cloud Connector
- Custom Cloud Connector
- Webhook Cloud Connector
Azure Cloud Connector
Azure Cloud Connector Overview
The Azure cloud platform provides cloud services and products to build, run, and manage applications on multiple clouds and premises. Microsoft Azure cloud services are available in three national clouds in addition to the global datacenter network.
Azure national clouds are unique and a separate environment from Azure global and physically isolated instances of Azure global. In addition to the global cloud, Azure Active Directory (Azure AD) is deployed in these national clouds: Azure Government, Azure Germany, and Azure China 21Vianet. For more information see Azure National Clouds.
If you also need to collect Azure Active Directory (AAD) events, use the Exabeam Office 365 Cloud Connector. The connector collects AAD access events (e.g. login failed, login success), anomaly events, and risk events.
Azure is a suite of cloud services platform, provides Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) services. Azure helps organizations consume compute power and needed services, all without the need to buy or manage hardware.
Azure National Clouds (aka Sovereign clouds) are physically isolated instances of Azure. These regions of Azure are designed to make sure that data residency, sovereignty, and compliance requirements are honored within geographical boundaries.
The Exabeam Azure Cloud Connector supports the entire available Azure National Clouds.
To configure your Exabeam Azure Cloud Connector to support any of the National Clouds, see the Configure the Azure Cloud Connector.
Azure Audit Source and Event Support
The availability of Azure services as security and compliance services depends on the Azure region. To verify the available Azure audit sources and coverage for using the Exabeam Azure cloud connector, perform the following steps.
Navigate to the Monitoring + Management section by accessing https://azure.microsoft.com/en-us/global-infrastructure/services/.
Verify that the Monitoring + Management section displays the following monitoring services for the Azure regions you use:
Log Analytics
Security and Compliance
Protection and Recovery
Note
For any of the Azure regions that you use, if these services are not available, the audit logs and events from these services are also not available.
Azure Log Analytics
After you configure the Azure cloud connector for Exabeam, the cloud connector discovers all the Log Analytics that are deployed in the subscriptions to which the Azure AD app has permissions to query.
To reduce the scope of the data that is collected from each ALA, use Log Analytics KQL query (reference). Verify the KQL query via Azure ALA UI.
Do not restrict the KQL query to a certain time frame because the time frame is automatically added to the query suffix for each sync that the connector performs.
The following table displays audit source API and security events supported by the connector.
Endpoint/API | Service/ Module Covered | Event included | Notes |
|---|---|---|---|
Security Alerts | Security Alerts generated across MS platform | Supported in Exabeam Cloud Connectors 2.4.254 and later releases Alerts generated from:
| |
Administrative | Administrative activities from different modules | This category contains the record of all create, update, delete, and action operations performed through Resource Manager. Examples of the types of events you would see in this category include | |
Azure Virtual Machines | VM events (e.g. VM started) | Supports events related to both Windows and Linux VM | |
Azure Networking Resources | VNETs, Subnets, NSG, Route Tables etc | ||
Log Analytics (aka OMS Workspace) | Azure OS Logs | OS events (e.g. Windows OS events) | Events are collected by a dedicated Windows/Linux agent and attached to a Log Analytics workspace which will then be used by the Exabeam Azure cloud connector to retrieve the events. See more information on how to use the Azure agent at: https://docs.microsoft.com/en-us/azure/azure-monitor/platform/log-analytics-agent |
Log Analytics (aka OMS Workspace) | Azure HDInsight | Hadoop events | See: https://docs.microsoft.com/en-us/azure/hdinsight/hdinsight-hadoop-oms-log-analytics-tutorial |
Log Analytics (aka OMS Workspace) | Azure App Insights | Insights on Azure Apps | Forwards Azure App Insights events to a Log Analytics workspace from which the Azure Cloud Connector will collect the events. For more information on Azure App Insights, see: https://docs.microsoft.com/en-us/azure/azure-monitor/platform/app-insights-connector. |
Azure Key Vault | Key vault events | See: https://docs.microsoft.com/en-us/azure/security/security-azure-log-integration-keyvault-eventhub | |
Azure Diagnostics Events | Diagnostic Events from multiple services | Diagnostic information from many services such as: Application Gateways, Azure Automation, Azure Batch, Customer Insights, Content Delivery Network (CDN), CosmosDB, Data Lake Analytics, Data Lake Store, Event Hubs, Key Vault, Load Balancer | |
Azure Storage Analytics | Activities in Blob, Queue, and Table services | Activities as blob downloaded, table created etc | |
Azure Monitor (Resource Monitor) | To forward the Azure Monitor events to an EventHubs which will then be used by Azure Cloud Connector to collect the events, see https://docs.microsoft.com/en-us/azure/azure-monitor/overview. The following data is collected by the Azure monitor:
For more information on the events collected by the Azure Monitor, see: https://docs.microsoft.com/en-us/azure/azure-monitor/overview#what-data-does-azure-monitor-collect | ||
Subscription Monitoring | Included as part of the Azure Monitor data collected (see above) | ||
IIS | Included as part of the Azure Monitor data collected (see above) See: https://docs.microsoft.com/en-us/azure/azure-monitor/platform/data-sources-iis-logs | ||
Azure Kubernetes Service (AKS) | Master components events | See: https://docs.microsoft.com/en-us/azure/aks/view-master-logs | |
Unknown | Kublets events | See: https://docs.microsoft.com/en-us/azure/aks/kubelet-logs | |
Unknown | Real-time container logs | See: https://docs.microsoft.com/en-us/azure/azure-monitor/insights/container-insights-live-logs | |
or | Azure SQL DB | SQL DB events | See: https://docs.microsoft.com/en-us/azure/sql-database/sql-database-auditing |
Web Application Firewall (WAF) | Included as part of the Azure Monitor data collected (see above) For more information on the WAF data collected, see https://docs.microsoft.com/en-us/azure/application-gateway/waf-overview#monitoring | ||
Azure Security Center | Security center alerts | ||
Azure NSG Flow Logs | NSG Flow Logs | After the NSG flow logs are enabled (see https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-nsg-flow-logging-powershell), the Azure Cloud Connector will automatically discover the related watchers and flow logs and start collecting the logs. | |
Microsoft Graph Security API | Security alerts from the entire Microsoft security products | ||
Log Analytics (aka OMS Workspace) | Azure API Management | Gets the events configure the audit via App Insights. This can be configured in App Insights. For more information, see https://docs.microsoft.com/en-us/azure/api-management/api-management-howto-app-insights. | |
Azure Service Health | Service Health incidents | This category contains the record of any service health incidents that have occurred in Azure. An example of the type of event you would see in this category is | |
Azure Service Alert | Activation of Azure Alerts | This category contains the record of all activations of Azure alerts. An example of the type of event you would see in this category is | |
Azure Autoscale Events | Autoscale events | This category contains the record of any events related to the operation of the autoscale engine based on any autoscale settings you have defined in your subscription. An example of the type of event you would see in this category is | |
Azure Recommendation | Recommendation | This category contains recommendation events from certain resource types, such as web sites and SQL servers. These events offer recommendations for how to better utilize your resources. | |
Microsoft Defender ATP events | Security Events |
Note
You may experience some delay in data ingestion for the following dynamic endpoints because Azure takes some time to make data available at a data collection endpoint. For more information about the delays in pulling the logs from source, see Azure metrics, resource logs, activity log in Azure documentation.
Endpoint | Approximate Delay in Pulling Logs |
|---|---|
Activity Log | 10 minutes |
Storage Analytics | 10 minutes |
Log Analytics OMS Workspace | 15 minutes |
NSG Flow logs | 5 minutes |
Prerequisites to Configure the Azure Cloud Connector
Before you configure the Azure connector, you must create an Azure AD application to obtain the relevant information for your authentication method.
Create an Azure AD Application for the Azure Cloud Connector
Have the following information available depending on your authentication method:
OAuth2:
Azure tenant ID
Client ID (of the Exabeam Cloud Connectors app created in Azure)
Secret ID (of the Exabeam Cloud Connectors app created in Azure)
Certificate:
Azure tenant ID
Client ID (of the Exabeam Cloud Connectors app created in Azure)
Certificate
Private key
Proceed to Configure the Azure Cloud Connector.
Enable access to the regional Domains and URLs Required by the Azure Cloud Connector
Required Azure Subscriptions
Following is the list of minimum Azure subscriptions required per feature.
Feature | Minimum Azure Subscription |
|---|---|
Ingestion from Activity Log | Basic |
Ingestion from EventHub | EventHub Standard or Premium |
Network Security Group (NSG) Flow Logs | Basic |
Log Analytics (OMS Workspace) | Basic |
Storage Analytics | Basic |
Domains and URLs Required by the Azure Cloud Connector
Enable access for the domains and URLs for your Azure cloud region.
Cloud Region | URLs |
|---|---|
Azure AD (global service) |
|
Azure AD China operated by 21Vianet |
|
Azure AD Germany |
|
Azure AD for US Government |
|
Create an Azure AD Application for the Azure Cloud Connector
Open Azure Active Directory.
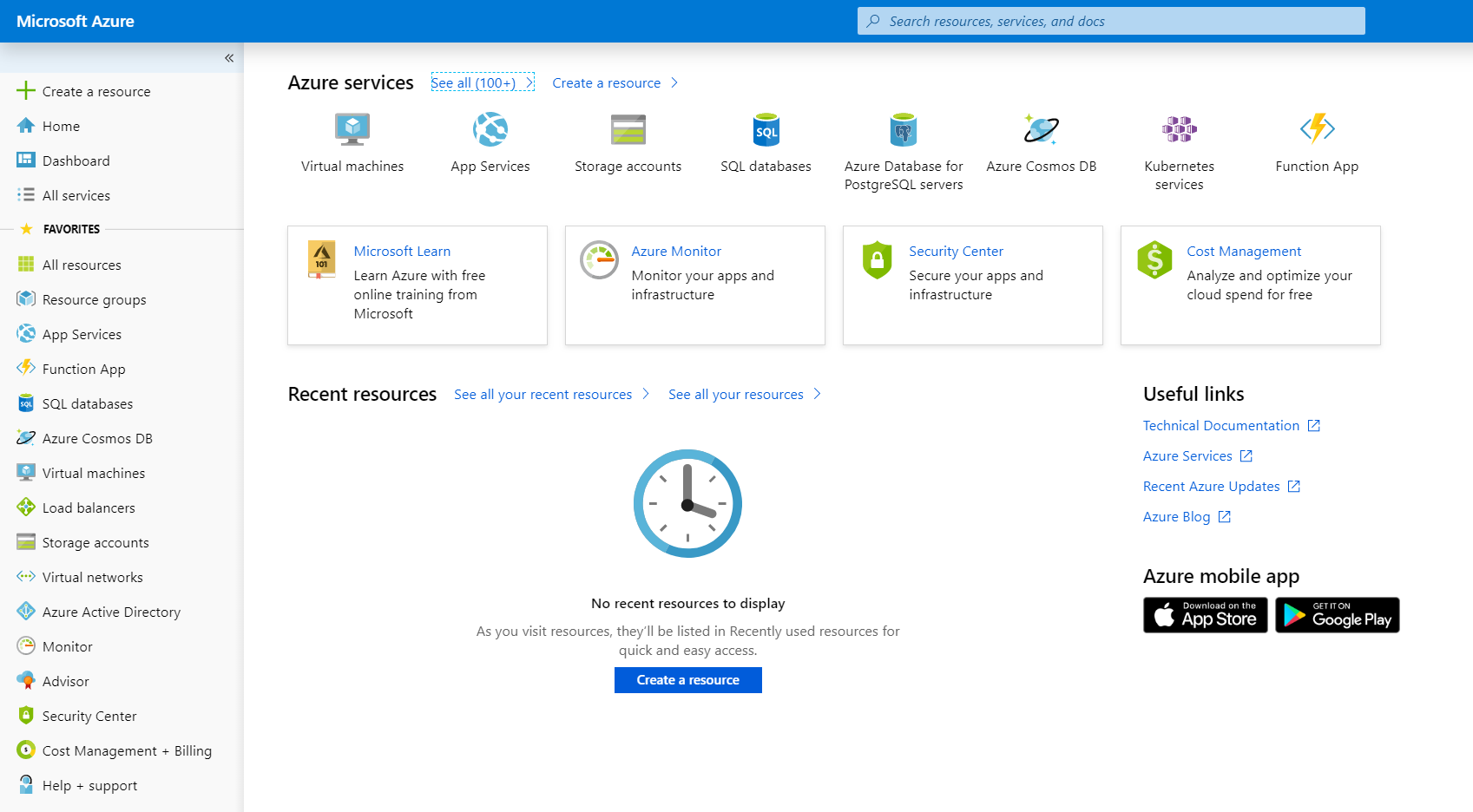
Navigate to Properties. keep aside the value of Directory ID, a.k.a Tenant ID.
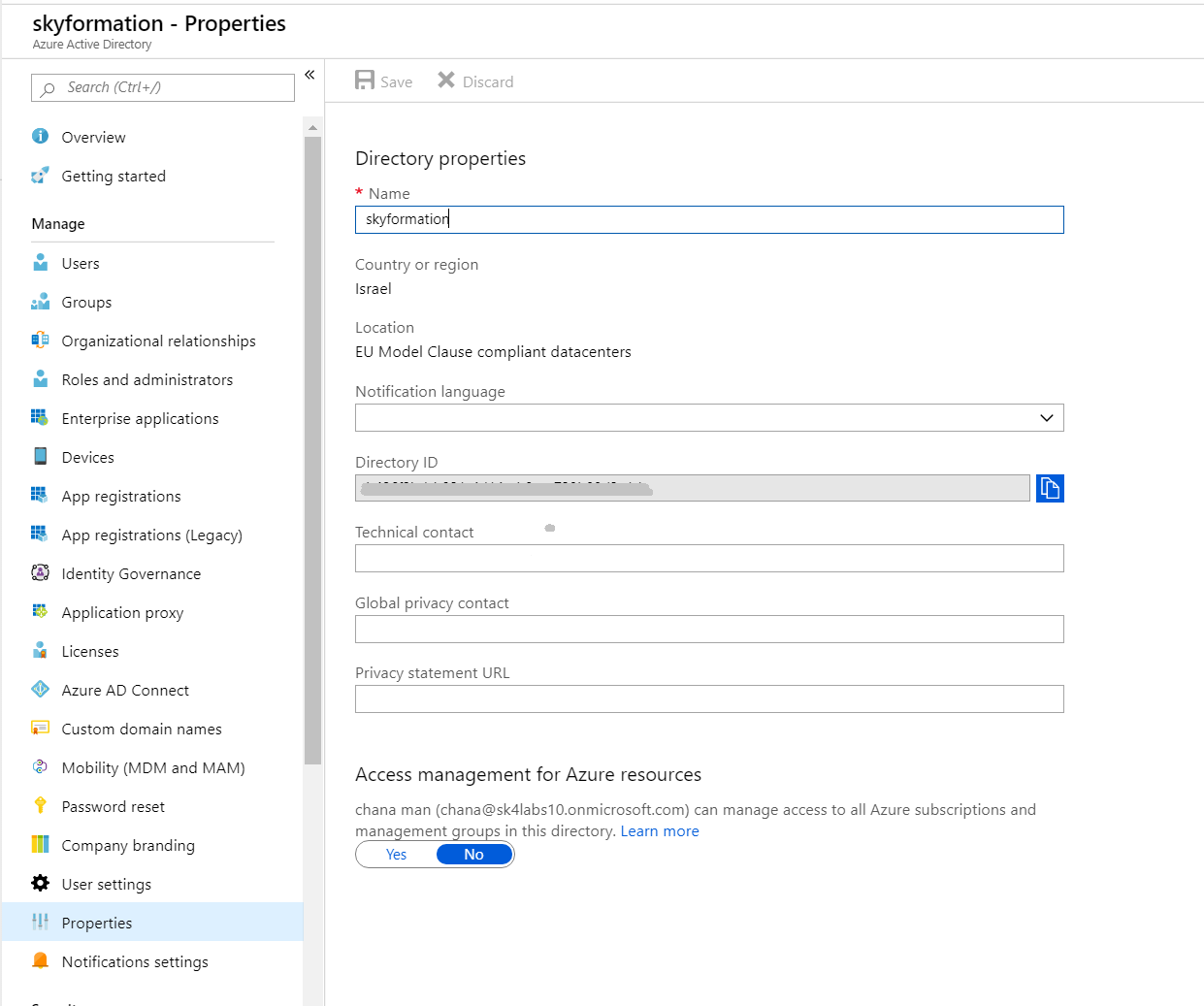
Navigate to App registrations, create a new app by clicking + New registration.
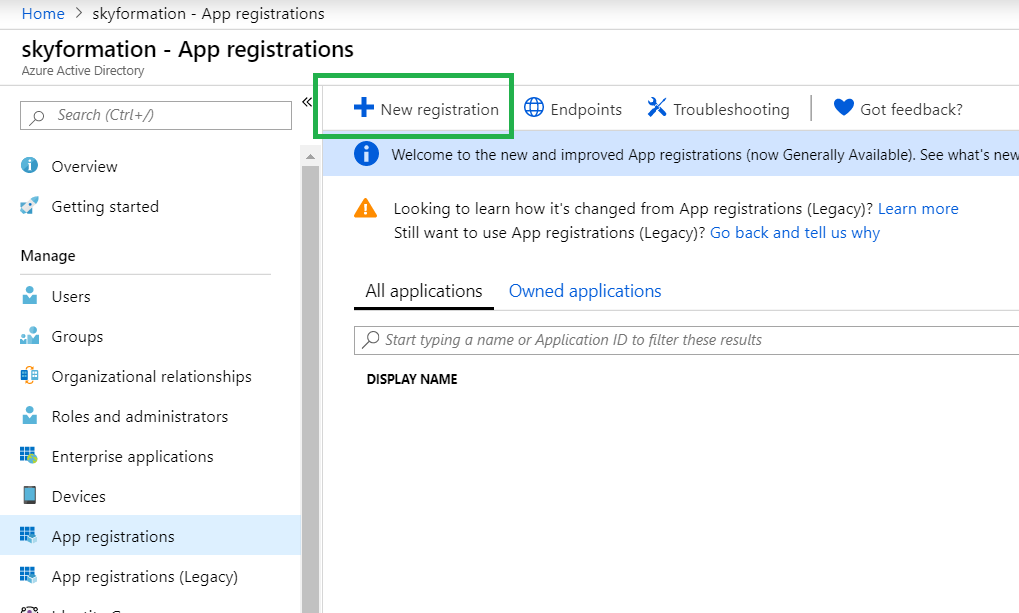
Enter the application details:
Name – ExabeamApp
Supported account types – Choose Accounts in this organizational directory only ([Your organization ID])
Click Register.
From the page of the just created app keep aside the value of Application ID (Client ID).
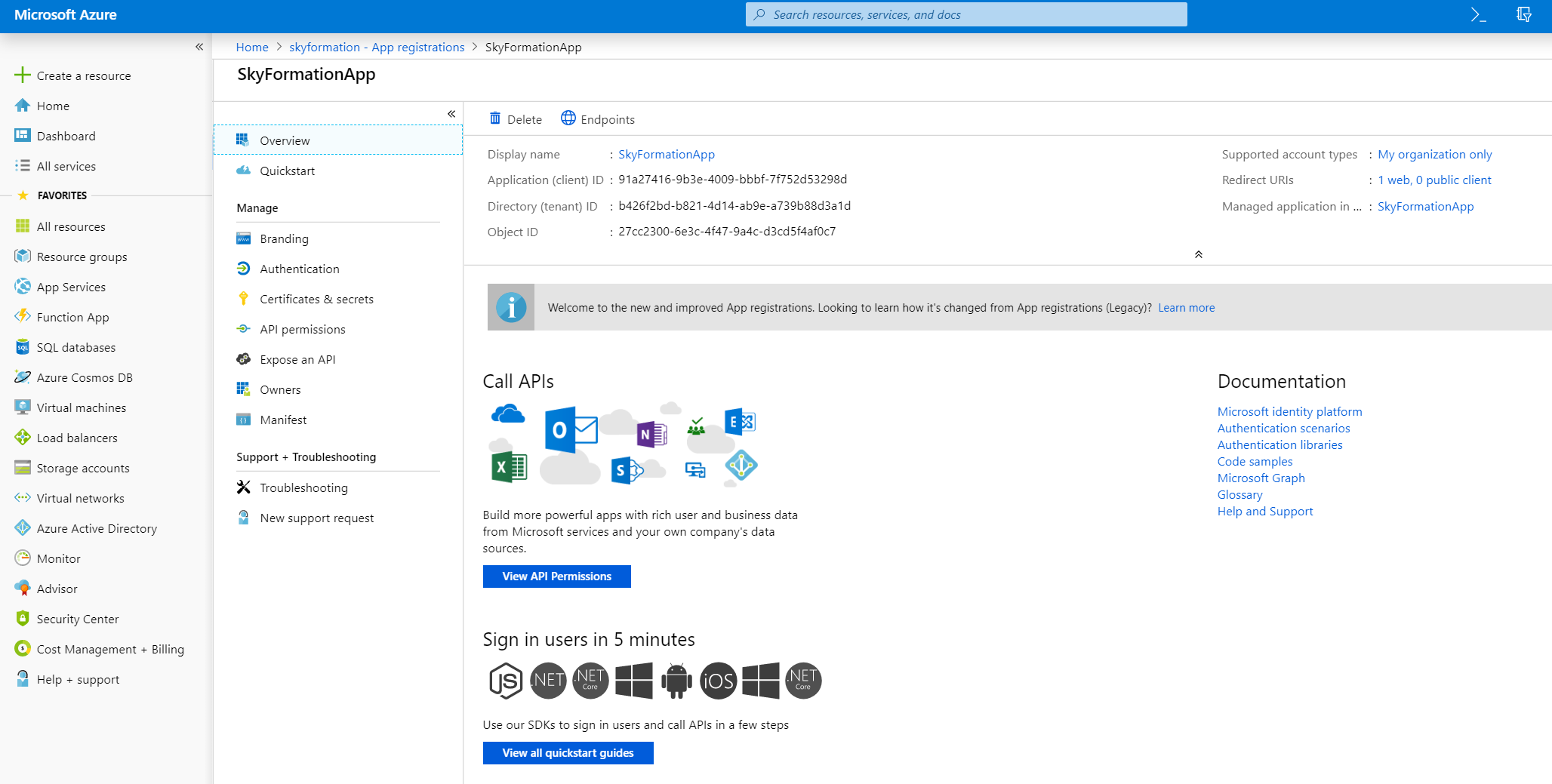
Navigate to Certificates & secrets from the just created app page.
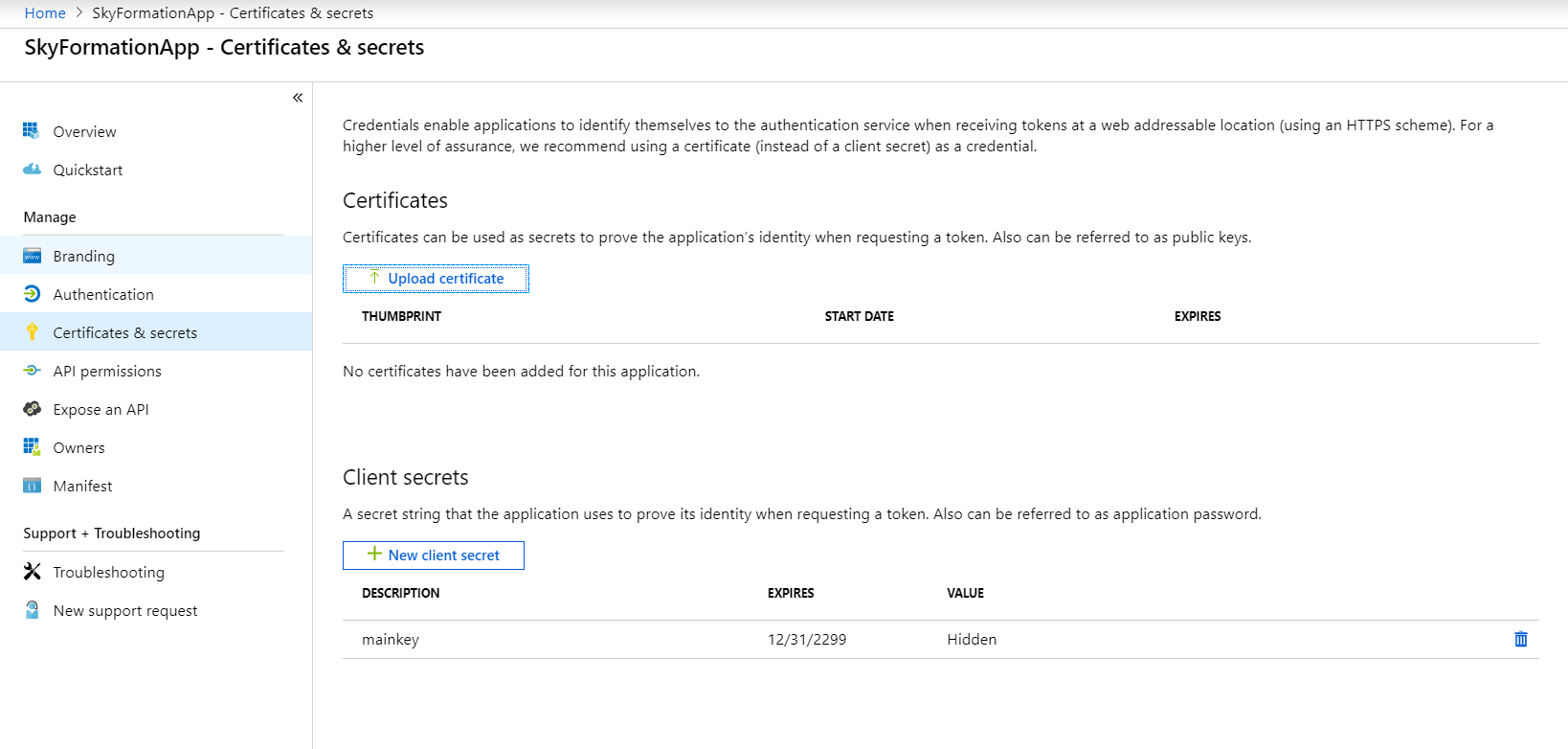
Choose an authentication method. Starting with Exabeam Cloud Connectors 2.4.108, two authentication methods are available: oauth2 and certificate. If you select the authentication method OAuth2, add a client secret. If you select the authentication method Certification, upload a certificate for the app.
Add permissions for the application by navigating to API Permissions in the app page.
In the API Permissions, Add a permission > Select an API.
Add the app permissions to according to the below table (for example Microsoft Graph API).
Verify the needed permissions to the API according to the below table (for example in the Application permissions select the
read all users full profilespermission).Repeat this for each permission needed in the API page.
Click Add permissions.
Repeat the above step for each API you need to add permissions according to the following table.
API
Permission
Microsoft Graph
Directory.Read.All
Group.Read.All
User.Read.All
SecurityEvents.Read.All
Note
For Exabeam Cloud Connectors 2.4.254 and later releases, additionally grant the Application the SecurityEvents.Read.All permission for Graph Security Alerts endpoint. For example:
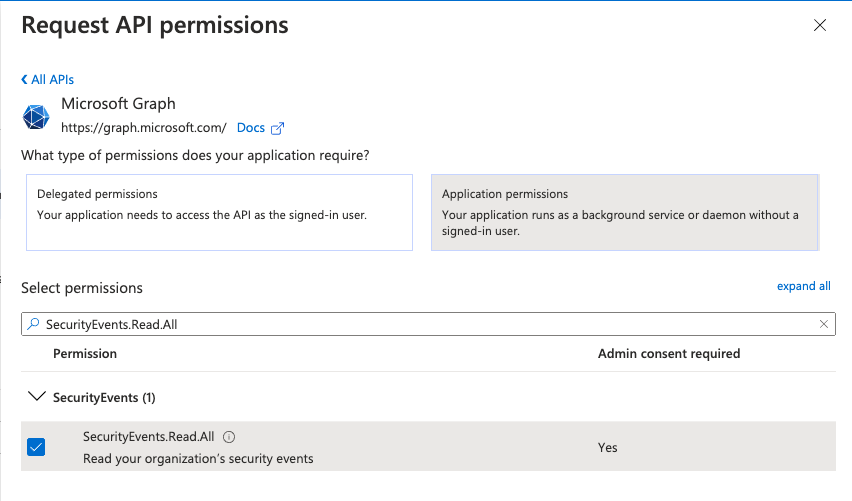
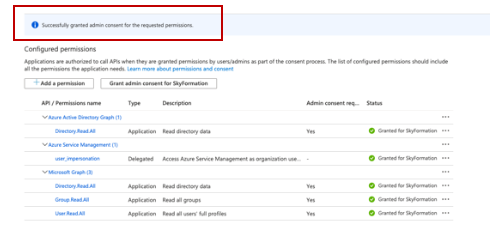
Grant admin consent to save all the permissions.
Make sure you see a message that verifies the permissions were successfully granted.
Navigate to Subscriptions in the Main Azure services menu by searching for
Subscriptionsin the All Services page.Select a subscription that you want to monitor (you need to repeat the below process for each subscription you want the Exabeam Azure Cloud Connector to monitor).
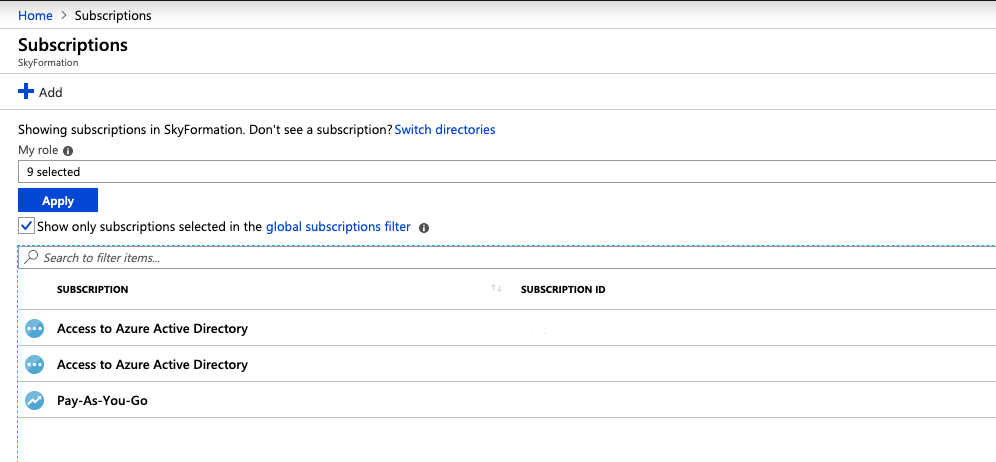
Assign roles and a subscription scope to the application, one of the following:
Option 1: Set minimal permissions via CLI/PowerShell
Create a JSON file with minimal permissions.
Make sure to:
Assign in the last row all the IDs of the subscriptions that you want to attach.
Make sure NOT to suffix the subscription ID with trailing / character
{ "Name":"SK4 FlowLogs", "IsCustom":true, "Description":"SkyFormation role for pulling flow logs.", "Actions":[ "Microsoft.Storage/storageAccounts/listKeys/action", "Microsoft.Network/networkWatchers/queryFlowLogStatus/action" ], "NotActions":[ ], "DataActions":[ ], "NotDataActions":[ ], "AssignableScopes":[ "/subscriptions/<id>" ] }
Option 2: Assign roles manually
The Azure built-in roles are more permissive than required, but the below are the minimal subset that contain the required permissions
On the Access control (IAM) page, in the left pane, click Access control (IAM).
Note
If the UI shows an error where it states the user does not have permission to set permissions, it could be caused by either:
The user is not an administrator of the Subscription.
The subscription was generated by Office365. This is a bug with Office365. To overcome it create a new Subscription. Free or Pay-As-You-Go is sufficient.
Click Add.
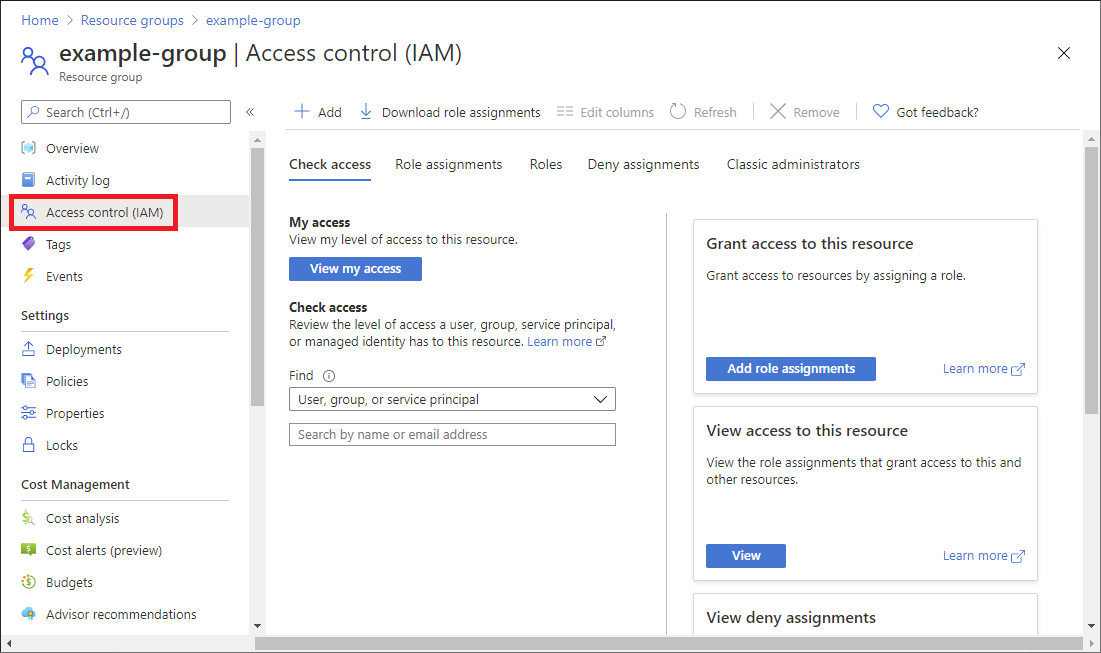
On the Add role assignment page, in the search box search for the following roles:
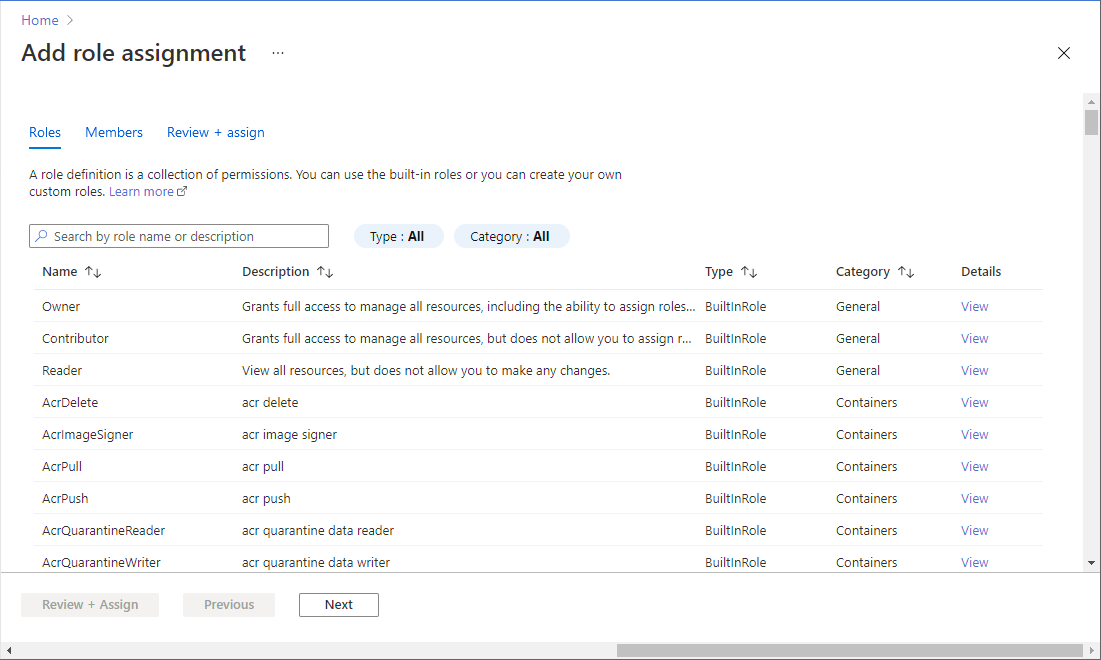
Note
The Network Contributor and Storage Account Contributor roles are required for the Storage Analytics and NSG flow logs endpoints. The Cloud Connectors app will only read from any data source and never make any changes. The only reason we require these roles is because Azure does not have equivalent 'Reader' role for network and storage, only contributor.
Log Analytics Reader
Network Contributor
Storage Account Contributor
For each role that you select, perform the following steps. For example, this procedure lists the steps for the role Log Analytics.
Click the role, in this case, Log Analytics.
Click Next.
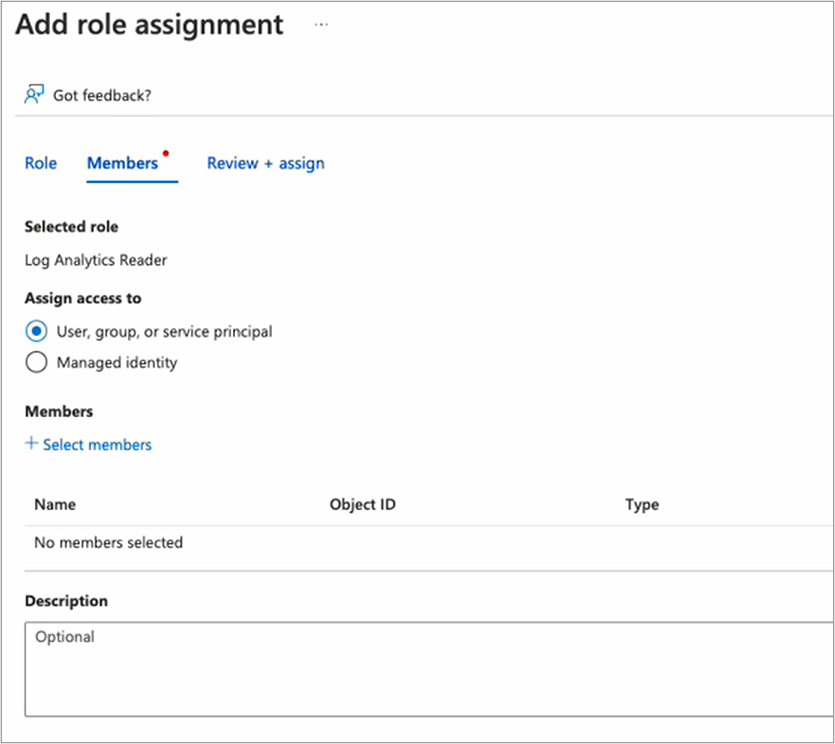
In the Assign access to section select the User, group, or service principal option.
Click Select Members.
Enter the name of the added Azure app name. For example: AzureAuditSK4. Then click the app name and click Select.
Click Next. The app name with object ID appears.
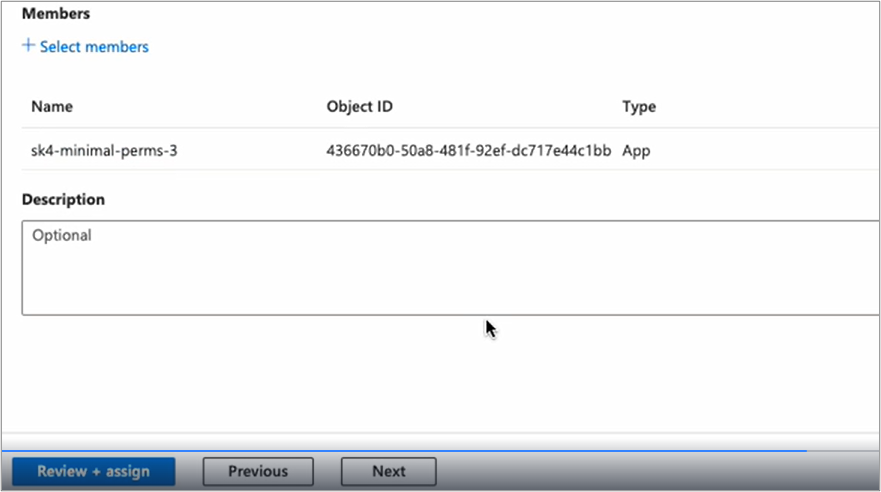
Click Next.
Click Review + Assign.
Navigate back to the Access control (IAM) page to verify the role assignment.
Proceed to Configure the Azure Cloud Connector and have the following information handy:
Client ID of your newly created Azure app
Your tenant ID and generated secret ID
Add Client Secret for Authentication Method OAuth2
For the authentication method OAuth2:
In the Azure portal, navigate to Azure Active Directory > App registrations.
Select the application that you created.
Navigate to Certificates & secrets.
In the Client secrets area, click New client secret.
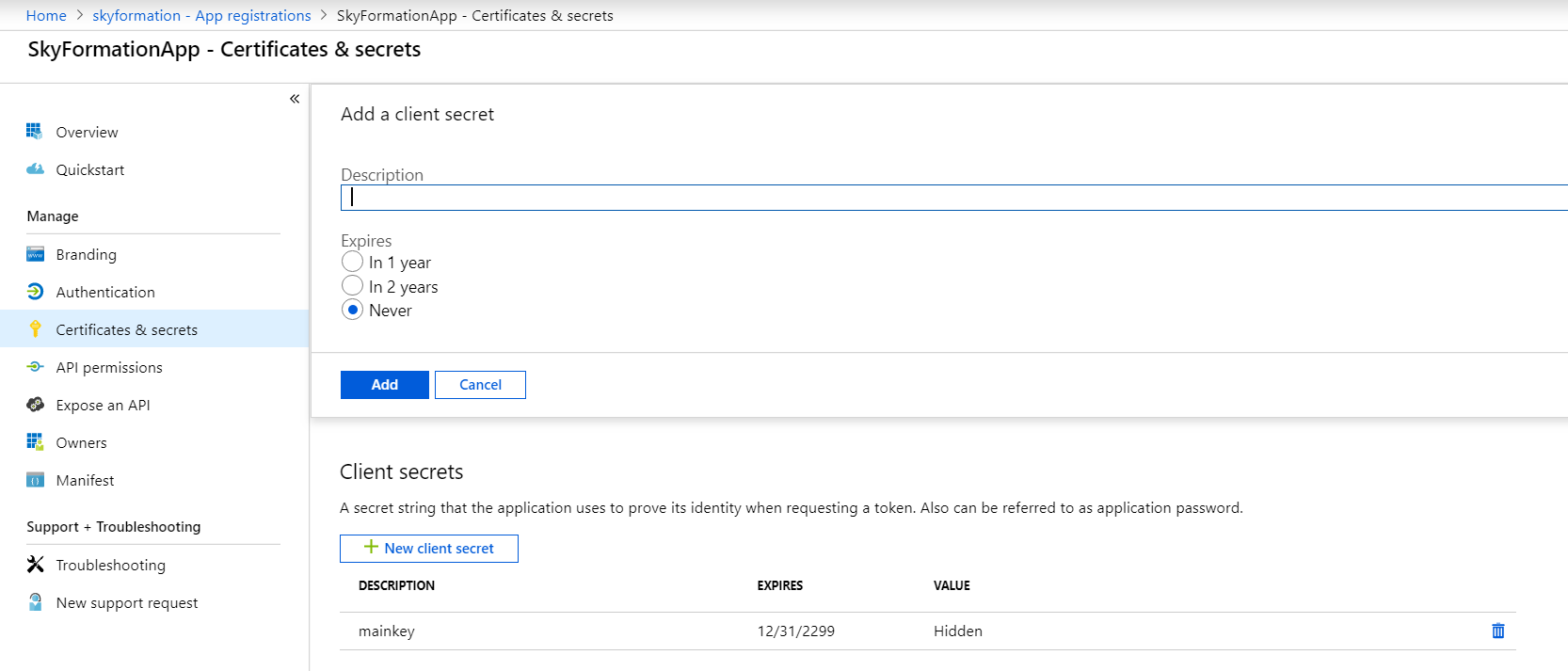
Provide a relevant description for the key and select Never for the expiration.
Click Add.
The Client secrets section displays the client secret value in the Value column.
Copy the value for client secret.
Note
You must note the value immediately after you add the new client secret, otherwise you can’t retrieve the value after leaving the page. If you select the authentication method OAuth2, use the value, represented by a string of letters and numbers, to configure the Office 365 cloud connector.
Upload a Certificate for Authentication Method Certificate
In the Azure portal, navigate to Azure Active Directory > App registrations.
Select the application that you created.
Navigate to the Certificates & secrets section.
If you don't already have the certificate and private key files, create them.
Generate the X.509 asymmetric key by running the following command in the terminal:
openssl req -newkey rsa:2048 -nodes -keyout key.pem -x509 -days 3650 -out certificate.pem
Two files are created in the directory where you ran the command:
certificate.pem - The certificate or public key
key.pem - The private key
In the Certificates area, click Upload certificate.
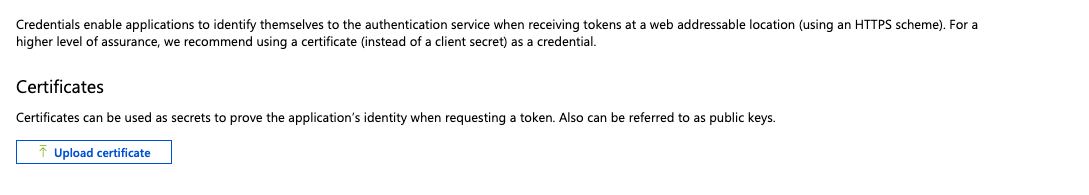
Select a file and browse to the folder where the certificate file is saved and upload the certificate.pem file. Then click Add.
Configure the Azure Cloud Connector
Ensure that you have satisfied the Prerequisites to Configure the Azure Cloud Connector.
Log in to the Exabeam Cloud Connectors platform with your registered credentials.
Navigate to Settings > Accounts > Add Account.
Click Select Service to Add, then select Azure from the list.
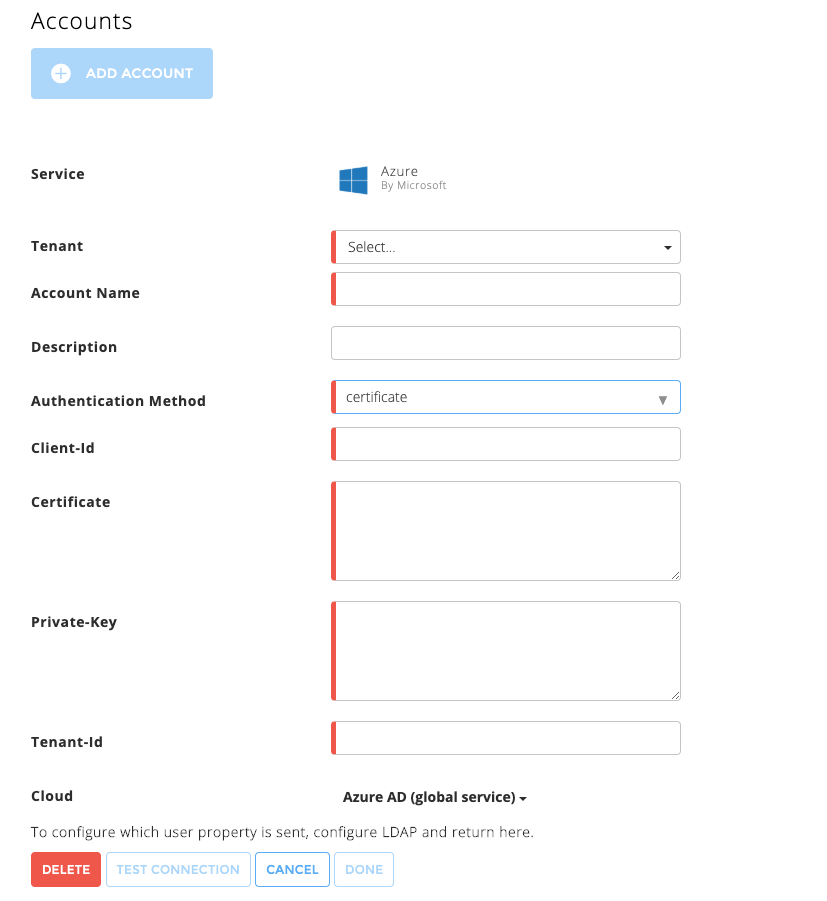
Fill in the following information:
Account Name – Provide this cloud connector a meaningful name. Exabeam uses this name to identify the cloud connector across the Exabeam Cloud Connectors platform and in entire events sent by your connector to your SIEM/Log/Splunk system. For example,
Corp Azure staging cloud.Description – Enter any text that describes the specific cloud connector function and provides meaning for your organization. For example,
corporate Azure cloud environment for staging.Authentication Method – Either oauth2 or certificate.
Client-id – Enter the client ID you generated during the prerequisite steps. For example, 4e11ab22-6d1c-5077-9d73-f7776d3851e8.
Client-Secret – (OAuth2 authentication only) Enter the client secret you obtained during the prerequisite steps. For example, W17FnTeyRWUasdTGBdVeB+A3kASDaYUH0lre+MzuxRT=
Certificate – (Certificate authentication only) The content of the certificate file you obtained during the prerequisite steps. For example:
-----BEGIN CERTIFICATE----- ***************** ***************** ***************** ..... -----END CERTIFICATE-----
Private Key – (Certificate authentication only) The content of the private file you obtained during the prerequisite steps. For example:
-----BEGIN PRIVATE KEY----- ************** ************** ************** ..... -----END PRIVATE KEY-----
Tenant-id – The Azure tenant ID you obtained during the prerequisite steps. For example, 3d70c501-bb21-1122-9330-c4a25e252086.
Cloud (support Azure National Clouds)
Warning
This field should only be changed from its default Azure AD (global service) if your Azure is deployed in one of the Azure National Clouds : China, Germany, or US Government.
To set your Azure National cloud in use please choose the one from the dropdown list:
Azure AD (global service) – Default
Azure AD China operated by 21Vianet
Azure AD Germany
Azure AD for US Government
To confirm that the Exabeam Cloud Connector platform communicates with the service, click Test Connection.
Click Done to save your changes. The cloud connector is now set up on the Exabeam Cloud Connector platform.
To ensure that the connector is ready to send and collect data, Start the connector and check that the status shows
OK.(Optional) Collect EventHub Information for Azure EventHub Endpoints.
(Optional) To modify the data collected from Azure Log Analytics (a.k.a ALA, OMS Workspaces), edit the base search query for each:
Click EDIT for the Azure account, find the section for the ALA by its name, and then replace the default query ("search *") with the desired search query.
Make sure not to add limitation to the TimeGenerated column. This is added by the connector itself to build time buckets for its syncs.
Make sure that the output of your query contains the TimeGenerated column.
You can use any query, including saved functions built and save in the workspace
(Optional) Collect all Microsoft Defender ATP Events.
(Optional) Configure Azure to Monitor Security Center Events in Azure VMs.
Collect EventHub Information for Azure EventHub Endpoints
Use this workflow to collect the needed information to add an EventHub endpoint to your existing Exabeam Azure Cloud Connector.
Review the following network requirements for Azure EventHub endpoints:
For each EventHub namespace that needs to be monitored, outgoing connectivity to <eventhub namespace>.servicebus.windows.net.
In versions prior to 2.5.86 - ports 5671, 5672
In versions 2.5.86 onward - port 9093
Note the name of the consumer group of the EventHub:
Navigate to the EventHubs namespace in which the EventHub with the data you want to retrieve resides.
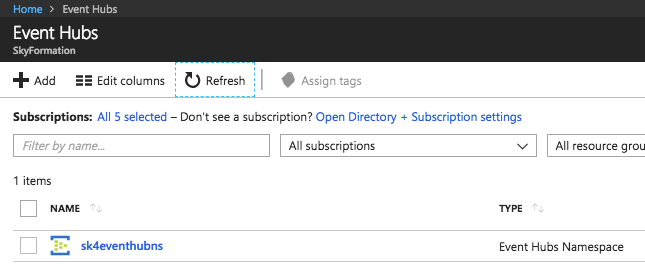
Select the EventHub where your data to retrieve resides.
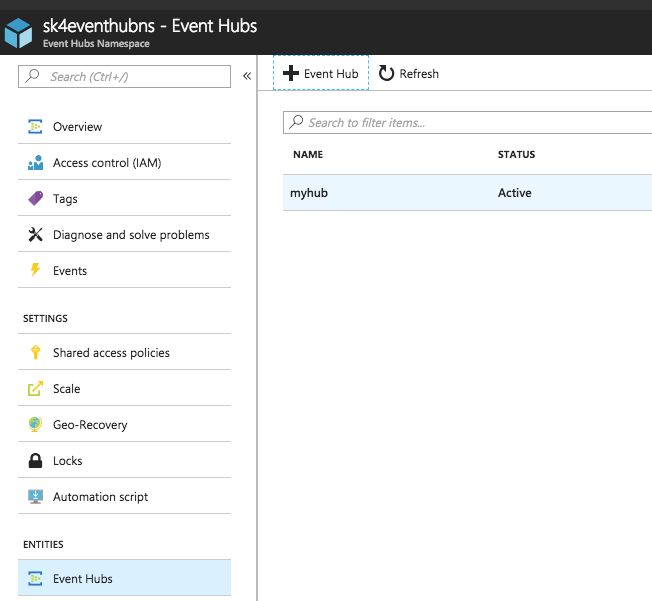
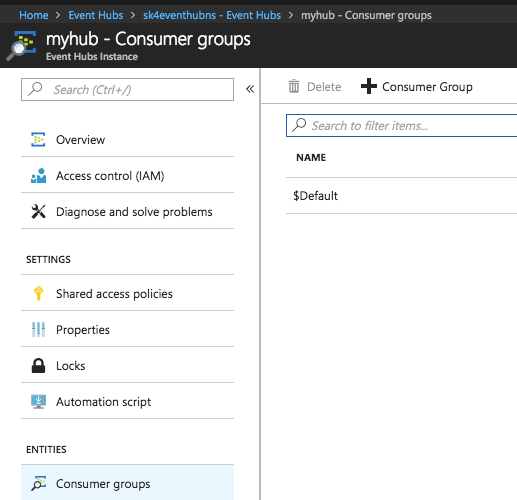
Navigate to Consumer groups to get the name of the consumer group.
If only Exabeam is going to read data from the EventHub then you can use the default consumer group, otherwise create a dedicated consumer group for Exabeam.
Note
A consumer group is how Azure keeps track of which data was consumed, sort of like a queue. So if two consumers are using the same consumer group, both will miss data.
Create a SAS token with listen-only permissions for Exabeam to use:
In the EventHub navigate to Shared access policies.
+ Add a new Policy In the Add SAS Policy screen and enable the Listen permission.
Provide a descriptive name for the token (i.e. listenonly) and then click Create when done.
After you see the Creating SAS Policy successful message, enter the policy you just created and take a note of:
The SAS policy name
The Primary key value
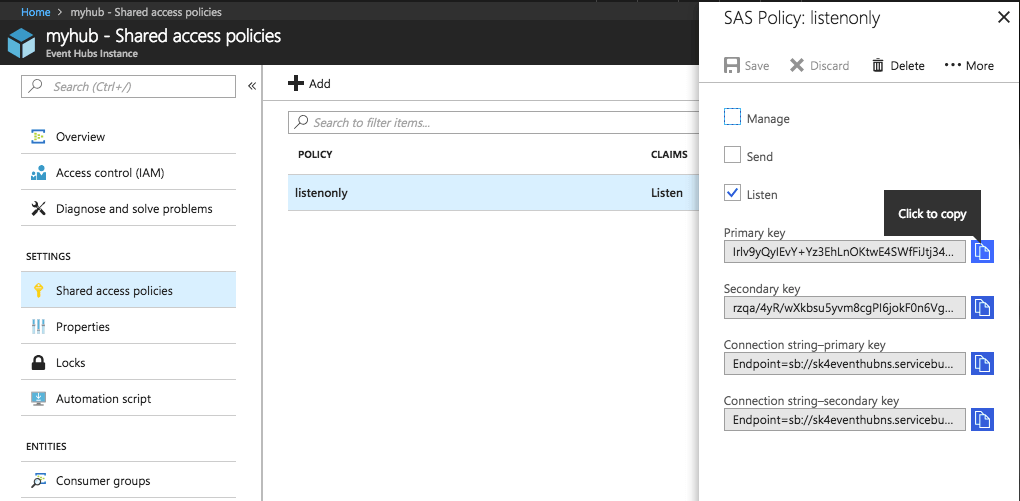
You are ready to configure your Exabeam EventHub endpoint in an existing Exabeam Azure Cloud Connector.
Collect all Microsoft Defender ATP Events
Microsoft Defender Advanced Threat Protection is a platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats. For more information about Microsoft Defender Advanced Threat Protection, see the Microsoft documentation.
If your organization utilizes this tool, you can ingest its data into your SIEM for various reasons.
To collect only the alerts generated by Defender ATP then use the Azure Connector's Security Center endpoint.
To facilitate collection of the Microsoft Defender ATP events, Stream the Events to Azure Event Hub and Use the Azure Connector for Collection.
Stream the Events to Azure Event Hub and Use the Azure Connector for Collection
This method utilizes the Microsoft Defender ATP capability to stream its events to Azure Event Hub.
See the Microsoft documentation to set up event streaming to a dedicated Azure Event Hub.
If you already have an Azure connector set up in your Cloud Connectors instance to collect data from the subscription in which the Event Hub was set up, force it to refresh it’s list of Event Hubs in your Azure deployment. If you do not have an Azure connector setup, Configure the Azure Cloud Connector to onboard it,
From Exabeam Cloud Connectors, stop the Azure Cloud Connector: Go to Settings > Accounts and then click STOP on the relevant Azure Cloud Connector
Wait 1 minute and then START the connector.
It takes about 5 minutes for the connector to explore your deployment and identify all Event Hubs.
Collect EventHub Information for Azure EventHub Endpoints.
Record the information such as Consumer Group Name and shared access key name and value as you will need them to complete the following step.
Configure Azure EventHub endpoint in an existing Azure Cloud Connector.
In the connector configuration, select event type Pass-thru to onboard the Event Hub to which the Microsoft Defender ATP events are streamed.
Click Edit on the Azure account that monitors the subscription with the EventHub.
In the section that describes your EventHubs list, supply the Consumer Group Name, Data Type (Pass-thru), SharedAccessKeyName, and SharedAccessKey.
Start the Event Hub endpoint in the Azure Cloud Connector.
Configure Azure to Monitor Security Center Events in Azure VMs
Using Azure services you might be running Virtual Machines with Windows or Linux OS. In this case, you can configure the Azure Security Center to collect Security Events from the VMs of your choice and storm them the Security Events in Azure workspace of your choice. Azure can then forward OS Security Events as Windows Security Events to any SIEM. If you configured an Azure Cloud Connector, the connector will automatically collect all events collected into the Azure workspace and forward them to the SIEM configured in Exabeam Cloud Connectors for the specific connector.
Security Events ingested by the Azure Cloud Connector will be ingested as a generic event and forwarded to your SIEM of choice as-is for the SIEM to perform its Security Events parsing and modeling.
To configure Azure Security Center to Collect the Security Events from the relevant VMs:
Open the Azure Security Center page from the Azure portal.
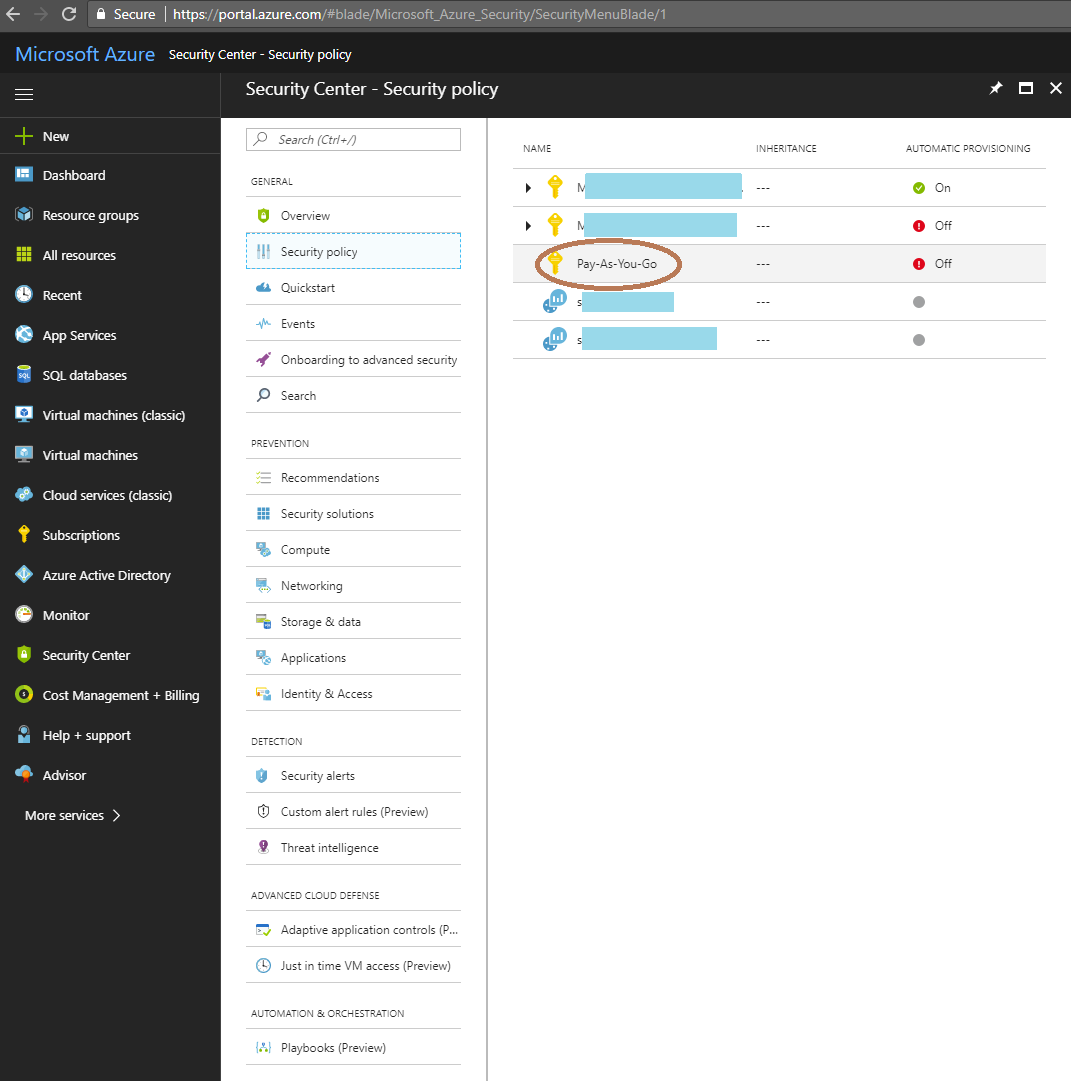
Go to the Security Policy page.
On this page you can choose the Azure subscription(s) for which you want to collect Security Events from its VMs.
In this example we will choose the subscription named
Pay as You Goand set the VMs to collect Security Events automatically. In addition, the AUTOMATIC PROVISION status is Off in our subscription, which indicates the Security Events will not be collected automatically for all VMs in the subscription.Click on the subscription you want to configure for automatic data collection of Security Events.
Enable Automatic provisioning of monitoring agent.
This installs the Azure agent on all the VMs in the subscription, which in turn will start collecting the Security Events. If you only want to collect Security Events from specific VMs, you can choose the specific resource(s) in the previous page under the relevant subscription.
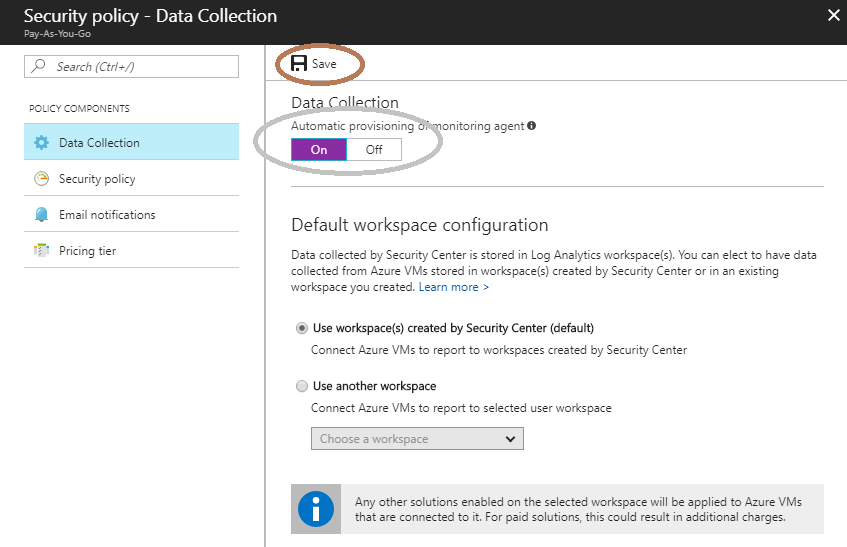
Choose the workspace in which you want to store the collected events.
The Azure Cloud Connector will ingest all the events from any workspace available at the Azure connector monitored, hence choosing a Workspace other then the default Security Center is only for your internal Azure administrative needs.
Save your changes.
Azure provisions its agents to all the VMs in the subscription you configured and starts collecting existing, historical, and any future Security Events.
Configure the Azure Cloud Connector to Ingest the new Security Events.
The Azure Cloud Connector will ingest all the events from any workspace in the monitored Azure account. As a result, make sure that you on-boarded a Azure Cloud Connector that monitors the specific Azure account.
