- 2026 Release Notes
- 2025 Release Notes
- December 2025
- November 2025
- October 2025
- September 2025
- August 2025
- July 2025
- June 2025
- May 2025
- April 2025
- March 2025
- February 2025
- January 2025
- Known Issues
December 2025
The New-Scale Security Operations Platform includes the following addressed features and new features for December 2025.
Attack Surface Insights
Feature | Description |
|---|---|
User Entity Linking Using Custom Context Tables | To ensure related identities are accurately unified under a single user entity, you can now control how Attack Surface Insights links identities to entities by defining relationships in a new customizable pre-built context table, the User Entity Links context table. By default, the User Entity Links context table has four columns: KeyType1, Key1, KeyType2, and Key2. You can configure these columns and add data to the context table, either programmatically using APIs or manually. Attack Surface Insights prioritizes enriching user entities with context data from the User Entity Links context data first, alongside Microsoft Active Directory and before any other context source. |
Extended Entity Deletion Window | To more easily maintain entities over the long term, you now have a larger window to delete obsolete entities. You can now delete entities created in the past 1,000 days. |
User Entity Details Event ID Hover Enhancement | To better understand all the events associated with a user entity, you can now hover over the Event ID field to view the events that created a user entity and their accounts. To navigate to all events associated with a user entity in Search, you can now click Find in search. To copy all associated event IDs to your clipboard, you can now click Copy to clipboard. 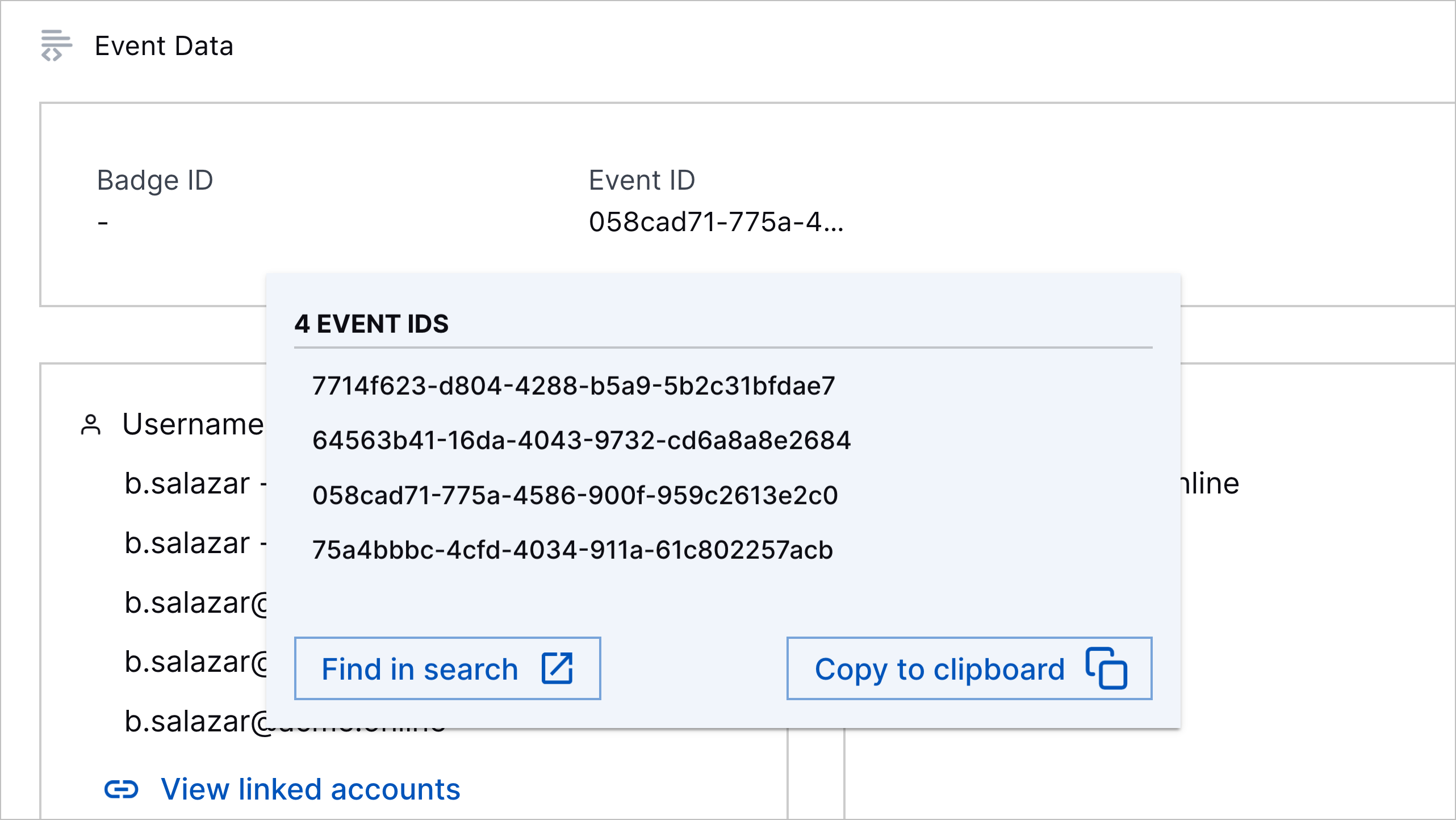 |
Cloud Collectors
Feature | Description |
|---|---|
Azure Blob Storage Cloud Collector | The Azure Blob Storage Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of the logs from Azure data sources such as threat detections, security alerts, and defender OTP logs. |
Azure Virtual Network Flow Cloud Collector | The Azure Virtual Network Flow Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of the virtual network flow logs. |
Gemini Enterprise Cloud Collector | The Gemini Enterprise Cloud Collector is now available as part of Cloud Collectors to facilitate ingestion of the Model Armor prompts logs of Gemini Enterprise Apps via GCP Pub/Sub topic. |
Early Access Collectors | |
Gmail BigQuery Cloud Collector | The Gmail BigQuery Cloud Collector is now available as part of Cloud Collectors Early Access program, to facilitate ingestion of the gmail logs. The early access program offers you an opportunity to gain access to the latest cloud collectors before their official release. To participate, see Sign Up for the Early Access Program. |
Context Management
Feature | Description |
|---|---|
New Attack Surface Insights Context Table | Context Management now provides a new pre-built Attack Surface Insights context table. The new table is the User Entity Links context table. It supports the detection and enrichment rule activities of of the Attack Surface Insights application by providing mapping information for custom user entities. For more information about Attack Surface Insights context tables, see Pre-Built Detection Context Tables in the Context Management Guide. |
New Condition Operators Available for Filtered Tables | Additional condition options have been made available for creating a custom filtered context table in Context Management. Previously, data could only be filtered based on whether is was equal to or contained in a specific value. Now the set of available filtering operators are expanded to include all of the following:
For more information about filtered context tables, see Working with Filtered Context Tables in the Context Management Guide. |
Correlation Rules
Feature | Description |
|---|---|
Granular Correlation Rule Detection Grouping by Detection ID | You can now create a unique case for each correlation rule detection using a detection grouping rule. Detection grouping rules can now group correlation rule detections into a case by their detection ID, a unique identifier assigned to a detection when it's created. 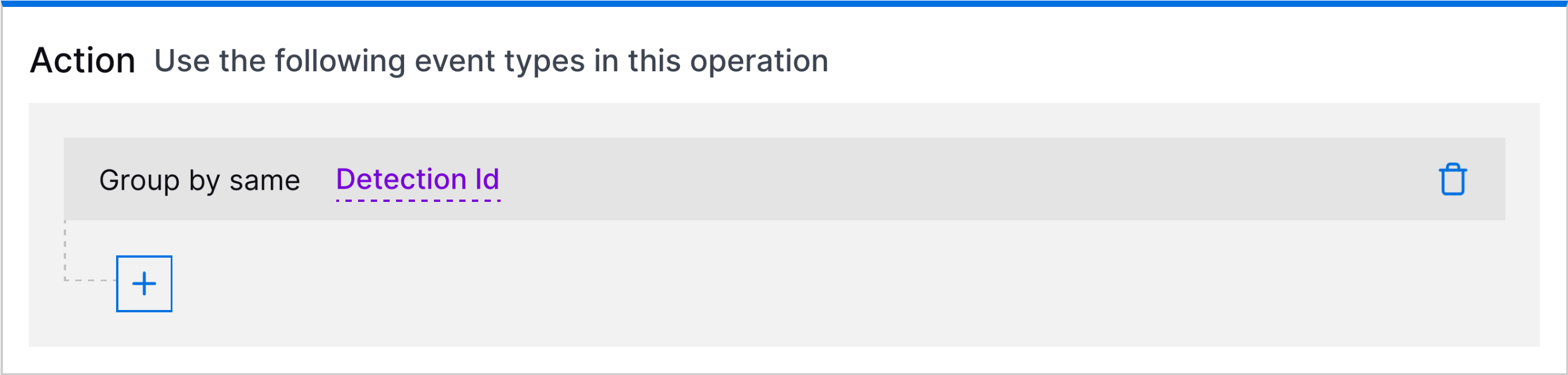 If you're grouping detections by detection ID, the only additional field by which you can group detections is rule name. |
Log Sources
Feature | Description |
|---|---|
Enhancements to the Log Source Policy | You can now use the following enhancements for Log Source policies:
|
Log Stream
Feature | Description |
|---|---|
Enhanced Host to IP Enrichment | New-Scale Host to IP enrichment has been enhanced so that the default condition covers an expanded set of filters. It now includes all of the mapping functionality that was available in Advanced Analytics static mapping. In addition, early access opportunities are available to customize the enrichment condition or to exclude specific entities from the enrichment process. See the note below. For more information about this type of enrichment, see Host to IP Enrichment in the Log Stream Guide. NoteEarly Access Opportunity An early access opportunity is available to customize the host to IP enrichment functionality. You may want to take advantage of this opportunity if any of the following reasons apply to your environment:
If you would like to take advantage of this early access customization, email the following group: [email protected]. |
New-Scale Platform
Feature | Description |
|---|---|
Global Token Revocation | When editing or adding a new identity provider, you can now enable Global Token Revocation (Universal Logout) when using Auth0 with Okta Workforce Identity. With Global Token Revocation, if a user is logged out with the identity provider, such as during an admin-initiated logout or a security event, they will also be logged out of all applications, including Exabeam. For more information, see Set up Okta as your Identity Provider in the New-Scale Security Operations Platform Administration Guide. |
Webhook View Details | When viewing the details of a webhook with a large amount of recent calls, the dialog could take a long time to load or fail to load the responses entirely. Now, only the 10 most recent responses are displayed over the last 48 hours to ensure no issues with loading the View Details dialogue for webhooks. For more information, see View Details/Edit a Webhook in the New-Scale Security Operations Platform Administration Guide. |
Search
Feature | Description |
|---|---|
Improvements to the Timeline View of Search Results | The layout and functional behavior of the Timeline view of search results has been enhanced to both reduce visual noise and make the investigational workflow more intuitive. For easier scanning and to provide a more streamlined view of events, the display of parsed fields can be toggled on and off from an option at the top of the results list. In addition, fewer clicks are now needed to drill into events and detection when looking for detailed information. For more information, see Timeline View of Search Results in the Search Guide. |
Increased in Storage Retention for Some Licenses | Default search retention has been extended from 31 days to 45 days for customers using New-Scale Analytics and New-Scale Fusion licenses. For information about the storage capacity available for your specific license, see Exabeam Product Entitlements. For more information about different types of storage, see Log Retention in the Search Guide. |
Threat Center
Feature | Description |
|---|---|
Granular Correlation Rule Detection Grouping by Detection ID | You can now create a unique case for each correlation rule detection using a detection grouping rule. Detection grouping rules can now group correlation rule detections into a case by their detection ID, a unique identifier assigned to a detection when it's created.  If you're grouping detections by detection ID, the only additional field by which you can group detections is rule name. |
New Case Global Notification Enhancement | To ensure you can immediately access important case information from anywhere, you can now get more detailed Threat Center global notifications when a case is created. Global notifications sent when a case is created now include:
|
Threat Detection Management
Feature | Description |
|---|---|
Analytics Rules Insights | To troubleshoot over-triggering analytics rules, you can now view suggestions for exclusion expressions that reduce noise for the analytics engine and prevent them from over-triggering. The analytics engine automatically generates the suggestions during training. The COMPATIBILITY column has been renamed the RULE INSIGHTS column. Under the RULE INSIGHTS column, an analytics rule that is most likely to generate false positives is marked as having Insights. 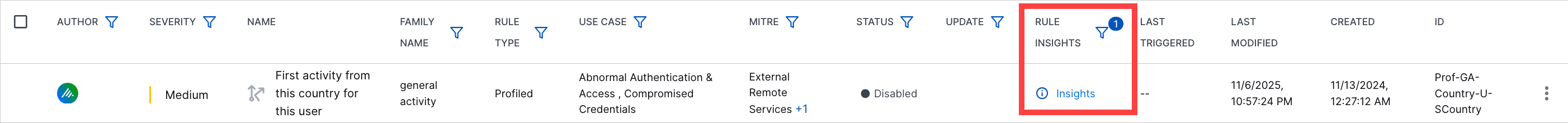 To view suggested exclusion expressions for the analytics rule, click Insights. You can then copy the exclusion expression and use it to create an exclusion for the analytics rule. If there are no suggested exclusions available, a message suggests that you review the analytics rule. 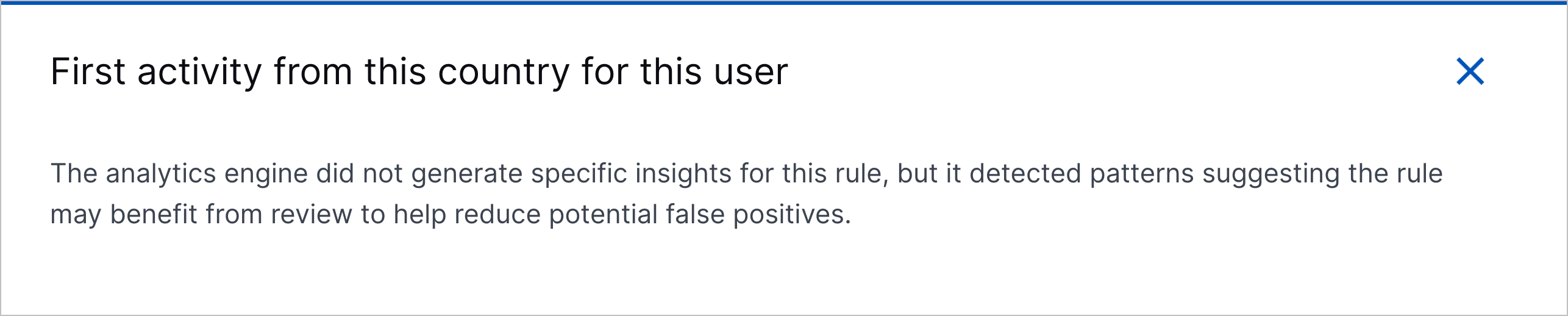 |
JSON Configuration in Analytics Rule Details | To copy or reference the JSON configuration of an analytics rule, you can now view the JSON configuration under the JSON tab in the analytics rule details. 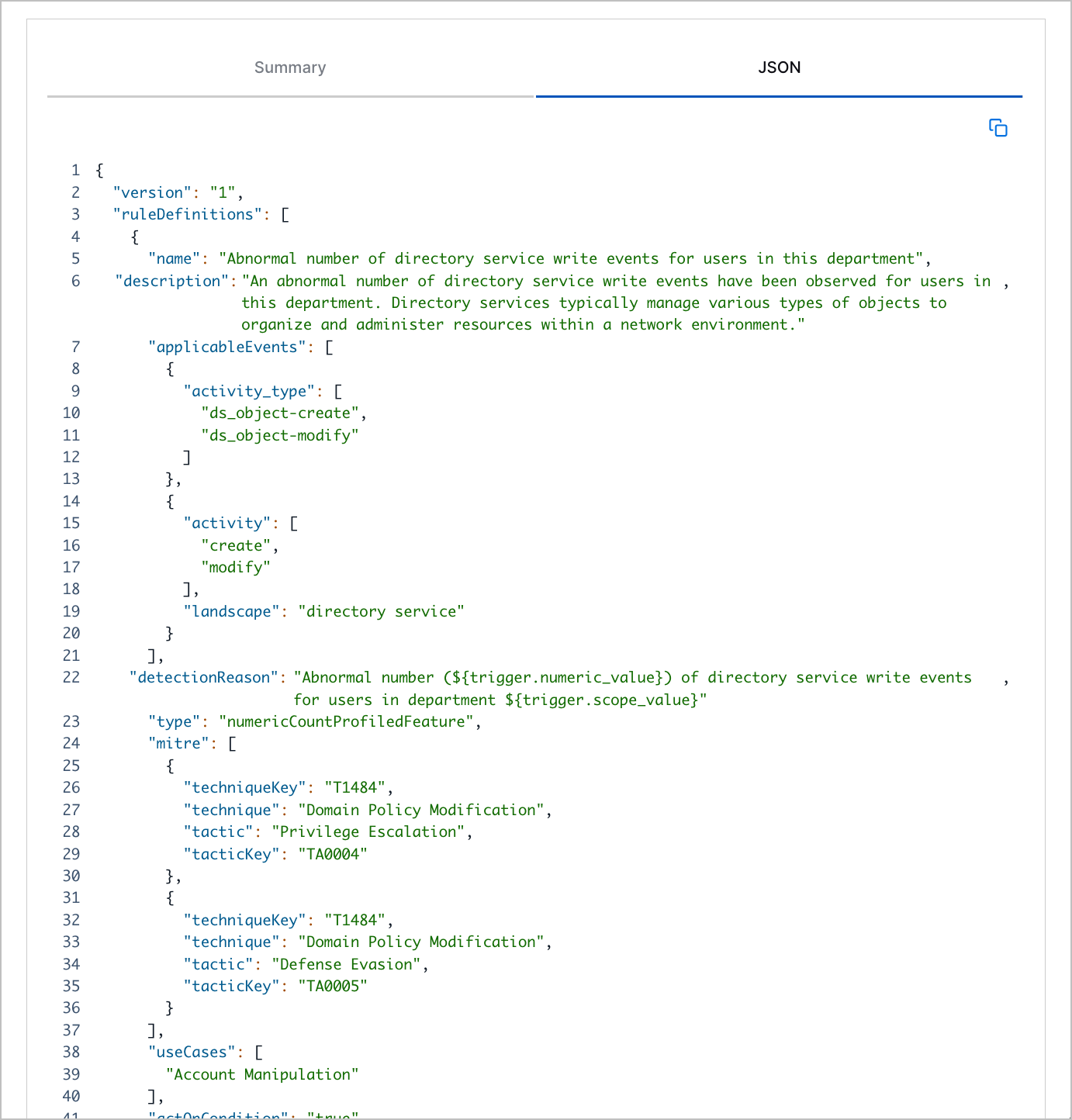 |
Required Event Fields in Analytics Rule Details | To determine if events have the necessary fields for an analytics rule to trigger, you can now review those required fields under REQUIRED EVENT FIELDS in the analytics rule details. This list of fields is automatically generated and used by Outcomes Navigator to calculate coverage scores. 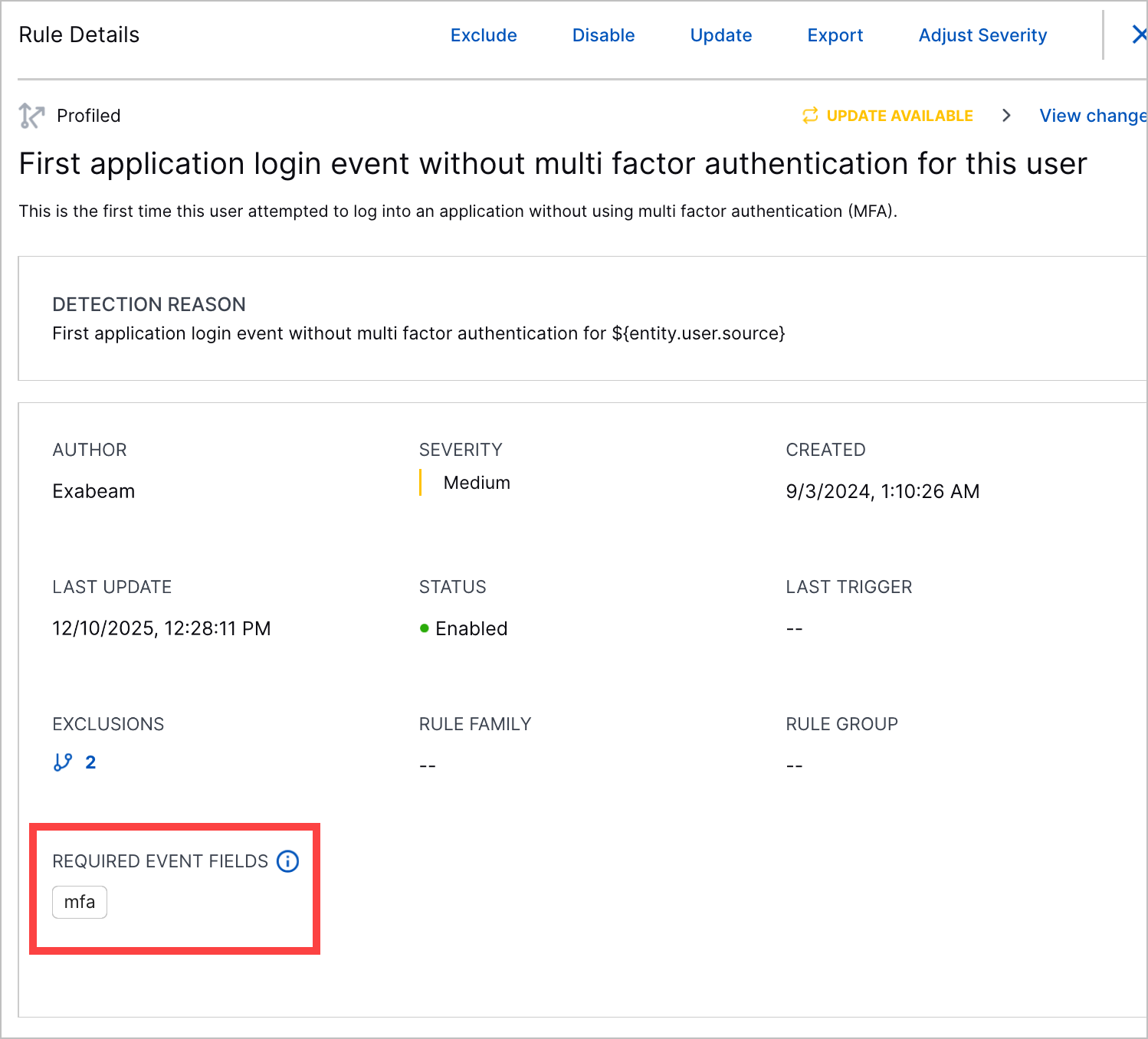 |
Prerequisite for Enabling and Deleting Exclusions | To prevent changes to exclusions from inadvertently retraining analytics rules, you can no longer enable or delete exclusions while you have pending analytics rule changes. You must apply or revert the pending changes first. If there are any pending changes, you receive an error. 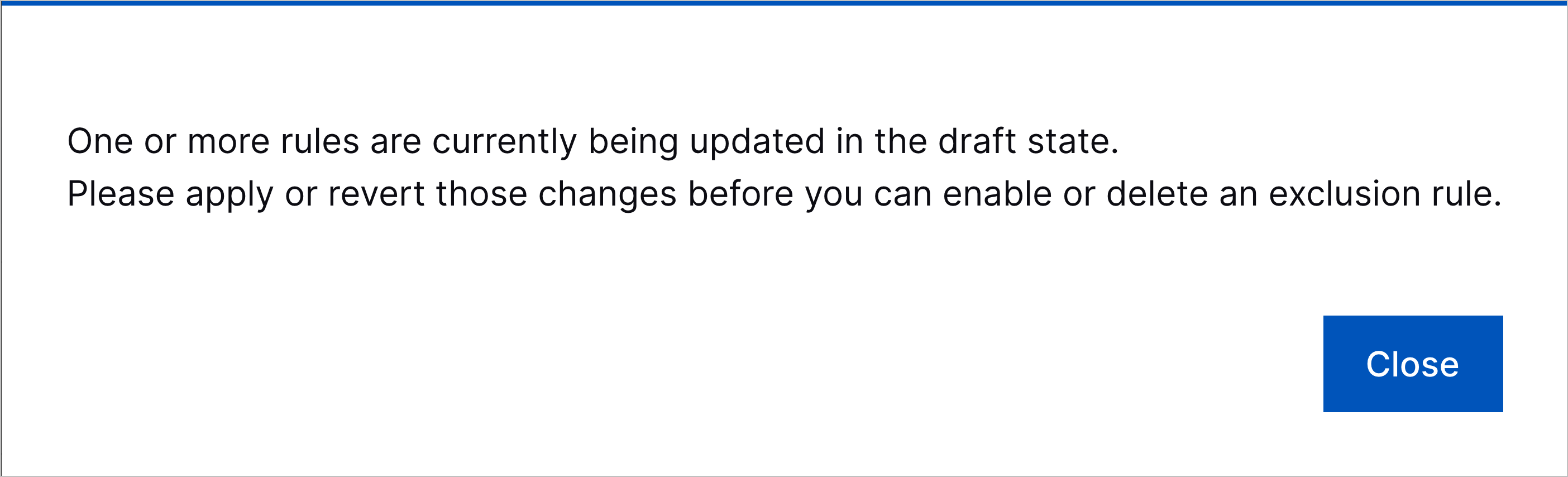 |
Granular Correlation Rule Detection Grouping by Detection ID | You can now create a unique case for each correlation rule detection using a detection grouping rule. Detection grouping rules can now group correlation rule detections into a case by their detection ID, a unique identifier assigned to a detection when it's created.  If you're grouping detections by detection ID, the only additional field by which you can group detections is rule name. |
New and Updated Pre-Built Analytics Rules | You can now better detect defense evasion, persistence, privilege escalation, and reconnaissance with new and updated analytics rules. New pre-built analytics rules include:
Pre-built analytics rules for which
Pre-built analytics rules for which
Pre-built analytics rules for which
Pre-built analytics rules for which
Pre-built analytics rules for which
Pre-built analytics rules for which
Pre-built analytics rules for which
Pre-built analytics rules for which
Removed obsolete pre-built analytics include:
|
