- Get Started with Threat Detection Management
- Analytics Rules
- Analytics Rule Classifications
- Create an Analytics Rule
- 1. Define the analytics rule
- 2. Import the analytics rule
- 3. Enable the analytics rule
- 4. Apply the analytics rule to your environment
- factFeature Analytics Rule JSON Configuration
- profiledFeature Analytics Rule JSON Configurationh
- contextFeature Analytics Rule JSON Configuration
- numericCountProfiledFeature Analytics Rule JSON Configuration
- numericDistinctCountProfiledFeature Analytics Rule JSON Configuration
- numericSumProfiledFeature Analytics Rule JSON Configuration
- Manage Analytics Rules
- Tune Analytics Rules
- Share Analytics Rules
- Troubleshoot Analytics Rules
- Analytics Rules Syntax
- Advanced Analytics Rule Syntax vs. Analytics Rule Syntax
- Logical Expressions in Analytics Rule Syntax
- String Operations Using Analytics Rule Syntax
- Integer Operations Using Analytics Rule Syntax
- Time Operations Using Analytics Rule Syntax
- Network Operations Using Analytics Rule Syntax
- Context Operations Using Analytics Rule Syntax
- Entity Operations Using Analytics Rule Syntax
- Correlation Rule Operations Using Analytics Rule Syntax
- Monitor the Analytics Engine
- Correlation Rules
- Threat Scoring
factFeature Analytics Rule JSON Configuration
As you define a factFeature analytics rule, review the structure and required fields for a factFeature analytics rule.
Let's look at an example JSON configuration for a factFeature analytics rule:
{
"version":"1",
"ruleDefinitions": [
{
"templateId": "DM-Fact-BPM-Public-AccessBlock",
"name": "Public access block was removed from an AWS bucket",
"description": "The public access block of a bucket or an account in AWS was modified to remove public access prevention. This activity enables the bucket or the entire account to become public to all users.",
"applicableEvents": [
{
"activity_type": "bucket-accessblock-modify",
"platform": "AWS"
}
],
"detectionReason": "The public access block of bucket ${event.bucket_name} was removed",
"type": "factFeature",
"mitre": [
{
"techniqueKey": "T1530",
"technique": "Data from Cloud Storage",
"tactic": "Collection",
"tacticKey": "TA0009"
}
],
"useCases": [
"Cloud Data Protection"
],
"trainOnCondition": "true",
"actOnCondition": "containsAny(toLower(operation), 'putbucketpublicaccessblock', 'putaccountpublicaccessblock') && (toLower(restrict_public_buckets)='false' || toLower(block_public_policy)='false' || toLower(block_public_acls)='false' || toLower(ignore_public_acls)='false')",
"value": "true",
"suppressThreshold": "10 minutes",
"suppressScope": "
"scoreUnless": [
"Prof-WinSC-E-O-DE"
],
"familyId": "bucket-permission-modification-activity",
"ruleGroupId": "bpm-public-group"
}
]
}An analytics rule is a JSON object that includes two mandatory fields: version and ruleDefinitions.
version indicates the layout version. It tracks the layout version if there are any updates to the layout or the New-Scale Security Operations Platform. Currently, the version is 1.
ruleDefinitions contains one or more rule definitions. The value of ruleDefinitions is an array. The array contains an object, and each object is a rule definition. The rule definition contains the fields that define an analytics rule and how it functions. Some fields are mandatory for the analytics rule to function while other fields are optional.
Ensure you include all necessary fields for your analytics rule to work as you expect and ensure all field values meet the requirements for a factFeature rule:
Field | Description | Mandatory or Optional | Value Requirements |
|---|---|---|---|
templateId | A unique identifier associated with the analytics rule. | Mandatory |
|
name | The analytics rule name. | Mandatory |
|
description | A description of the analytics rule. | Optional |
|
applicableEvents | The type of events the analytics rule evaluates. | Mandatory |
|
detectionReason | A dynamic name describing the rule and why it triggered on a specific event. It elaborates on the 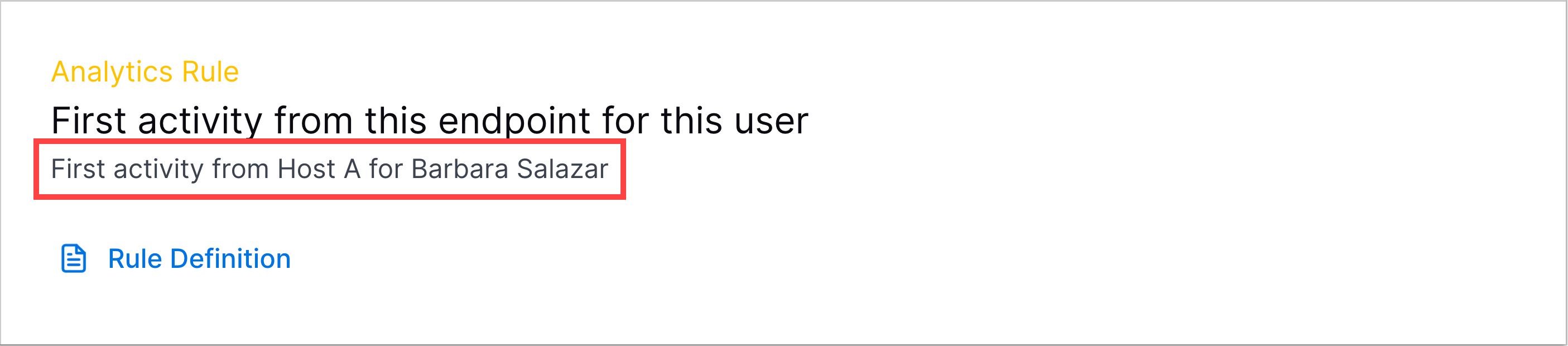 | Mandatory |
|
type | The analytics rule type. | Mandatory |
|
mitre | The MITRE ATT&CK® tactics and techniques associated with the analytics rule. | Optional |
|
useCases | Exabeam use case associated with the analytics rule. | Optional | Must be an array of strings. Each string must be an existing Exabeam use case:
|
trainOnCondition | The events on which the analytics rule trains. | Optional |
|
actOnCondition | A high-level filter for the events on which the analytics rule triggers. | Optional |
|
value | The expression used to evaluate whether the conditions required for the rule to trigger are true. | Mandatory |
|
suppressThreshold | How long the analytics rule is suppressed after it's first triggered. When a rule over-triggers, it creates noise, can indicate it's detecting false positives, and cause alert fatigue. To prevent the analytics rule from over-triggering, you can suppress the rule from triggering repeatedly. For example, if you set | Mandatory |
|
suppressScope | The field value on which the analytics rule is suppressed from triggering. To prevent the analytics rule from over-triggering, you can suppress the rule from triggering repeatedly on the values of a specified field. For example, you can suppress the rule from over-triggering on a specific user or an entire network. When the analytics rule is suppressed, it triggers on the first event with a specific field value but is suppressed for all subsequent events with the same field value. | Optional |
|
scoreUnless | A list of analytics rules. If any analytics rule in the list triggers, the given analytics rule doesn't trigger. | Optional |
|
familyId | The analytics rule family to which the rule belongs. | Mandatory |
|
ruleGroupId | The analytics rule group to which the rule belongs. | Mandatory |
|