- Site Collector Overview
- Get Started with Site Collectors
- Install Site Collector
- Set Up Collectors
- Sign Up for the Early Access Program: Site Collectors
- Choose the Right Collector based on Data Sources
- Set Up Archive Windows Collector
- Set Up Archive Linux Collector
- Set Up EStreamer Collector
- Set Up Fortinet Collector
- Set Up IBM Security QRadar Collector
- Set Up Kafka Collector
- Set Up Splunk Collector
- Set Up Linux File Collector
- Set Up Microsoft SQL Collector
- Set Up MySQL Collector
- Set Up Oracle Collector
- Set Up Syslog Collector
- Set Up Windows Active Directory Collector
- Set Up Windows Event Log Collector
- Set Up Windows File Collector
- Manage Site Collectors
- Apply Antivirus Exclusions
- Migrate to the New-Scale Site Collectors Service
- Modify Collector Configuration
- Modify a Site Collector Instance
- Manage Templates
- Monitor Log Sources
- Add Filters to Set Egress Log Filtering Conditions
- New Site Collector Management Service NGSCD
- Regenerate Certificates for Collectors
- Upgrade the Site Collector
- Upgrade the Site Collector Specifications
- Vulnerability Remediation Policy
- Site Collector Monitoring
- Troubleshoot the Site Collector
- Pre-checks failed during Site Collector installation and upgrade
- Site Collector UI shows the status INSTALLATION_ERROR
- Download Support Packages for Troubleshooting
- How to reboot the Virtual Machine (VM) successfully to apply security updates?
- What information must be added while creating a support ticket to resolve an issue?
- Site Collector UI is not displaying the heartbeats
- Splunk Collector can't be set up
- Splunk Collector is set up however, logs are not reaching DL/AA
- Only a few of the installed Splunk Collectors are processing logs or EPS has dropped by 50% as compared to last hour
- The Windows Active Directory Collector (formerly known as LDAP Collector) is set up, however, the context data is not reaching DL/AA
- The Windows Active Directory Collector (formerly known as LDAP Collector) is stuck in the ‘Update’ mode after deployment
- Installation is initiated; however, the collector shows the status as ‘Setting Up’ for some time
- Data Lake and Advanced Analytics Does Not Show Context Data
- Context Data from Windows Active Directory Collector is Segmented
- Minifi Permission Denied - Logback.xml File Missing and Config File Update - Failed Error Occurred while Installing the Windows Event Log Collector
- Where should I upload proxy certificates if I am running proxy with TLS interception?
- How to upgrade Linux collector instance?
Regenerate Certificates for Collectors
Site Collector Core (Nifi) generates security certificates for secure communication. If the security certificates expire within one year, the Windows Event Log Collector stops communicating with the Site Collector instance. To avoid disrupting collector operation, refresh the SSL/TLS certificates by using the following steps.
Upgrade the Site Collector version to 1.19.2 or later.
You can update the Windows certificate for Site Collector version 1.19.1 and later and the Linux certificate for Site Collector version 1.19.2 and later.
Log in to the VM on which Site Collector is installed and use the following command to generate new SSL certificates for Site Collector versions before Site Collector 2.2.
sudo /opt/exabeam/nifi/nifi_scripts/regenerate_certificate.sh
Refer to the following screenshot as an example of how the output may look like.
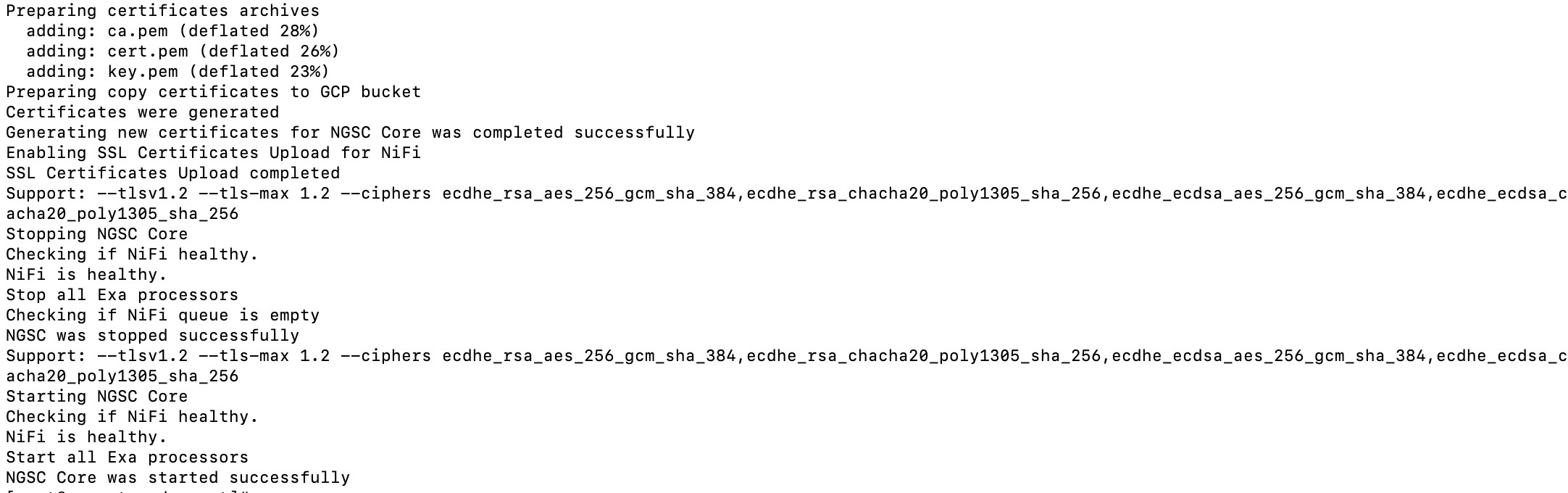
If you are using Site Collector version 2.2 and later, use the steps mentioned in the Generate TLS Certificate section to refresh the security certificates.
To refresh certificates to resume communication with Site Collector Core (Nifi), for Windows collectors including Windows Event Log collector, Windows File collector, and Windows Archive collector, run the following command in PowerShell on the Windows VM on which the collector is installed.
Note
You must be an administrator to run the command.
powershell.exe -NoLogo -ExecutionPolicy Bypass -Command "Invoke-WebRequest -OutFile 'windows_certificates_update.ps1' -Uri 'http://<SiteCollectorIP>:9875/?filename=windows_certificates_update.ps1'; .\windows_certificates_update.ps1 <SiteCollectorIP> -force"
Replace <SiteCollectorIP> with the private IP of the VM on which the Site Collector is installed.
Refer to the following screenshot as an example of how the output may look like to indicate that certificate update is successful.
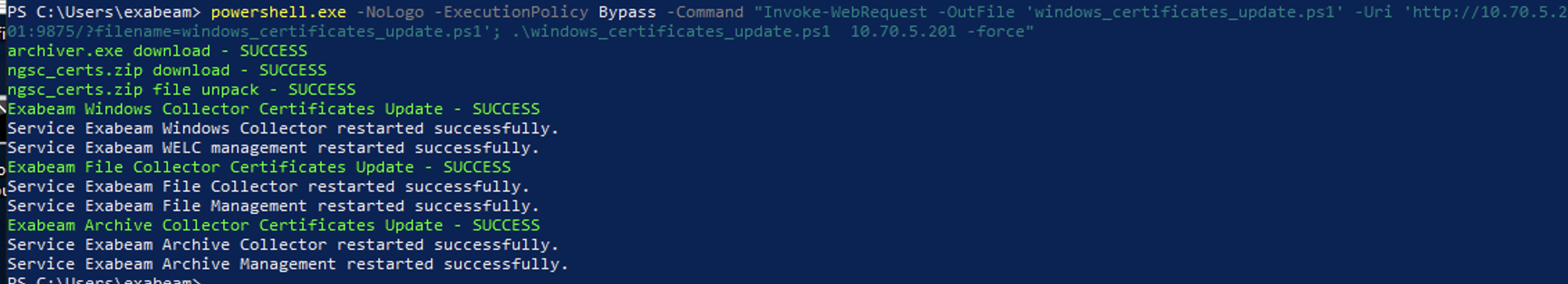
If the above script does not download the certificates directly from the Site Collector instance, download the certificates directly from the user interface and copy them to the Windows server. Then, run the following script in the directory in which the certificates are placed.
powershell.exe -NoLogo -ExecutionPolicy Bypass -Command "Invoke-WebRequest -OutFile 'windows_certificates_update.ps1' -Uri 'http://<SiteCollectorIP>:9875/?filename=windows_certificates_update.ps1'; .\windows_certificates_update.ps1 <SiteCollectorIP> -force"
Replace <SiteCollectorIP> with the private IP of the VM on which the Site Collector is installed.
For the Linux based collectors such as, Linux File collector and Linux Archive collector, run the following command on the Linux machine on which collector is installed.
sudo -- sh -c 'curl -o linux_certifcates_update.sh http://<SiteCollectorIP>:9875/?filename=linux_certifcates_update.sh; chmod +x linux_certifcates_update.sh | bash -s; ./linux_certifcates_update.sh <SiteCollectorIP>'
Replace <SiteCollectorIP> with the private IP of the VM on which the Site Collector is installed.
Troubleshoot Common Issues
Scenario 1: If the regenerate_certificate script at /opt/exabeam/nifi/nifi_scripts/regenerate_certificate.sh fails because of incompatibility of specific CURL versions with Site Collector Core (Nifi) API, modify the script on your VM by updating the generate_nifi_token() function as follows.
generate_nifi_token() {
NIFI_WEB_UI_TOKEN=$(curl --silent $TLS_FLAG $CIPHERS_FLAG $CURVES_FLAG --fail -XPOST -k "$NIFI_API/access/token" -H "Content-Type: application/x-www-form-urlencoded" -d "username=$SINGLE_USER_CREDENTIALS_USERNAME&password=$SINGLE_USER_CREDENTIALS_PASSWORD" 2>&1)
NIFI_VERSION="2.0.0-SNAPSHOT"
return 0
}
Save the changes to generate and upload a new certificate, then restart your Site Collector instance.
Scenario 2: The regenerate_certificate.sh restarts Site Collector core. However if the certificate is already expired, restarting Site Collector core fails. In this case, restart the Nifi service using systemctl restart exabeam-ngsc.
Generate TLS Certificate for Release 2.2 and Later
If you use the Site Collector version 2.2, use the following steps to regenerate TLS certificates.
Generate CA Certificate and Server Certificate
To regenerate new certificates for Site Collector and upload the certificates to the Exabeam cloud, use the following steps.
Stop the site collector service.
sudo ./ngsccli sitecollector stop
Run the following command to regenerate the certificate.
sudo ./ngsccli certificate regenerate
The existing TLS certificates that Site Collector Core (NiFi) uses to receive data are replaced with the latest certificates.
Start the Site Collector service.
sudo ./ngsccli sitecollector start
Update the all the existing collectors that use certificates to send data.
Generate Server Certificate Only
If you have installed Site Collectors version 2.2 and want to retain the existing CA certificate, and generate only the server certificate, set the --newca flag to false. Refer to the following command.
sudo ./ngsccli certificate regenerate --newca=false
If you want to check the expiration of an existing CA certificate:
Check if the
ca.certfile is available in /opt/exabeam/auth/ssl/ngsc/.If the
ca.certfile is not available, it indicates that the Site Collector version is prior to version 2.2 and you must regenerate the CA certificate.To check the expiration of the CA certificate, use the following openssl command.
openssl x509 -in ca.pem -text -noout | grep "Not After"
Set Custom Expiration
The default expiration that is set for CA certificate is 10 years, and for server certificate is 2 years. To set custom expiration, use --ca-expiration and --cert-expiration flags to set expiration in years.
sudo ./ngsccli certificate regenerate --ca-expiration=5 --cert-expiration=1
Upload Certificates
If the automatic upload of certificates to the Exabeam cloud fails, to manually upload the certificates use the following command.
sudo ./ngsccli certificate upload
Upgrade to Set Up Automatic Certificate Refresh
The Site Collector version 2.3 enables you to start an automated process for updating the security certificates, hence upgrade the Site Collector instance to version 2.3 or later.
It is recommended to upgrade Windows Event Log Collector, Windows File Collector, and the Windows Archive Collector to version 2.3 or later before starting with the certificate refresh process.
Use the following steps to start the certificate refresh process.
Log in to the New-Scale Security Operations Platform with your registered credentials.
Navigate to Collectors > Site Collectors.
Ensure that Site Collector is installed and in running state.
On the Site Collector page, click the Site Collector Instances tab.
In the CERTIFICATE EXPIRES IN DAYS column, click the refresh button that appears within two weeks of certificate expiration.
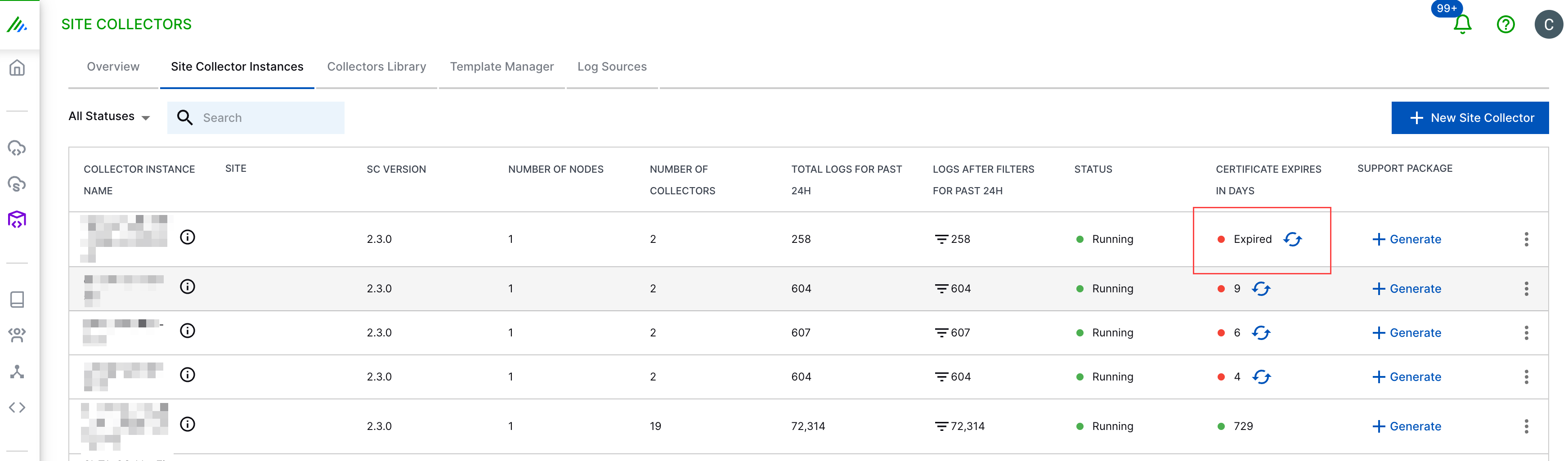
In the confirmation message window, click Confirm.
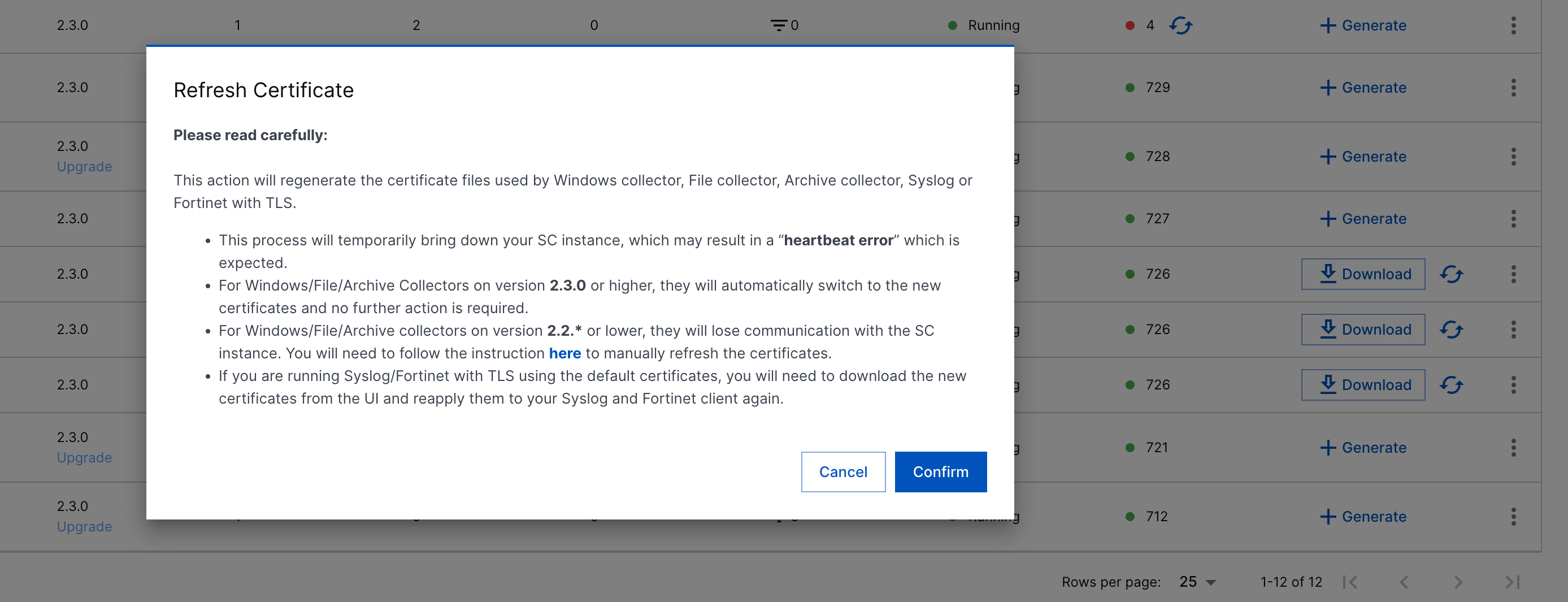
The Site Collector instance generates new security certificates. This may affect the performance and pause the data flow until new certificates are added to the Site Collector's trust store and the Site Collector instance is restarted.
For Windows Event Log Collector, Windows File Collector, and Windows Archive Collector instances on Site Collectors 2.3, new security certificates are automatically downloaded and applied without any need for user action. The collector instance may show a heartbeat error during the automatic certificate generation process. For the Windows collector instances that are configured on the previous versions of Site Collector such as version 2.2 and earlier, refresh the security certificates using the following command.
powershell.exe -NoLogo -ExecutionPolicy Bypass -Command "Invoke-WebRequest -OutFile 'windows_certificates_update.ps1' -Uri 'http://<SiteCollectorIP>:9875/?filename=windows_certificates_update.ps1'; .\windows_certificates_update.ps1 <SiteCollectorIP> -force"
Note
For Syslog collector with TLS and for the Fortinet collector with TLS, the security certificates are updated when you start with the automatic certificate refresh via the user interface. Edit the configuration for the collector instance and click Download Certificate. Then upload this downloaded certificate to the Syslog or Fortinet server.
