- Site Collector Overview
- Get Started with Site Collectors
- Install Site Collector
- Set Up Collectors
- Sign Up for the Early Access Program: Site Collectors
- Choose the Right Collector based on Data Sources
- Set Up Archive Windows Collector
- Set Up Archive Linux Collector
- Set Up EStreamer Collector
- Set Up Fortinet Collector
- Set Up IBM Security QRadar Collector
- Set Up Kafka Collector
- Set Up Splunk Collector
- Set Up Linux File Collector
- Set Up Microsoft SQL Collector
- Set Up MySQL Collector
- Set Up Oracle Collector
- Set Up Syslog Collector
- Set Up Windows Active Directory Collector
- Set Up Windows Event Log Collector
- Set Up Windows File Collector
- Manage Site Collectors
- Apply Antivirus Exclusions
- Migrate to the New-Scale Site Collectors Service
- Modify Collector Configuration
- Modify a Site Collector Instance
- Manage Templates
- Monitor Log Sources
- Add Filters to Set Egress Log Filtering Conditions
- New Site Collector Management Service NGSCD
- Regenerate Certificates for Collectors
- Upgrade the Site Collector
- Upgrade the Site Collector Specifications
- Vulnerability Remediation Policy
- Site Collector Monitoring
- Troubleshoot the Site Collector
- Pre-checks failed during Site Collector installation and upgrade
- Site Collector UI shows the status INSTALLATION_ERROR
- Download Support Packages for Troubleshooting
- How to reboot the Virtual Machine (VM) successfully to apply security updates?
- What information must be added while creating a support ticket to resolve an issue?
- Site Collector UI is not displaying the heartbeats
- Splunk Collector can't be set up
- Splunk Collector is set up however, logs are not reaching DL/AA
- Only a few of the installed Splunk Collectors are processing logs or EPS has dropped by 50% as compared to last hour
- The Windows Active Directory Collector (formerly known as LDAP Collector) is set up, however, the context data is not reaching DL/AA
- The Windows Active Directory Collector (formerly known as LDAP Collector) is stuck in the ‘Update’ mode after deployment
- Installation is initiated; however, the collector shows the status as ‘Setting Up’ for some time
- Data Lake and Advanced Analytics Does Not Show Context Data
- Context Data from Windows Active Directory Collector is Segmented
- Minifi Permission Denied - Logback.xml File Missing and Config File Update - Failed Error Occurred while Installing the Windows Event Log Collector
- Where should I upload proxy certificates if I am running proxy with TLS interception?
- How to upgrade Linux collector instance?
Set Up Syslog Collector
Syslog Collector is a set of Site Collector flows, out-of-the-box processors, groups, custom processors, other components, and integrations aimed at getting syslog logs from various sources such as Linux OS logs, FTP, and network, and pushing the logs to New-Scale Security Operations Platform for further processing. For a successful use case implementation in Exabeam Cloud and easy monitoring of log sources, the Syslog collector helps to enable log onboarding from various sources.
Note
The Site Collectors service supports ingestion of single line and multi-line syslog events. The events can be of various Syslog protocols such as RFC 5424, RFC 5425, RFC 5427, and RFC 5848.
To set up the Syslog collector:
Log in to the New-Scale Security Operations Platform with your registered credentials.
Navigate to Collectors > Site Collectors.
Ensure that Site Collector is installed and in running state.
On the Site Collector page, click the Collectors Library tab, then click Syslog.
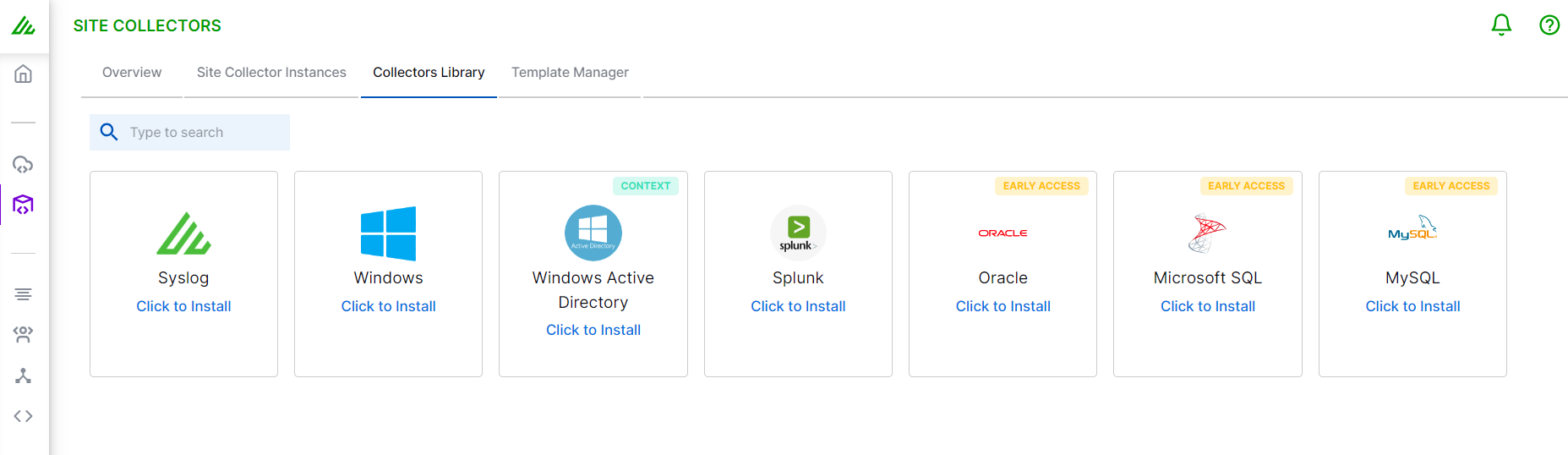
In the Definition section, enter the required information as follows.
Collector Name – Specify a name for the Syslog collector.
Note
Ensure that you specify different names for Site Collector instance and the Syslog collector.
Site Collector Instance – Select the site collector instance for which you want to install the Syslog collector.
Port – Enter the port number of the Syslog server, 514, or 515, or from the supported port range 1024 - 49151.
To support ports 514 and 515, Site Collector version 2.11.0 or higher is required.
Note
Creating multiple Syslog collectors under the same Site Collector instance with the same protocol and port causes conflicts, because only one collector can bind to that protocol–port combination. The user interface displays a validation warning when you attempt to assign a port that is already in use by another Syslog collector within the same Site Collector instance.
Click Next.
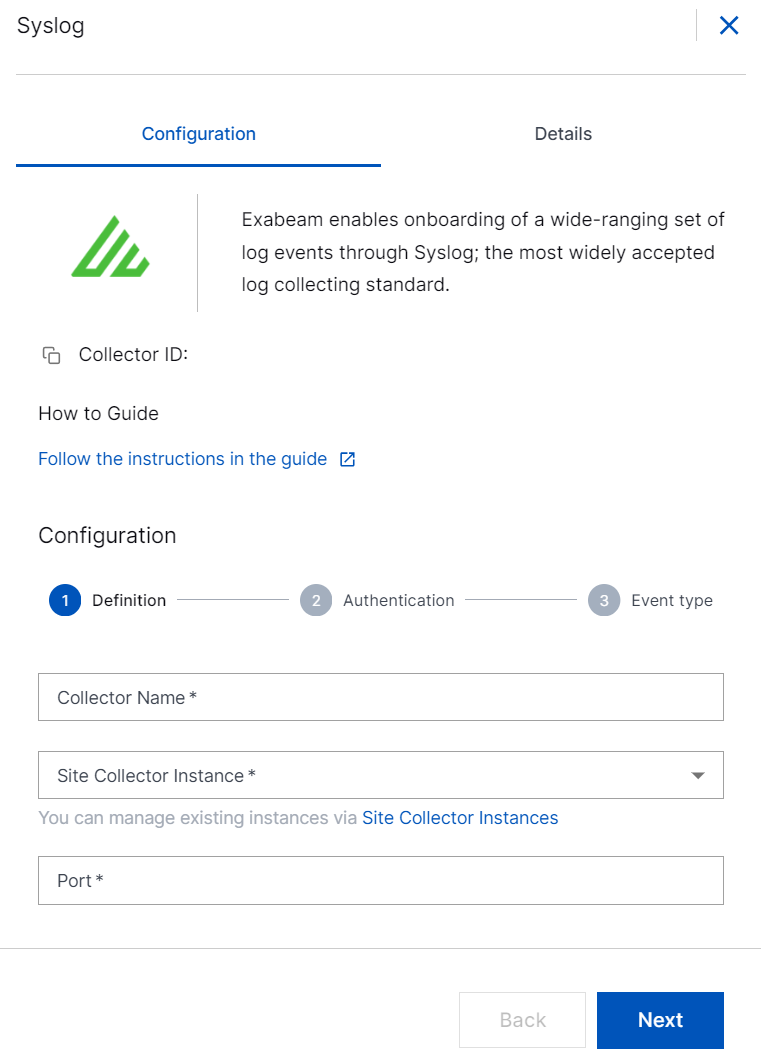
In the Authentication section, select the required protocol from the list: UDP or TCP.
UDP – For faster log collection and reduced transmission overhead, considering lower network costs for logs with increased variability, select UDP. A huge amount of Syslog data within the same network with minimal packet loss is transmitted over UDP.
Syslog UDP supports maximum 1024 Byte message size because of Syslog UDP RFC, and 10k EPS with minimal data loss.
Use UDP when the log size is less than 1Kb because based on the UDP protocol, UDP packets are of 1Kb size and there is minimal data loss for the log size that is less than 1kb. To optimize data loss prevention for Syslog UDP, the updated configuration changes related to operating system have been implemented. The Operating System level socket receive buffer size is configured as follows:
net.core.rmem_default = 17039360
net.core.rmem_max = 17039360
Note
Syslog UDP may not work reliably on RHEL 9.6, and may lead to data loss.
TCP – If you need reliable and ordered data transmission between networks, select TCP, to transmit Syslog data over TCP securely. To configure a secure syslog ingestion, select TCP and enable the Secure Connection option.
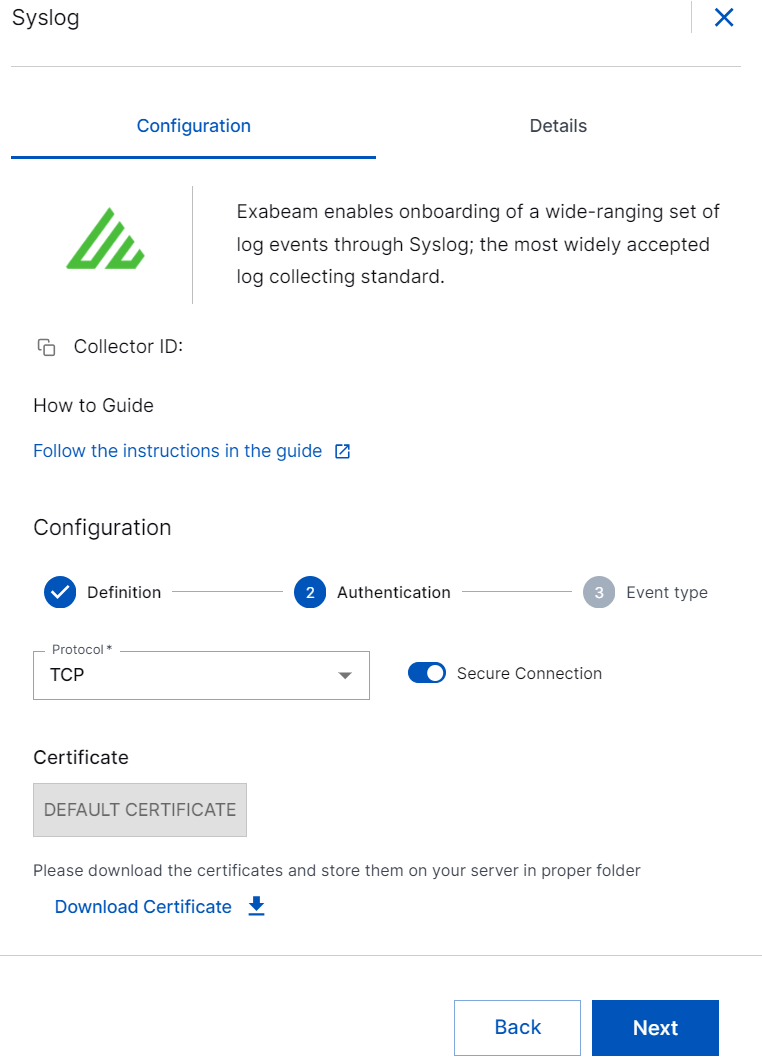
To enable secure and encrypted TLS communication between your syslog server and the Syslog Collector, download the Exabeam generated default security certificates, or upload your custom certificates. You can use default or custom certificates.
Click DEFAULT CERTIFICATE, and click Download Certificate. Then save and apply the downloaded certificates on your syslog server.
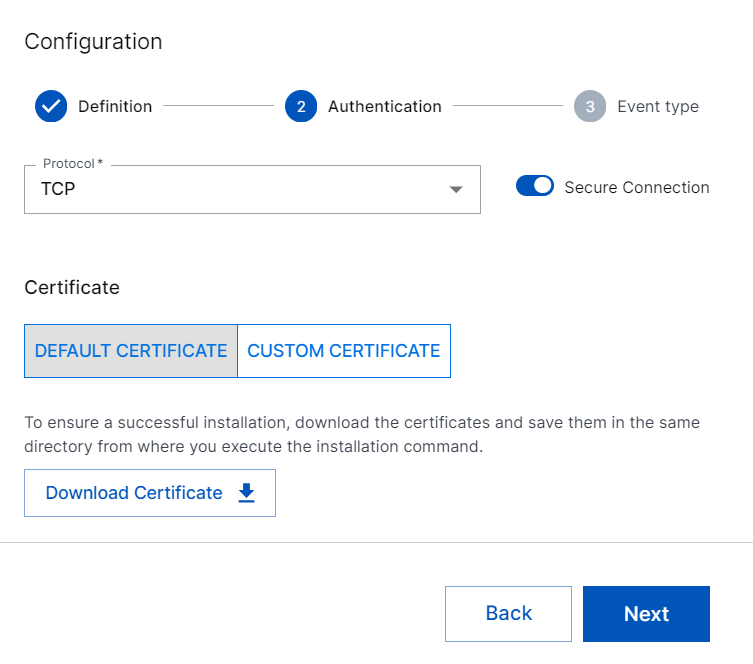
To use custom certificates signed by Certificate Authority (CA), click CUSTOM CERTIFICATE, and click Select File. Upload the certificate files: cert.pem, key.pem, and (optional) ca.pem that are bundled in a .tar.gz archive file. If you upload the optional ca.pem, all the subsequently uploaded certificates that are signed by this Certificate Authority (CA) will be accepted. To know how to generate the cert.pem, key.pem, and ca.pem files, see Generate Custom Certificate Using OpenSSL.
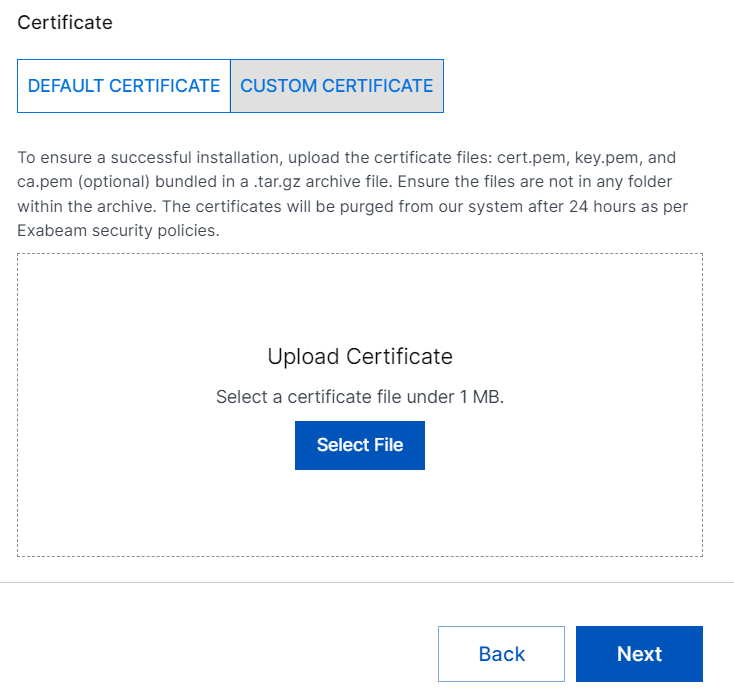
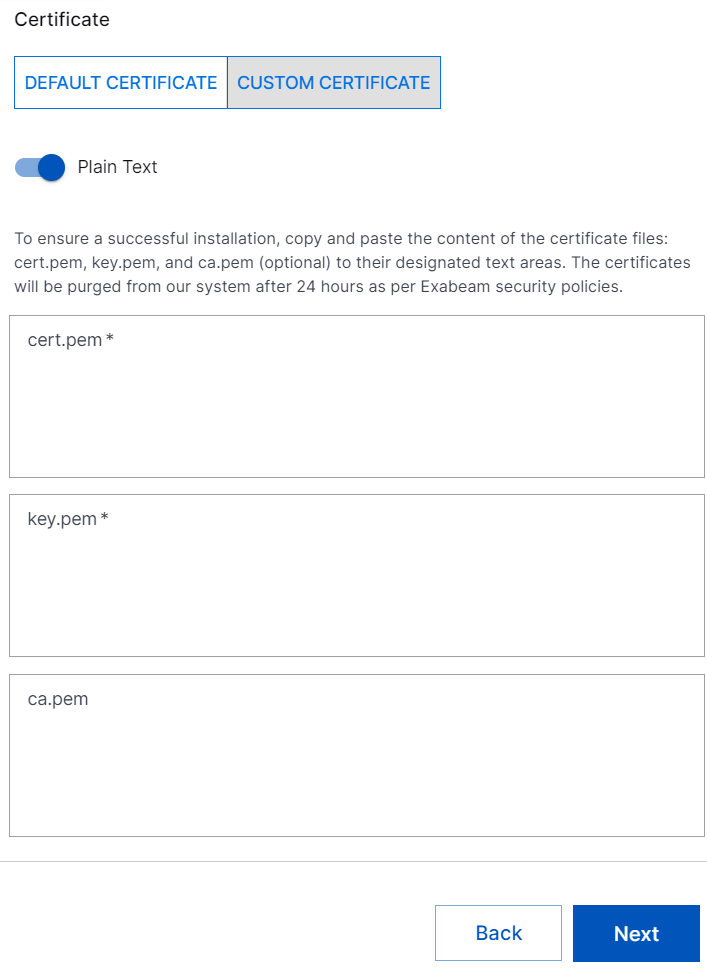
In addition to uploading the certificates in .tar.gz format, you can paste the content of your custom certificates that are in key.pem, cert.pem, or ca.pem format into the relevant text box.
In the Event type section, select the required event type in which you want the collector to read logs: SINGLE LINE or MULTI-LINE.
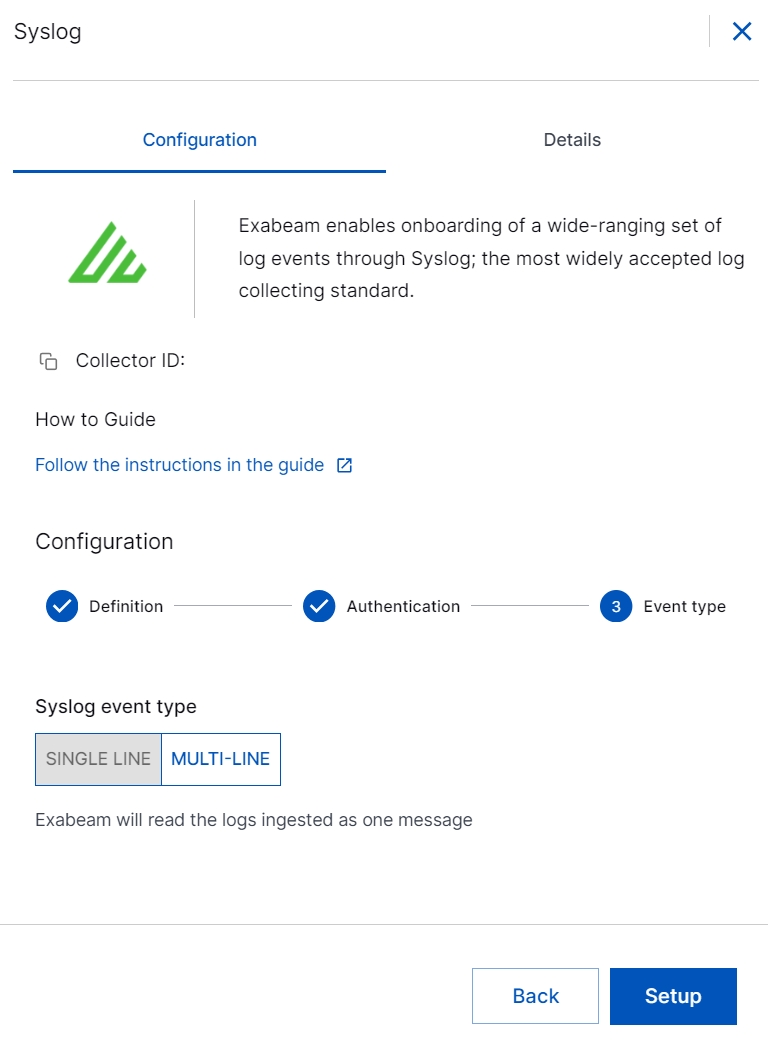
If you select SINGLE LINE, the collector reads ingested logs as one message. The message is split by line breaks.
If you select MULTI-LINE, specify a regex pattern (regular expressions) to define where a message starts and ends which extends across multiple lines, by clicking +Pattern.
To test the accuracy of the regular expressions, click Check Patterns.
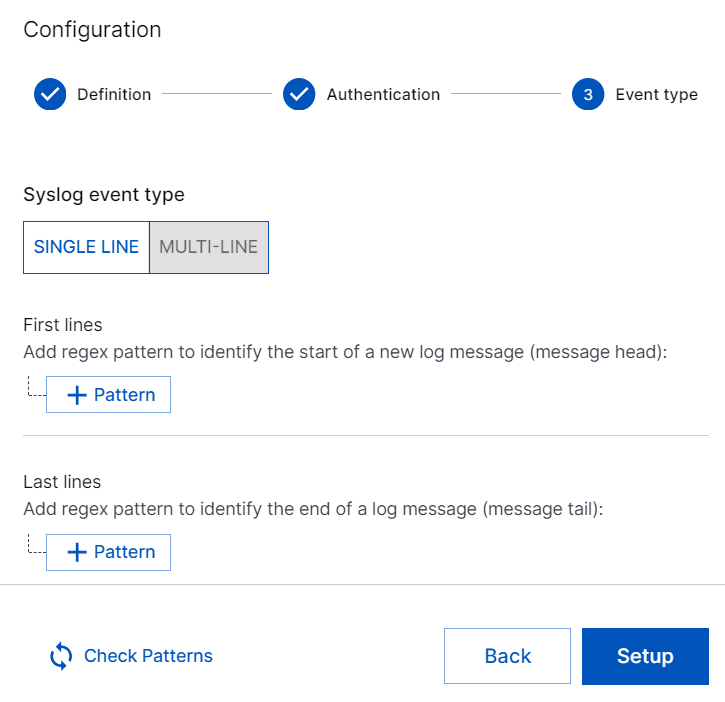
To set up the Syslog collector, click Setup.
The configuration for Syslog Collector is complete. The collector is set up and ready to receive the logs pushed by syslog sources.
While configuring the Syslog Collector, if you need assistance for managing ports, refer to the following sections on managing ports. For more information, refer to Set up virtual machine on your cloud platform.
Generate Custom Certificate Using OpenSSL
Using the open-source command-line toolkit OpenSSL that allows you to perform SSL and TLS protocols related tasks, you can create custom certificates to ensure secure and encrypted TLS communication between your syslog server and the Syslog Collector.
To generate an SSL certificate using the OpenSSL, perform the following steps.
To generate a private key for the Certificate Authority (CA), use the following command.
openssl genrsa 4096 > ca-key.pem
To generate the X509 certificate for the CA, use the following command.
openssl req -new -x509 -nodes -days 365 \ -key ca-key.pem \ -out ca.pem \ -subj "/CN=ca"
To generate the private key and certificate request, use the following command.
openssl req -newkey rsa:4096 -nodes -days 365 \ -keyout key.pem \ -out req.pem
To generate the X509 certificate for the server, use the following command.
openssl x509 -req -days 365 -set_serial 01 \ -in req.pem \ -out cert.pem \ -CA ca.pem \ -CAkey ca-key.pem \ -subj "/CN=server"
Manage Ports with Firewall on Ubuntu
If you use Ubuntu, use Uncomplicated Firewall (ufw) that is a frontend for iptables. To enable ufw firewall, allow ssh access, enable logging, and check the status of the firewall by using the following commands.
Before enabling the firewall for Ubuntu, use the following command to allow SSH.
sudo ufw allow ssh sudo ufw enable;sudo ufw reload;sudo ufw status
To ensure that the destination port is enabled for TCP traffic, use the following command:
sudo ufw allow exposed_port/tcp sudo ufw allow effective_port/tcp
To edit the UFW configuration, use the following command:
sudo vi /etc/ufw/before.rules
Before * filter section, insert the following commands, modify the parameters
exposed_portandeffective_portwith the port number on which you want to enable the requests from outside and port number of the port on which the service is listening respectively.*nat :PREROUTING ACCEPT [0:0] -A PREROUTING -p tcp --dport exposed_port -j REDIRECT --to-port effective_port COMMIT
To enable and reload the firewall, use the following command:
sudo ufw enable sudo ufw reload
To check the status, run
sudo ufw statusand get the expected output as follows:Status: active To Action From -- ------ ---- exposed_port/tcp ALLOW Anywhere effective_port/tcp ALLOW Anywhere exposed_port/tcp (v6) ALLOW Anywhere (v6) effective_port/tcp (v6) ALLOW Anywhere (v6)
Manage Ports with Firewall on RHEL
If you use RHEL, before enabling the firewall for RHEL, use the following command to allow SSH.
sudo firewall-cmd --permanent --add-service ssh sudo firewall-cmd --reload
You must see 'success' after you run the above commands. Following is an example of the output that you receive.
[exabeam@ngsc ~]$ sudo firewall-cmd --permanent --add-service ssh success [exabeam@ngsc ~]$ sudo firewall-cmd --reload success
To validate your changes after reloading, use the following command.
sudo firewall-cmd --list-services
You can now see ssh and any other services you have configured here. Following is an example of the output that you receive. This allows users to SSH into the VM after firewall is enabled, to execute shell command for installing Site Collector.
[exabeam@ngsc ~]$ sudo firewall-cmd --list-services ssh
To setup port forwarding, run the following commands:
sudo firewall-cmd --add-forward-port=port=514:proto=tcp:toport=1514 --permanent sudo firewall-cmd --reload
