- Dashboards
- Navigation Overview
- View and Interact with Dashboards
- View and Interact with Visualizations
- User Management
- Configure and Manage Dashboards
- Create a Dashboard
- Add a Visualization to a Dashboard
- Add a Text Tile
- Modify a Dashboard Layout
- Add Dashboard Filters
- Manage Automatic Refresh Rates
- Create a Scheduled Report
- Make a Dashboard Public
- Export and Import Dashboards
- Edit Dashboard Filters
- Edit Dashboard Details
- Duplicate a Dashboard
- Delete a Dashboard
- Configure and Manage Visualizations
- Create a Visualization
- Auto-Create a Visualization from a Natural Language Prompt
- Create a Visualization from a Search Query
- Add Visualizations from the Library to a Dashboard
- Modify a Visualization
- Configure Visualization Query Filters
- Include Context Filtering in Visualizations
- Make a Visualization Public
- Export and Import Visualizations
- Duplicate a Visualization
- Remove a Visualization from a Dashboard
- Delete Visualizations from the Library
- Configure and Manage Scheduled Reports
- Pre-Built Dashboards
- Advanced Analytics Dashboards
- AI/LLM Dashboards
- Case Manager Dashboards
- Compliance Dashboards
- Correlation Rules Dashboards
- Event Store Dashboards
- Access Grant and Revoke Activity
- Account Logout Summary
- Account Management Activity
- Application Security Event Summary
- Authenticated User Accounts on Hosts
- AWS CloudTrail Summary
- Data Loss Prevention Activity – Host-Based
- Data Loss Prevention Activity – User-Based
- Data Loss Prevention Activity Summary
- Default Account Access
- Default Credential Usage and Change Activity
- Denied Web Access Activity
- Disabled User Account Summary
- Discovered Attacks by Source and Destination
- Endpoint Detection and Response
- Failed Application Logon Activity
- Failed Audit Logs Summary
- Failed Host Login Attempt Counts by Users
- Failed VPN Login Attempts and Remote Session Timeouts
- Firewall Activity
- Firewall and Router Device Interfaces
- Insecure Authentication Attempts
- IOC Statistics
- Log Delay Insights
- Microsoft 365 Summary
- Microsoft Windows Overview
- Network Applications by Traffic Volume
- Policy Activity Summary
- Ports Usage Trend
- Privileged Access
- Privileged Access – User-Based
- Project Collateral
- Protocols by Network Traffic
- Remote Session Overview
- Security Alert Summary – Impacted Hosts
- Security Alert Summary – Origin Hosts
- Security Alert Summary – Users
- Successful Application Logon Activity
- Successful Database Login Activity
- Successful Physical Access
- Top Attackers
- User Account Creation Summary
- User Account Lockout Activity
- Vendor Authentication Activity
- Windows Audit Failure Summary by Hosts
- Windows Audit Failure Summary by Users
- Windows User Privilege Elevation
- Zscaler HTTP Dashboard
- Security Operations Center Management Dashboards
- Threat Center Dashboards
- Pre-Built Visualizations
- Anomalies - Use Case & MITRE Coverage
- Anomalies by Rule Name
- Anomalies by Use Case
- Anomalies Count Over Time
- Anomaly Distribution by MITRE Tactic & Score
- Application Count
- Closed Incidents
- Correlation Rules by Severity
- Correlation Rules Triggered Over Time
- Detected Anomalies
- Host-Based DLP Alerts Count
- Incidents Created
- Incident Summary by Incident Type
- Number of Hosts with DLP Alerts
- SOC Incident Distribution
- Top 5 Host-Based DLP Alert Categories
- Top 5 Protocols in Host-Based DLP Alerts
- Top 10 Host-Based DLP Alert Types
- Top 10 Hosts with DLP Alerts
- Top Activities per Top 10 Applications
- Top Users per Top 10 Applications
- Trend of Application Security Events
Correlation Rules
The Correlation Rules Management pre-built dashboard provides visibility into use case activity levels, what rules are being triggered and when, and what rules are triggered the least.
Dashboard Filters
You can filter the dashboard by trigger time, rule severity, and trigger count.
To set the filters:
Click the drop-down icon on the right.

Do any of the following:
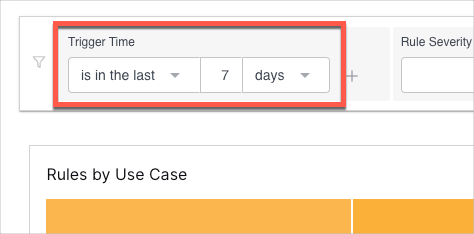
To set the Trigger Time filter, select an operator from the first drop-down menu, and then enter or select values in the adjacent fields to complete the filter phrase.
To add an additional filter phrase, click the plus icon.
Note
The default setting for Trigger Time is in the last seven days.
To set the Rule Severity filter, click the drop-down menu and select an option.
To set the Trigger Count filter, drag the handles at the ends of the slider bar to set a count range.

Click Apply.
The filters are applied to all visualizations on the dashboard.
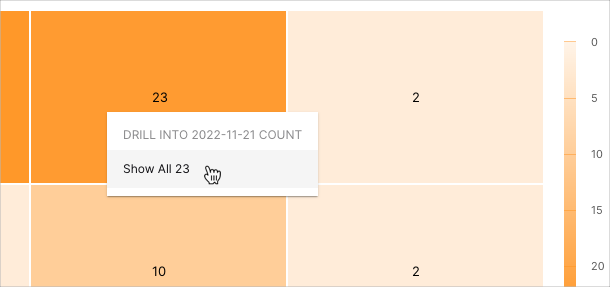
Rules by Use Case
This heat map breaks down the number of triggered rules by use case over the selected time range. Darker shading indicates a greater number of triggered rules. To drill down into a graph value and view the different rule names and their respective counts, click the graph square, and then click Show All [n].
 |
Rules Triggered Over Time
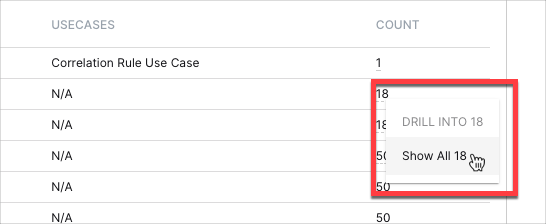
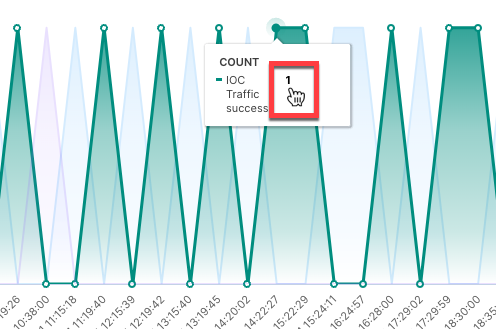
This area chart represents the count changes of the different triggered rules over the selected time range. Move your pointer over a graph area to highlight it and display the data points, which you can click to view the represented values and drill down into the data. To view the different reasons for a triggered rule and their respective counts, click the rule's count value, and then click Show All [n].
Most Rarely Triggered Rules
This table displays your rules in the order of most rarely triggered to most often triggered. It includes information on the severity and use cases associated with the rules, and their trigger counts. To drill down into a rule's trigger count and view the different rule reasons and their respective counts, click the count value, and then click Show All [n].