- Search Overview
- Search Home Page
- Performing Searches
- Basic Search
- Advanced Search
- Advanced Search Building Blocks
- Running an Advanced Search Query
- Query Syntax
- Query by Subject
- Query by Vendor and Product
- Query by Field and Value
- Query by Context Table
- Query Using Regex
- Query Using Wildcards
- Free Text Search
- Query Using Advanced Query Language Operators
- Query Using Aggregation Functions
- Query Using Structured Fields
- Dynamic Field Extraction
- Natural Language Search
- Anomaly Search
- Refine a Search
- Context Tables in Search
- Search Best Practices
- Search Results
- Histogram View of Search Results
- Search Results Navigation Bar
- Timeline View of Search Results
- List View of Search Results
- Table View of Search Results
- Aggregated Search Results
- Event Details
- Detection Details
- Entity Details
- Data Insights
- Export Search Results
- View and Download Exported Search Result Files
- Dashboard Visualizations
Query by Field and Value
You can search inside any field in the log for specific values. For example, you might want to search the logs for all events involving a specific dest_host.
Key points:
Queries can use the following syntax to search for specific fields and values:
<field>:"<value>"or<field>="<value>"<field>:"`<value>`"or<field>="`<value>`"<field>=="<value>"
The entered query will be persisted if you save your search.
You can search a range within a field by using square brackets [ ] to indicate that the results are inclusive. Or you can use curly brackets { } to show that the results are exclusive.
You cannot use wildcards inside of phrases.
Note
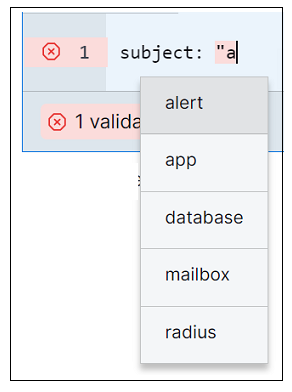
As you enter your query, Search offers suggestions to choose from, for both fields and operators.
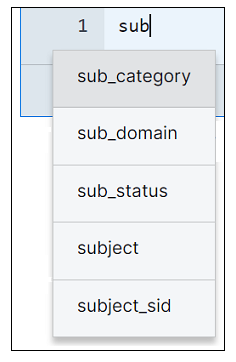
This feature applies to custom fields as well as common fields and allows you to enter your queries faster and with higher accuracy, catching errors before query execution.
Search also offers suggestions to choose from for possible subject, vendor, and products values.
The following sections illustrate examples of querying by field name:
Query by Field - Generic Syntax
This syntax is used when the data to be searched for is located in a specific field. Most syntax can be combined with each other to create more complex queries.
Note
In query syntax, : and = are interchangeable (field : value and field = value mean the same thing). We recommend that you move to using = exclusively.
Syntax | Description |
|---|---|
| Keyword matching Search a field for entries that contain a specific keyword or combination of keywords. Different syntax is available to search for the following types of keyword matches:
For more details and specific syntax, see Query by Field - Data Type-Specific Syntax. |
| Multi-value search Search for the strings where the value of the subject field is in the set ("alert", "datastore"). This is equivalent to This syntax also works for a single value, NoteLimitations:
|
| Null operator Search for rows where the To search for rows where the field does have a value (is not null), add the |
| NOT operator Search for events that do not have "Exabeam" as a vendor. The The NOT operator can also be used to ensure that a field query does not return null values, use the NOT<field>:null syntax:
|
| AND operator Search the subject field for any entries that contain the token "Exabeam" and the product field containing "Advanced Analytics". This syntax is case sensitive. Also supported are combinations with |
| OR operator Search for events where the subject field contains "alert" or the activity field contains "trigger". This syntax can be used for the same or different fields. |
| Parentheses for grouping operations Search for any network HTTP events where the subject is "Web" or the product is "Symantec." This syntax is used to group phrases within a query. |
| Context table lookup Checks if the field has a value that is listed in a specific column of a specified context table as in the following example: Note: If no column is specified in the query syntax, the search defaults to looking for values in the key column. To add a second context table to the query, use an AND operator as in the following example: See Query by Context Table or ??? for more information. |
Query by Field - Data Type-Specific Syntax
The syntax for your search will vary depending on the data type of the field (string, email, ipv4/ipv6, number, Boolean, datetime, array, etc.).
Data Type | Syntax | Description |
|---|---|---|
For example: |
| Loose Keyword Match (single word) Search the subject field for any records that contain the token/word Web. This syntax is not case-insensitive and does not find substrings of words. For example, “Webs” would not be a match. Possible Results: Web, weB |
| Loose Keyword Match (multiple words) Search the product field for records that contain both of the words This syntax is not case-insensitive and does not find substrings of words. NoteIn a loose keyword match, some special characters allow multiple words to be treated as a single token and others do not. For example:
To ensure that multiple words with a special character are treated as a single token, use the Exact Keyword Match. Possible Results: application for web search, WEB like Application, First Name, name-of-the-month-first | |
| Exact Keyword Match Search the product field for records that contain the literal string This syntax is case-sensitive. NoteThe search token is bracketed with back tick characters `. Possible Results: web application, web application user, new web application | |
| Exact Full Match Search the product field for records that contain only the literal string This syntax is case-sensitive. Possible Results: web application | |
| Optional Multi-character Wildcard Wildcard syntax searches the subject field for any entries that contain the token with the regex This syntax is not case-sensitive. | |
| Single-character Wildcard Wildcard syntax searches the subject field for any entries that contain the token with the regex This syntax is not case-sensitive. | |
| Regular Expression For details see Query Using Regex. | |
| Escaping Character To search for entries that contain double or single quotes, or a back tick character, use a back slash to escape these characters, \. NoteTo escape a back slash character that's part of a search term, use two back slashes. | |
| File Path Back slash characters, \, need to be escaped with a back slash, \. NoteThe search string cannot start with a front slash / character. | |
|
| Search for exact Boolean matches. |
|
| Search for the row where |
| Search for the row where | |
| Search for the row where | |
| Search for the row where | |
| Search for the row where | |
| Search for the row where | |
| Search for the rows where 1 <= | |
| Search for the rows where 1 <= | |
| Search for the rows where | |
| Search for the rows where 1 <= | |
|
| Search by range of IPs (inclusive). NoteLimitations:
|
| Search a range of IPs by CIDR notation (bit mask). Examples:
NoteLimitations:
| |
|
| Search a time range (inclusive) Examples:
|
