- Get Started with Threat Detection Management
- Analytics Rules
- Analytics Rule Classifications
- Create an Analytics Rule
- 1. Define the analytics rule
- 2. Import the analytics rule
- 3. Enable the analytics rule
- 4. Apply the analytics rule to your environment
- factFeature Analytics Rule JSON Configuration
- profiledFeature Analytics Rule JSON Configurationh
- contextFeature Analytics Rule JSON Configuration
- numericCountProfiledFeature Analytics Rule JSON Configuration
- numericDistinctCountProfiledFeature Analytics Rule JSON Configuration
- numericSumProfiledFeature Analytics Rule JSON Configuration
- Manage Analytics Rules
- Tune Analytics Rules
- Share Analytics Rules
- Troubleshoot Analytics Rules
- Analytics Rules Syntax
- Advanced Analytics Rule Syntax vs. Analytics Rule Syntax
- Logical Expressions in Analytics Rule Syntax
- String Operations Using Analytics Rule Syntax
- Integer Operations Using Analytics Rule Syntax
- Time Operations Using Analytics Rule Syntax
- Network Operations Using Analytics Rule Syntax
- Context Operations Using Analytics Rule Syntax
- Entity Operations Using Analytics Rule Syntax
- Correlation Rule Operations Using Analytics Rule Syntax
- Monitor the Analytics Engine
- Correlation Rules
- Threat Scoring
numericSumProfiledFeature Analytics Rule JSON Configuration
As you define a numericSumProfiledFeature analytics rule, review the structure and required fields for a numericSumProfiledFeature analytics rule.
Let's look at an example JSON configuration for a numericSumProfiledFeature analytics rule:
{
"version":"1",
"ruleDefinitions": [
{
"templateId": "DM-NumSP-EMR-Bytes-DU-Bytes",
"name": "Abnormal amount of bytes received in incoming emails for this user",
"description": "An abnormal amount of bytes have been received in incoming emails for this user.",
"applicableEvents": [
{
"activity_type": "email-receive",
"outcome": "success"
}
],
"detectionReason": "Abnormal amount (${trigger.numeric_value}) of bytes received in incoming emails for ${entity.user.dest}",
"type": "numericSumProfiledFeature",
"mitre": [
{
"techniqueKey": "T1566",
"technique": "Phishing",
"tactic": "Initial Access",
"tacticKey": "TA0001"
}
],
"useCases": [
"Phishing"
],
"scopeValue": "EntityId('type: User && direction: Dest')",
"featureValue": "bytes",
"trainOnCondition": "exists(bytes, vendor)",
"actOnCondition": "true",
"anomalyThreshold": "90 days",
"checkScopeMaturity": "true",
"maturityThreshold": "14 days",
"windowDuration": "1 day",
"windowPeriod": "12 hours",
"logBase": 2,
"minOrderOfMagnitude": 17.0,
"query": "(activity_type = \"email-receive\" AND outcome = \"success\") AND (dest_user_entity_id = \"${trigger.scope_value}\") AND (NOT bytes = null)",
"familyId": "email-receive-activity",
"ruleGroupId": "emailr-bytes-sum-magnitude-group"
}
}
}An analytics rule is a JSON object that includes two mandatory fields: version and ruleDefinitions.
version indicates the layout version. It tracks the layout version if there are any updates to the layout or the New-Scale Security Operations Platform. Currently, the version is 1.
ruleDefinitions contains one or more rule definitions. The value of ruleDefinitions is an array. The array contains an object, and each object is a rule definition. The rule definition contains the fields that define an analytics rule and how it functions. Some fields are mandatory for the analytics rule to function while other fields are optional.
Ensure you include all necessary fields for your analytics rule to work as you expect and ensure all field values meet the requirements for a numericSumProfiledFeature rule:
Field | Description | Mandatory or Optional | Value Requirements |
|---|---|---|---|
templateId | A unique identifier associated with the analytics rule. | Mandatory |
|
name | The analytics rule name. | Mandatory |
|
description | A description of the analytics rule. | Optional |
|
applicableEvents | The type of events the analytics rule evaluates. | Mandatory |
|
detectionReason | A dynamic name describing the rule and why it triggered on a specific event. It elaborates on the 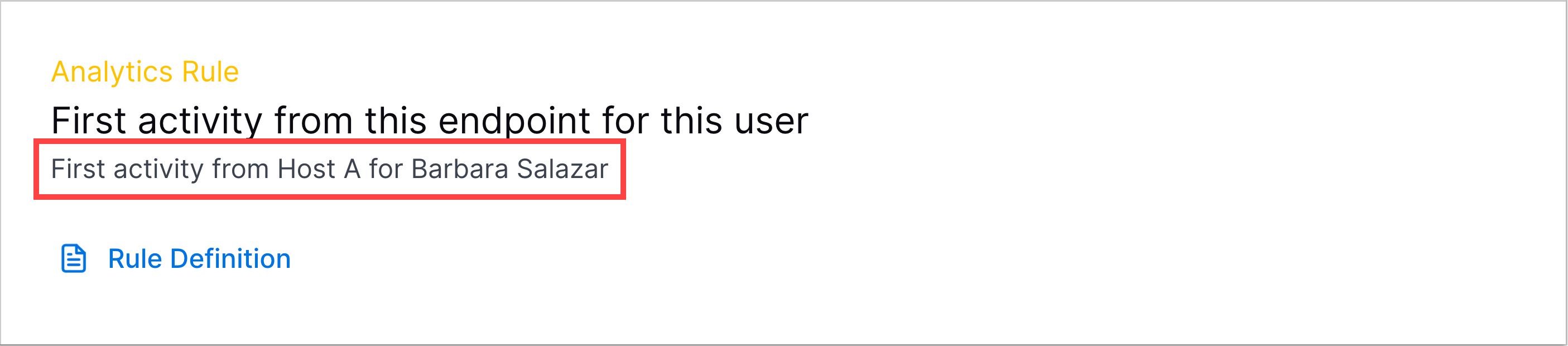 | Mandatory |
|
type | The analytics rule type. | Mandatory |
|
mitre | The MITRE ATT&CK® tactics and techniques associated with the analytics rule. | Optional |
|
useCases | Exabeam use case associated with the analytics rule. | Optional | Must be an array of strings. Each string must be an existing Exabeam use case:
|
scopeValue | The event field on which the model for the analytics rule trains; typically an object or entity. | Mandatory |
|
featureValue | The event field on which the model for the analytics rule trains for the scopeValue. For example, if scopeValue is hostname and featureValue is process, the model trains on the behavior of processes executed on hostnames. | Mandatory |
|
trainOnCondition | The events on which the analytics rule trains. | Mandatory |
|
actOnCondition | A high-level filter for the events on which the analytics rule triggers. | Mandatory |
|
scoreUnless | A list of analytics rules. If any analytics rule in the list triggers, the given analytics rule doesn't trigger. | Optional |
|
anomalyThreshold | The period of time the model for the analytics rule remembers and trains on an observed data point. After this period, the model forgets the data point and the analytics rule can trigger on the data point again. | Mandatory |
|
checkScopeMaturity | Whether the rule should learn more about the entities defined in | Optional |
|
maturityThreshold | The duration of the training period for | Optional |
|
countPer | What of the For example, you can use You use | Optional |
|
windowDuration | The duration of the summing period. | Mandatory |
|
windowPeriod | How often the rule evaluates events during the period defined in | Mandatory |
|
logBase | The log base value used to calculate the minimum count of a given behavior considered anomalous in relation to a previous trigger. The analytics engine uses an exponential function to determine when the count of a given behavior is considered anomalous. With an exponential function, the count of a given behavior must be ever increasing to be considered anomalous. For example, let's say the analytics rule counts number of emails a user sends. The analytics rule triggers when a user sends 10 emails. If the user sends 12 emails, you may not want the analytics rule to trigger again because 12 emails is not unusual compared to 10 emails. However, if the user sends 30 emails, you may consider this behavior anomalous, and you may want the analytics rule to trigger again. With a higher With a lower | Mandatory |
|
minOrderOfMagnitude | The count of a given behavior up to which the analytics rule considers normal and never triggers, as a factor of the For example, let's say the analytics rule counts number of emails a user sends. If the | Mandatory |
|
query | A query that retrieves the specific events that triggered the analytics rule. In many cases, The events retrieved using | Mandatory |
|
familyId | The analytics rule family to which the rule belongs. | Mandatory |
|
ruleGroupId | The analytics rule group to which the rule belongs. | Mandatory |
|